This article, Incorporating VMware Zero-Trust for the Presidential Executive Order, was originally published at the VMware Digital Workspace Tech Zone Blog.
By Andrew Osborn.
Across the Industry, Zero Trust security (ZT) has gained wide acceptance as the next generation model for securely delivering IT services and solutions anywhere in the world, on any device or system. Zero Trust is not a single product, but a modern security framework based on the notion of never trust, always verify. The journey to a full Zero Trust Architecture (ZTA) implementation requires careful planning across people, processes and technologies. No matter where a Public Sector entity is in the journey to secure users, applications, endpoints and the data; VMware has the extensive experience as a leader in cybersecurity and recently identified as such in the 3Q21 Forrester Wave Report for ZTNA, with the tools and technology to work with those agencies/organizations, as well as with your partner(s) of choice to complete the journey in the deployment of NextGen Identity Management (IdM), Network Security and Data Protection, while providing continuous monitoring and access visibility.
Cybersecurity Mandates
Several key aspects of the cybersecurity framework have come to the foreground in the last several years. For example, the NIST Special Publication 800-207 on Zero-Trust, as well as agency and branch-specific endeavors. In April of 2021, the White House released an Industrial Control Systems Cybersecurity Initiative to improve critical infrastructure cybersecurity. In July of the same year, the White House published a National Security Memorandum that tasks several federal agencies with developing cybersecurity performance standards for critical infrastructure. However, the bottom line of these executive orders, memorandums and policies can be summarized into two key directives for all Federal entities:

In parallel with the public sector’s evolution into a SaaS-first focus, VMware continues to deliver trusted, secure capabilities to thousands of customers. These customers depend on our solutions for critical workloads, devices and infrastructure.
Go Beyond Zero Trust with VMware
The past year has seen a constant onslaught of cyberattacks, ranging from supply chain compromise to extortion and ransomware. These attacks have disrupted critical infrastructure and impacted economic and political stability. In response, VMware initiated a companywide Beyond Zero Trust program.
Beyond Zero Trust was created as a collaborative endeavor between the office of our CIO, VMware Engineering Services and the Security & Risk department. This initiative drives specific actions that ensure we are prepared against security threats and that we continue earning and keeping our customers’ trust.
Beyond Zero Trust is a series of transformative efforts aimed at protecting VMware by better detecting and limiting impact from insider threats. These efforts range from the implementation of new policies and security protocols to a more robust authentication framework and each of them require a huge focus on security programs, policies, teams and culture, to support the initiative’s primary goals:
Quality Software
Enable teams to produce products and services that serve our customers in terms of reliability, integrity and usability.
- Performing ongoing analysis of our development environments identifying improvements, clarifying ownership, and taking remediation steps.
- Standardizing our build environments with stricter access controls and deploying mechanisms to allow for a full understanding of the provenance of a build.
Colleague Security
Continually secure our environment and platforms while replacing legacy environments as we accelerate our SaaS transformation.
- Driving identity-based segmentation, moving credentials to a leased password model and making secure, encrypted multifactor authentication (MFA).
- Consolidating wireless, remote and cloud access avenues for accessing the VMware network, internal systems and all applications/services by enforcing MFA.
- Requiring a baseline of controls on all endpoints accessing any VMware data or resources including encryption, endpoint services and additional management controls.
Detect & Defend
Expand our security services to be able to better detect or defend against malicious activity.
- Deploying additional, robust threat protection and threat hunting solutions on all our systems, including a critical focus on our development environments.
- Expanding our vulnerability management program to further defend against threats arising in our cloud, development and short-term environments.
Furthermore, as an industry leader in innovation, VMware has earned the trust of our customers by delivering powerful and effective solutions. Beyond Zero Trust marks a great step into a safer future for our company, its products, and services, as well as our colleagues and trusted customers. This, however, will require great commitment from all of us. We now seek your help to become the benchmark for excellent security.
For more information on VMware’s Zero Trust story, visit our security solution resources portal and the public sector page on VMware TechZone.
VMware Aligns with Zero Trust Guidance
The journey began over 20 years ago with our long-standing commitment to intrinsic security and engineering compliance directly into server platforms and has been greatly enhanced to include solutions to secure the network, storage and end-point devices, whether they be PC or Mac, Android or iOS. VMware’s implementation of Zero Trust protects your data and applications not only at the start of a session, but also with continuous verification of users and endpoints throughout an application session, from the endpoint to the data centers and clouds.
