The content for this blog is created by Trevor Gerdes (@trevorgerdes). Posting it here with minor changes.
VMware vCloud Networking and Security Edge Gateway is part of the vCloud Networking and Security solution and provides network edge security and gateway services such as DHCP, VPN, NAT, Firewall, Load Balancing, IPSEC VPN and SSL VPN. In this blog, we will look at the details in configuring the SSL VPN function to allow remote users connect securely to private networks behind an Edge Gateway.
Edge Gateway supports 25 simultaneous connections from SSL VPN clients on the Compact version and 100 simultaneous connections from SSL VPN clients on the Large version. The X-Large appliance does not support SSL VPN.
You first need to deploy an Edge Gateway within the vCloud Networking and Security Manager (Refer an earlier blog for instructions).  Once you have the Edge Gateway deployed and operational, you will need to click on the VPN tab within the configuration panel.
Once you have the Edge Gateway deployed and operational, you will need to click on the VPN tab within the configuration panel.
 Then click on the SSL VPN-Plus menu item.
Then click on the SSL VPN-Plus menu item.
 From this dashboard you can see the operational state of the SSL VPN subsystem. Enable SSL VPN service in Edge Gateway when disabled.
From this dashboard you can see the operational state of the SSL VPN subsystem. Enable SSL VPN service in Edge Gateway when disabled.
Configuration Preparation
To configure the SSL VPN function we will need a number of different parameters and options to be prepared.
- Edge External IP Address: The outside IP address of the Edge Gateway.
- Edge External TCP Port: The default is 443, but this can be changed to any TCP port to suit business requirements.
- Encryption Cipher: The default is AES256-SHA, multiple ciphers preferential ordering can be used.
- SSL Digital Certificate: An SSL certificate can be specified or the default self signed certificate can be used.
- VPN IP Network: You add this as an IP Pool in SSL VPN configuration. The remote user is assigned a virtual IP address from this pool.
- VPN IP Network Gateway: The IP address that acts as an Edge Gateway virtual interface between the VPN IP Network and the corporate IP Networks.
- Corporate IP Networks: List of networks behind Edge Gateway that you want the remote user to be able to access.
- Authentication System: The SSL VPN function supports authenticating with RADIUS, Active Directory, LDAP, RSA-ACE or Local sources. Multiples sources can be selected.
 Let’s configure the Edge SSL VPN function using the above parameters.
Let’s configure the Edge SSL VPN function using the above parameters.
Server Settings
The first configuration item is the IP address and port number for SSL VPN traffic to the Edge Gateway. The IP address possibly is different from the default external address, if you have multiple overlay IP address networks on the external interface. The TCP port number by default is 443 (that is used by default for HTTPS/SSL traffic). It is feasible to use any TCP port number for communications and for a proof point I have configured this scenario to use TCP 8443. 
The second configuration item is to choose which encryption algorithms to use. You can choose one or multiple to support, bear in mind the security risks involved with each algorithm. The choices are AES256-SHA, AES128-SHA, DES-CBC3-SHA and RC4-MD5.
 The third item is your identity certificate. There are a variety of ways to utilise certificates within the Edge Gateway. You can choose to use the default self signed certificate that is generated for each individual Edge Gateway, or to use a previously imported externally generated digital certificate for an individual Edge or one that has been imported into the vShield Manager. See the section Working with Certificates on page 67 of the vShield Admin Guide http://www.vmware.com/pdf/vshield_51_admin.pdf
The third item is your identity certificate. There are a variety of ways to utilise certificates within the Edge Gateway. You can choose to use the default self signed certificate that is generated for each individual Edge Gateway, or to use a previously imported externally generated digital certificate for an individual Edge or one that has been imported into the vShield Manager. See the section Working with Certificates on page 67 of the vShield Admin Guide http://www.vmware.com/pdf/vshield_51_admin.pdf
IP Pool
Next we need to create a pool of IP addresses that are distributed to the connecting VPN clients. This is a new virtual IP address subnet configured on the Edge Gateway. This address range must be different from all other networks configured on the Edge. The IP Pool also contains gateway, DNS server and DNS suffix details.
 The Gateway address configured here can be any address, within the subnet range, that is not utilised by the IP Pool. This address is given to virtual interface within the Edge Gateway on creation of the IP Pool.
