From Kubernetes Security Posture Management (KSPM) to Cloud Infrastructure Entitlement Management (CIEM), the cloud security market is continuously disrupting and delivering new ways to protect your cloud infrastructure. As you evaluate how a new cloud security tool fits into your toolkit, you must consider the impact it has on your team’s ability to prevent and respond to security breaches.
Take for instance the siloed focus on compliance and misconfiguration risk management in the early generations of Cloud Security Posture Management (CSPM) tooling. A typical organization today has approximately 250,000 unresolved misconfigurations in their cloud environment*. While a security team spends months rallying developer resources to fix these vulnerabilities, an attacker simply needs to find one risky misconfiguration to break in.
Yes, the attacker has an unfair advantage over your cloud team. And the siloed ways in which various vendors are bundling together products and approaching cloud security isn’t helping your team.
Identify The Gaps in Your Risk Equation
Risk = Correlate (Vulnerabilities, Assets, Threats)
To effectively manage risk, one must implement a cloud risk detection strategy that understands and correlates security insights from multiple sources. For instance, if your current technology stack is a CSPM focused entirely on vulnerability management, you must find better ways to integrate asset context and threat monitoring capabilities to help optimize security decision making.
Identities
In a recent conversation, the head of cloud operations at a large enterprise mentioned that building a good understanding of cloud assets including the entire architecture is a priority onboarding activity for new cloud administrators joining their team. And this makes logical sense. Knowing what workloads drive your most critical apps and where your most sensitive data lives can help you better prioritize your security posture management activities.
Assets = Correlate (Resources, Identities, Entitlements, Business Value)
However, missing in their view of cloud assets are the entitlements that various human and non-human identities have to their cloud resources. And given that nearly 84% of organizations experienced an identity related breach in the last year, this concern is valid**.
When beginning to assess cloud infrastructure entitlement risk, you must understand –
- How many human and machine identities exist in your cloud environment?
- What roles and permissions entitle identities to sensitive data and cloud resources?
- Do these identities need or use the level of access available to data or resources?
Threat Activity
According to Cybersecurity Ventures, a new Ransomware attack will hit organizations every 11 seconds***. While this statistic sounds overwhelming, what if your team can turn this into an advantage by prioritizing vulnerabilities management efforts on assets that are most prone to such threat activity?
In his book The Art of War, author Sun Tzu said, “if you know your enemy and yourself, you need not fear the result of a hundred battles.” Today, cyberspace is the new battleground in modern warfare. Applying the lessons from traditional warfare, you can relate that having a good understanding of cloud asset context coupled with vulnerability insights can help your organization better understand gaps in the cloud security posture. But understanding the mindset of your enemy i.e., attacker can help you prevent and circumvent a major attack on your cloud infrastructure.
Harness The Power of Correlation
To help your organizations better prioritize and mitigate cloud risk, today, we are pleased to announce new public betas for AWS entitlement visibility, anomaly detection, and threat correlation capabilities in CloudHealth Secure State. Additionally, we are also announcing the general availability of our Free Tier service offering to democratize access to enterprise grade cloud security for all developer teams.
By delivering an integrated platform that correlates infrastructure relationships, entitlements, and misconfigurations with anomalies, CloudHealth Secure State helps you get into the mindset of an attacker and visualize how they could move laterally to gain access to your sensitive cloud resources. Powered by real-time change detection, machine learning, and automation, the solution helps your teams differentiate critical threats from other alerts and leverage context to reduce mean time to respond (MTTR) to security breaches.
