While the evolution of ransomware techniques is to be expected, the speed at which the Royal Ransomware Group has been able to adapt is impressive. Since it was first reported, those responsible for Royal ransomware have advanced quickly over a short period of time, leveraging old and new techniques as well as exploiting novel vulnerabilities as they are discovered. In just the last six months, they have rapidly escalated attacks targeting victims across numerous industries and countries.
The Royal Ransomware Group has also leveraged evasion techniques such as Virtual Instances [1], which made it challenging for defenders to prevent encryption once the threat actor had gained access to the targeted victim environment. Interestingly, some of the attributes were reminiscent of an older 2020 sample of Conti ransomware. External research by Vitali Kremez from AdvIntel has stated a direct relationship between Conti and Royal ransomware [2]. Comparing a recent Royal sample against Conti’s and other Royal ransomware variants over the past six months could provide insight into the threat actors’ future activity.
Who is Royal Ransomware?
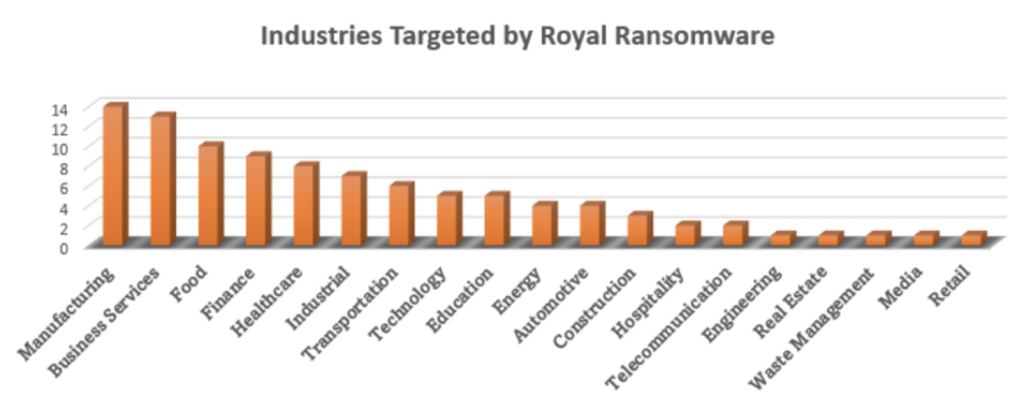
Initially identified as Zeon in January of 2022, Royal ransomware has been rebranded as “Royal” since September of 2022 [3]. Since then, they have targeted companies across numerous industries such as Manufacturing, Healthcare, Food, and Education. Although over 60% of targeted companies have been in the United States, the Royal Ransomware Group has not shied away from targeting countries around the world including Europe and Latin America.
Figure 1: Graph of Industries Targeted by the Royal Ransomware Group collected via their Leak Site from September 2022 – February 2023.
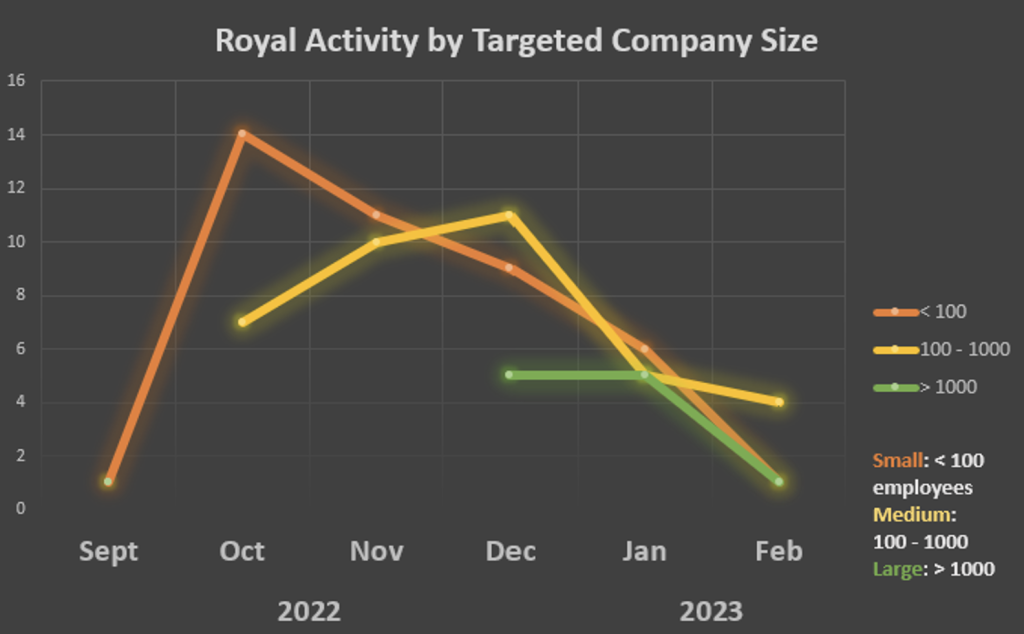
Over the past six months, the Royal Ransomware Group has targeted both small and large companies. In December of 2022, there appeared to be a clear pivot to targeting larger companies and a steady decline in targeting smaller organizations. There has also been an overall decline in the number of reported attacks in the first quarter of 2023.
