Contributors: Chris Wagner and Nikki Benoit
Executive Summary
LummaStealer is a Malware-as-a-Service (MaaS) that is available on the dark web. MAAS models have substantially reduced the barrier to entry in the realm of big game hunting. Instead of executing malspam and phishing campaigns directly, developers offer their platforms to other threat actors through an ecosystem of forums on both the public internet and the Dark Web. The malware marketplace has evolved in some places – transitioning from exclusive and highly technical requirements to advertisements that highlight improved user experience, ease of use, and ongoing development to evade antivirus detection. Emerging threat actors now have access to professionally crafted malware that comes with guaranteed troubleshooting and customer support.
History
Lumma Stealer was initially detected by security researchers in mid-to-late 2022 when it was advertised on Dark Web forums. Although its promotion began on exclusive underground platforms, we’ve since noticed its advertisements transitioning to Clear Net hacking forums.
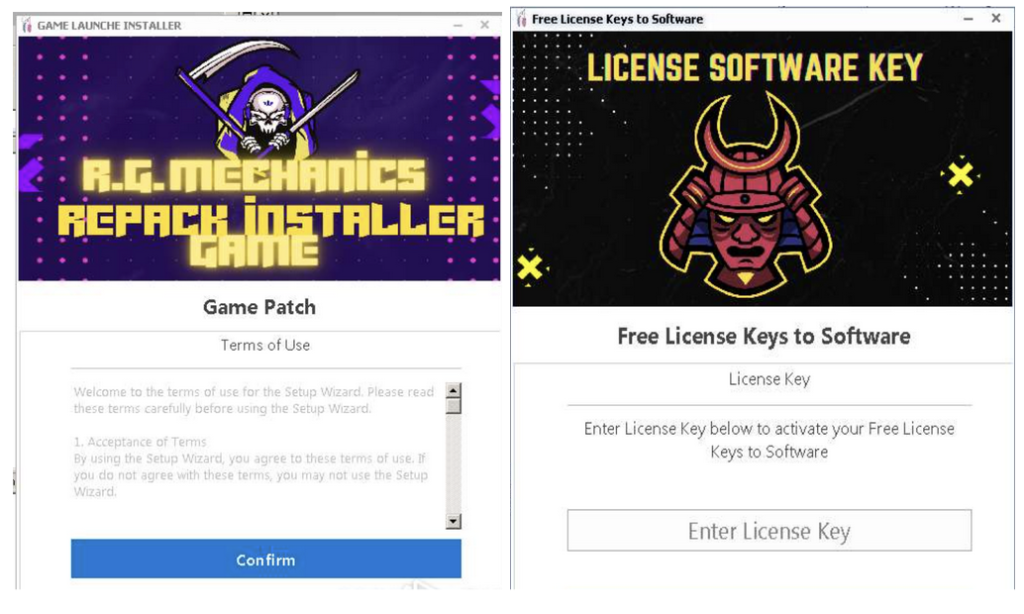
Throughout its existence, Lumma Stealer’s affiliates have employed a mix of intensive reconnaissance and targeted spear-phishing campaigns. In addition, they’ve utilized broader strategies, such as software phishing sites that mimic popular applications and platforms to deceive its users, ultimately leading to the distribution of Lumma Stealer. Most recently, in 2023, Lumma Stealer has been observed being distributed through drive-by-downloads, masquerading as browser updates, and through deceptive sites offering game downloads and software cracks.
