When deploying Zero Trust to quickly address security gaps and improve segmentation posture in a brownfield or greenfield environment, customers need a prescriptive, multi-stage segmentation workflow designed to progressively secure east-west traffic in the VMware Cloud Foundation (VCF) private cloud. vDefend delivers Distributed Firewall (DFW) 1-2-3-4* — an automated workflow that helps security administrators systematically strengthen their private cloud security posture. Customers can now simplify and fast-track the path to Zero Trust with a structured sequence of segmentation phases — from protecting critical infrastructure services to securing traffic between zones, and ultimately achieving application-level micro-segmentation. Additionally, over time, security policies can become bloated and inefficient. The new Firewall Rule Analysis feature efficiently manages this by analyzing DFW rules, so organizations can ensure their security policies are lean and effective.
Why Comprehensive Segmentation is the Need of the Hour
In today’s ransomware threat landscape, protecting only the perimeter has proven to be insufficient. Traditional security solutions, such as perimeter firewalls, protect only north-south traffic. Given that east-west (lateral) application traffic is approximately four times the volume of north-south traffic, it is critical and urgent to deploy lateral security to extend defenses beyond the perimeter.
As a result, large portions of the private cloud workloads remain vulnerable, enabling attackers to compromise underprotected workloads and laterally move to compromise high-value assets—the “crown jewels”. In 2025, cyber attacks caused substantial business downtime in days and weeks across various industries (including automobile, retail, and manufacturing), leading to financial losses in hundreds of millions.
Additionally, attackers are adopting AI/GenAI technologies to identify weaknesses in enterprise environments. These AI-driven attacks are not only faster, but in many cases, autonomous. Now more than ever, organizations need segmentation to get deployed faster. However, many organizations jump to app-level micro-segmentation and then face deployment challenges due to the lack of visibility into application communications and time-consuming coordination between infrastructure and app team silos. What they need is a guided zero-trust journey to quickly deploy comprehensive segmentation for all their workloads.
vDefend is purpose-built to auto-discover application communications, provide guidance on security rules, and verify policy correctness in a non-disruptive manner. The result: 360-degree segmentation with built-in automated workflows that include both macro- and micro-segmentation and continuous monitoring, all in a prescriptive manner.
vDefend DFW 1-2-3-4
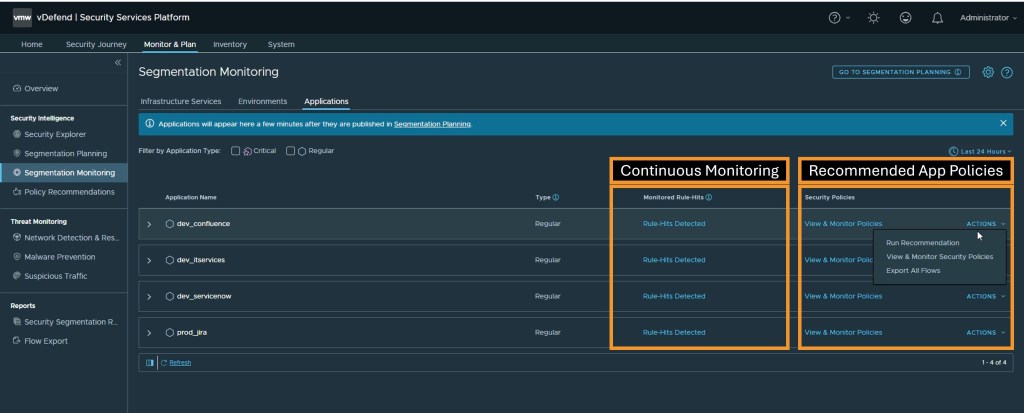
A practical Zero Trust deployment in a datacenter requires detailed visibility into workload communication, accurate zone and application mapping, and coordination across multiple IT teams. vDefend makes this process intuitive and data-driven, with real-time segmentation assessment of an organization’s security posture. DFW 1-2-3-4 provides a single, unified workflow guide through segmentation planning, auto-tagging and grouping, continuous monitoring pre- and post-deployment of DFW rules, and alerting on changes to enforcement. This new capability leverages an analytics engine that discovers communication patterns, identifies unprotected traffic, and recommends segmentation rules.