What’s New
Entitlements Visibility
- Bi-directional visibility into relationships between identities, entitlements, and cloud resources
- Visualize and categorize what humans or machine identities are entitled to access cloud resources
- Identify sensitive entitlements that could lead to risky conditions such as a credential exposure across cloud infrastructure
Threat Correlation and Anomaly Detection
- Isolate critical threats from noise by correlating anomalies with risky misconfigurations to prioritize response to critical security incidents
- Identify anomalous user and machine behavior by leveraging machine learning to monitor audit logs
- Monitor key storage services such as Amazon S3 and Amazon DynamoDB for anomalous data access or exfiltration
Free Tier
- Monitor one cloud account and one Kubernetes cluster, and add unlimited users for free
- Investigate issues, search cloud inventory, and understand resources relationships using visual graphs
- Benchmark security posture against Center for Internet Security (CIS) frameworks and review misconfigurations with visual risk context
Sample Breach Analysis: S3 Bucket Compromise
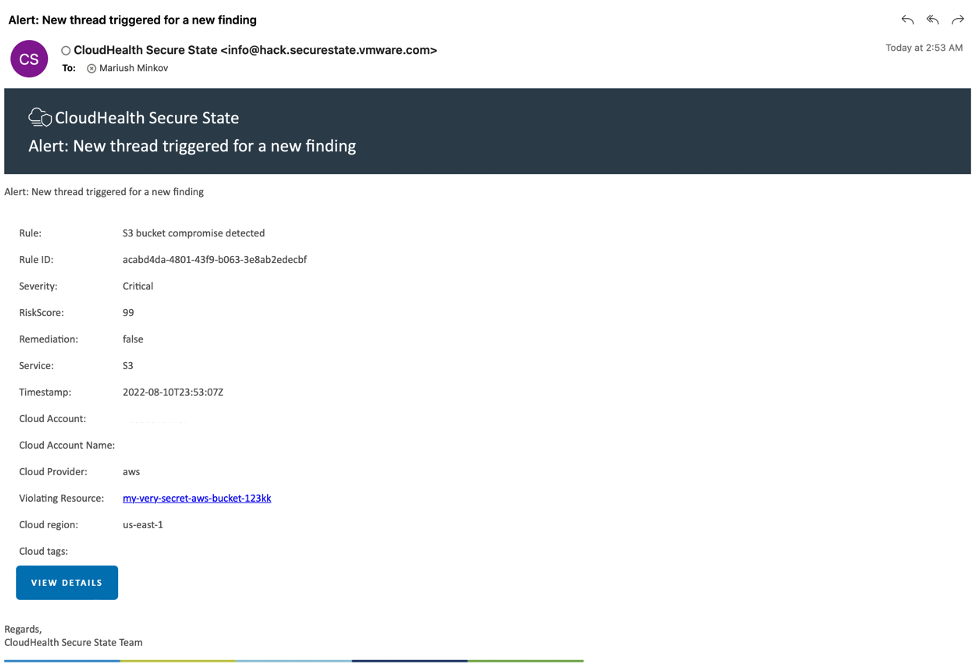
Figure 1: Email alert indicating S3 bucket compromise
Let’s look at an example scenario in which you get an alert from our Secure Cloud solution indicating a S3 bucket in your AWS infrastructure has been compromised (Figure 1).
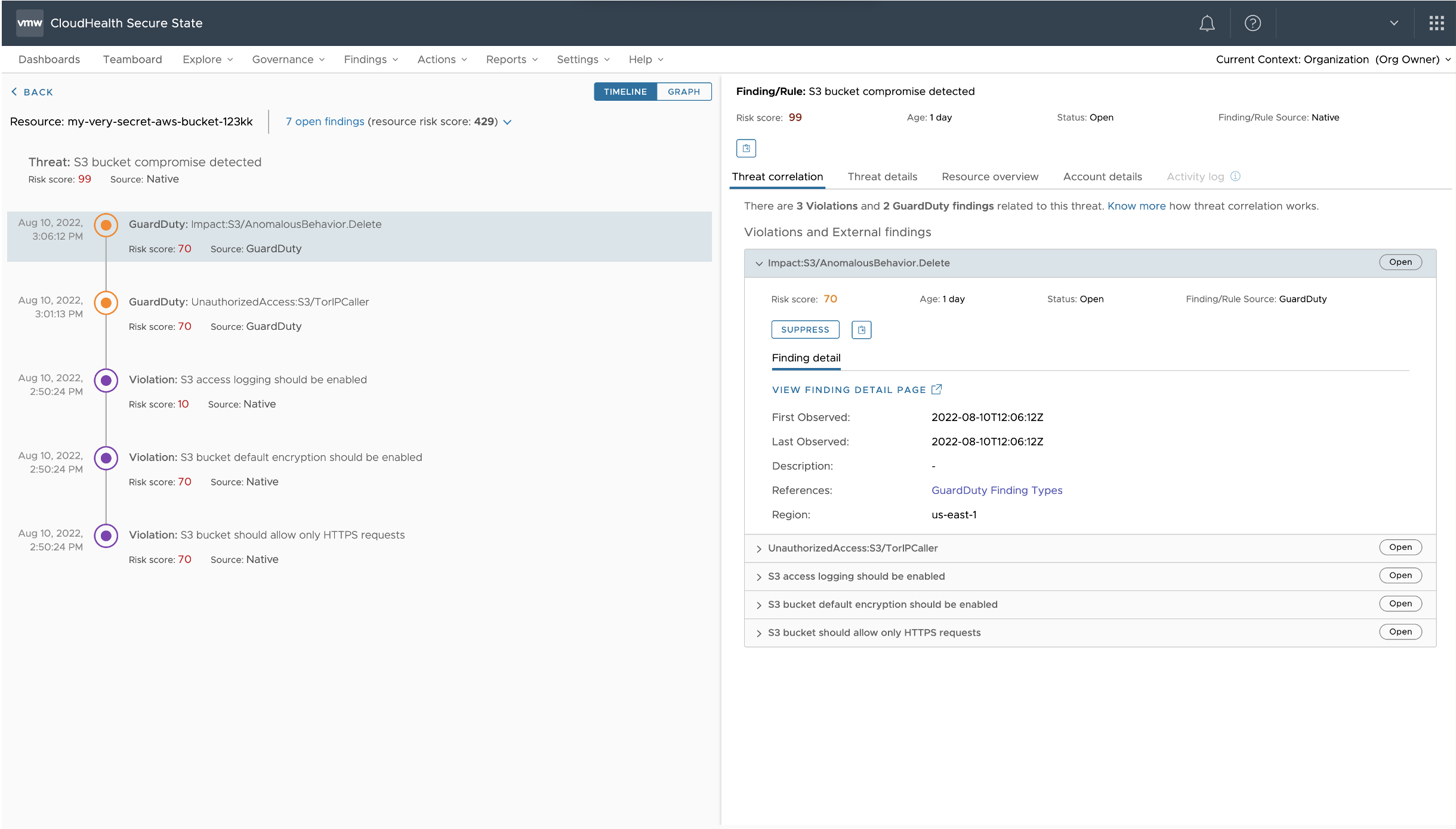
Figure 2: Threat context
One click into that email, the service takes you to a single screen (Figure 2) that delivers all context you need to prepare a speedy response. This includes overall threat severity score, multiple anomalies that triggered the alert, different misconfiguration findings that increase the risk level, and asset context to identify the breached S3 bucket, associated cloud account, users, and permissions to the resource.
As you review the context, you notice there are several Amazon GuardDuty alert indicating suspicious activity including users deleting data in unusual ways and accessing the bucket from a Tor IP. The S3 bucket also has several violations that could be exploited to access the bucket without