Building on last year’s success of 25 million viewers, Apple elected to virtualize their Worldwide Developer Conference, commonly called WWDC, again in 2021. Virtual WWDC allows anyone to view any recorded session on-demand, including the Keynote and Platform State of the Union. As is tradition, the week started with Tim Cook kicking off the keynote presentation with a quick handoff to Craig Federighi to discuss the highlight capabilities of iOS 15, iPadOS 15, macOS Monterey 12, AirPods, HomeKit and more.
While the enterprise-specific announcements came later in the week, the keynote primarily focused on consumer-first solutions. However, many of these solutions have reaching impacts on the work experience of these OSes.
For iOS 15 and iPadOS 15, Apple released updates to the style and intelligence of notifications with its new “Focus” capability. This mode allows users to specify what activity they are focusing on (e.g., Work, Sleep, or custom) and to isolate themselves and only receive notifications set for those activities. Focus even includes a Do Not Disturb function to block all notifications except urgent exceptions.
macOS Monterey 12 continues its apparent journey to align with iPadOS by introducing Universal Control to sync mouse and keyboard actions between Macs and iPads. Meanwhile, iPadOS 15 had its bevy of enhancements to improve multitasking, widget layouts and the Notes app. Check out Apple’s keynote and developer documentation for more details.
As exciting as consumer features can be, this was a prosperous year for the management of Apple work devices. This document will be your guide to all the new announcements and what they mean for your organization and the world of enterprise mobility. Also, be sure to watch out for our Tech Zone articles for a deeper look at each feature, as well as “Getting Ready for Fall 2021 Apple Releases” for specific changes coming to Workspace ONE UEM.
Declarative Device Management
This year Apple announced a new management paradigm for Apple devices running the latest operating systems, called Declarative Device Management.
The current nature of MDM can be described as “imperative” in its design. Generally, at least in software frameworks, this implies that changes and requests are pushed from an external system or server to instruct the device or client what action to complete and when. This “push” communication style means the device remains relatively passive until the MDM system sends a command triggering an app install, remote wipe, device information sample or other behavior.
A declarative model essentially behaves in a reverse manner, where the client device is actively updating the server with any changes on the system. The MDM server still specifies which changes it would like the device to make, but no longer needs to poll the device for completed changes.
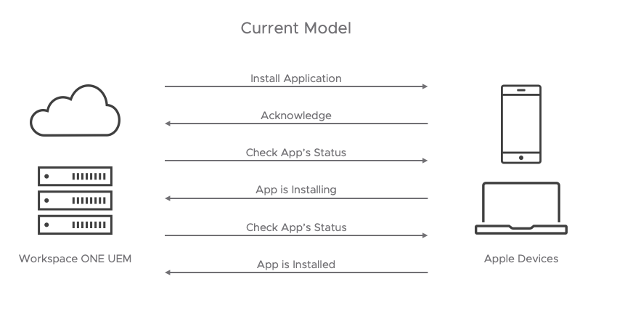
Here is an example of an app install contrasting the two behaviors.
Current push model:
New declarative model:
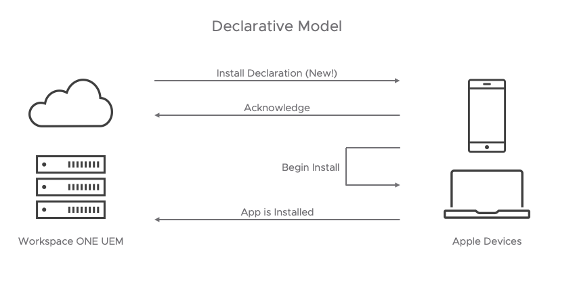
The logical next question is what advantages this new model has over the existing model. The illustrations above demonstrate the first and most obvious ones. First, performance and scalability improve considerably in a model where extra commands are not necessary to check the status. The changes reduce the previous model’s three command and response conversations to a single command conversation with a subsequent notification. Second, the notification channel allows the device to proactively send changes to the server rather than waiting for a server request. As a result, the server maintains an accurate representation of the actual live state of the device.
Let’s now jump into some of the specifics of Apple’s declarative MDM protocol and some of the other advantages it offers. Overall, Apple’s declarative protocol leverages the same MDM enrollment profile and commands. However, declarative MDM defines three new components: Declarations, Statuses and Extensibility. Let’s look at each separately.
Declarations
Declarations are the meat of the new protocol and, in so many words, allow admins to specify what items they want on a device. Subsequently, Apple breaks these declarations down into four categories: Configurations, Assets, Activations and Management.