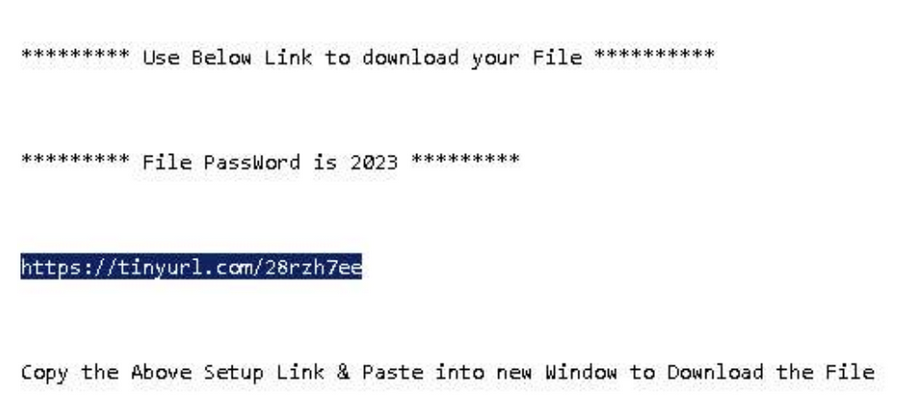
These websites promote “100% working product keys” and serial numbers. When a victim visits one of these malicious URLs a text file is provided that prompts the user to visit a TINYURL link with a download to the malicious binary.
Dark Web
Sellers & Origins
LummaStealer is being sold widely across numerous Dark Web and hacker forums. While researching Lumma, the VMware Carbon Black team discovered that there are several sellers for this malware. While we cannot definitively say how many sellers there are, at the time of research our team found several seller accounts that go by “LummaStealer”, “LummaC2”, “Lumma”, “Lumma Stealer”, “Lummaseller126”, and “lummanowork”. Some of these accounts may be run by the same person or group.
For example, “Lumma Stealer” is seen posting their contact as @LummaStealer126. They also may be related to “LummaStealer” given they use the same avatar on different sites and use the same verbiage. Both accounts appear to be a developer for the malware as they post several updates regarding it. While the account “lummanowork” appears to be for troubleshooting and for assistance addressing bugs with their malware.
In one post on a seller forum, a user asks for the seller to confirm the legitimacy of the account to which “LummaStealer” confirms the existence of verified sellers and partners and advises that there are fakes out there as well:
The account “LummaStealer” is also responsible for posting several updates about the malware – the most important of which is how the malware is being detected by antivirus (AV). In the latest update, the seller shows that all AV (including Windows Defender) is showing their malware as clean.
We believe that this malware is Russian in origin. Aside from the malware being sold primarily on Russian hacker forums, another key indicator that this malware originates from Russia is that the tool only supports the Russian language:
Lumma Updates
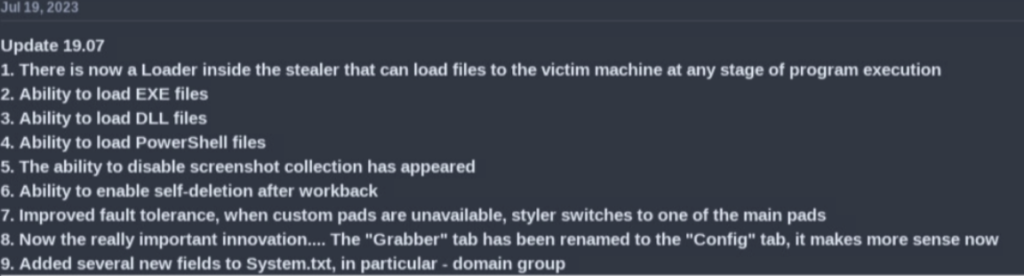
Since its launch, there have been several updates to this malware. Many updates to the malware have been released within the last few months strengthening the malware in its capabilities and stealth. One of the more recent updates includes a loader provided inside LummaStealer:
This takes the malware from being a stealer type to a more devious malware that can load second-stage attacks on its victims. The loader provides a way for the threat actor to escalate its attack from data theft to anything up to infecting its victims with ransomware.
Another powerful update provides the threat actor a way to randomly generate a build for LummaStealer providing obfuscation and making it harder for an AV to be able to detect the malware on hashes alone. It should be noted that once this malware is discovered in an environment or detected by AV, a new build will be required to retain obfuscation.
Carbon Black and its products, like Managed Detection and Response, do not rely on hashes the same way traditional AVs do. While traditional AVs are focused on pre-exploit alone, Carbon Black is focused on pre and post-exploit defense making Carbon Black more effective at detecting malware like LummaStealer, stopping the attack, and containing the infection.
