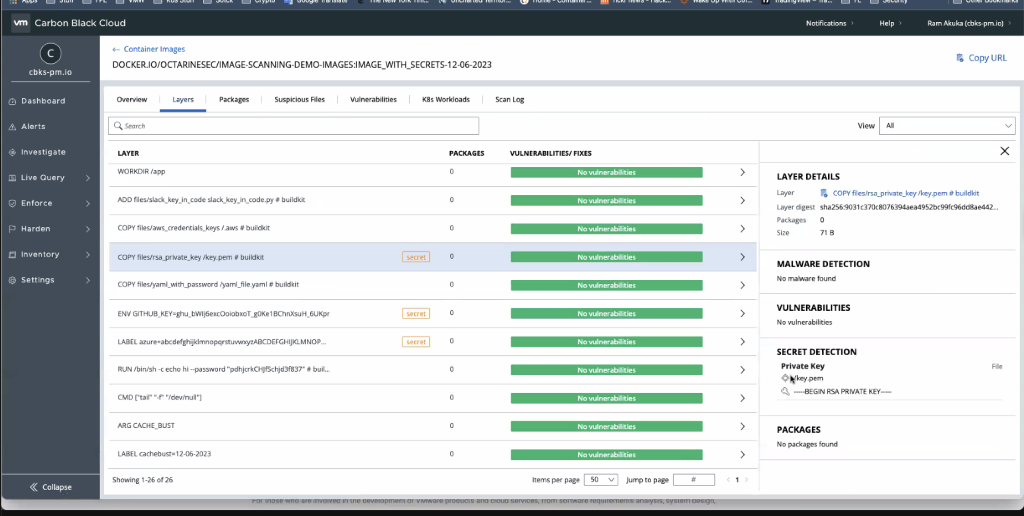
As organizations continue to adopt containers and Kubernetes for their applications, the need to secure these containers becomes increasingly important. Many applications are built with third-party sourced components from public image registries. Attackers are privy to the growing use of these third-party image registries, and often target them with malware, thus requiring special attention. Additionally, backdoors can be hidden in images, allowing the attacker to have access after the image is deployed.
When it comes to securing your data, “secrets” usually fall under a few categories:
- Passwords
- Database Keys
- External APIs
- Cloud Keys
- Code Repo Credentials
Not only is secret detection an important part of your container security strategy but it is crucial to keeping sensitive data out of the hands of attackers. Typically, attackers have a specific secret in mind and these secrets are exposed due to errors early in the development lifecycle. Developers may take a file with a specific password, and accidentally bake that entire file in with the container image. Thus, the password file is unencrypted and gets exposed. But what are attackers doing with these secrets once they are exposed? Here are two scenarios that can happen if an attacker gets a hold of cloud credentials and keys.
Cloud Keys Compromised
Cryptomining is one way that attackers are exploiting these secrets. For example, if an attacker is on the hunt for AWS credentials, and then can find those credentials in the specific pod, they can start deploying resources to the organization’s cloud and drive up a large cloud consumption bill before getting shut down. Another example is
Although dwell time is a much different scenario, it can be just as detrimental to an organization. For example, many organizations have AWS regions set up all over the world but may use significantly more resources in certain regions than others. If an attacker were to get a hold of these AWS credentials, they could set up a small environment using a small number of resources and go undetected for a long period of time, all while stealing information, spreading malware, or carrying out a plethora of other harmful attackers.
Secrets can also be exposed with no ill intent but rather just from plain human error. Oftentimes, a secret is exposed because someone was in a hurry and left the secret in plain text or accidentally baked it into the image itself.
New Secret Detection Capabilities
In order to stop these secrets from being exposed, whether from attackers or human error, security teams and development teams need the right tools and practices in place to secure the entire application lifecycle. With VMware Carbon Black Container, customers can now scan all executable files in their containerized applications to detect secrets. This adds to the existing image scanning and malware detection capabilities available to Carbon Black Container customers.
Users can now:
- Detect secrets throughout the entire application lifecycle
- Create and manage policies that prevent secrets from being exposed
- Alert or block containers and workloads with exposed / non-encrypted secrets
- Use the image scan log to review all scan activities, including file reputation scan information for all scan types
Additional Resources For more information, check out our technical release notes and the VMware Carbon Black Container page.