Over the last weeks, we covered a whole range of base and value-added services for multi-cloud. Starting from cloud landing zones, managed infrastructure, managed applications all the way to managed networking services. And we looked at the different VMware Aria solutions that enable internal and external service providers to deliver these services.
All of these areas of multi-cloud have a security dimension to it:
- Cloud Landing Zones incorporate guardrails that ensure identity, access management and policies around cloud resources. Based on Aria Automation and Aria Guardrails, these practices ensure the right level of compliance and security of the deployment of standardizes services.
- Managed Infrastructure can help measure and ensure compliance with relevant security standards through Aria Operations. This includes VMware SDDC and Private Cloud security configuration guidelines, as well as regulatory and custom benchmarks.
- Managed Application services can support security of the application, Kubernetes and even full-stack level. This is achieved via Aria Operations for Applications and its various integrations.
- Managed Networking practices deliver security services on the networking level. It helps with detecting and understanding anomalies, component relationships that inform micro-segmentation policies and more. The tool of choice here is Aria Operations for Networks.
Security of the Cloud vs. Security in the Cloud
Depending on the underlying cloud, different actors in the multi-cloud ecosystem may have different responsibilities when it comes to security. The common hyperscale shared responsibility models distinguish between security “of” the cloud and security “in” the cloud. Security “of” the cloud meaning all the hardware and software components that make up the consumable cloud services. It’s the responsibility of the provider. Security “in” the cloud refers to the customer’s responsibility for secure configuration, access management as well as encryption of data and patching of workloads in the cloud.
This model is also applicable for cloud services consumed from VMware Cloud Service providers. In many cases, the providers ensure security of their cloud using the Aria Operations tools mentioned above. And they may offer the same secure operations as a value-added service for customer-owned private and edge clouds.
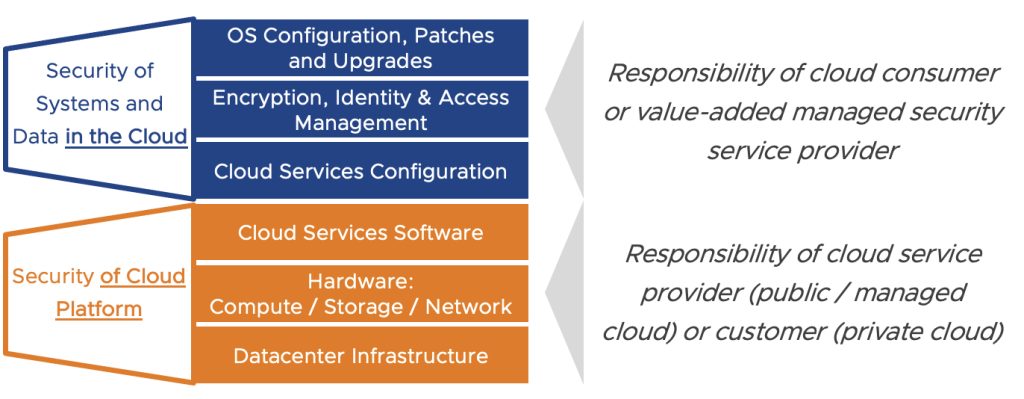
In this part of the series, we are going to focus on security “in” the cloud and the value-added managed security services associated with them. In detail, these are securing the cloud services configuration and securing workloads in the cloud.
Aria Automation for Secure Hosts and Secure Clouds
There are many solutions in the VMware portfolio that play a role in delivering cloud security. Since this blog series is about VMware Aria, we will focus on the relevant Aria solutions. Yet we are going to mention and briefly cover other components where expedient.
Aria Automation for Secure Clouds
The first solution that plays a vital role here is Aria Automation for Secure Clouds. VMware Aria Automation for Secure Clouds is a context-based, public cloud security and compliance platform that helps reduce misconfigurations across connected clouds and Kubernetes environments. It minimizes public cloud security and compliance risks with real-time visibility into misconfigurations, threats, resource relationships, and associated risks. Delivered as a SaaS service, it helps prioritize issues, enables collaboration with developers on remediation actions, and to verify security proactively within in CI/CD processes.
