Welcome to the sixth part of our Managed Services Monday series with VMware Aria. This time, we will explore the opportunity for managed networking and how service providers can leverage VMware Aria Operations for Networks, Aria Operations for Integrations, and Aria Operations for Applications to build a managed networking business for multi-cloud environments. Due to the complexity, the managed networking topic is split into two parts across two weeks.
We already covered how to build a managed infrastructure and managed application business for multi-cloud. With the complexity contained in these areas, managed networking plays a crucial role in optimizing the network infrastructure and ensuring reliable and efficient connectivity for workloads across multiple clouds.
According to the 2022 Gartner Magic Quadrant for Managed Network Services, „35% of enterprise buyers will demand managed network services“ by the end of 2024. The scope traditionally covers LAN and WAN, while “visibility into cloud resources and the networks connecting them remains relatively limited”. Yet some providers “offer service visibility, contextualization and service mapping across the entire estate, including public cloud visibility”.
Managed Network Services for Multi-Cloud with Aria
The Aria solution that builds an important foundation, besides what we already covered, is Aria Operations for Networks. VMware Aria Operations for Networks is a network monitoring tool that helps build an optimized, highly available and secure network infrastructure across cloud environments. This includes VMware NSX, VMware vSphere, Kubernetes, AWS, Azure, and VMware Cloud deployments.

It collects and analyzes metrics, APIs, configurations, metadata, integrations, telemetry netflow, sFlow, and IPFIX flow traffic, which traverses the cloud infrastructure. Once the traffic is analyzed, VMware Aria Operations for Networks provides traffic distribution details and a real-time view of network traffic patterns. It also collects configuration details and performance metrics for full visibility. These capabilities make it a solid basis for building managed networking services.
“The new Aria branding replaces three existing cloud management brands: vRealize portfolio, CloudHealth by VMware Suite, and Tanzu Observability by Wavefront.”
https://blogs.vmware.com/management/2023/04/aria-rebranding.html
Aria Operations for Networks comes with a wide range of support for VMware and third party network solutions that can be observed. These go way beyond what’s available in the Aria Operations solutions we covered so far. Automatically detecting these network components is another critical part of delivering managed cloud networking services. A good demo of using this capability, including as part of a managed networking practice, is available here:
To learn more about the basics of Aria Operations for Networks, including a 30-day trial, click here.
Aria Operations for Networks Deployment
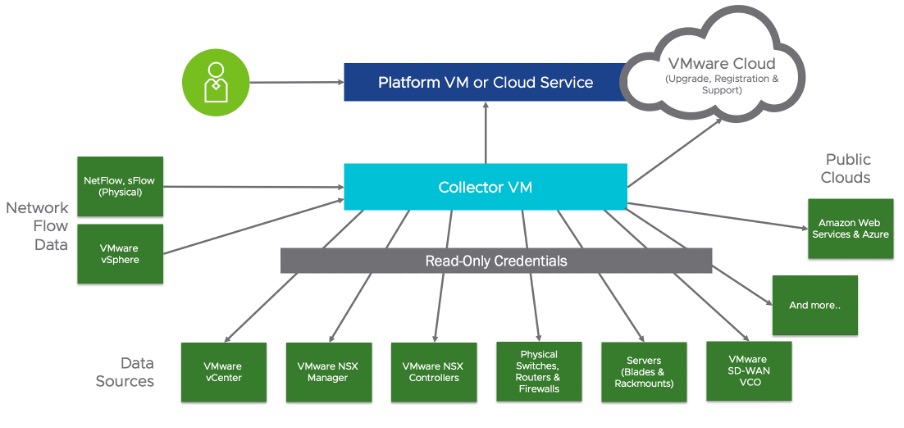
Since most of the managed networking service areas we cover here are based on Aria Operations for Networks, let’s briefly look at the initial deployment from the service providers perspective. Aria Operations for Networks is available as SaaS or on-premises deployment. The on-premises version requires the service provider to deploy the Aria Operations for Network Platform OVA and activate it with a license. Providers leveraging the SaaS version can simply onboard their tenant to a new instance via Cloud Partner Navigator. We have seen his process for other Aria solutions in previous blog posts.