Customers can:
- Speed up micro-segmentation deployment without guesswork
- Improve efficiency through automated multi-stage segmentation workflow
- Secure VCF workloads quickly and easily
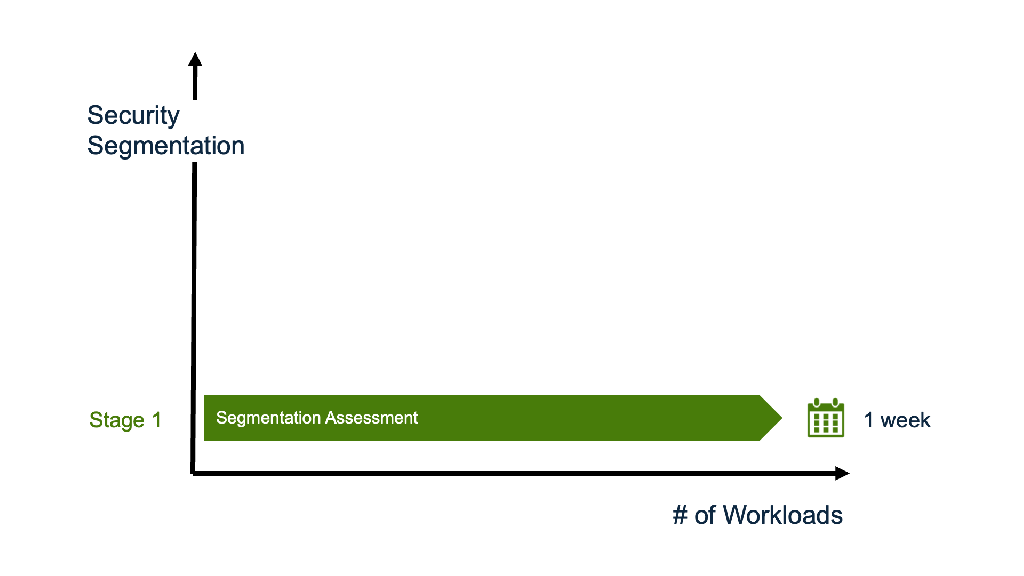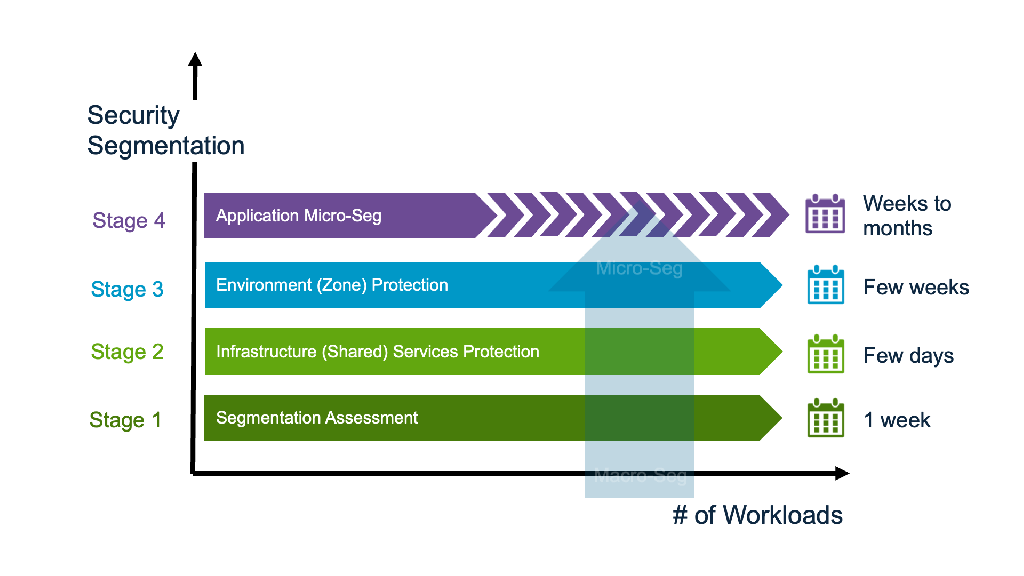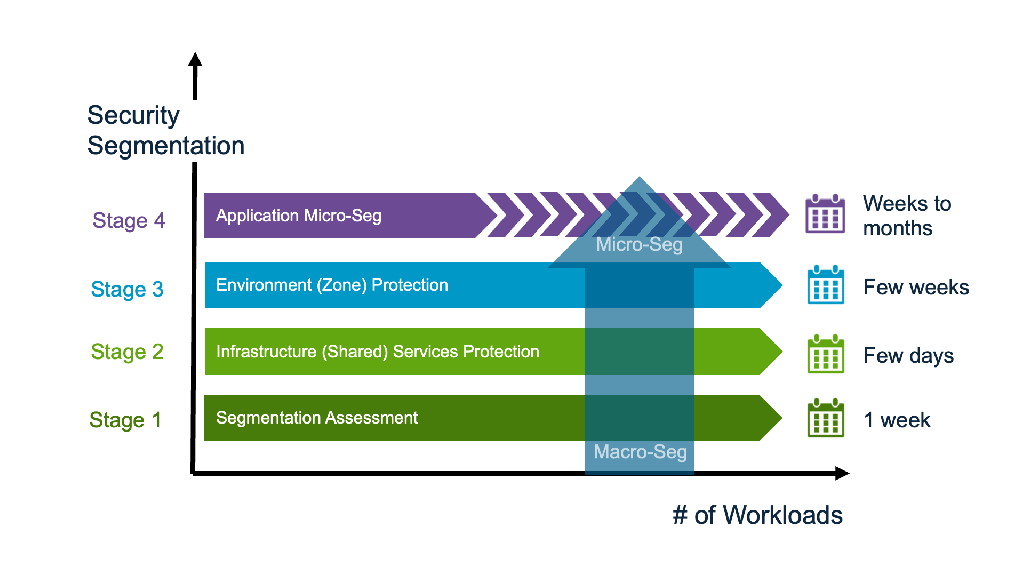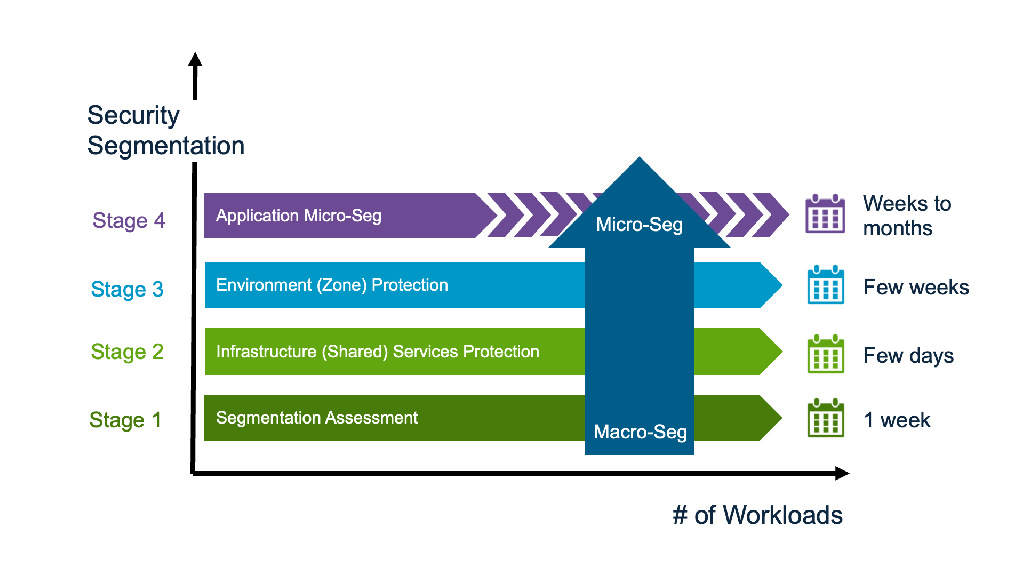
