This year at VMworld 2021, we are excited to bring to you many innovations around security that surely will get you rethinking your strategy.
For the longest time, organizations have had little choice but to be behind the ball and respond to the possibility of a security issue by investing in multiple security tools, with the hope of building enough redundancy that they would be protected. The unintended consequences of this approach are fragmented security and poor employee experience — not to mention operational complexity and added costs.

VMware is in a unique position to leverage its industry-leading technologies to solve these challenges for organizations, and we intend to do just that. That’s why earlier this year we announced the VMware Anywhere Workspace solution, which brings together three of our best products in an integrated fashion – VMware Workspace ONE, VMware SASE and VMware Carbon Black Cloud.
VMware Anywhere Workspace builds on the Zero Trust security capabilities that are already intrinsic in our Workspace ONE Platform, first to expand it to add endpoint security capabilities from Carbon Black, and then to extend out to the network and cloud with our newest additions from VMware SASE.
At VMworld this year, we have some great announcements across several areas:
- Zero Trust User and Device Controls
- Endpoint Compliance and Protection
- Zero Trust Network Access
The core tenet of Zero Trust is continuous verification and enforcement, and we continue to add more capabilities there. We have had powerful risk-based conditional access capabilities in our Workspace ONE Platform for a few years now. These are great and help us to assess risk and accordingly adjust the access levels to users or devices. Now, we want to make this more continuous.
Continuous Access Control with Workspace ONE Tunnel
Today, we announced our new capabilities for continuous access control with Workspace ONE Tunnel. With this, we will be able to continuously evaluate activity even after users are initially authenticated. Tunnel will leverage signals from the Workspace ONE platform and then take enforcement actions, such as interrupting app sessions or requiring identity validation. You can read more in this blog.
Desired State Management powered by our new compliance engine
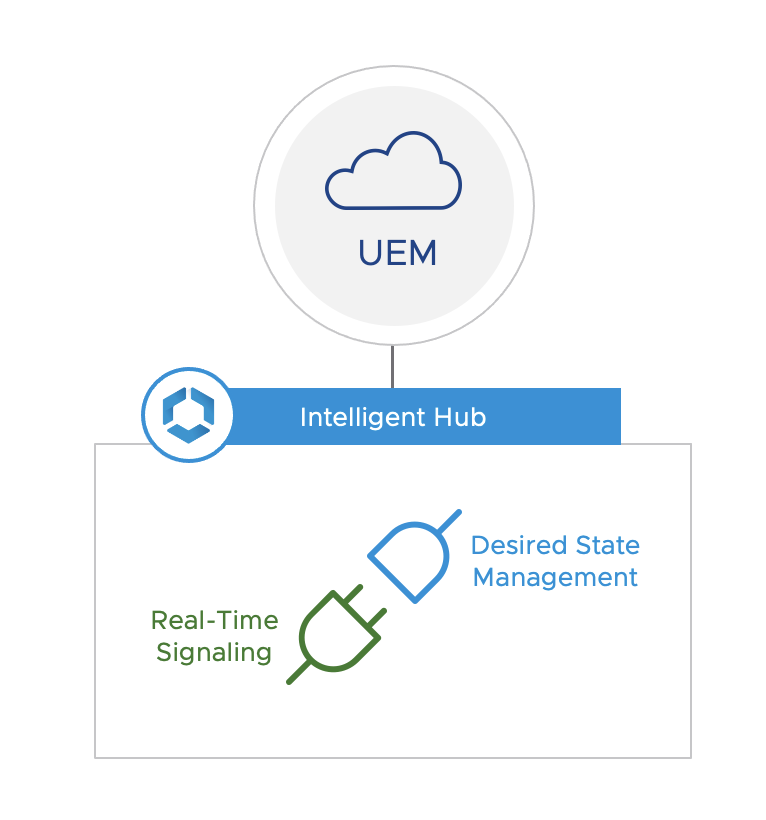
Today, we announced a new compliance engine built right into the heart of Workspace ONE. This will give us the ability to react to changes in device security posture in near real time, which is a critical aspect of Zero Trust.
With an upcoming version of Intelligent Hub for Windows 10, we will introduce the RTS (Real-time signaling) plugin to rapidly detect changes and react. This plugin will interact with the Desired State Module (DSM) to enable a consistent desired state to be maintained on the device. We like to think of this as “endpoint hygiene on autopilot,” enabling richer posture checks with more attributes, using real time data instead of fixed intervals and leveraging on-device capabilities to directly remediate any drift in state.
Chip-to-cloud PC Management and Security
We are excited to bring to market a unique partnership with Intel to protect against modern cyberattacks that can aim to exploit vulnerabilities below the OS layer. This partnership allows us to offer to customers certain unique capabilities, such as Remote Secure Erase for better end-of-life management, as well as out-of-band patching for seamlessly bringing the device back into compliance. Together, we will provide an integrated security solution that follows devices, apps, and data, no matter where they are. You can read more about our partnership in today’s blog.
Cross-Platform Vulnerability Management
We continue to build on our vulnerability management capabilities – something that’s even more important in a remote work environment. While we first built these capabilities to serve our Windows customers, we have since expanded them to support macOS and iOS as well. Support for Android will be coming soon. With our out-of-the-box dashboards, alerting and automation, we believe customers have a powerful solution to meet and exceed SLAs.
VMware Secure Access
As we continue to extend our Zero Trust capabilities beyond users and devices, the next logical level of protection is on the network. To address the network, most organizations have resorted to the traditional VPN as a blanket solution. While this gives the illusion of security, in reality it is exposing users to different vulnerabilities with equally worse potential outcomes, not to mention the added cost and complexity when a majority of the workforce depends on it to be productive.
To address these challenges, VMware introduced our ZTNA (Zero Trust Network Access) solution earlier this year, called VMware Secure Access.
Our solution enables a modern, cloud-native approach to remote access with continuous authentication methodologies that:
- Shrink the attack surface
- Enable consistent user experiences irrespective of where they are accessing enterprise data
- Improve application performance by avoiding routing cloud/SaaS traffic through legacy solutions
- Reduce additional management overhead and cost