In either case, providers (or customers) will need to deploy and maintain network collector VMs. These collect the data from the respective data sources via various protocols and upload them to the Aria Operations for Network platform. Size and number of the collector VMs will depend on the architecture and number of systems to monitor in the environment and vary between customers. You can learn more about this here.
We now have an understanding about the tools for a base managed service to use by the customer or provider. With that, let’s look deeper into delivering value-added services on top.
Identifying Areas for Managed Networking
Some of the key areas for providers to consider in a managed networking business for multi-cloud are the following (Figure 2):
- 1. Private Clouds: Customer workloads in their own data centers, private clouds and edge locations. Depending on the architecture, these may involve a wide range of physical networking components, software-defined networking solutions from VMware and other vendors, as well as connectivity to campus LANs.
- 2. VMware Cloud Service Provider Clouds: Service providers that offer hosted and managed cloud services in their data centers may have a similar networking stack. In most cases, this will also involve VMware NSX capabilities operated by the provider. Many providers expose the NSX features for self-service consumption or to deliver managed services.
- 3. Application Networking: Irrespective of the underlying IaaS cloud, the networking towards and in the application layer has become increasingly complex. This area uses technologies like Kubernetes, Container Ingress, Service Mesh, API Gateways and more.
- 4. Cloud Interconnectivity: All of the clouds in a multi-cloud environment need to be interconnected in some way. Besides VPN, this is typically done via private connections and the respective hyperscale services. These includes technologies like AWS Direct Connect, Azure ExpressRoute and Google Cloud Interconnect. To increase reliability and flexibility, solutions like VMware SD-WAN may be layered on top of this.
- 5. Public Clouds: In each public cloud, there are more or less proprietary network technologies and services. At the most basic level, these are for example AWS VPC, Azure VNet and GCP VPC. Yet they come with a plethora of potential additional services. Examples of these can be found here for AWS, Azure and GCP.

The set of managed value-added services that providers may specialize in, can go broad, deep or both. Deep meaning starting on the infrastructure level and going towards to application level. Broad in this context means from a single cloud focus to a multi-cloud focus. We are going to look at both dimensions in alignment with the different areas for managed networking from the above figure:

Let’s look a bit closer into these areas, the tools and integrations that allow providers to build managed services around them with Aria. For Private, Edge and VMware Cloud Service Provider clouds, we are going to focus on bottom left quadrant: single cloud, infrastructure level.
1. Private and Edge Cloud Networking
Integration into the existing infrastructure management
Private and edge clouds typically run on a set of virtual and physical network devices. Aria Operations and Operations for Integrations Advanced and Enterprise come with support for many of these devices. This allows the provider to expand their existing infrastructure managed services to the network layer to get started. The relevant components include devices from VMware NSX, Arista, Cisco, F5, HPE, Palo Alto Networks and more. There are also management packs for network management platforms like Nagios and SolarWinds NPM. If these already exist in the environment, integration is easily possible:
You can find the full list of integrations here and a set of Techzone demo videos here. Bringing network components into the existing Aria Operations platform allows the provider to expand visibility. The platforms boundaries presents a natural handover point between managed infrastructure and managed networking teams. While infrastructure operations uses Aria Operations, network operations uses Aria Operations for Networks.