- Configurations are the simplest to comprehend and map from the existing MDM world. Configurations are like the current profile payloads used to configure things like email accounts, passcodes, restrictions, etc.
- Assets are a new concept and help provide reference data for configurations. Assets might include things like user information, passwords, or identities for configurations like mail to refer. Any number of Configurations can use Assets, so when the user of a device changes, only the asset needs updating, and all connected configurations will automatically update as well.
- Activations are a set of configurations that can be applied concurrently and include “predicates” or pre-requisites to meet before applying the activation to a device. An example of these predicates is devices with the type ‘iPad’ or an OS version above ‘14.0’.
- Management declarations include general information about the overall state of the device, such as the managing organization and device management permissions or capabilities.
Status
Status, or more precisely the status channel, is a model where devices proactively report any update to their device to the MDM server. The reported list derives from the types of statuses to which the MDM server subscribes, such as device model, OS version, and hardware family. There isn’t much to this process, except it drastically removes the need to query devices iteratively and parse differences between the reported and currently stored state. This change presents an excellent opportunity to improve the reliability and efficiency of device compliance for things like OS updates and app installations.
Extensibility
One of the things we love about Apple devices also can be the most challenging. Apple is a highly innovative company, so their devices are constantly receiving updates to software and hardware. Within enterprise management, this constant change makes it tricky to understand which permutation of the device model, OS and MDM server version supports a particular capability.
With declarative device management extensibility, devices and management servers declare their supported capabilities. As a result, both the device and server update each other when this information changes. Extensibility features allow different versions of Workspace ONE UEM to remain in sync with its managed devices as they evolve.
Timing
Declarative device management appears to be the future of modern Apple management, starting in iOS/iPadOS 15 User Enrollment. However, this will likely be a multi-year effort with more and more options and enhancements coming to each platform release. For now, this is an exciting time to be in the enterprise Apple space.
Account-Driven User Enrollment
The current iteration of User Enrollment will celebrate its second birthday this fall. As a present from Apple, the new fall OS releases introduce a revamped version of this management mode, described as account-driven User Enrollment. This update comes with an improved onboarding experience, more authentication options for MDM providers, and the introduction of a “required” app that allows a single pre-defined app to install silently without prompting for user permission. This “required” app also cannot be removed by the user while they remain enrolled.
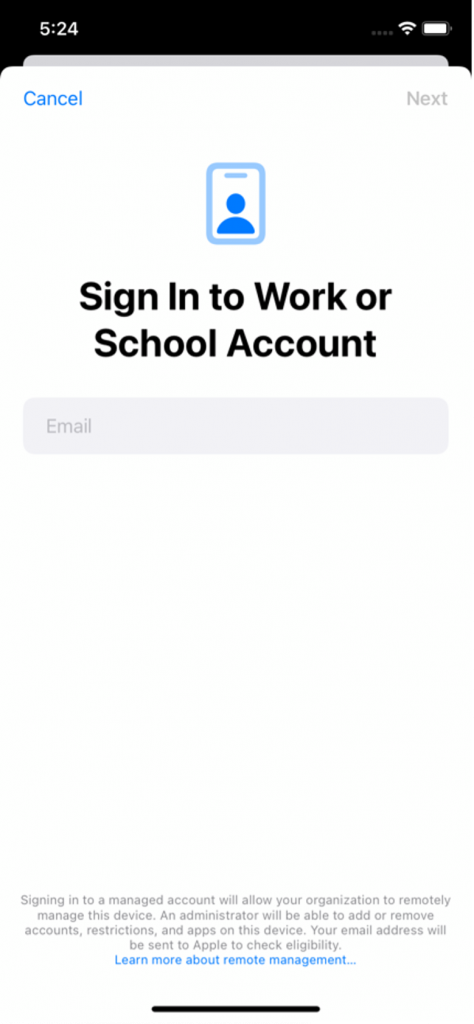
Overall, the new onboarding flow is a dramatic step up from its predecessor, without seeming unfamiliar. Users can see a new VPN & Device Management section in the Settings app to begin the Sign into Work or School Account, which kicks off the enrollment flow. This change to the Settings app replaces the need for an MDM provider to initiate the downloading and enrollment of an MDM profile Safari or a native agent app.
From here, MDM providers can insert a stream of authentication screens for username/password, MFA, Terms of Use, etc. Once completed, users receive one final authentication from their Azure AD tenant, which is still required to complete the User Enrollment. It’s unclear how this will evolve or if authentications from MDM providers will be sufficient for enrollment in the future.
