Computer networks have become larger, more complex, and highly dynamic. Similarly, the tactics, techniques, and procedures (TTPs) adopted by powerful adversaries often backed by nation-states have evolved, creating challenges for security administrators and SOC analysts, who must make sense of the flood of data and alerts produced by security tools.
Since attacks have the inherent goal of achieving progressively higher access to resources, they often follow a common process in which an initial compromised endpoint is used as a bridgehead to access additional parts of the target’s infrastructure. This process has been in part codified in the MITRE ATT&CK framework in which the kill-chain of an attack is described as a series of tactical achievements, namely reconnaissance, resource development, initial access, execution, persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, collection, command and control, exfiltration, and impact. While there are few cases that rigidly follow a process that touches on these tactics in a linear manner, most attacks have only a few of these steps and often have sub-patterns that reflect the repetitive nature of the exploitation process. However, one of the most essential (and often overlooked) aspects of multi-step attacks is lateral movement.
Why is Lateral Movement Overlooked?
Understanding lateral movement is essential because it describes the actions that attackers take to expand their foothold on the target network, which is often essential to the success of an attack, as the first compromised host is rarely the final target of a breach. Lateral movement is also often overlooked because most security tools focus on the perimeter of the network, and they seldom look at the interactions among internal hosts, and, as a result, these tools might miss important aspects of a multi-step attack.
If we look at the techniques listed by the MITRE framework in association with the tactical goal of lateral movement, we see mentioned the use and exploitation of remote services, internal spearphishing, lateral tool transfer, session hijacking, the use of removable media and shared content, and software deployment tools, among others. In practice, most of the lateral movement techniques involve the use of RATs (e.g., the notorious Cobalt Strike) or the use of existing services, such as the Remote Desktop Protocol (RDP) or PsExec.
In this report, we present some data about lateral movement that is based on the telemetry that was collected from NSX customers. However, a caveat is necessary: while the attacks and statistics described here are based on real-world data, they are also partial and do not represent every possible scenario for every possible network. Nonetheless, there are interesting insights that can be gained to support a better security posture for complex networks and a higher chance to detect and block an intrusion before it becomes a full breach.
Understanding Intrusions and Lateral Movement
Our analysis begins from the concept of an intrusion, which in VMware’s NSX Advance Threat Protection solution is a set of alerts generated on a victim’s network that are correlated together. We selected a VMware Contexa dataset that spans 30 days, starting from April 1st, 2022, and whose intrusions involve at least five hosts.
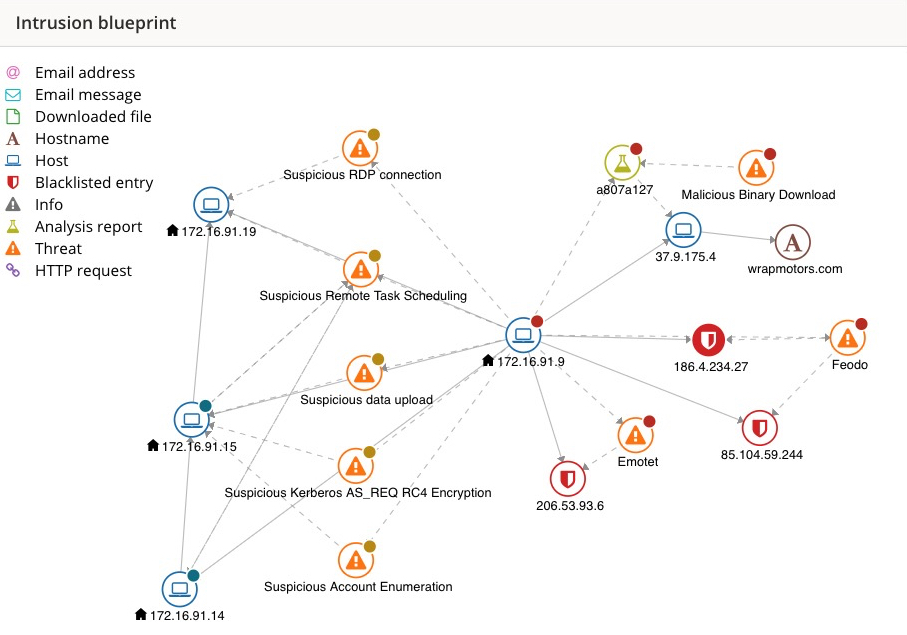
Figure 1 shows an example of one of the intrusions included in this dataset.