4 Stage Prescriptive Segmentation Deployment Journey
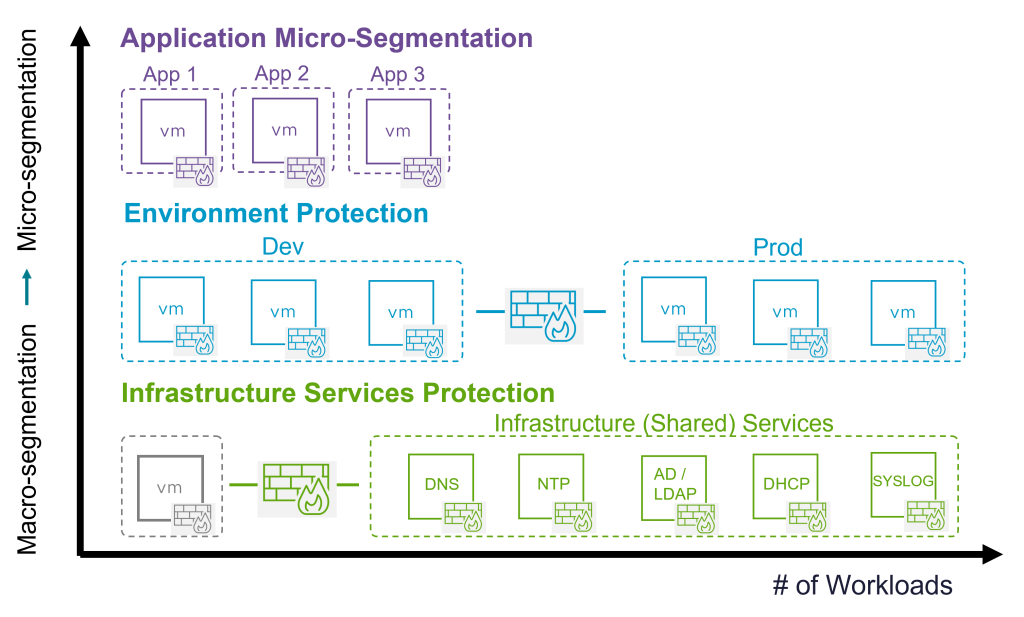
DFW provides a 4 stage prescriptive deployment process that follows lateral traffic patterns to quickly secure each of them, with guidance built-in that mirrors lateral traffic components and policy categories inside the vDefend DFW table.