Figure 2: Line Chart summarizing the Size of Targeted Companies collected via their Leak Site from September 2022 – February 2023.
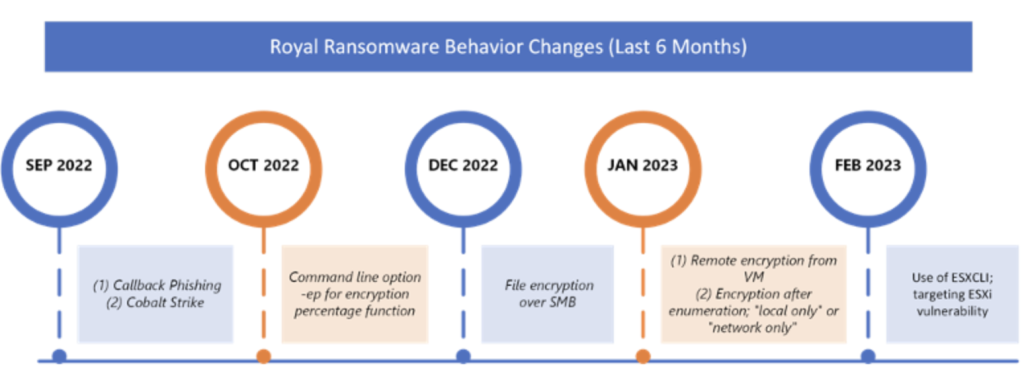
With each new variant of Royal ransomware since September comes different techniques and features, old and new such as:
- Callback phishing (BazarCall) [3]
- File encryption over SMB
- Expansive LOLbin utilization
- Rapid abuse of new vulnerabilities such as CVE-2022-27510 [4]
- Leveraging popular malware and tools such as Qbot, Batloader, Cobalt Strike, etc.
Figure 3: Timeline of major changes observed with Royal ransomware over the last six months as reported by security researchers [3] [8]
A Royal Delivery
VMware Carbon Black’s Threat Analysis Unit (TAU) recently investigated a Royal ransomware attack leveraging file encryption over SMB. The threat actor was able to gain access to a customer’s environment and remotely encrypt files across five devices. Unlike what has previously been seen by the Royal Ransomware Group [5], the threat actor did not disable the antivirus/EDR and did not delete volume shadow copies. These actions may have been omitted to avoid alerting any sensors or to avoid being blocked, but it is important to consider that the sample itself has the ability to delete volume shadow copies.
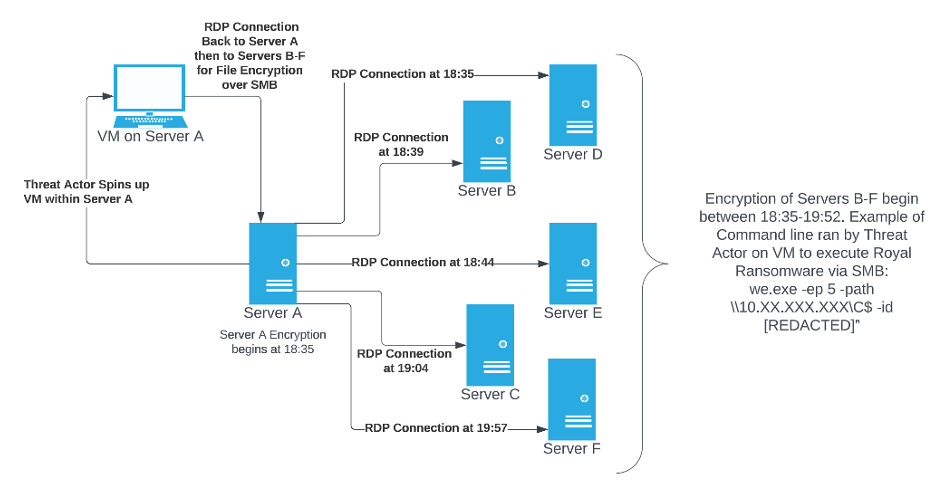
To begin, Carbon Black was informed that the threat actor gained access to Server A and spun up a Virtual Machine (VM). From that VM, they successfully connected back to the host device via SMB as well as five additional servers.