Figure 1: An example of an intrusion as shown in the NSX Advance Threat Protection console (local IP addresses have been anonymized).
The dataset contains 489 intrusions 219 (44.7%) of which contain a lateral movement event.
The Shape of Lateral Movements
We first look at the shape of the lateral movement activity. We want to understand what the size of intrusion blueprints is in terms of the number of hosts, for intrusions that contain lateral movement events.
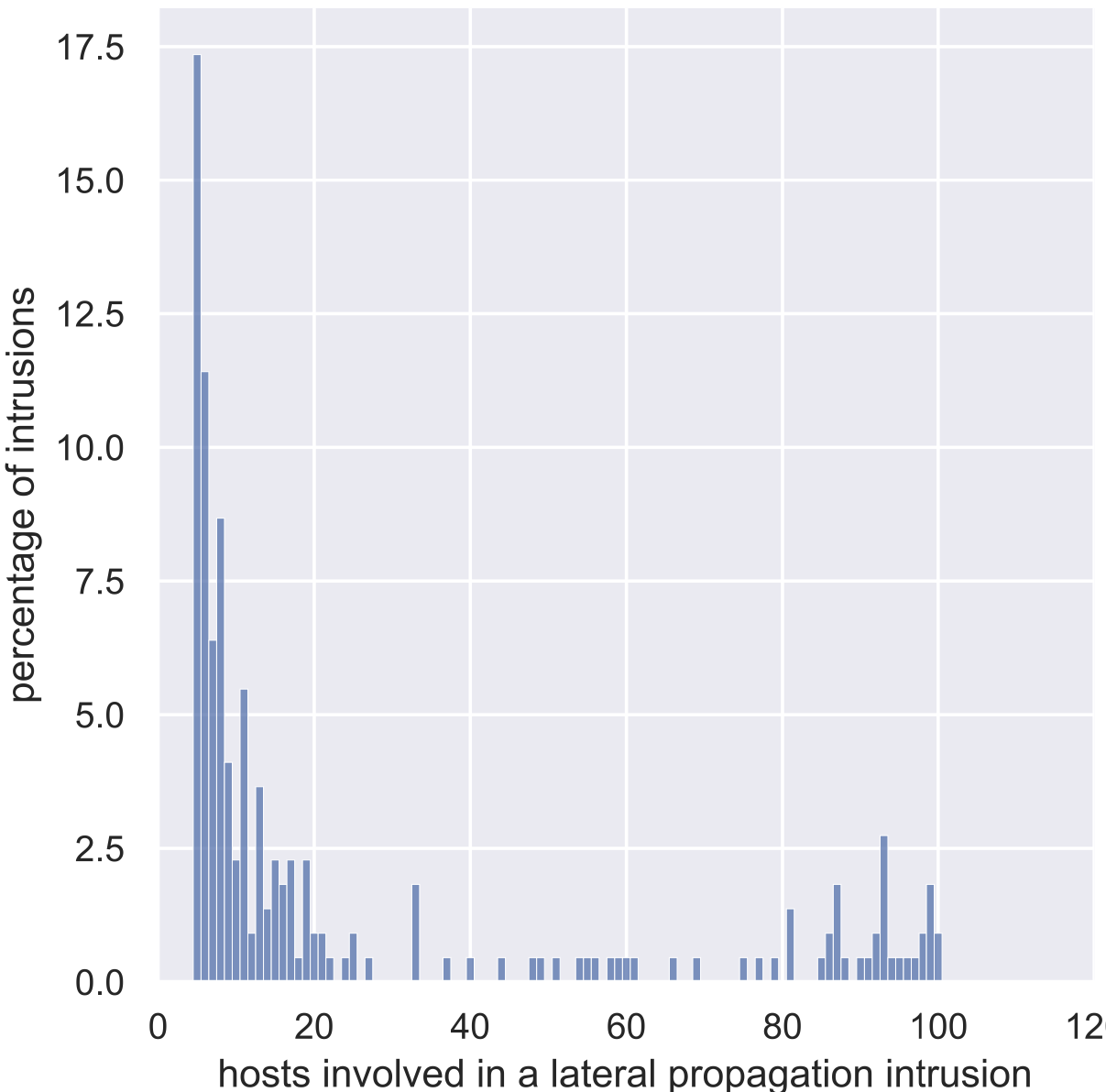
Figure 2: Distribution of the number of hosts across intrusions that contain a lateral movement event.