Stage 1: Security Segmentation Assessment & Report
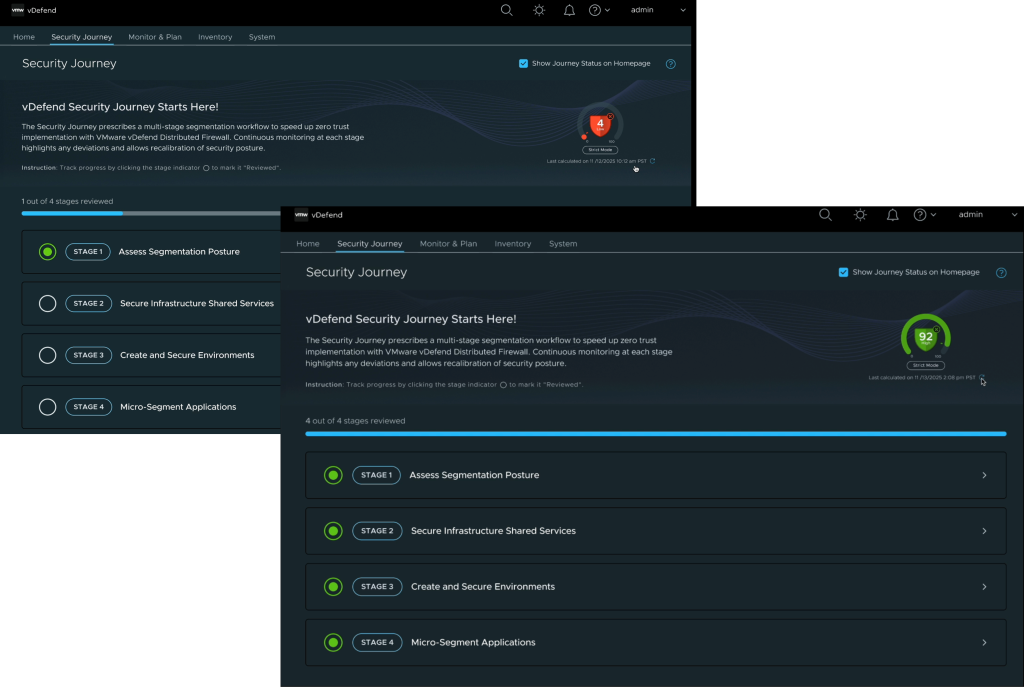
Administrators can activate DFW 1-2-3-4, visualize host clusters, and generate a Security Segmentation Report that highlights their current security posture and identifies opportunities for improvement. Learn more about this assessment in this blog.
As each phase is completed, customers can generate a Security Segmentation Report to assess their current segmentation score. The score recalibrates automatically whenever your environment changes, providing continuous feedback and helping customers track progress over time. This visibility helps teams demonstrate measurable progress toward Zero Trust objectives – and communicate outcomes clearly to executives and auditors.