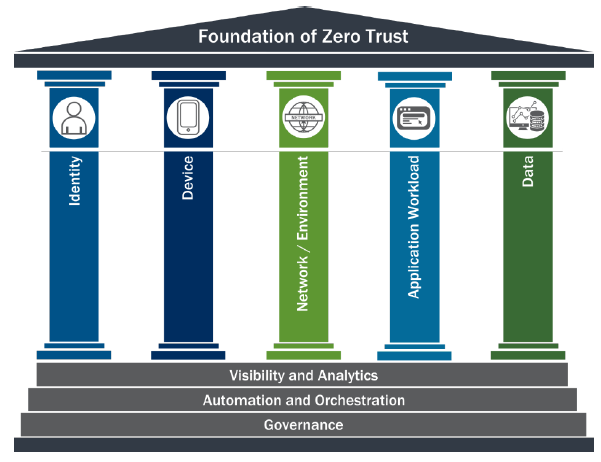
VMware’s blueprint for the journey to Zero Trust consists of the following pillars:

This approach allows agencies the flexibility to implement the solution in a phased approach and to decide what pillar(s) are most important to the agency and its stakeholders and ties directly back to our efforts within the End-User Computing (EUC) and Anywhere Workspace: and within this realm, provide foundations of Secure Access Service Edge (SASE) model as well.
However, we understand that the government’s journey to Zero Trust may be a non-linear one that is customized for individual teams within the organization. VMware can enable any model of Zero Trust that you adopt with our industry recognized VMware Validated Designs, a prescriptive blueprint that describes the technology solutions and best practices for rapidly and securely implementing and integrating into your environment; including helping force general improvements to cybersecurity nationwide, but issues its most authoritative directions to the Federal government to modernize IT infrastructure and security concepts and practices.
To that end, the government model continues to evolve at a rapid pace, such as in the case CISA recently released two separate cyber and zero-trust related ‘Cloud Security Technical Reference Architecture‘ (TRA) and ZT Maturity Model, along with a White House Office of Management & Budget (OMB) draft ‘Federal Zero Trust Strategy’; all are intended to clarify key zero-trust priorities for civilian agencies as they roll out the cybersecurity architecture over the next few years.
Some of those key aspects and goals for the models and the TRA are for consolidating agency identity systems, combatting phishing through strong multifactor authentication and treating internal networks as untrusted. It also lays out the requirements for encrypting Data-in-Transit (DiT) and strengthening application security through areas such as Application Security Testing and app-wrapping. Lastly, ensuring logging requirements that are pursuant to Section 8 of the EO, as well as asset / data identification and labeling are a must for any ZT implementation to work.
Furthermore, the hope is that these drafts (with their accompanied final versions) will further strengthen the plans laid out in the EO and provide guidance to agencies as well as the commercial, while supporting communities in creating implementation plans for Zero-Trust. As such, VMware will continue to focus our solutions and enablement for customers to meet the Executive Order and as the final enhancements are finalized and moved from draft forms of both the ‘CISA’s Zero Trust Maturity Model‘ for Civilian agencies, and the DoD Zero Trust Reference Architecture for the military branches respectively, our solutions are geared to provide each group the ability to implement our VMware solutions to meet these ZT frameworks current and future guidance.
Lastly, since CISA and the OMB publish these three documents simultaneously and the DoD within the same timeframe, the interlinkages and interdependencies between them will undoubtedly help maintain their close collaboration during the changes that may come going from the draft to final revisions stages, hopefully allowing the interagency exchange and appropriately reflect them in the remaining documents. As CISA, OMB and the DoD revise the initial Zero Trust guideline drafts, VMware will continue to offer recommendations on further alignment and strategies for implementation and integration of our solutions against both the drafts and final versions.
As an example, VMware will be augmenting our solution alignment and future whitepapers to incorporate the new CISA foundational pillars shown below, which unlike the ACT, include a data pillar to better facilitate the transition to Zero Trust Security:
Getting Started with Zero Trust
As a long-time partner of the Public Sector, VMware is committed to delivering tangible zero-trust compliance guidance. The Zero Trust Networking and Architecture Whitepaper provides a deeper dive into how VMware products and solutions can help the Federal, SLED & associated partner market for all Public Sector to assist in achieving their Zero Trust goals.