Figure 2 shows the distribution of the number of hosts for intrusions that contain some form of lateral movement. One can easily see that most of these intrusions involve a limited number of hosts (the most common number of hosts is less than 20).
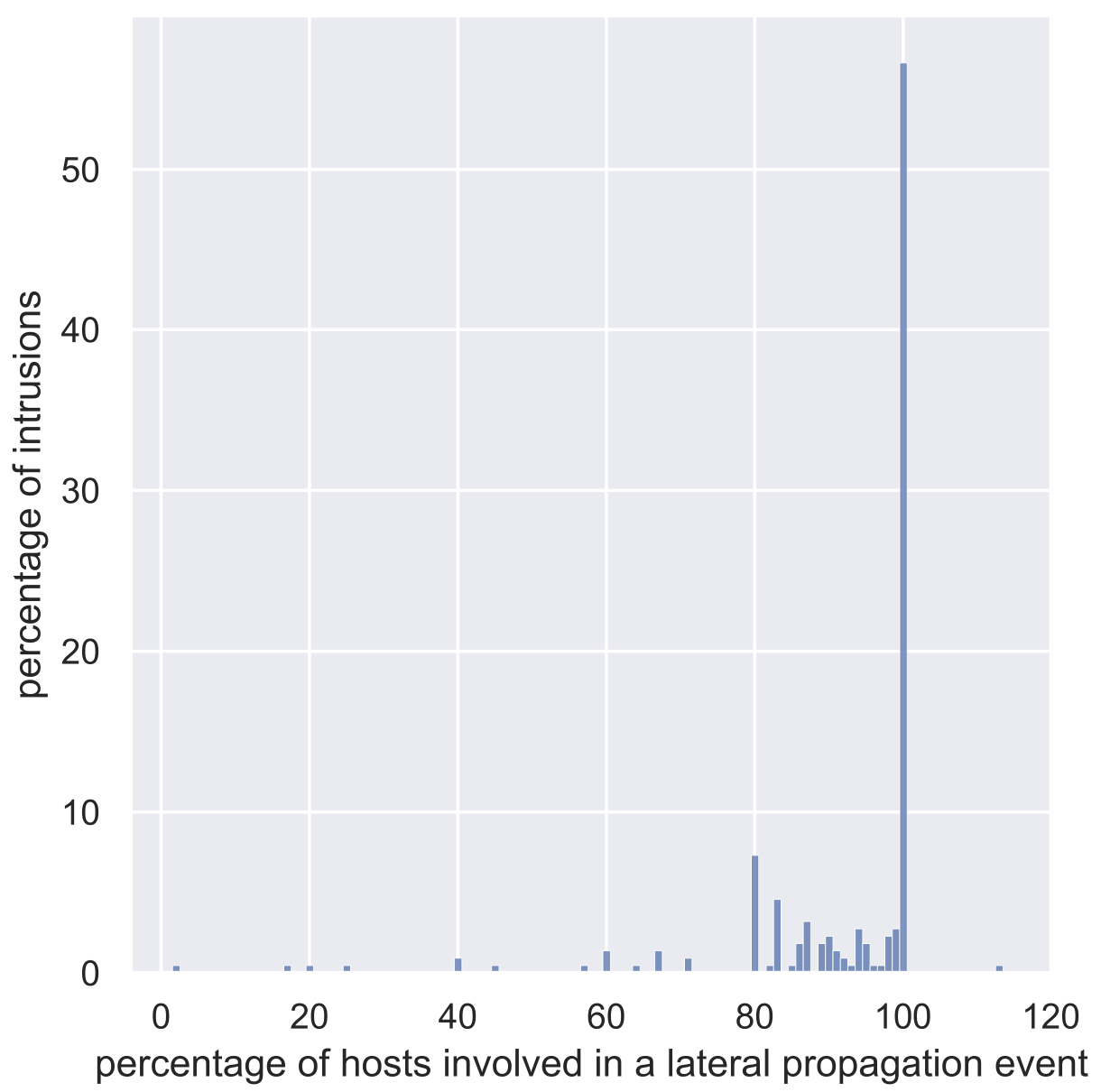
As a second step, we want to understand how many hosts are involved in lateral movement activity, that is, how many hosts in an intrusion are the source or destination of a lateral movement event. In Figure 3, we show the absolute numbers (a) and the percentage with respect to the total number of hosts (b).