secure HTTPS access, exfiltrate unencrypted data, and go untraced as the logging is disabled. Immediately after this analysis your attention turns towards the bucket owner email under cloud account details. You send them a slack alert and an email asking them to immediately address these violations to limit further damage from this active breach.
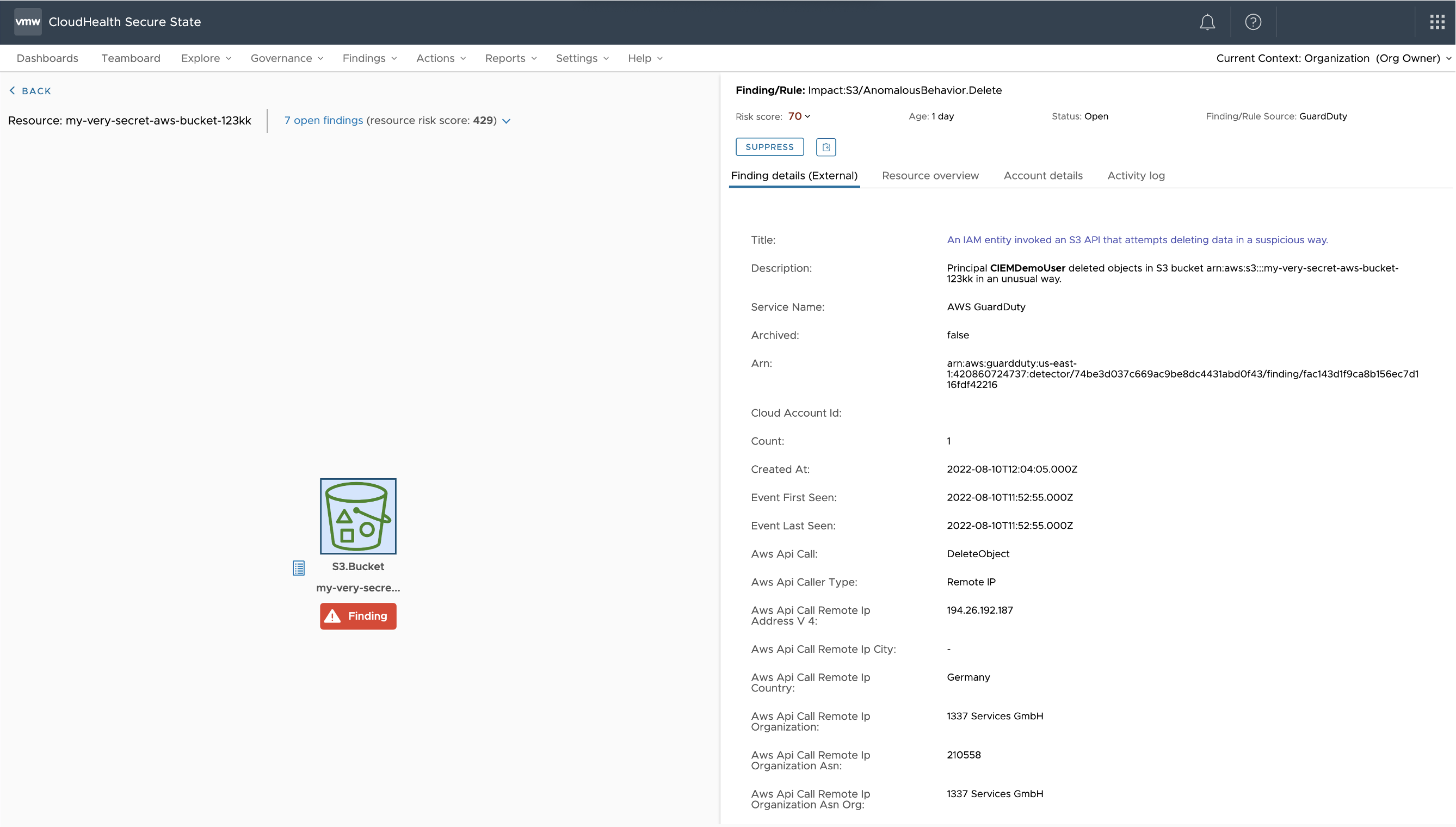
Figure 3: Anomaly details
As you continue investigation (Figure 3), you see the GuardDuty finding “AnomalousBehavior.Delete” and notice that the principal “CIEMDemoUser” has deleted data and potentially been compromised in the breach.
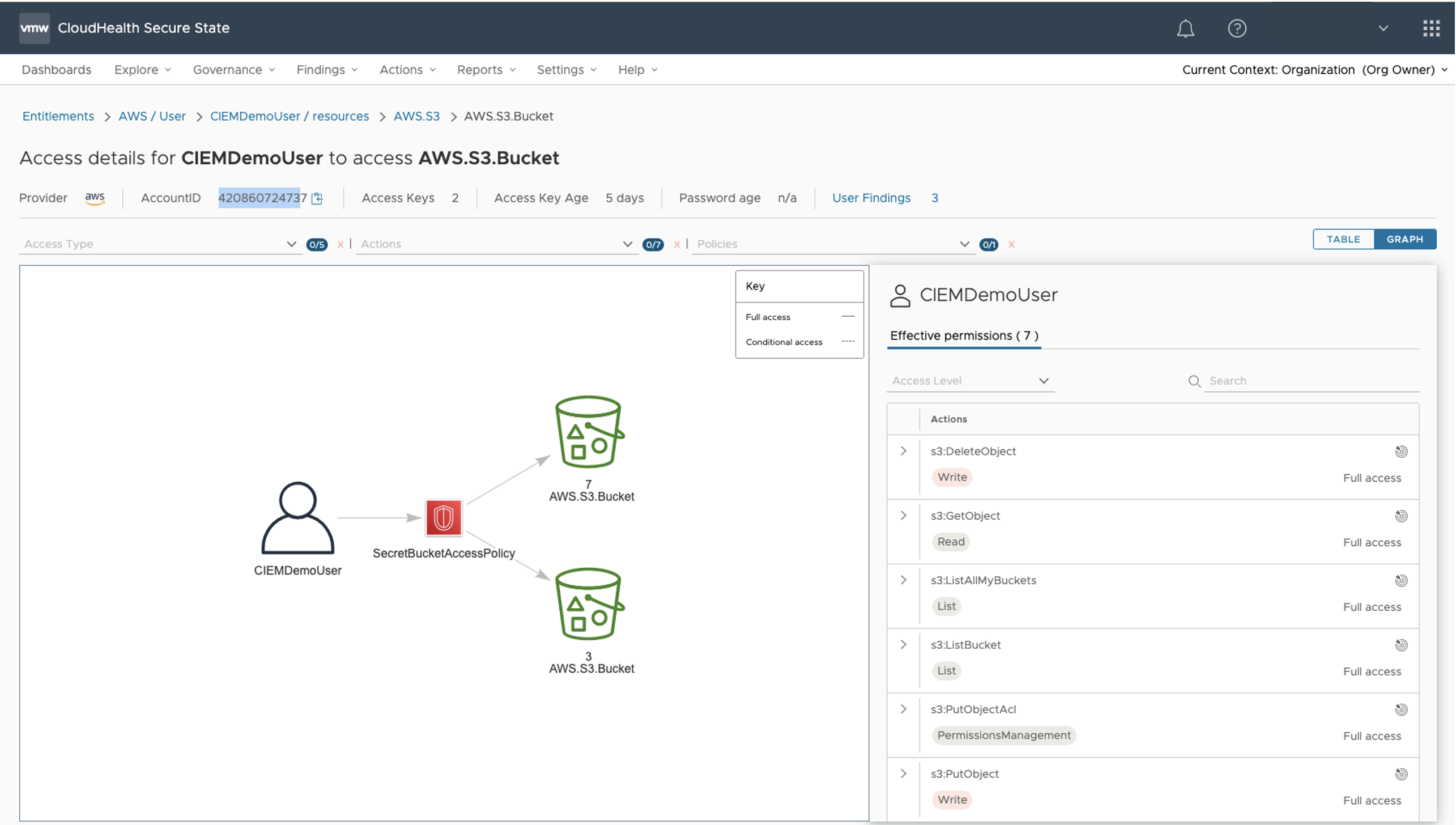
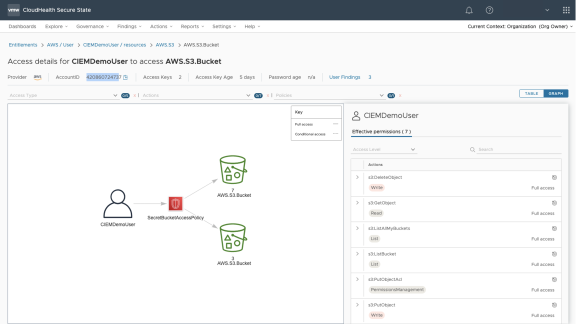
Figure 4: Entitlement visibility
Explore further in the Entitlements view, you realize that CIEMDemoUser has list and write permissions to several other S3 buckets. Concerned that the hacker might further escalate the attack to those buckets, you send another alert to the account owner asking them to review and right size CIEMDemoUser access.
Get Your Free Account Now!
As a cloud user, securing the control plane by hardening platform configurations across IaaS, PaaS, and SaaS services is a foundational priority for your team. Getting started on this journey is easy! All you need is a minute to fill out a simple form to get instant access to your free CloudHealth Secure State account. Within minutes, you will be reviewing critical misconfigurations and reviewing architecture of the cloud infrastructure supporting your applications. And with a head start on your security journey, we make it easier to prioritize risk with a unified platform that delivers CSPM, KSPM, CIEM, & Threat Correlation as one integrated cloud configuration security solution. For a deeper dive on CloudHealth Secure State, contact your cloud security expert now!
Sources:
*VMware proprietary research, CloudHealth Secure State
**New Study Reveals 84% of Organizations Experienced an Identity-Related Breach in the Last Year, Press Release, June 22,2022, Identity Defined Security Alliance
***Global Ransomware Damage Costs Predicted To Reach $20 Billion (USD) By 2021, Oct 21, 2019, Cybersecurity Ventures