In fact, in our first year of participation in The Forrester New Wave™: Zero Trust Network Access (ZTNA), Q3 2021 report, VMware has been recognized as a Leader.
Cloud Web Security
As organizations continue to move applications to the cloud and embrace SaaS apps, it’s increasingly important to protect access to these applications. With that in mind, we announced the general availability of our Cloud Web Security capabilities earlier this year. This provides threat protection, visibility, and control so employees can access applications with fewer worries about policy violations. It includes an SSL Proxy with decryption for traffic inspection, and IT can control website access with URL filtering. IT can also build policies around what users can upload and content can be inspected for virus signatures and zero-day malware threats.

This week at VMworld, we announced new inline cloud access security broker (CASB) and data loss prevention (DLP) enhancements, hosted in our PoPs. Both capabilities will add an additional layer of protection by allowing admins to restrict access to sites that they deem risky to the business. With our data loss prevention capabilities, organizations will have a greater ability to prevent enterprise data from being accidentally or intentionally stolen or directed to personal storage accounts. Our CASB and DLP will both be generally available soon.
Recommended sessions at VMworld 2021
- VI3130 – Anywhere Workspace Solution Keynote: The Future of Hybrid Work Made Possible Today
- SEC2715 – VMware on VMware: Zero Trust Security Story
- SEC2733 – A Practical Approach for End-to-End Zero Trust
- EUS2470 – EUC Solution Keynote Part 1: Vision and Announcements
- EUS2467 – EUC Solution Keynote Part 2: Technical Deep Dives on SASE and Horizon
- SEC1287 – Mount a Robust Defense in Depth Strategy against Ransomware