(a)
(b)
Figure 3: Number of hosts involved in lateral movement events: (a) shows the distribution in terms of the absolute number of hosts, and (b) shows the distribution of the hosts involved in lateral movement as a percentage of the total number of hosts.
From the data, one can see that when lateral movement is involved this activity usually includes most of the hosts that are part of the intrusion.
We then look at the actual shape of the lateral movement graph, which is the subset of an intrusion blueprint that contains only the hosts involved in lateral movement.
In this case, we want to analyze the path length and the fan-out. The goal of this analysis is to understand if attackers usually use one node to attack many others or if they move linearly from host to host in an island-hopping pattern. Figure 4 (a) shows the characterization of the length of the path. From the graph, one can see that in our dataset the most common average path length is 2, and the maximum is 4, meaning that excluding larger intrusions (where often brute-forcing is involved) island hopping is quite limited in terms of the number of involved nodes, meaning that attackers are often able to close in on the final target swiftly. Figure 4 (b) shows the distribution of the absolute number of distinct lateral paths, which highlights that most intrusions have less than 20 distinct paths in the graph.
(a)
(b)
Figure 4: Length of a lateral propagation path: (1) shows the average path length, and (b) shows the distribution of all lateral propagation paths even if more than one per intrusion.
Another way to characterize the shape of the lateral movement graph is to look at the fan-out of the nodes involved. Figure 5 (a) shows that the average number of target nodes for a lateral propagation event is 1, meaning that lateral propagation attempts tend to be laser-focused, i.e., affecting only those hosts that are needed by the intrusion to succeed. When looking instead at the maximum number of targeted nodes (see Figure 5 (b)), we can see again that while most intrusions have a limited maximum fan-out, in a few cases lateral propagation efforts rely on brute-forcing their way to the target, as the number of target nodes can spike up to more than 90 nodes.
(a)
(b)
Figure 5: Fan out of a host in a lateral propagation event: (a) shows the average host fan out, and (b) shows the distribution of the maximum fan-out across all analyzed intrusions.
5 Techniques Used by Attackers
While the lateral movement shape analysis supports our understanding of the form of lateral movement, hereinafter we look at the type of techniques used for lateral movement.