In-The-Wild-Attacks
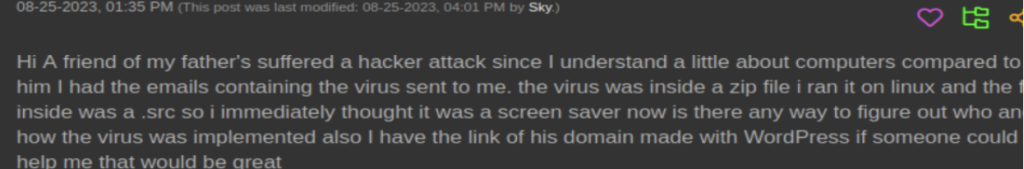
As Lumma is sold as malware-as-a-service, the potential for attack delivery and its associated C2 domains can vary wildly. One of the attack methods discovered was through the download of a screensaver. The zip file of the screensaver the victim downloaded contained several DLLs and references to malicious URLs. These sites would then drop the actual LummaStealer.
Above is a screenshot of someone asking for help after an infection of LummaStealer. Below is a screenshot of the file source:
As mentioned, the download and its C2 domains can vary based on the attacker. For intelligence tracking, we have provided several of the hashes and domains that we have seen to be a part of Lumma attacks in the wild below:
Hashes:
- ae282aecde2e74cadc73ee114e6760959686dc5ee99c608e5e4047766b5137d1
- 9f59fa8bfc22e7f8eeb0aabf9ccea130eecd3a825822abd5e8e5347ba0c1402d
- Bc3a6e84e41faeb57e7c21aa3b60c2a64777107009727c5b7c0ed8fe658909e5
- 2e204c673fb342d5b0472a765ce8576487d83ed25957365f9df744d12ac04893
- 96f35b8f39ac3630a9c58f2621bb0cfce873b69c5a1c2a40612130076e07a533
- 203cb15f8c2bf45792e72bf75366e3eacf563a7470c66acce935c15f498c1806
Domains:
- Safvo[.]com
- Dbdesing[.]com
Attack Chain & Threat Intelligence
It should be noted that because LummaStealer is a malware-as-a-service, each attack will be unique according to how the attacker configures the malware. Given the malware’s custom capabilities, IOCs will have different naming conventions, domains contacted, and distinct artifacts.
In the attack chains Carbon Black observed, the LummaC2 stealer payload was delivered via a succession of loaders closely resembling the sequence noted by Rapid7: The victim initially downloads a fake Chrome browser update which results in the download of the IDAT loader for the first time. The IDAT loader then infects a series of legitimate processes and, ultimately, downloads and executes the LummaC2 stealer.
Delivery
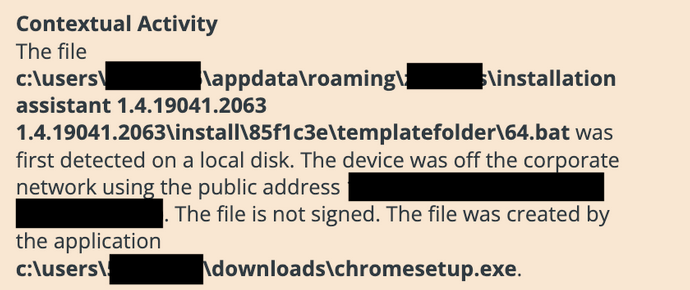
The attacker gains initial access to the victim’s system when the victim downloads a fake Chrome browser update, chromesetup.exe. This chromesetup.exe file claims to be published by “Paramount Software UK Ltd” and does not have a valid signature. Once downloaded by the victim, this fake chrome update drops several files into a new “Ziaozius” directory within the “c:\users\<user>\appdata\roaming” file path. Included in these dropped files is an installer, installation assistant 1.4.19041.2063.msi, a file with a .tmp extension, and a script, 64.bat. The “installation assistant” MSI package is then silently installed using the following command:
“C:\Windows\system32\msiexec.exe” /i “C:\Users\<user>\AppData\Roaming\REDACTED\Installation Assistant 1.4.19041.2063 1.4.19041.2063\install\85F1C3E\Installation Assistant 1.4.19041.2063.msi” /quiet /qn /norestart AI_SETUPEXEPATH=C:\Users\<user>\Downloads\СhrоmеSеtuр.exe SETUPEXEDIR=C:\Users\<user>\Downloads\ EXE_CMD_LINE=”/exenoupdates /forcecleanup /wintime <timestamp> ” AI_EUIMSI=””