As described, the solution focusses on detecting security issues in public clouds and Kubernetes, that stem from misconfiguration. It supports the leading hyperscalers AWS, Azure and GCP. For VMware SDDC-based service provider and private clouds, similar practices that ensure secure configuration is needed. These will typically be based on the VMware Aria Operations family of solutions.
Aria Automation for Secure Hosts
VMware Aria Automation for Secure Hosts is the compliance and vulnerability management add-on component of VMware Aria Automation. We already covered all other Aria Automation components in previous posts on cloud landing zones and GitOps. Aria Automation for Secure Hosts delivers closed-loop automation for system compliance and vulnerability remediation. With VMware Aria Automation for Secure Hosts, (managed) security and operations teams can work together to define a tailored security policy for customers, scan systems against it, detect vulnerabilities and non-compliance issues, and actively remediate them.
“The new Aria branding replaces three existing cloud management brands: vRealize portfolio, CloudHealth by VMware Suite, and Tanzu Observability by Wavefront.”
https://blogs.vmware.com/management/2023/04/aria-rebranding.html
Aria Automation for Secure Hosts focusses on the workload security in the cloud. This is also where VMware Carbon Black Workload Security delivers additional value for managed security services customers and providers. You can learn about this solution here.
Managed Cloud Security Services
A recent global survey of 350 IT leaders revealed that “72% believe their companies moved to the cloud without properly understanding the skills, maturity curve, and complexities of making it all work securely.” Also, “68% said their organization’s security skill set across all clouds was only ‘somewhat mature’.” This combination of customer challenges makes cloud security a great fit for value-added services. Even further, the complexities and disconnects between the various tools grow significantly when the focus moves from a single cloud to multi-cloud. And as we have seen in other areas already, this is where VMware Aria can reduce complexity by enabling effective management of multiple clouds.
Bringing the VMware Aria pieces and its multi-cloud capabilities together results in the following big picture of multi-cloud security and compliance management. This can help providers identify the right tools, where to focus in the space depending on their capabilities and customer needs:
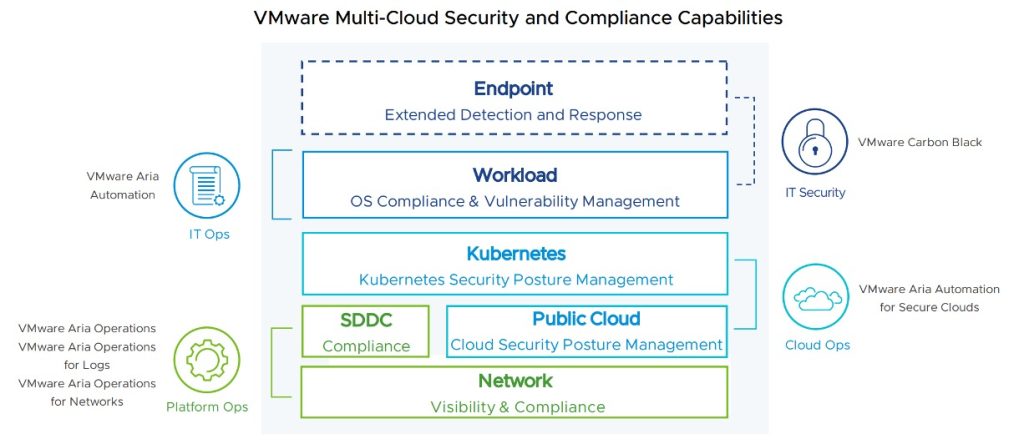
The right Tool for the right Service
Managed Cloud Network Security
Let’s break figure 3 down into more details and understand the various types of value-added managed security services. We already covered the network layer at the bottom in the previous two posts. In a nutshell, we can break managed network security services down into securing the network devices and securing network traffic.