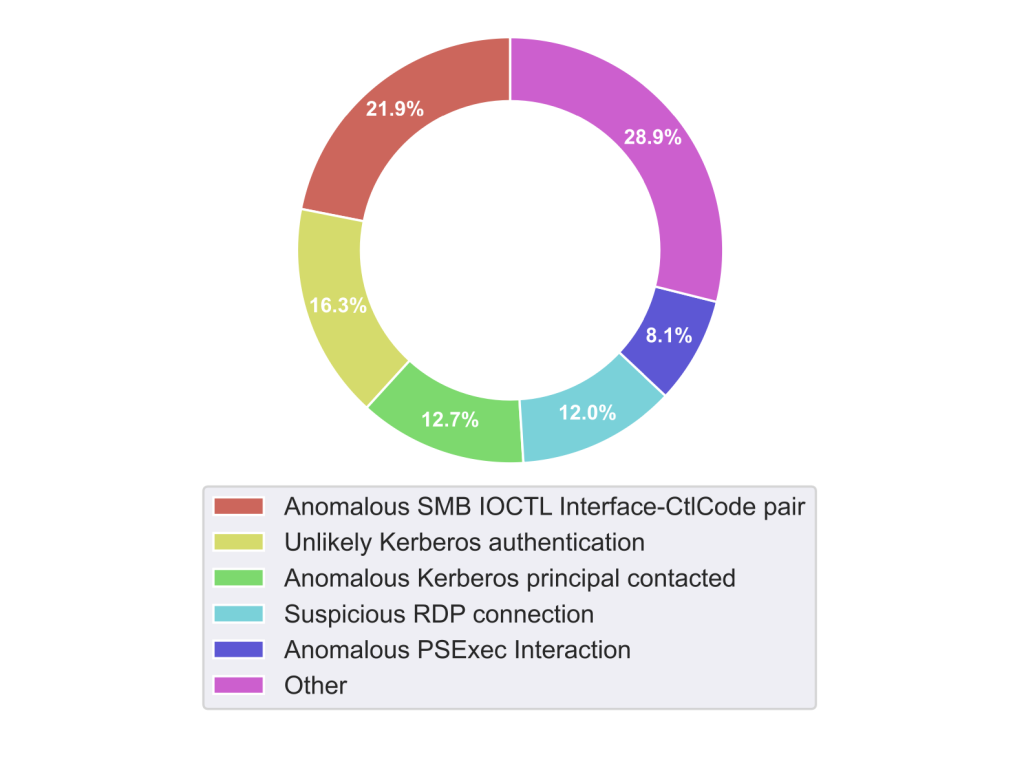
Figure 6 shows the techniques that we observed being used for lateral movement in our dataset: the use of the Samba service and the Remote Desktop Protocol are the most common techniques, followed by anomalous use of Kerberos and the use of the PsExec tool; anomalous SMB/IOCTL pairs are detected when accessing anomalous types of resources (for example named pipes that are not usually opened), while Kerberos anomalies are the main ingredient of all privilege escalation techniques that rely on the domain controller granting the additional permissions.
Figure 6: Most common observed network behaviors associated with lateral movement.
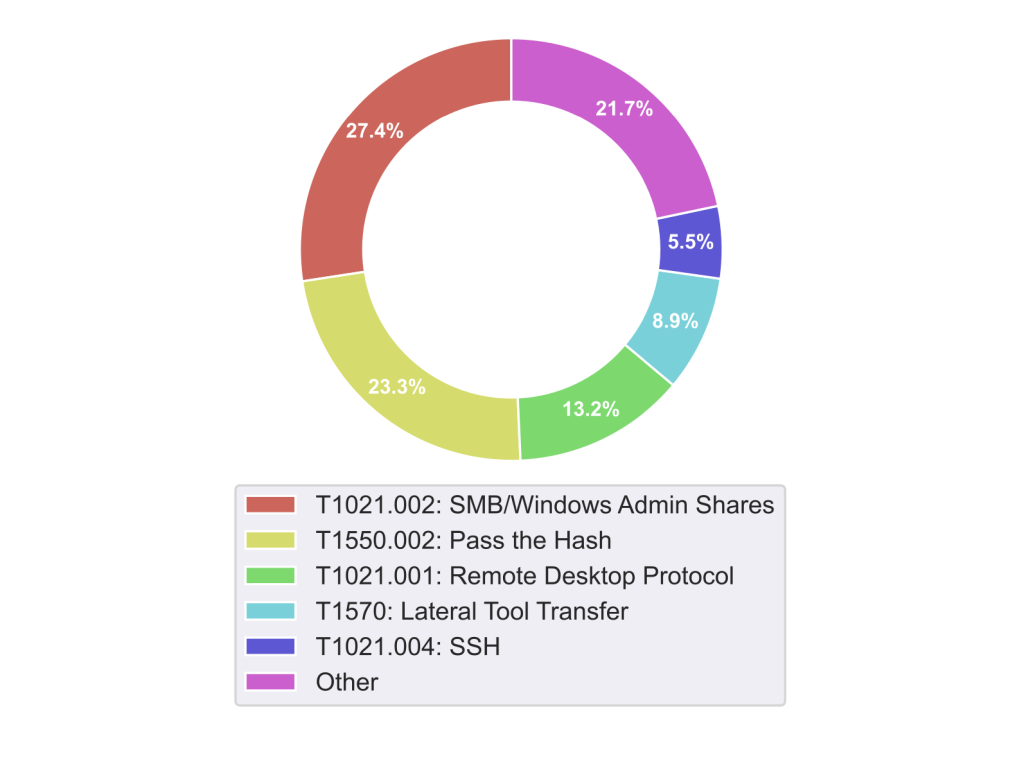
We have also looked at the MITRE techniques associated with the events observed during lateral movement. Figure 7 shows that Samba, once again, is a common technique to spread from host to host, and so is the “Pass the Hash” technique.