Following installation, the .bat script then invokes cmd.exe, which invokes powershell.exe. PowerShell runs the following command to download and silently install a second MSI package, DirectX12AdvancedSupport.msi, from the ocmtancmi2c5t[.]life domain which resolves to /172[.]67[.]205[.]82:
IDAT Loader
The IDAT loader files are contained in the downloaded DirectX12AdvancedSupport.msi package. The “IDAT” name originates from the loader’s use of a PNG file format’s IDAT chunk to store its payload. The loader consists of a DLL, an executable, and a PNG. These three files can change between instances of the loader – potentially as a method to evade detection – but they appear to always adhere to the following pattern:
- The executable is a signed, legitimate file that is vulnerable to DLL load order hijacking
- The DLL file impersonates a legitimate DLL required by the executable but, in fact, contains malicious code
- The PNG file contains an XOR encoded payload within its IDAT chunk
In a slight deviation from previously analyzed versions of the IDAT loader, Carbon Black noted a new executable and DLL pairing packaged in one version of the MSI. Additionally, a .mov file extension was used to disguise the malicious PNG file, a technique that also differed from other attacks. This particular version of the MSI package contained a legitimate InstallShield Setup Suite Launcher executable file, suiteappxhelper.exe, published by Flexera, a malicious version of the Microsoft Windows xmllite.dll, and a PNG file with a .mov extension – samarskite.mov.
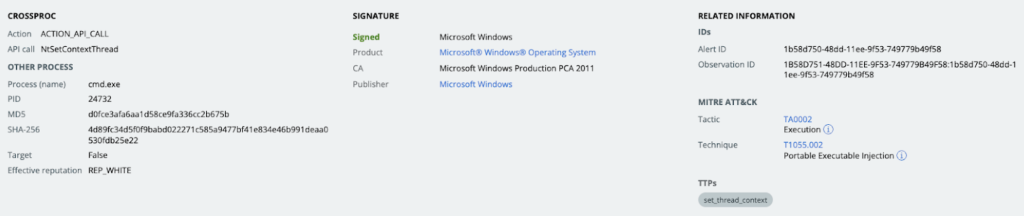
While the contents of this MSI package were unique, the loader’s behavior remained the same. The IDAT loader behavior Carbon Black observed aligns with Rapid7’s earlier findings. DLL load order hijacking is used to load the malicious DLL into the legitimate executable (in this case the InstallShield launcher) and co-opt it. Once the malicious DLL is loaded, it decodes the payload contained in the PNG file and injects the decoded payload into another DLL, mshtml.dll. The mshtml.dll code is loaded into a second instance of suiteappxhelper.exe, and once it’s executed, it creates and injects into a cmd.exe process.
LummaC2 Payload
The injected cmd.exe creates a file with a randomized name in the c:\users\<user>\appdata\local\temp path. The cmd.exe process then invokes conhost.exe using “conhost.exe \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1” – this technique will run conhost.exe in legacy mode and connect it with the first available console session regardless if attached to a physical console. Second, cmd.exe injects the LummaC2 payload into explorer.exe using the technique of process doppelgänging.
Once injected into, explorer.exe collects environment information, modifies several registry keys, and attempts to reach out to a command and control server to pull down the final payload.