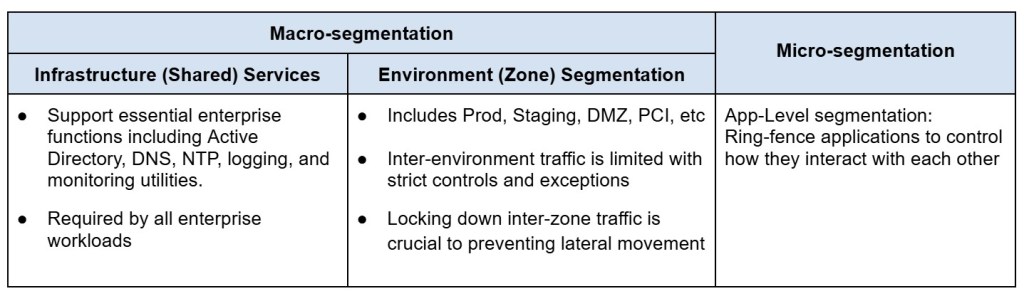
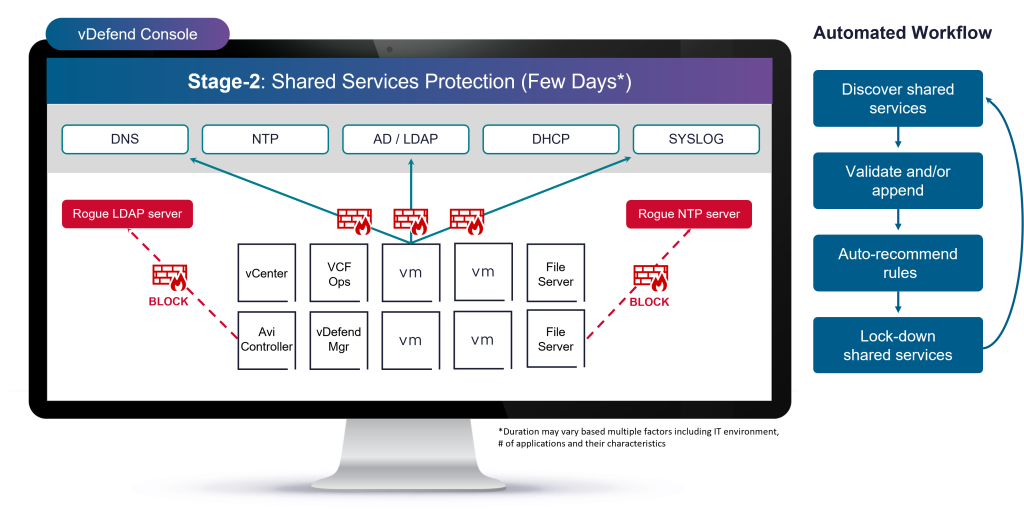
Stage 2: Infrastructure (Shared) Services Segmentation
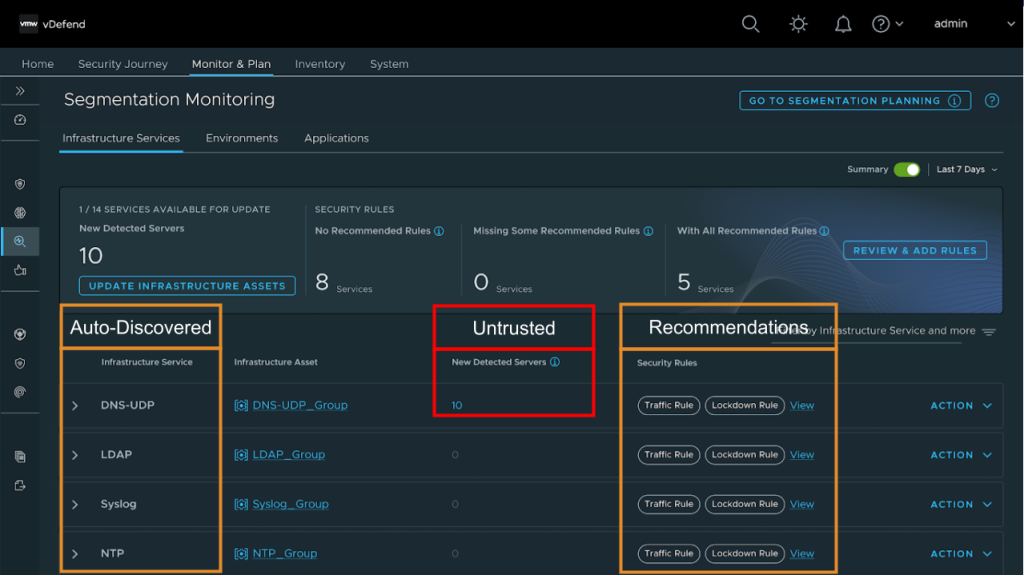
Start with the foundational layer of your datacenter – shared services such as DNS, NTP, Syslog, SNMP, DHCP, and LDAP/LDAPs. DFW 1-2-3-4 automatically discovers infrastructure services to identify service endpoints and allows the user to validate and automatically create protection rules to these services. Alternatively, users can feed their known infrastructure service endpoints via CSV file for the system to add infrastructure services. This step delivers quick security gains with minimal disruption—the ideal “low-hanging fruit” for teams beginning their Zero Trust journey. Locking down these services, especially DNS servers, allows the user to remove the most common Command & Control (C&C) and exfiltration paths for malicious actors.