Adding Aria Operation for Networks
To truly build a managed networking business, expanding the monitoring platform to network devices is usually not enough. For value-added, pro-active services, providers will amongst others need to:
- Gain unified visibility across hybrid and multi-cloud environments
- Gain visibility between overlay and underlay networks
- Conduct end-to-end troubleshooting, traffic and path analytics
- Leverage network assurance and verification
- Analyze traffic and apps across hybrid cloud and multi-cloud
- Measure application latency and performance
- And more …
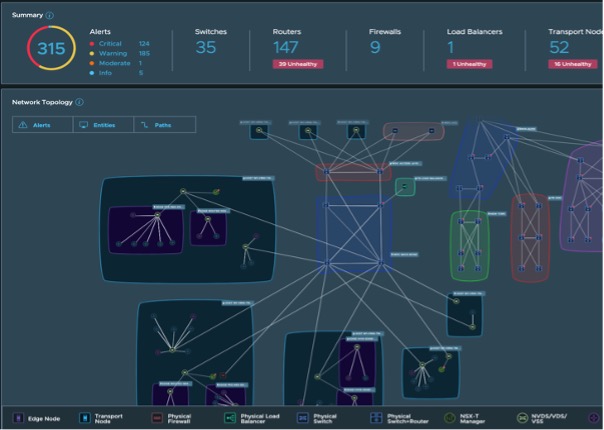
This is where Aria Operations for Networks comes into the picture. It creates the required end-to-end network visibility by combining Metrics, Events, Streams, Logs, Metadata, Configurations, APIs and Flows (Figure 4). These information, combined and correlated, help manage the network of a given cloud holistically. This is particularly important for customer-owned private and edge clouds with physical and virtual devices that need pro-active management.
2. VMware Cloud Service Provider Clouds
Fully managed network infrastructure
Like private and edge clouds, the providers’ clouds contain both, physical and virtual network components that need management. The main difference is that self-service management of these underlying components will not be available for the customer. It’s solely the responsibility of the provider.
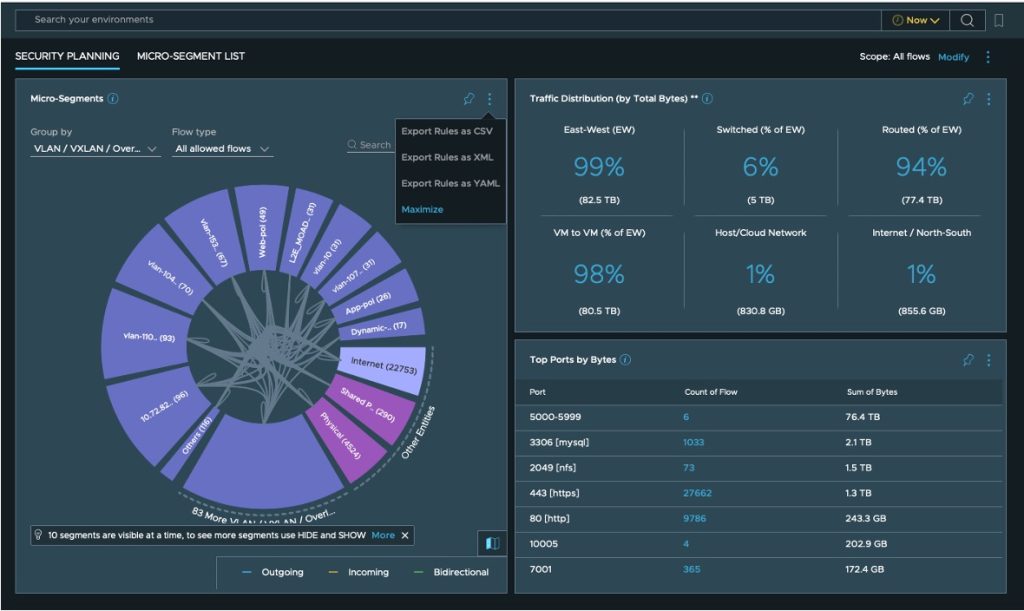
However, the value-added services we are going cover are equally applicable on customers’ private and edge clouds. First and foremost, service providers need to ensure stability, security and SLA compliance of their network components as a base service. A similar service can be delivered as a value-add for managed customer-owned network component (Figure 6). Common managed services for these components are event monitoring, security hardening of the devices, patching and update, as well as performance monitoring.