We’ve seen the following domains and IP addresses contacted in this final stage:
- lindodeusercontent[.]com
- fibrodoorsbig[.]xyz
- doorblu[.]xyz
- lpsserversonlene[.]xyz
Carbon Black Detection
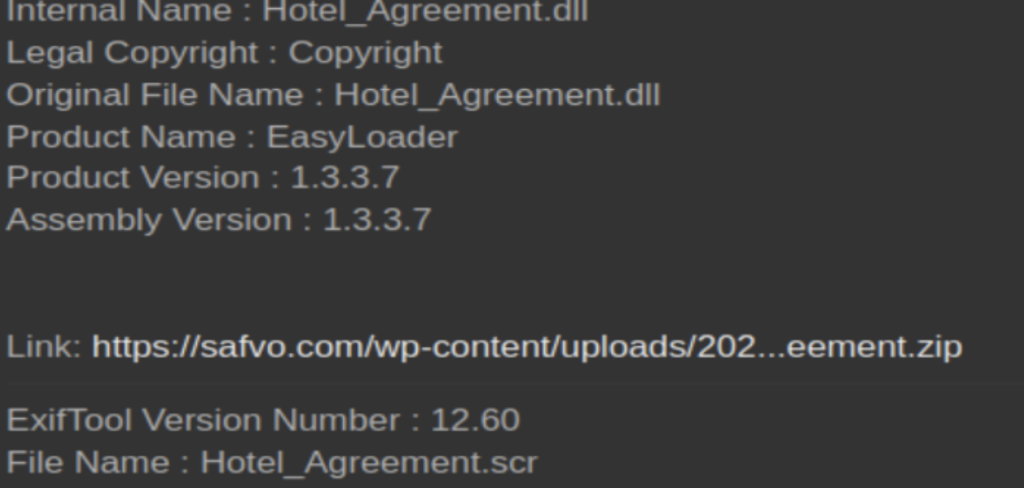
LummaStealer has been observed by Carbon Black with attacks all at different stages. We observed a more advanced stage of the LummaStealer attack, a malicious copy of chromesetup.exe was seen dropping the batch file 64.bat. This copy of chromesetup.exe was observed with the publisher “Paramount Software UK Ltd”.
Figure 1. Chromesetup.exe creates 64.bat
Threat actors commonly use batch files to execute various commands, disable security features, deliver payloads, modify systems, or conduct phishing attacks. In this instance we see 64.bat being dropped to invoke cmd.exe. This in turn invokes powershell.exe. Powershell.exe and cmd.exe are used in Windows environments to run commands or scripts to get programs to run in certain ways or to output certain information (such as OS version or users in an environment).
Figure 2. 64.bat invokes cmd.exe
It is then observed that powershell.exe runs the command that downloads the malicious MSI dropper named DirectX12AdvancedSupport.msi from a remote server, ocmtancmi2c5t[.]life, and saves it as C:\ProgramData\DirectX12AdvancedSupport.msi.
DirectX12 is a Windows application and is normally updated through Windows Update and should be found in the file path C:\Windows\System32. In another observed event, the PowerShell command connects to the remote server, ocmtancmi2c5t[.]xyz, to download the malicious application which was observed as DirectX12AdvancedSupport.msi as well.
Figure 3. Alert Triage tree
Figure 4. Powershell.exe downloads DirectX12AdvancedSupport.msi from ocmtancmi2c5t[.]life
The command then checks if the file is fully downloaded and, once verified, silently installs the MSI package on the system using “msiexec.exe /i”. Keep in mind that the MSI dropper can be named whatever the threat actor wants, but in this instance, it is named DirectX12AdvancedSupport and is not associated with DirectX whatsoever.
PowerShell Command:
In another attack, it was seen that a C2 server was set up as doorblu[.]xyz. A C2 server is normally set up by a threat actor in an attempt to create persistence, to launch their attacks, and to even exfiltrate data. In this event, there were no observations of any data being exfiltrated or any other use of the C2 server – only that it was set up.
Below are the indicators of compromise (IOCs) that Carbon Black has witnessed and some of the search queries that can be used to find artifacts of the attack in an environment using the Carbon Black Cloud. Hashes for the common IOCs can also be searched for, if they are available.
