The National Cybersecurity Center of Excellence (NCCoE), part of the U.S. National Institute of Standards and Technology (NIST), recently updated the “Implementing a Zero Trust Architecture” guide. VMware is a contributor to this seminal document, which aims to demystify zero trust security and architecture by laying out practical approaches to implementing zero trust solutions.
What is zero trust? Simply put, zero trust is an approach to security that requires authentication and authorization to access any resource within an organization’s IT environment. Zero trust security does not require a specific network or a specific device type. By design, it can handle variability in environments — for end users and application and resource hosting. This is a stark contrast to perimeter-based approaches, where authorized users are granted broad access to the entire network.
Search for “Zero Trust Security” on the web and you will find a variety of definitions, starting with “least privileged access.” I find that zero trust is more easily explained by how it works:
- Something (user, device, application) attempts to access an enterprise resource.
- Pre-defined policies are applied to that access request, potentially including assessments of the current posture of the device, user, and network, resulting in authorization or denial of access to a specific enterprise resource.
- In the meantime, information is gathered that provides observability and informs policy planning. This information can also be used for automations that continuously verify and authorize access to a specific enterprise resource.
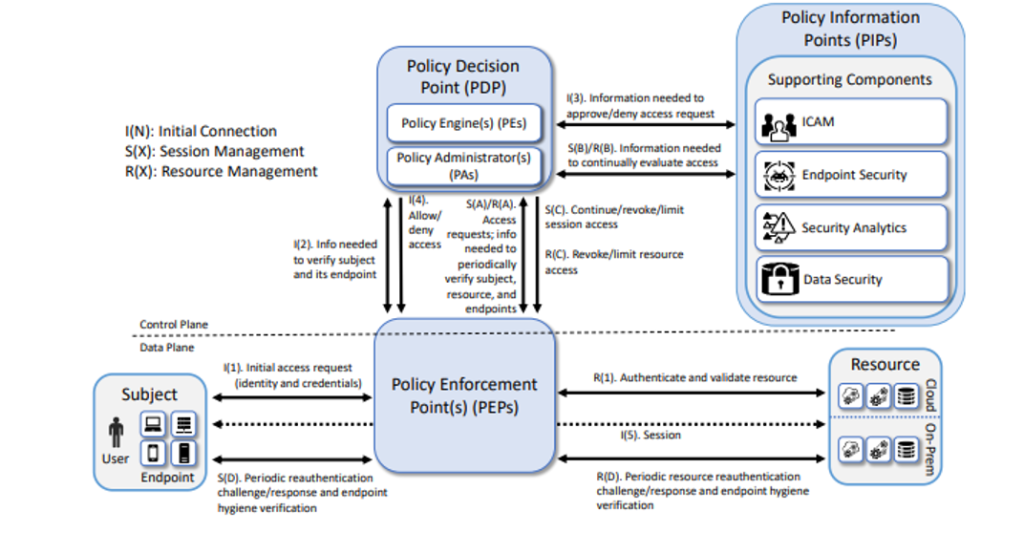
Zero trust architecture from NIST
VMware designed Workspace ONE to deliver exactly what IT and end users need to work efficiently, while securing the components of the environment. Give users the specific apps they need in one place. Then secure those apps individually, using access policies that consider the application sensitivity and ensure that device, user, network, and location attributes are assessed as needed prior to providing access. Enforce conditional access with strong authentication (phishing-resistant MFA) while using passwordless mobile SSO and secure tunneling (a modern alternative to VPN) to provide seamless and secure individual access to applications and resources.
What are your zero trust needs and goals? Securing remote workers, limiting the impact of credential theft, and reducing network and resource exposure could be a few of your priorities. Zero trust projects exist along a continuum that includes fundamentals as well as more complex implementations. Here are some zero trust project examples, from fundamental to advanced.
Fundamental zero trust projects:
- Strong authentication
- Identity federation with single or multiple identity providers (IdPs)
- Endpoint protection
- Device posture assessment prior to granting access
- Encrypting all network traffic
- No trusted networks
- Application and desktop virtualization
Advanced zero trust projects:
- More advanced projects often include automation and intelligence.
- Conditional, risk-based access controls based on typical and atypical behavior
- Aggregate reporting and real-time risk analytics
- Policy automation for varying user security profiles as well as corporate and BYOD devices
- Continuous device posture assessment
- Per-user application access via catalogs
- App access based on centralized authentication
- Per-application secure tunneling
- Identity-based network micro-segmentation
Zero trust at VMware Explore 2023 Las Vegas
If you are interested in learning more about zero trust security, don’t miss our panel session “Accelerate Zero Trust: Vision and Practical Projects with NIST and VMware Workspace ONE” on August 23, 2023, at VMware Explore 2023 Las Vegas. The session will also be available for streaming online following the event.
The VMware team’s contributions to NIST zero trust efforts are ongoing, and we’ll continue to invest in their vision and practical applications, such as architecture and implementation. Please review NIST Special Publication 1800-35B, “Implementing a Zero Trust Architecture,” on the NIST website during the public commenting period ending September 4, 2023.