The Gateway address configured here can be any address, within the subnet range, that is not utilised by the IP Pool. This address is given to virtual interface within the Edge Gateway on creation of the IP Pool.
Multiple IP address pools can be created and used. At this point in time the Edge Gateway only supports 25 simultaneous client VPN tunnels in Compact version and 100 simultaneous client VPN tunnels in Large version. So keep this in mind when deciding how large to make the pool.
If multiple address pools are used with different gateway addresses for each pool. Each gateway address is assigned to the same interface within the Edge Gateway.
The private networks is a list of all reachable IP networks behind Edge Gateway that you wish to encrypt traffic for, or exclude from encrypting, from a VPN client. Each network you wish to tunnel traffic for will require a separate entry. You can use a route summarisation strategy to limit the number of entries.
For each private network you can specify whether you want to enable TCP optimization, this is a unique method of enhancing the performance of TCP packets within the VPN tunnel by removing the original TCP header and only shipping the data. This does not improve performance of UDP traffic.
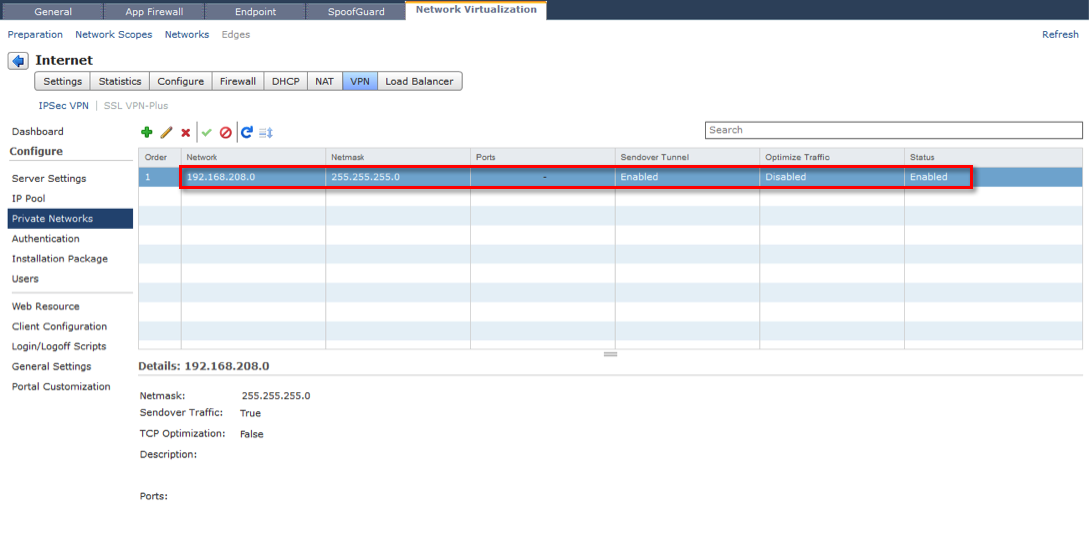
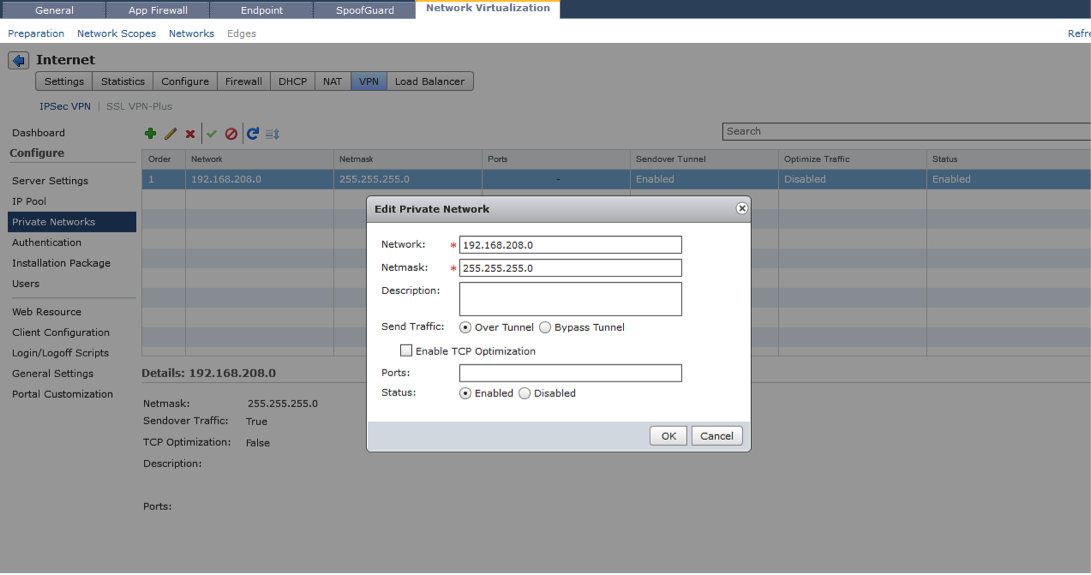 Type the port numbers that you want to open for the remote user to access the internal servers like 3389 for RDP, 20/21 for FTP, and 80 for http. If you want to give unrestricted access to the user, you can leave the Ports field blank.