Figure 7: MITRE Techniques associated with lateral movement.
The Samba/Windows Admin Shares technique uses the Samba service to mount remote filesystems and perform lateral movement by transferring executables to remote hosts and invoking their execution (among other abuses of the SMB/RPC protocol).
The Pass the Hash technique is not listed by the MITRE ATT&CK Framework under “lateral movement” and is instead considered a “Defense Evasion” technique. However, it is categorized, this technique is often used to gain access to additional hosts by using authentication credentials collected on compromised hosts, effectively achieving lateral movement.
The Remote Desktop Protocol and SSH connections are probably two of the easiest techniques to perform lateral movement, as they entail using existing legitimate remote session protocols (RDP and SSH, respectively) with stolen credentials. These intrusion events are particularly difficult to identify as they easily get lost among the events associated with legitimate administrative activity.
Finally, Lateral Tool Transfer is a technique that is associated with lateral movement and is not necessarily the means to achieve additional access. In this case, the event describes the transfer of tools used by the attacker to recreate on the compromised host an environment that can be leveraged for further exploitation. This is a key aspect of lateral movement, as the compromise of a host is just the starting point for additional probing and access, which require scanning and exploitation tools.
Interestingly, the techniques described above are those often provided by RATs and other post-exploitation frameworks, such as Cobalt Strike’s Beacon and Metasploit’s Meterpreter.
To further understand the link between network behaviors and MITRE techniques, Figure 8 shows the underlying correlation for each lateral propagation event; the analysis shows that the network behaviors captured by an NDR system are in some cases capable of further differentiating how a MITRE technique is actually exercised; for example, T1550.002, the technique that relies on “Pass The Hash” to escalate privileges, is here detected by two different behaviors detailing two orthogonal events: “Unlikely Kerberos Authentication” triggered when two hosts have a Kerberos interaction for the first time, and “Anomalous Kerberos principal contacted”, which is triggered when a specific Kerberos service is contacted for the first time.
Figure 8: How network behaviors are correlated to MITRE techniques.
Conclusions
Understanding lateral movement is important, as it is a key activity in complex, multi-step attacks.
Unfortunately, identifying lateral movement events in computer networks that generate thousands of events every day is challenging, especially because many of the events might be associated with legitimate administrative activity (e.g., the use of SSH or RDP to connect to a host).
Therefore, it is of paramount importance to have sophisticated analysis tools that can enrich and amplify the relevant signals so that they can stand out from the noise.
For example, identifying RDP connections between hosts that have never had a session in the past might be a way to identify unusual and anomalous events. As another example, a series of events that represent a host contacting many other hosts (i.e., a communication pattern with an elevated fan-out) might indicate a brute-forcing attempt.
These examples, outline the need for sophisticated Network Analysis Tools (NAT) feeding into a Network Detection and Response (NDR) system that uses machine learning and statistical analysis to discriminate between normal traffic and malicious behavior.
VMware NSX has a key advantage in detecting lateral movement, as the virtualization of network connectivity, combined with sophisticated policies and micro-segmentation, supports the identification of both known patterns of attack and anomalous behavior.