In an era where telecommunication networks are at the heart of digital modern society, security is paramount. This blog delves into the critical need for a robust, multi-layered security approach within these networks, with a specific focus on the shift to cloud-native functions. Discover why out-of-the-box Kubernetes security isn’t enough to meet operators’ requirements, and how a Zero Trust model, coupled with advanced policy management, is essential to protect against vulnerabilities and comply with stringent regulations like NSA/CISA and NIS2 standards.
Read on to understand the complex security landscape and learn about the solutions Telia Company and Broadcom have built to help safeguard our interconnected world.
Securing Telecom Networks Layer by Layer
Telecommunication providers like Telia Company, a market leader in the Nordic and Baltic regions, offer essential services that carry sensitive data and support critical infrastructure. These services must comply with data protection, privacy, and network security regulations for national security. Therefore, service availability, integrity, and especially security is vital, as a breach could severely compromise delivery.
Going cloud-native for telecommunications environments involves introducing Kubernetes and transforming 3GPP-defined network functions into Cloud Native Network Functions (CNFs). This journey requires the three key stakeholders to actively work together to find the best compromise in terms of efficiency and the different layers of security.
- Telecommunication Providers (e.g., Telia)
- Cloud Infrastructure Providers (e.g., Broadcom)
- CNF Providers
VMware Telco Cloud Platform, built on VMware Cloud Foundation, provides telecommunication providers a unified infrastructure stack with compute, and networking, as well as VNF management and containers as a service through carrier-grade Kubernetes. While the VMware vSphere hypervisor inherently provides security through strict virtual machine isolation, and micro-segmentation with VMware NSX network virtualization offers network traffic isolation as part of a zero-trust model, further minimizing the attack surface at the Kubernetes layer is also important and contributes to the overall efficiency of the solution.
Why out of the box Kubernetes security is not enough
Kubernetes brings in significant security capabilities together with container orchestration. Telia Company’s cloud infrastructure, powered by VMware Telco Cloud Platform, has a Kubernetes layer operating on virtual machines serving as worker nodes running a secure operating system.
Kubernetes provides several security features for workload isolation, network segmentation, and access control. These include CNI-enabled network policies, namespaces, RBAC, Linux kernel security, secrets/config management, and Pod Security Admission Control (PSA).
However, these native security capabilities often lack the granularity and end-to-end visibility required for achieving least privilege access at all layers, and they are challenging to manage at scale. This is especially true for certain CNFs where specific pods, particularly those based on DPDK implementations, require elevated privileges to access hardware.
Telia then, in addition to working closely with CNF providers, saw the need for an advanced policy engine that would allow for increased flexibility, customization, granular control while operating at scale across their data centers. This requirement led to a collaboration between Telia and Broadcom to deliver a solution.
Kubernetes Policy Manager in VMware Telco Cloud Platform
To achieve the governance expected by telecommunication providers with restricted CNFs access to the container infrastructure, a Kubernetes policy manager is essential to enforce custom policies in Kubernetes. This prevents misconfigurations and ensures security and compliance by acting as an admission controller that validates or denies resource requests in real-time.
VMware Telco Cloud Platform 5.1 now features a centralized policy governance framework, leveraging OPA Gatekeeper with integrated Kubernetes hardening policies. These policies are based on recommendations from the NSA and CISA.
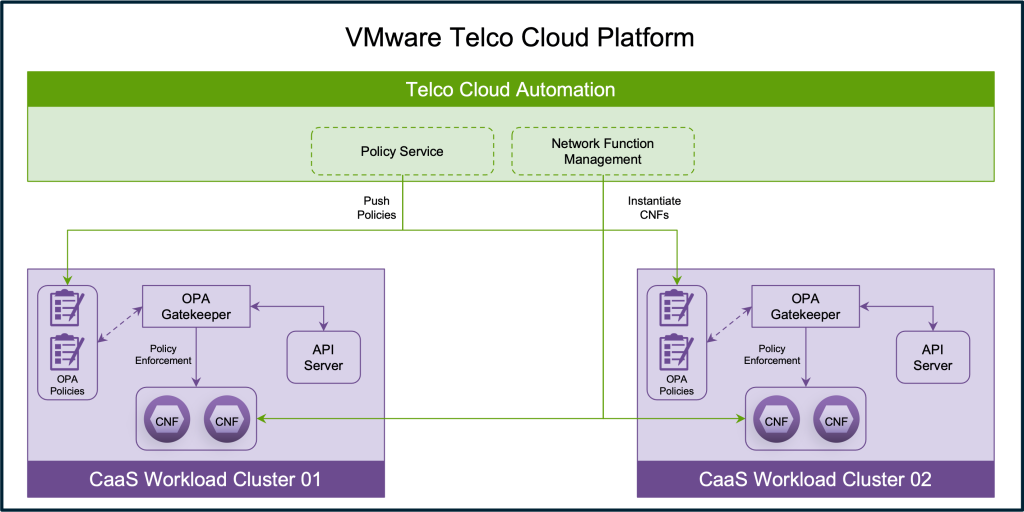
This framework allows platform administrators to control their clusters through fleet-wide enforcement of deployment rules, ensuring consistency and enabling audits of existing resources for violations. Violations can be reported either at the time of CNF deployment or afterward. If a violation is detected during deployment, the deployment fails and is reported as an admission violation. If a violation is found on an already deployed CNF in a running Kubernetes cluster, it’s flagged as an audit violation. In this case, pods are not evicted, but administrators are informed with a detailed message to take necessary action.
The built-in policies proactively prevent risky actions by disallowing host resource access, restricting image registry access, preventing escalation to root privileges, and ensuring non-root users operate within resource limits. If a malicious actor manipulates policy code on a worker node, the framework immediately detects the drift and reconciles the nodes to enforce adherence. Administrators can define granular policies, including or excluding specific Kubernetes resources from enforcement. This is particularly useful when certain pods require exceptions, allowing for approved deviations while still enforcing policies on other CNFs, thereby limiting the attack surface on the Kubernetes infrastructure.
Conclusion
To summarize, safeguarding telecommunication networks necessitates a robust, multi-layered security strategy, especially with the integration of Kubernetes and cloud-native functions. While out-of-the-box Kubernetes security offers a baseline, it’s insufficient for the stringent compliance needs of providers like Telia. A Zero Trust model, coupled with advanced policy management like that offered by VMware Telco Cloud Platform with OPA Gatekeeper, is crucial to prevent misconfigurations, protect against vulnerabilities, and ensure adherence to critical regulations, ultimately securing our interconnected world.
To learn more about VMware Telco Cloud platform and its built-in security policies, see the documentation.
Discover more from VMware Telco Cloud Blog
Subscribe to get the latest posts sent to your email.