Type the port numbers that you want to open for the remote user to access the internal servers like 3389 for RDP, 20/21 for FTP, and 80 for http. If you want to give unrestricted access to the user, you can leave the Ports field blank.
Authentication
We need to configure an appropriate mechanism to authenticate users for VPN access. The Edge Gateway supports a number of industry standards for external authentication of users, as well a local username database. The choice of which authentication system to use is generally be decided by your corporate IT security policy. The choices for external authentication are RADIUS, LDAP, Active Directory and RSA-ACE. Each authentication option has its own individual configuration parameters. 
Multiple authentication systems can be configured and a hierarchical ordering system can be instituted to cycle automatically through the list.
Remember that there may be specific attributes that need to be configured on the authentication servers to allow user or group access.
Installation Package
In this section we can specify the behaviour of the VPN Client after installation. We also select what VPN client package we want to build for the OS’s we want to support.
 Multiple client packages can be produced, each with different parameters. Each client package produced is directly accessible for download from the Edge Gateway VPN portal.
Multiple client packages can be produced, each with different parameters. Each client package produced is directly accessible for download from the Edge Gateway VPN portal.
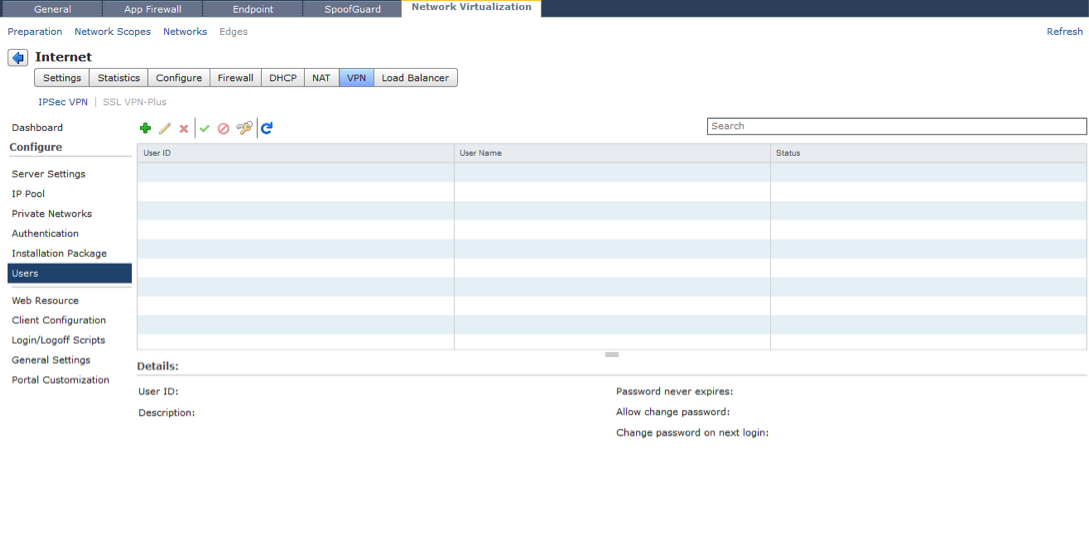
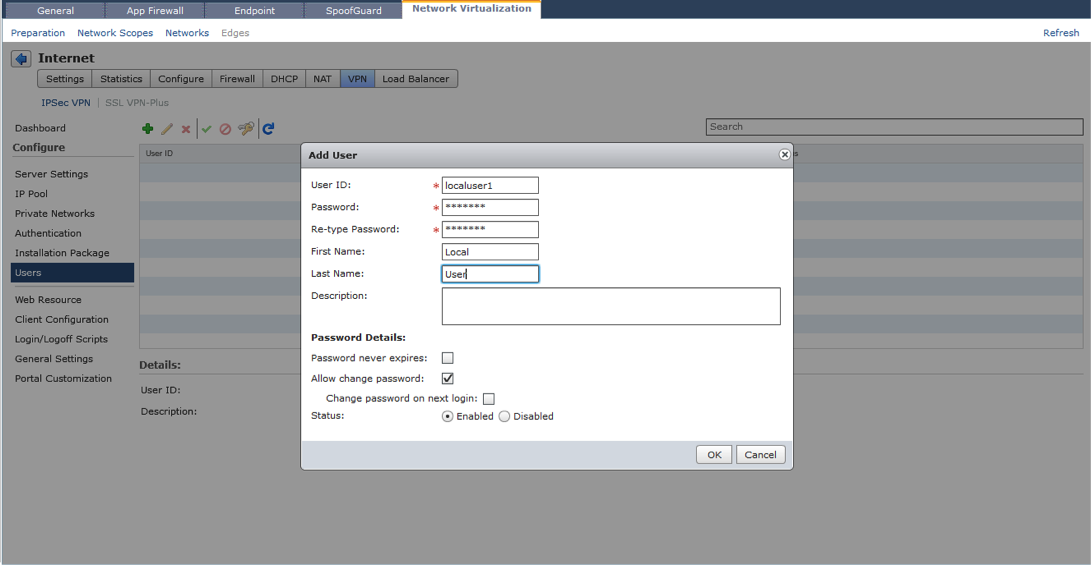
This section is where you can configure local users for authentication. By putting a user in this section, it automatically configures a local user authentication mechanism in the Authentication menu.
The Web Resource function is to provide a secure portal to access web content behind the Edge Firewall. When you open a web connection from the Internet on the port defined in the server settings (i.e. 8443 in our example), you are prompted with a sign-on page to the access portal. It is through this access portal that you first download the SSL-VPN client, but this page can also be used to access other resources defined below.
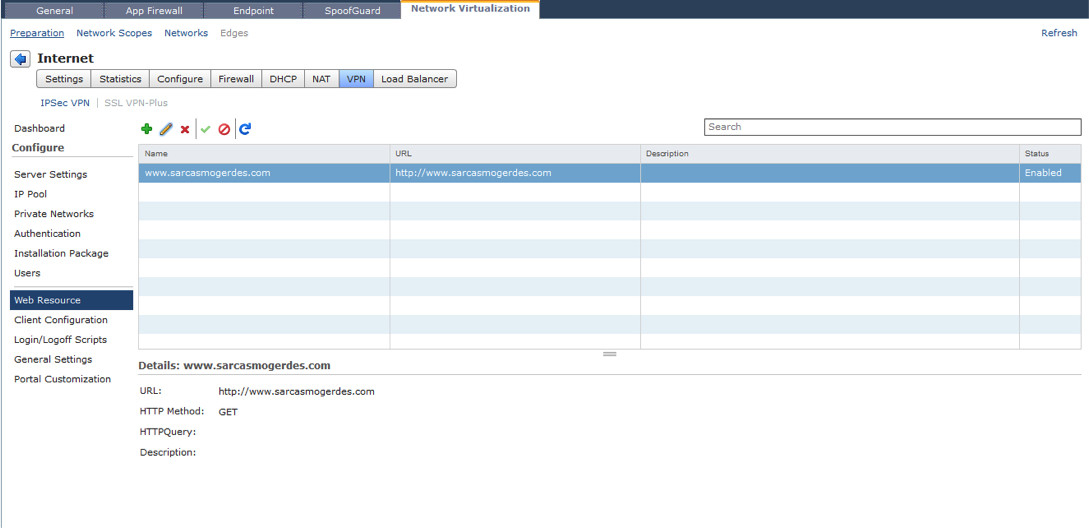
Use the + button to add a URL that will be presented after login to the portal. This feature could be used to interact with selected corporate web resources. One note though is the HTTPMethod, depending on whether the remote user wants to read from or write to the web resource select either a GET or PUT method for each resource created.