Additionally, flow analysis provides visibility into who is talking to who on the single-cloud network. Leveraging network flow protocols such as IPFix and NetFlow allows for vendor agnostic network discovery and planning. The provider can leverage this capability to ensure network infrastructure health, identify and resolve bottlenecks, provide network hardening, proactive alerting, support security planning and give visibility of top-talkers, outliers and more via reports and dashboards.
Virtual network devices and self-service deployment
In many cases, providers will offer a self-service consumption experience for resources in their cloud. VMware Cloud Director is an example platform that allows customers to deploy the compute, storage and network resources they need. Similar to the AWS, Azure and GCP management consoles, this includes the capabilities to deploy and manage various networking services:
- IP Spaces, Networks and Network Pools
- Routing and Network Address Translation
- Load Balancing
- North-South and Distributed Firewalls
- IPSec and L2 VPNs
- And more…
These services are instantiated using VMware NSX capabilities that are part of the providers managed cloud stack. In case of an edge or a managed / hosted private cloud, each customer may even have their own NSX stack – or multiple. Whether these services get provisioned via customer self-service or managed by the provider, the platform for delivering managed networking services needs to be able to detect and monitor them.
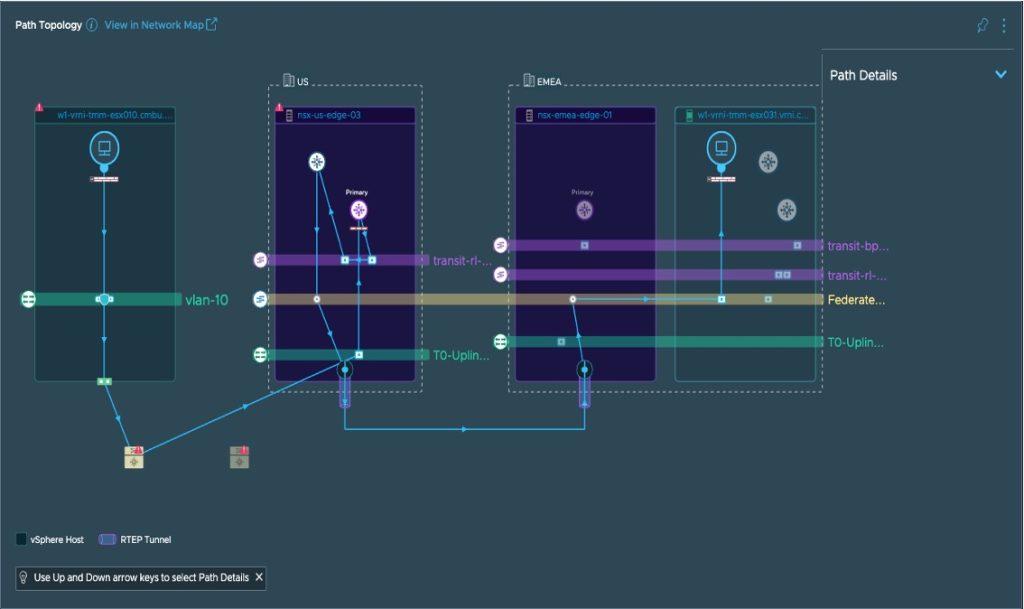
Aria Operations for Networks provides a federated view on the NSX-T environment. This gives visibility into global NSX-T entities and cross-site VM-to-VM paths. The provider can use this to operate and troubleshoot workload connectivity across the entire NSX infrastructure as a managed service.
This will either be a base managed service (provider-owned devices) or a value-added service (customer-owned devices). And it gives visibility into how NSX-T connects to other virtual and physical networks for pro-active troubleshooting and assurance of network service SLAs (Figure 7).

With this, we end the first part on managed networking for this week and will continue in the next post.