In public clouds, the provider manages and secures the networking services they offer for consumption. Therefore, managed network device security is usually more important for private, edge, managed and hosted cloud environments. These contain physical and virtual network devices that need to be hardened and secured, as well as monitored and kept up to date. This is either the responsibility of the customer (unmanaged private and edge clouds) or the provider. The tools to get started on this are Aria Operations, Operations for Logs and Operations for Integrations with its various management packs.
Managed network traffic security is about securing the traffic between devices, workloads and clouds. It focusses on detecting anomalies, enforcing segmentation and restricting traffic, as well as auditing the compliance of the respective rules. This is independent of the underlying cloud and can be enabled using Aria Automation for Networks.
Managed Cloud Configuration Security
The practice of ensuring secure and compliant configuration of cloud services varies greatly between VMware clouds and hyperscale clouds. We largely covered the VMware clouds part in the post on managed infrastructure. The tools of choice here are the Aria Operations family of solutions.
Managing security of hyperscale clouds, including proprietary services above the IaaS layer, requires different capabilities and practices. These resources are likely more ephemeral and highly automated, compared to many traditional workloads with lower rates of change. They span many technologies that have traditionally been operated in silos and operators may lack context and visibility into the risk profile and threats.
VMware Aria Automation for Secure Clouds can help customers and managed service providers with cloud security posture management (CSPM). It basically helps to reduce misconfiguration mistakes, which are a common source of security breach in public clouds. To do this, Aria Automation for Secure Clouds provides support for 1,000+ cloud security best practices. It monitors compliance with these best practices across a wide range of resources in AWS, Azure, GCP and on Kubernetes. That allows providers to follow an integrated approach for securing public cloud services, but also Kubernetes environments with a single view. Secondly, it enables providers to continuously benchmark and improve compliance on their customers behalf. This is supported through various included industry standard as well as customer-specific custom compliance frameworks. To scale the managed public cloud security practice, providers can leverage the real-time API to shift-left security and verify resource configurations more proactively during CI/CD processes.
The following video gives more and in-depth information on the solution. It includes a demo from minute 17:40 which shows the work a managed security team for public clouds could conduct as a value-added service:
Managed Cloud Workload Security
The last major area is managed security for workloads in the cloud. An important differentiation must be made between securing IaaS VMs or Kubernetes workloads and securing non-IaaS, serverless or PaaS workloads. The latter is usually found in hyperscale public clouds. Ensuring security of these managed platform services is best done using the formerly described Aria Automation for Secure Clouds. It supports the following hyperscale services, amongst others:
Amazon Web Services
- Amazon Athena
- Amazon API Gateway
- Amazon CloudFront
- Amazon Cognito
- Amazon DynamoDB
- Amazon ECR
- Amazon ECS
- Amazon EFS
- Amazon ElastiCache
- Amazon GuardDuty
- Amazon Kinesis
- Amazon OpenSearch
- Amazon RDS
- Amazon RedShift
- Amazon SNS
- Amazon SQS
- AWS Elastic Beanstalk
- AWS Lambda
- AWS SageMaker
- …
Microsoft Azure
- App Service
- Azure Active Directory
- Azure Database
- Azure Cache for Redis
- Azure CDN
- Azure Container Instances
- Azure Container Registry
- Azure Cosmos DB
- Azure Functions
- Azure HDInsight
- Azure Machine Learning
- Azure Monitor
- Azure SQL
- Azure WAF
- Traffic Manager
- …
Google Cloud Platform
- AppEngine
- BigQuery
- Cloud Bigtable
- Cloud Functions
- Cloud Key Management
- Cloud Logging
- Cloud Monitoring
- Cloud Run
- Cloud Spanner
- Cloud SQL
- Cloud Storage
- Cloud DNS
- Google Kubernetes Engine
- Identity and Access Management
- Resource Manager
- Secret Manager
- Service Usage
- …
For IaaS and Kubernetes-as-a-Service (KaaS), there is the aspect of securing the contained operating system and service components. A common offering in that space is managed endpoint detection and response (EDR), which is mainly concerned with securing these resources at runtime. EDR involves memory scanning, monitoring active processes and network traffic, as well as rules to pro-actively prevent threats before they cause harm. The main tool here is VMware Carbon Black, which is also available for service providers but beyond the scope of this post.