In general you will leave the HTTPQuery section blank, unless you want to send a specific HTTP request to a web resource.
The final result is a login page that lists available resources like this.
The Client Configuration section is where we specify operating attributes for the SSL VPN client. The three options that can be configured are, Tunneling mode, Auto reconnect and Upgrade client notification.
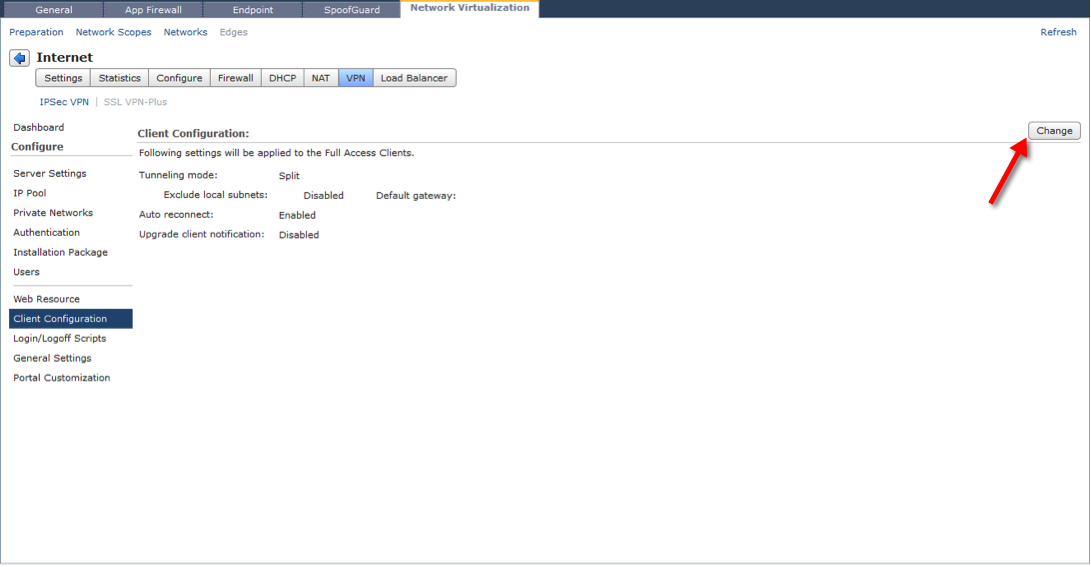 Tunneling mode – Split tunnel versus Full Tunnel. A full tunnel sends all traffic to the SSL gateway including all Internet traffic. Split tunnel, only sends traffic to networks defined in the Private Networks configuration section. When you select full tunnel you can also choose to exclude locally attached subnets, i.e. home networks, this allows for a “tunnel everything” except my home network scenario, to allow access to things like home printers etc.
Tunneling mode – Split tunnel versus Full Tunnel. A full tunnel sends all traffic to the SSL gateway including all Internet traffic. Split tunnel, only sends traffic to networks defined in the Private Networks configuration section. When you select full tunnel you can also choose to exclude locally attached subnets, i.e. home networks, this allows for a “tunnel everything” except my home network scenario, to allow access to things like home printers etc.
Auto reconnect – This changes the operating behaviour of the VPN client should the tunnel be disconnected during a session, i.e. mobile data/ DSL connection dropped, Edge transitioning through a HA scenario etc. Auto reconnect will continue to poll the Edge Gateway and automatically re-establish a connection for you.
Upgrade client notification – When a new version of the SSL VPN client is available, or the system policy for the VPN client configuration is changed, it will prompt you to upgrade the VPN client.
Login/Logoff Scripts
We provide a facility to execute login/logoff scripts that could be used to perform system administration or client usability functions at the time of connection, i.e. start email client, initiate a Horizon View session, or reconnect network drive mappings etc. once VPN is established.
The General Settings let you configure a range of global values for the SSL VPN system.
 Prevent multiple logon using same username: When enabled allows a remote user to login only once with a username.
Prevent multiple logon using same username: When enabled allows a remote user to login only once with a username.