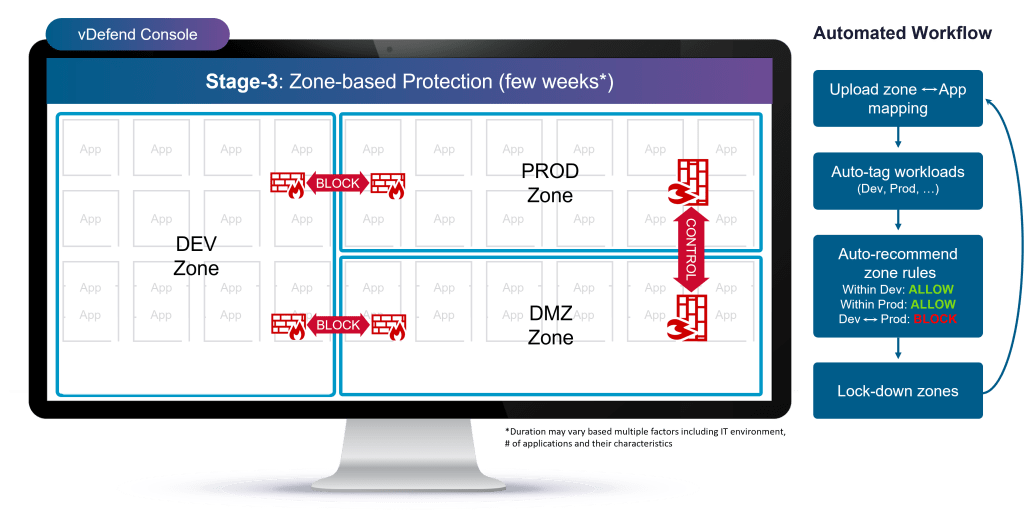
Stage 3: Environment (Zone) Segmentation
Once infrastructure (shared) services are protected, users can proceed to defining environment (zone) boundaries – for example, Development and Production. Users can import this metadata using a CSV file. The system supports CSV files that are exported from a CMDB system (such as from ServiceNow) or even from vCenter, or users can create a CSV file from a simple spreadsheet template provided by DFW 1-2-3-4. The platform assigns security tags for these workloads, validates relationships, and provides default environment-level rules through the DFW, while Zone Segmentation for existing workloads using traditional firewalls requires complicated Network and IP Address.
Users can monitor traffic leakage between zones and ask the system for either the list of traffic or a set of recommended rules that can then be granted exceptions. DFW 1-2-3-4 continuously monitors for these leakages and alerts the users to take action on newly discovered leakages. This phase ensures that environments remain isolated, minimizing cross-environment exposure and tightening your organization’s overall security posture.
