With 2024 off to a roaring start, it’s time to consider mobile security plans. Please don’t wait until after a breach to evaluate and implement advanced mobile protection. The recently released Verizon Mobile Security Index report reinforces the fact that advanced mobile threats are a clear and present danger to organizations. Mobile devices represent effective ways to gain access into systems and data. Access gained via credentials is a primary motivator for hackers, who target both personal and corporate mobile devices.
Corporate and personal mobile devices shared a stunning statistic: 28% of each were targeted according to a survey of 490 global security decision makers who experienced an external attack when their company was breached.
— Forrester, The State of IoT Security, 2023 (cited in the Verizon Mobile Security Index)
The global state of mobile security attack vectors
Mobile behaviors and environments yield a broad set of vectors of attack: credentials, Machine-in-the-Middle (MiTM), and even malware. What are threats looking like this year? At the top of the list are phishing threats, both in email as well as via SMS, QR codes, and pretty much any other mechanism that a hacker can dream up for delivering malicious content associated with a URL.
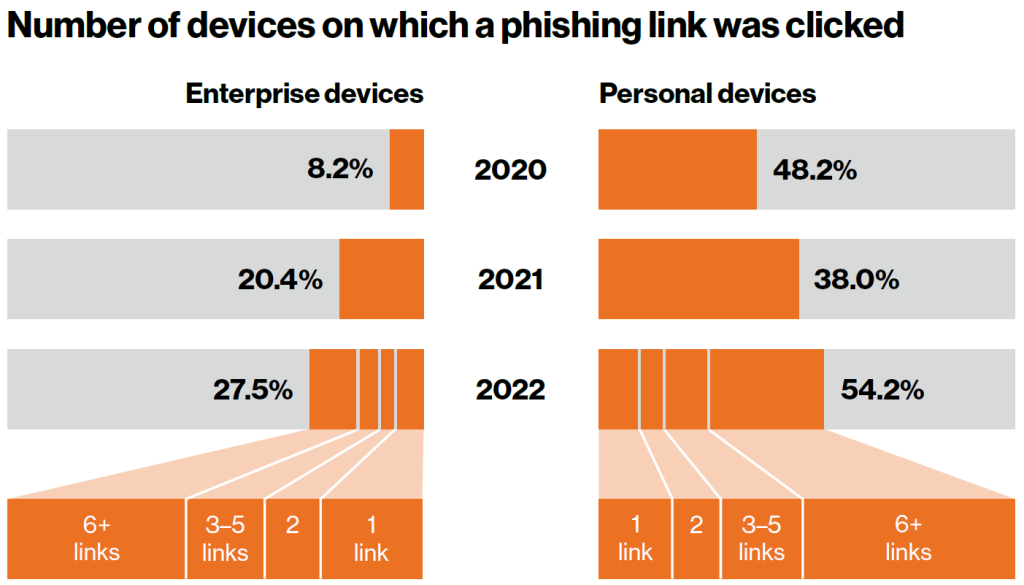
The percentage of devices that have yielded a click has increased steadily over the last few years. End users are clicking on multiple dangerous links. In fact, the number of corporate users that have clicked on more than six malicious links has increased by 637.50% from 2020 to 2022, according to Lookout’s The Global State of Mobile Phishing, 2023.
Another significant concern in addition to malware is leaky apps. We define leaky apps as things that are available in official app stores or via your corporate app catalog, that may not behave in a way that your IT and security teams are altogether comfortable with. (Our technical blog on how to block unwanted apps was one of the most read blogs of 2023, check it out here.) Also worth a review is the risk associated with MiTM attacks and unsecured traffic across fixed, remote, and public networks. And, of course, assessing and quickly responding to the risk associated with device and application vulnerabilities is critical.
More insights from the Verizon Mobile Security Index report
A highlight of the Verizon MSI report was an expanded viewpoint beyond what you need to address from a risk perspective to how you can more effectively address it. The report said it so well, that I will quote it here:
“Effectively protecting mobile devices and preventing them becoming the organization’s Achilles heel entails leveraging solutions that provide robust security while ensuring seamless user experience. Investing in continuous employee training, adopting multi-layered security protocols and using scalable, cloud-native solutions can help in achieving this delicate balance.”
We could not agree more. A broad set of capabilities are needed. User experience is vital. Cloud-native solutions perform, especially in the areas of observability and remediation.
How to plan your mobile security strategy for 2024
With the new year already under way, it’s important to launch a strong mobile security strategy — or update your existing plans — as soon as possible.
As you plan, here are seven key points and related questions to ask about your current mobile security solution:
1. Effectiveness. How easy is it to deploy and activate mobile security? A lot of organizations have struggled with installing and activating mobile security apps. Is your solution addressing this hurdle? Can you secure iOS, iPadOS, Chrome OS, and Android? What about rugged devices running Android via AOSP?
2. Range of threat detection provided. Is your mobile security solution automatically detecting threats? Is the protection broad? Some specific things to look for:
- Phishing and content protection. Does your solution cover messaging apps, QR codes, and typo-squatting? How configurable is the protection? For example, can you upload a list of URLs to be blocked?
- Application behavior. We covered leaky apps above. You need to be able to observe app behavior drift and detect and control app behavior. Note: You should be able to configure this via your mobile threat solution and coordinate response automatically. In our case you can do that via Workspace ONE Unified Endpoint Management (UEM). Orchestration could include controls to block and deny access to sensitive resources until a risky app is removed.
- Malware. Yes, malware is still an issue and you need protection against it.
- MiTM and rogue network threats. You’ll need protection against threats across fixed, remote, public, and home networks.
- Vulnerability detection. Your solution should include detection and automated remediation via UEM.
3. Automation, reporting, and response. Can your mobile security solution interconnect with your MDM or UEM solution so that issues can be automatically addressed? Can information feed into your IT service management solution and to your SIEM? How easy is it to inform teams automatically and to generate reports?
4. Privacy. Can you protect end users with the option of not collecting sensitive personal info?
5. Zero trust. Can phishing and content protection work in tandem with secure access to corporate apps and resources?
6. Usability. Are security messages to end users easy to understand? If a security issue is present, is the user notified instead of being cut off from an app or service with no notice?
7. Cloud. Is your mobile security a service? A cloud-connected security platform can share information with your SOC, automate responses via UEM, and populate reports with observable data.
The End-User Computing Division team is here to support you with security that’s easy to use, creates connections across teams and technologies, and supports your organizational goals. For more information, please contact your sales representative.
Additional resources
eBook: Workspace ONE Unified Endpoint Management + Security








