With each passing day, more and more companies are finding themselves victims of security breaches. Data center architectures have been traditionally flat network architectures that rely on perimeter firewalls to be the only inspection point. This inherent trust of the high speed private data center has allowed both unfettered access between workloads and malicious payloads to propagate freely. As network/security professionals, it is critical that we protect east/west network traffic with more than just perimeter firewalls. We must protect everything from common services, all the way down to business-critical applications.
You might be asking yourself, what are the different ways I can do this? Are there established strategies to accomplish this goal quickly? The answer is, absolutely, but all of them require increased visibility into the data center flows. There are multiple ways you can achieve quick wins and begin to protect your workloads from potential threats.
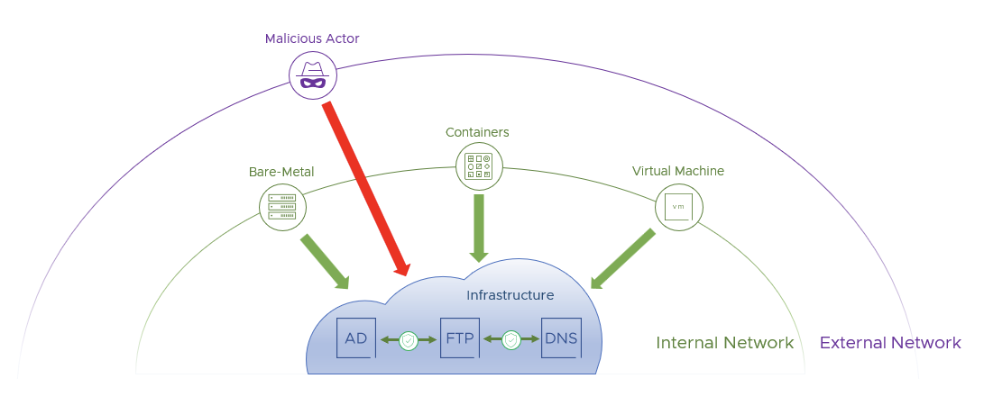
Secure Infrastructure
Applications need access to common services like Active Directory, DNS, software update delivery, logging, and others. These critical services are prime targets for bad actors to exploit because they can be used to enable access to additional workloads in the data center. The VMware vDefend Distributed Firewall can help secure access to these services to prevent lateral movement. This can give security teams a quick win, making it a great starting point from which to advance on your zero-trust journey. Securing the infrastructure in the data center includes:
- Restricting access to common services by only allowing only required sources to access critical infrastructure services
- Restricting lateral movement within common services
- Preventing the use of unsecure protocols like TLSv1, SMBv1, RDP and more
Secure Virtual Environments
Many applications run in multiple environments such as production, user acceptance testing, quality assurance, and development. Code updates, policy changes, and service expansions are usually created in development environments and moved up to the stack to production. There are many reasons that access to the different environments may need to be restricted. The VMware vDefend Distributed Firewall makes it possible to achieve this in a few clicks or a handful of API calls. Unlike traditional firewalls that use IP-based groups, vDefend uses metadata attached to the virtual machine to dynamically add them to groups. These groups, in turn, are utilized to create policy that is much more dynamic than simple IP-based rules. When a workload is created, it is automatically added to the group. When it is retired, the workload is removed from the group and policy resulting in optimized rulesets without human intervention.
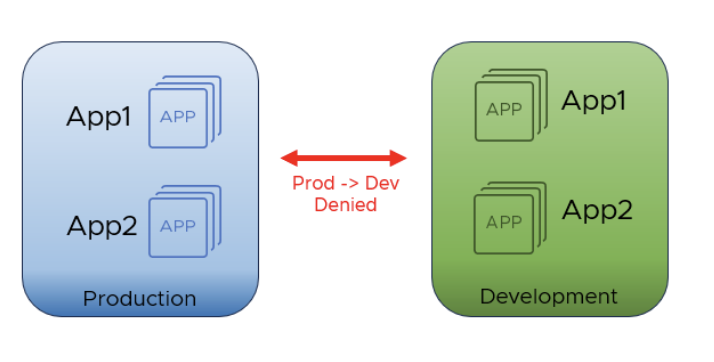
All these zones can be created in software with VMware vDefend. With a traditional perimeter firewall, network changes would be required to create new zones. IP address changes would need to be made to move a workload from one zone to another. Even with the zones separated, a compromised workload within a zone would still be allowed to execute unauthorized lateral movement. VMware vDefend can allow you to secure zones and applications within zones at the same time.
Secure Applications
Realizing zero trust security requires understanding the workloads that are critical for the organization’s day-to-day operations in great detail. Securing east-west communications between these workloads is essential for preventing malicious lateral movement. This means ensuring that only required traffic is allowed. VMware vDefend Intelligence can help you gain all-important visibility and automate creation of security policies that prevent lateral movement of real world threats.
If a web server in a multi-tier application becomes compromised, it would be able to exploit other workloads, like a database server, without proper East/West lateral security. Securing flows between these tiers is essential to properly protect important company data. Deploying new workloads can be equally challenging and involve manual changes in parameter firewalls. These changes can take weeks to schedule if multiple operational teams are involved. Without constant upkeep, these firewall configurations can become suboptimal and complex to troubleshoot. The longer a rule exists in a firewall, the harder it becomes to reliably remove it without risk of potential service outages. VMware vDefend avoids these issues with dynamic groups and policy enforcement.
Most rules in a firewall focus on protecting apps from one another. We want to allow applications to talk to each other as long as it is absolutely required for them to function and provide a service to the customer. All other application have no need to communicate with the application and could leave it exposed if a breach occurs in the datacenter. Zero-Trust on the other hand, extends the security policy within the application ensuring only required flows between the tiers can happen. This protects both internal and external applications from threats. VMware vDefend allows you to do both at the same time depending on the application security requirements.
Application Isolation
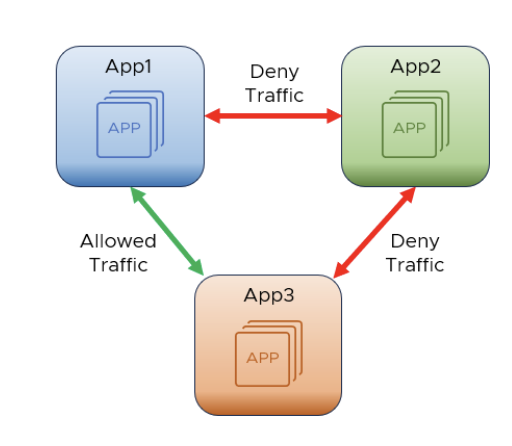
App 1 is allowed to talk to App 3. App 2 is not allowed to communicate with either App 1 or App 3.
Zero-Trust Microsegmentation

Inside App 1, traffic between Web and Application server is allowed but the Web server is not allowed to connect to the Database Server.
VMware vDefend has everything you need to secure your network traffic. Whether you are looking to secure your common services infrastructure, isolate your environments, or secure your business-critical apps, VMware vDefend can help you achieve your goal.
Resources:
Try this 2426 Hands on Lab to learn more about VMware vDefend Security.
Check out the following videos for demonstrations of VMware vDefend Security features:
Secure Virtual Infrastructure with VMware Distributed Firewall
Zone Segmentation using Gateway Firewall