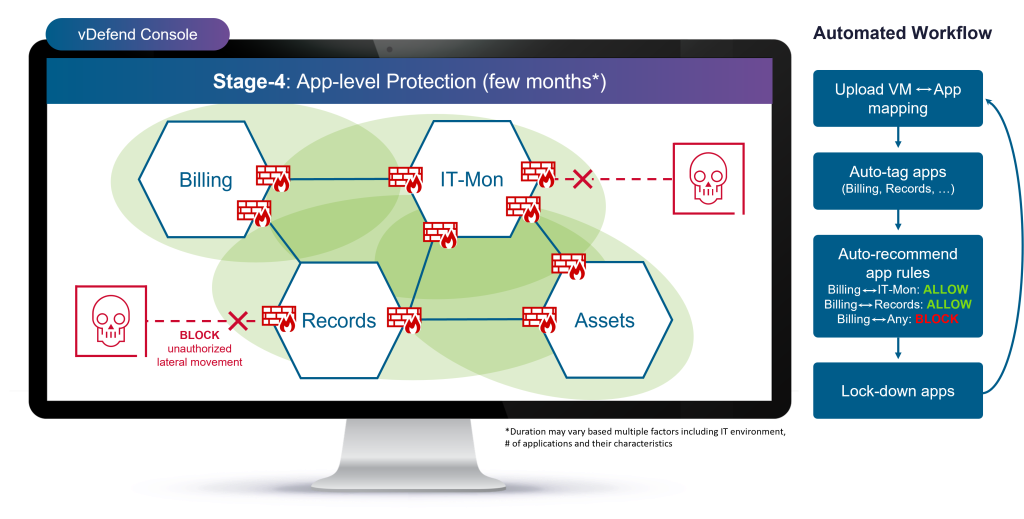
Stage 4: Application Micro-segmentation
Zero Trust for datacenter traffic requires defining controls for each application. In this stage, there are three steps: a. defining application boundaries used to convert them into tags and groups; b. defining application ring-fencing controls that control over which ports and protocols communication is allowed; c. defining micro-segmentation by defining controls within each application across tiers (web front end, application server and database). This fine-grained segmentation not only enforces least privilege but also strengthens resilience against east-west threats.
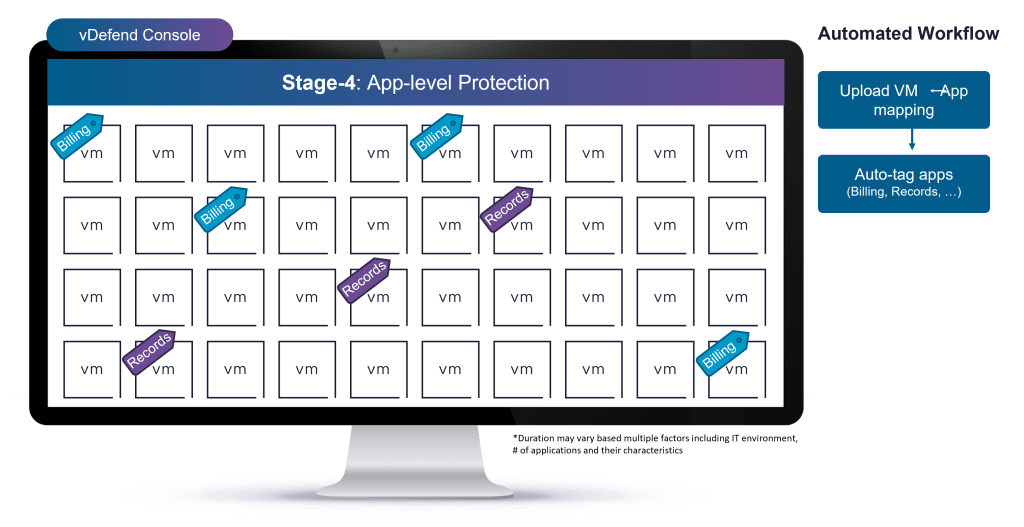
Stage 4a: Workload to Application Mapping
Users can upload into the system via a CSV file, VM-to-application mapping. DFW 1-2-3-4 will then auto-tag and create these application groups. These application groups can then be subsequently used for monitoring and defining DFW rules.
Stage 4b: Defining Application Ring-fencing Controls
DFW 1-2-3-4 can now monitor these tagged applications, and the system recommends application-specific firewall controls that allow communications only between permitted entities while locking down the applications.