Once enrolled, the new User Enrollment will allow a single required application to be installed silently, such as the Workspace ONE Intelligent Hub. This new functionality ensures that a critical anchor app cannot be ignored or removed by users. It’s essential to call out that this is only a single application per device installed in this manner. Any secondary apps will trigger a prompt to the user, who could disregard them.
The last change introduced in this new User Enrollment experience is the ongoing authentication that MDM providers can require for clients checking in to receive future commands post-enrollment. Re-authentication allows Workspace ONE UEM to prompt for reauthentication, if necessary, for any MDM client checking in and ensure a more secure and trusted connection.
Check out Apple’s session for Discover Account-Driven User Enrollment for more details.
New profiles and commands in iOS 15 and iPadOS 15
With the bulk of changes for Apple’s mobile platforms coming in the areas of declarative management and User Enrollment, new profiles and commands in iOS/iPadOS 15 were marginally limited, as detailed below.
- Managed Pasteboard – Admins can deploy a new restriction to force apps leveraging the clipboard to honor the existing managed open-in policies. This restriction is a long-awaited capability to help secure data in apps that may not have a built-in method to limit copy/paste and prevent data leaks.
- Required App – As previously mentioned, the required app capability allows MDM providers to define one App Store available application as “required” during enrollment. The MDM client will silently install the app on unsupervised devices. One important caveat is that apps already installed will still prompt users to manage the app.
- Update Path – Historically, admins did not choose what OS versions could be displayed or installed on iOS devices. Then with iOS 11.3, Apple introduced the ability to install specific versions of iOS. Still, this required admins to actively deploy older versions while deferring the latest to avoid users installing an untested version. With iOS 15, there is a new settings command to alter which versions get displayed to users in Settings > General > Software Update. This option, called a RecommendationCadence, can force a device to either show the highest available version, the lowest available version, or both (default).
- Siri on device – A new restriction allows admins to force devices to do all Siri translations on-device rather than via Apple servers.
- Preferred KDC – For extensible SSO, admins can specify that a device uses a set of preferred KDC servers unavailable by DNS.
macOS Monterey (12.0)
Like iOS, macOS Monterey contains quite an array of new capabilities in addition to the ones mentioned previously. These capabilities include changes like its mobile counterpart and others unique to the desktop platform. Below is a highlighted list of features coming in macOS Monterey.
OS updates:
- A new software update device ID is present to help admins determine which hardware models are compatible with the array of available updates.
- Alongside the existing InstallLater command, admins can add the option to set the maximum number of user deferrals. Once a user exhausts the configured number of deferrals, the system forces the install and restarts the device.
macOS Monterey Profiles and commands:
- A new capability that comes with a corresponding restriction is the Erase all content and settings option available for users to wipe their Mac device to factory standards. iOS users should be pretty familiar with this ability which is now available on macOS. However, admins can restrict users from wiping devices with this new restriction.
- Apple Silicon Macs are still relatively new, but they have been growing in popularity for consumers, with the enterprise following quickly. With macOS Monterey, a new device sample allows MDM to differentiate an Apple Silicon Mac from the previous Intel-based models.
- Recovery mode is critical for Mac IT admins to wipe, repair, troubleshoot, or reinstall macOS. However, this mode comes with some risk if users can change settings. Using a new Recovery Lock command, admins can configure and force passcode entry before accessing the recovery mode on macOS devices.
- As in iOS, admins can specify that a device uses a set of preferred KDC servers unavailable by DNS for extensible SSO.
tvOS 15
Unfortunately, tvOS 15 did not include any significant features or improvements. The only change worth considering is that Apple TVs will no longer broadcast their MAC address. This update is similar to the change introduced in iOS 14 and can be mitigated by a restriction key when configuring the Wi-Fi network.
Get ready for Fall releases
Overall, this was another successful WWDC whose announcements will impact the landscape of Apple in the enterprise for years to come.
As a set of actions to best prepare your organizations for the upcoming changes, check out the steps below.
- Be sure to add or vote on any new capabilities in our Workspace ONE UEM feature request portal at https://wsone.ideas.aha.io/
- Stay tuned to Tech Zone, the EUC Blog, and our knowledge base.
- Get up to speed on everything coming your way in Apple’s Fall 2021 releases, including new profile payloads and commands, now available at VMware Docs.