The other practice in regards to workload security is managing vulnerabilities in these IaaS workloads. Besides Aria Operations for Applications and the other tools we already covered in depth, Aria Operations for Secure Hosts plays an important role here. It allows providers or customers to assess the status of workloads agains the latest common vulnerabilities and exposures (CVEs). This involves creation of vulnerability and compliance policies and pro-actively remediate systems:
Besides pro-actively fixing issues, providers can also use dashboard and reports to inform customers of security and compliance issues to let them act accordingly. For this, Aria Automation for Secure Hosts provides various vulnerability reporting options including a quick, printable dashboard view to help assess vulnerability trends over time. Following a scan, providers can access a downloadable list of all detected vulnerabilities, along with their corresponding advisory name, severity, vulnerability score, and affected assets. As an Aria Automation Config add-on, Automation for Secure Hosts Vulnerability goes beyond assessment, and takes advantage of Salt to actively remediate vulnerabilities while also giving full control over when and what to remediate.
The following picture summarises the different areas for managed multi-cloud security services and the supporting VMware solutions:
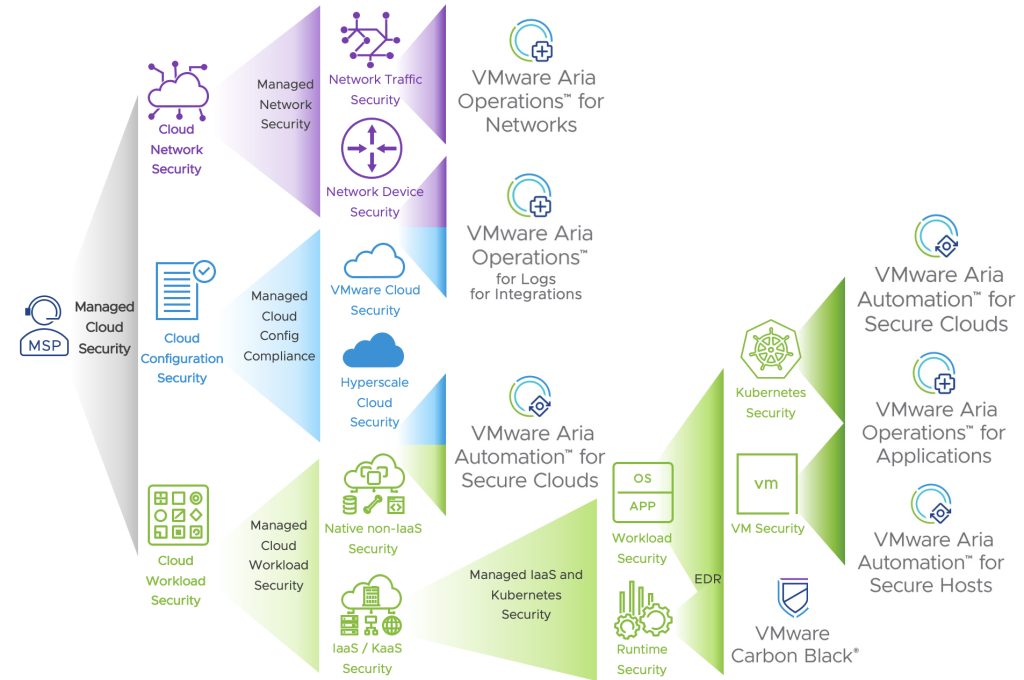
Conclusion
Similar to networking, managed multi-cloud security involved a wide range of different areas that services providers can focus on. The value-added services range from managed network security to managed cloud security posture management and workload security.
Besides the Aria Operations and Aria Automation solutions we covered previously, Aria Automation for Secure Cloud and Secure Hosts deliver the required capabilities. They enable providers to pro-actively monitor and remediate security issues in the configuration of public cloud and Kubernetes environments, as well as the workloads running in the cloud.
Next week, we will take a deep look into cloud financial management and FinOps. Until then, do not hesitate reach out to your account team if you have questions or want to get started with building your managed services business.