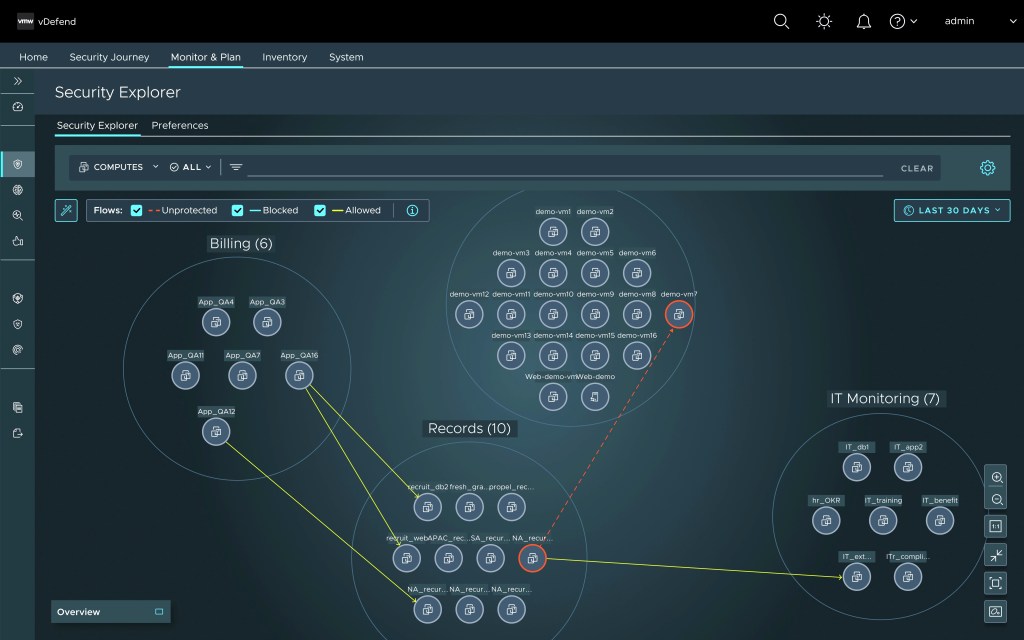
Stage 4c: Continuous Monitoring of Application Traffic and Fine-Tuning Micro-segmentation Controls for Application Tiers
DFW 1-2-3-4 continues to monitor each application, both before and after rule publishing. The system continues to track application flow metrics and security posture for rules in real-time. Users can fine-tune rules for application tiers to progressively harden their micro-segmentation posture.
Mission Accomplished – Macro/Micro-Segmentation in Record Time
With DFW 1-2-3-4 multi-stage security journey, a typical Zero Trust deployment can be rolled out in as little as a few weeks – comprehensively, systematically, and most of all, with confidence. Starting with an initial low-scoring assessment, the post-deployment high score validates the improvement to the organization’s security posture.
Optimizing Firewall Rules with Rule Impact Analysis
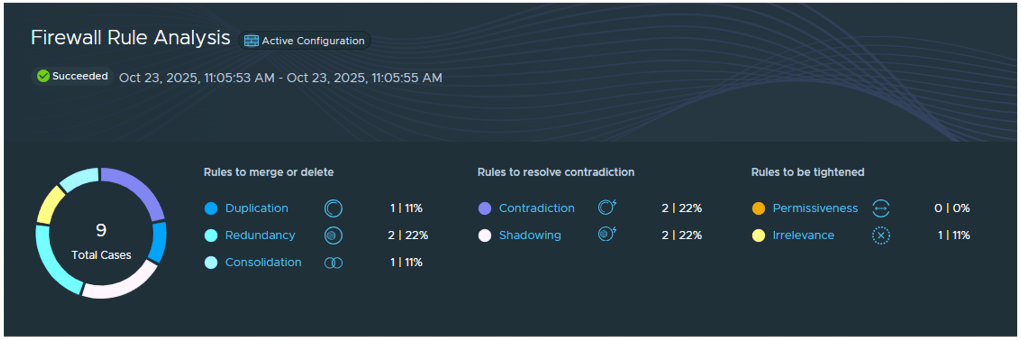
With a large number of apps being segmented, this can result in a significant number of security policies that are difficult to manage. Unlike traditional IP-address-centric firewall rules, vDefend simplifies and scales security policies with tag-based groups and policies, rather than IP-based rules. Still, over time, security policies can become suboptimal. That’s where Firewall Rule Analysis comes in. This powerful feature analyzes DFW rules, ensuring security policies are efficient.
vDefend’s Firewall Rule Analysis identifies and flags seven critical rule optimization opportunities: duplicate rules, redundant rules, rule consolidation opportunities, rule contradictions, shadow rules, overly permissive rules, and ineffective rules. This calibrated analysis helps eliminate rule bloating and fix potential security misconfigurations. Forget laborious manual scripts or the need for separate, third-party tools for DFW rule analysis within your VCF private cloud. vDefend offers faster, far more comprehensive detection for both firewall misconfigurations and firewall rule optimization opportunities at no additional cost.
*DFW 1-2-3-4 and Firewall Rule Analysis are features of Security Intelligence, available through Security Services Platform (SSP) release 5.1.
Additional Resources:
- SSP capabilities: read this blog.
- vDefend DFW 1-2-3-4 overview: Watch this video.
- vDefend Firewall Rule Analysis overview: watch this video.
- Join the new vDefend’s Edge Webinar Series for a deeper understanding of these and other vDefend capabilities.