Enable compression: Enable TCP based intelligent data compression and improve data transfer speed.
Enable logging: Maintain a log of the traffic passing through the SSL VPN gateway.
Force virtual keyboard: Allows remote users to enter web or client login information only via the virtual keyboard.
Randomize keys of virtual keyboard: Make the virtual keyboard keys random.
Enable forced timeout: Disconnect the remote user after the specified timeout period is over. Type the timeout period in minutes.
Session idle timeout: If there is no activity on the user session for the specified period, end the user session after that period is over.
User notification: Type a message to be displayed to the remote user after he logs in.
Enable public URL access: Allow remote user to access any site, which is not configured (and not listed on web portal) by administrator.
Portal Customization
You can configure the colors, logo and titles for the login portal to reflect your corporate presence.
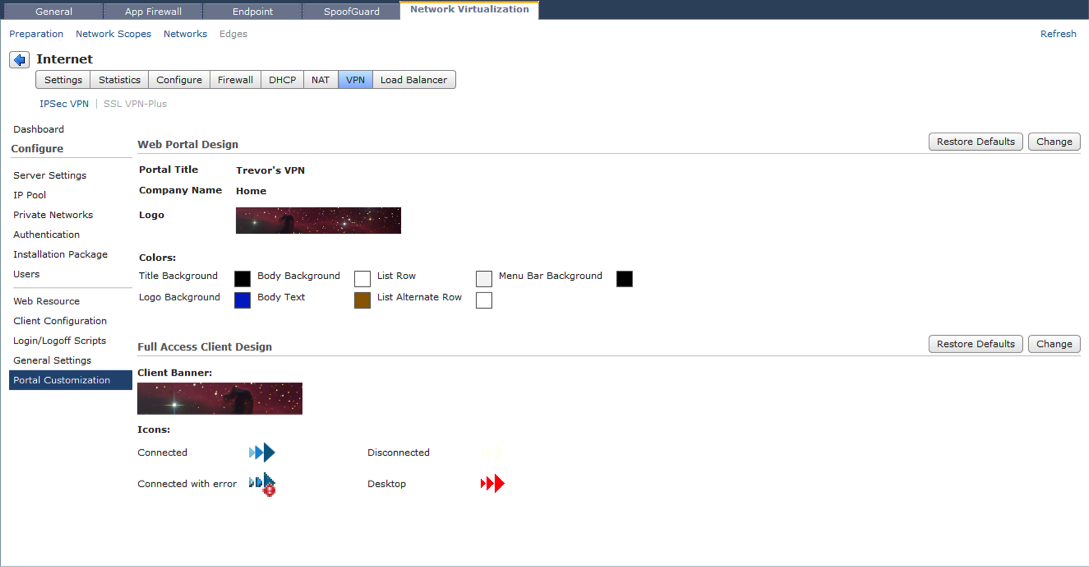 For the logo you are best served with an image that is a multiple of 70 x 10 pixels i.e. 7 times wider than it is long. We will scale the image pixels to suit the portal, but incorrect initial ratio will result in distorted appearance.
For the logo you are best served with an image that is a multiple of 70 x 10 pixels i.e. 7 times wider than it is long. We will scale the image pixels to suit the portal, but incorrect initial ratio will result in distorted appearance.
 Likewise, we can also change the appearance of the logo in the VPN client. The recommended image size is 390 x 75 pixels. We will scale the image to suit the space, but an incorrect ratio will result in image distortion. This is the last step of the SSL VPN configuration.
Likewise, we can also change the appearance of the logo in the VPN client. The recommended image size is 390 x 75 pixels. We will scale the image to suit the space, but an incorrect ratio will result in image distortion. This is the last step of the SSL VPN configuration.  You can now use the browser to connect to the Edge Gateway SSL VPN service using the IP address and port number configured in Server Settings e.g. https://10.1.1.2:8443. Once authenticated, you can access the web resources configured and download the SSL VPN client installation package.
You can now use the browser to connect to the Edge Gateway SSL VPN service using the IP address and port number configured in Server Settings e.g. https://10.1.1.2:8443. Once authenticated, you can access the web resources configured and download the SSL VPN client installation package.
Get notification of these blogs and more vCloud Networking and Security information by following me on Twitter @vCloudNetSec.