Indicators of Compromise:
| Name | SHA256 Hash |
| Chromesetup.exe | c9094685ae4851fd5a5b886b73c7b07efd9b47ea0bdae3f823d035cf1b3b9e48 |
| Chromesetup.exe | bd3ae41147c48bcea273f742ae19c229ad76c4a75895253e01a58bd4f3c2b9d1 |
| directx12advancedsupport.msi | 1d3978ca6fd781808dd7cea4cc31e622324a1f0ababd5020f597d2fcc9d378fd |
| directx12advancedsupport.msi | 3f379d60adb6c22a38ab81052458d7ced3361185d92ea7afe6d7b5d812080b95 |
| 64.bat | 407fb7c6accf306c766ccb68fb2247d3340fe5363cf991d16613af2ea46f8d0c |
| Domain: | |
| ocmtancmi2c5t[.]life | |
| ocmtancmi2c5t[.]xyz | |
| Doorblu[.]xyz |
Search Queries:
- process_name:powershell.exe AND ((process_cmdline:.msi AND process_cmdline:.getresponse AND process_cmdline:.contentlength AND process_cmdline:.downloadfileasync) OR (fileless_scriptload_cmdline:.msi AND fileless_scriptload_cmdline:.getresponse AND fileless_scriptload_cmdline:.contentlength AND fileless_scriptload_cmdline:.downloadfileasync))
- netconn_domain:ocmtancmi2c5* OR doorblu* OR (process_cmdline:ocmtancmi2c5* OR doorblu*)
Summary
LummaStealer, a malware-as-a-service, varies widely in attack potential and command-and-control domains. A new update allows random generation of LummaStealer builds, enhancing obfuscation, and complicating detection by traditional AV software relying on hashes. Due to its customizable nature, each LummaStealer attack differs leading to unique indicators of compromise including naming conventions, contacted domains, and specific artifacts.
Carbon Black adopts a different approach, focusing on both pre and post-exploit defense. This strategy proves more effective against LummaStealer, ensuring detection, prevention, and containment.
Carbon Black is particularly effective against LummaStealer due to its innovative approach to endpoint security. Unlike traditional antivirus (AV) solutions that rely solely on static signatures or hashes to detect malware, Carbon Black utilizes advanced techniques and behavioral analysis for threat detection. Here’s why Carbon Black is a superior endpoint protection to use against LummaStealer:
- Dynamic Detection Methods: Carbon Black employs dynamic detection methods, such as behavioral analysis and machine learning algorithms, to identify malicious behavior patterns. This proactive approach allows it to detect new and evolving threats such as LummaStealer even when their specific signatures or hashes are unknown.
- Focus on Pre and Post-Exploit Defense: Carbon Black focuses on both pre-exploit and post-exploit defense. While traditional AVs primarily concentrate on pre-exploit measures, Carbon Black also monitors activities after a potential breach. This comprehensive approach enables it to identify and mitigate LummaStealer’s malicious activities throughout the attack lifecycle.
- Adaptability to Unique Attacks: LummaStealer, being a malware-as-a-service, allows attackers to customize their attacks resulting in unique configurations for each instance. Carbon Black’s adaptive and behavioral analysis can recognize these custom configurations and detect LummaStealer variants regardless of the specific parameters set by the attacker.
- Containment Capabilities: Carbon Black not only detects malware but also offers effective containment measures. When LummaStealer is detected, Carbon Black can isolate the infected system preventing the malware from spreading further within the network. This containment feature helps prevent widespread damage and data breaches.
- Continuous Updates and Threat Intelligence: Carbon Black continuously updates its threat intelligence database, incorporating information about emerging threats and attack techniques including those used by LummaStealer. This up-to-date knowledge enhances its ability to recognize and thwart the latest variants of the malware.
- Adaptive Response: Carbon Black’s Managed Detection and Response products provide an adaptive response mechanism. In the event of a LummaStealer attack, it can respond dynamically, adapting its defense strategies based on the evolving threat landscape. This adaptability is crucial in dealing with constantly changing malware tactics.
- Managed Threat Hunting: Carbon Black’s newly released Managed Threat Hunting product provides proactive threat hunting on emerging threats. The Managed Threat Hunting product’s unique approach to detection and response allows it to quickly detect and respond to threats, including LummaStealer.
In summary, Carbon Black’s advanced, dynamic, and comprehensive approach to threat detection and response makes it highly effective against LummaStealer and other sophisticated malware threats. Carbon Black’s ability to adapt, analyze behavior, and contain attacks sets it apart as a robust solution in the fight against evolving cyber threats.