As you might know by now, with the release of vSphere 5.1, VMware has enhanced vSphere Distributed Switch (VDS) operationally as well as functionally. I talked about the new features briefly in the what’s new paper and also posted evaluation videos on some of the key features. In the next couple of weeks, I am planning to post more technical details about some of these new features. Since there were lots of questions around the new BPDU filter feature, I thought I will address that in this post.
First of all, I will provide some background behind the BPDU frames for those who are new to this particular networking term. BPDU stands for Bridged Packet Data Unit. These are the packets that are exchanged between physical switches as part of the Spanning Tree Protocol (STP). STP is used to prevent loops in the network and is enabled on the physical switches. When a link on the physical switch port goes up, STP protocol starts its calculation and BPDU exchange to determine if the port should be in forwarding or blocking state. Bridge Packet Data Unit (BPDU) packet exchanges across the physical switch ports help identify Root Bridge and form a tree topology. VMware’s virtual switch doesn’t support STP and thus doesn’t participate in BPDU exchanges. If a BPDU packet is received on an uplink, VDS drops that packet. Also, VDS doesn’t generate BPDU packets.
The STP process of identifying root bridge and finding if the switch ports are in forwarding or blocking state takes somewhere around 30 to 50 seconds. During that time no data can be passed from those switch ports. If a server connected to the port can’t communicate for that long, the applications running on them will time out. To avoid this issue of time out on the servers the best practice is to enable Port Fast configuration on the switch ports where server’s NICs are connected. The Port Fast configuration puts the switch port immediately into STP forwarding state. The port still participates in STP protocol and if a loop is detected the port can enter the blocked state.
Another recommended configuration on these vSphere host facing switch ports is to enable BPDU guard. This configuration defines the STP boundary and keeps the topology predictable by preventing the devices connected to those ports influencing the STP topology.
The diagram below shows the spanning tree protocol boundary created due to the BPDU guard configuration on the physical switch ports. With this setup if any BPDU frame is received on the switch port facing vSphere hosts that port is blocked.
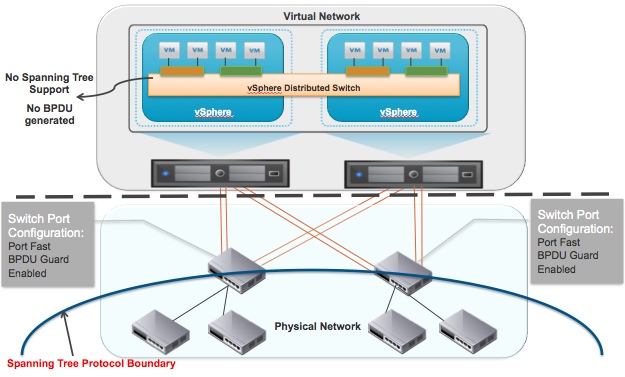
After taking a look at the reasoning behind the port fast and BPDU guard configuration, let’s discuss a scenario where these settings have caused issues.
Some customers have experienced Denial of Service attack situations when a compromised virtual machine starts generating BPDU frames. In this scenario the BPDU frames are forwarded through the VDS and reach physical switch port. The physical switch in turn disables the port because of the BPDU guard configuration. To recover from this uplink traffic path failure, the vSphere host moves that virtual machine traffic to another uplink and thus disables another switch port. This ultimately creates a cluster wide failure scenario as shown in the figure below (The red virtual machine is sending BPDU frames).
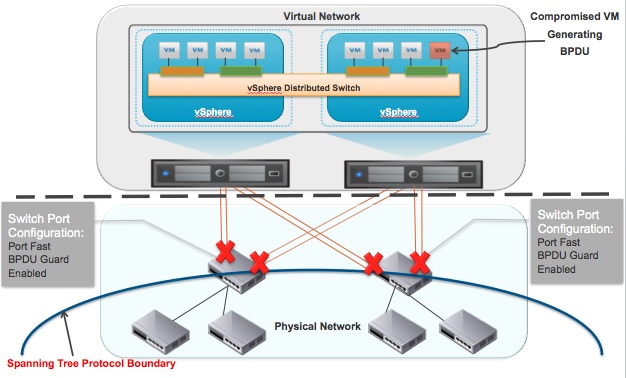
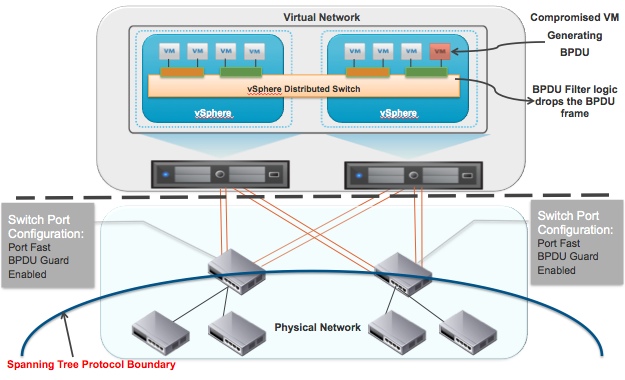
To prevent such Denail of Service attack scenarios, BPDU filter feature is supported as part of the vSphere 5.1 release. After configuring this feature at the vSphere host level, the BPDU frames from any virtual machine will be dropped by the virtual switch. This features is available on VDS as well as VSS. The diagram below shows a virtual machine (red) generating BPDUs and those BPDUs getting dropped by the virtual switch.
To configure this feature at the vSphere host level, you have to go to the advanced vSphere host setting. There you can modify the BPDU filter setting. First, filter the BPDU related property as shown below.
Default, guest BPDUs are not blocked. To change this setting select the property and click edit. Then change the value from 0 to 1 as shown below.
It is important to note that this is a host level configuration and you have to enable it on each host individually. If you are facing any Denail of Service (DoS) issue because of any compromised virtual machine sending BPDU frames, this feature will help you prevent that.
This feature should not be used in deployments where customers want to run software based bridging function in virtual machines by configuring multiple vnics. In such deployments, you have to make sure that Port Fast and BPDU guard feature on the switch port is also disabled. Please refer to the following KB article for other specific use cases and recommended settings
Please let me know if you have any questions on this feature. Next time, I will discuss some details on the Network Health Check feature and how it works.
Get notification of these blogs postings and more VMware Networking information by following me on Twitter: @VMWNetworking
