Figure 4: Diagram summarizing the flow of events in the Royal ransomware attack in the customer environment.
Shortly after gaining access to each server, the remote file encryption began. Royal ransomware must be executed via command line by a threat actor actively within the target environment. To remotely encrypt a server, the threat actor uses the IP address and targeted drive in the command line as shown:
[RansomwareName].exe -ep 5 -path \\XXX.XXX.XXX.XXX\C$ -id [32 char string]”
This activity masquerades as routine system activity. Additionally, with the threat actor using a newly created VM without a sensor installed, some malicious activity on the device could go undetected.
Conti Ransomware in Retrospect
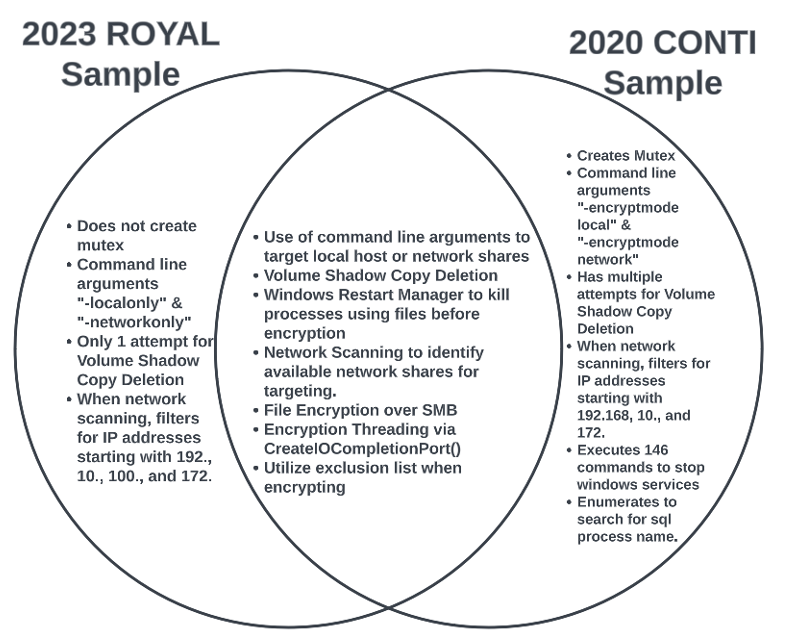
The investigated Royal ransomware attack revealed features previously identified in Conti ransomware [6]. Like Royal ransomware, Conti is designed to be executed by an adversary monitoring the environment. In 2020, it used a similar command line execution to target local drives, network shares, and even specific IP addresses. Upon deeper analysis, there are numerous similarities that were seen between this 2020 Conti sample and our 2023 sample of Royal ransomware.
Figure 5: Venn Diagram comparing the 2020 Conti sample with 2023 Royal ransomware sample [6]
Of the similarities, the most notable would be the use of:
- Encryption threading to speed up encryption
- Windows Restart Manager to kill processes using files before encryption
- Network scanning to identify network shares for encryption
- Filtering IP addresses to reduce noise
- File encryption over SMB
- Command line execution with the ability to specify local or network only
One of the key differences was the fact that the 2020 Conti sample was highly obfuscated using a Conti mutex and unique encoding strings for API resolution, while the 2023 Royal sample did not have a mutex and often had commands in clear text. This could be due to the Conti source code leak leaving no need to spend cycles obfuscating the code if it is already public.
Where is Royal Now?
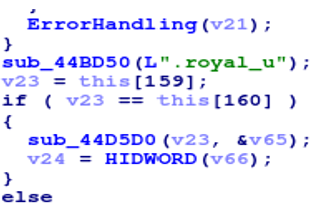
Compared to a sample [7] seen in late 2022, our sample of Royal ransomware had extra features to include two additional command line arguments, two additional file extensions to avoid, and a modified royal file extension to append to encrypted files. The command line arguments that were added, “-localonly” and “-networkonly”, allowed the user to specify whether to target the local host or scan and target network shares instead of relying on a specified path.
Figure 6: Screenshot of addition of command line arguments
The avoided file extensions identified were “.royal_w” and “.royal_u”. The extension “.royal_w” was used to append to files after encryption, while the purpose of “.royal_u” was not yet understood. In the past Royal ransomware appended encrypted files simply with “.royal”, while the new sample used “.royal_w”. It’s possible this change was utilized to evade detection in the case a rule had been written based on previous indicators.
More recently, a new variant [8] has been identified targeting Linux ESXi servers. Compared to our sample, this new variant appended encrypted files with the “.royal_u” file extension, which was foreshadowed in our sample. Replacing the “-localonly” and “-networkonly” command line arguments with new arguments such as “stopvm” and added more file extension exclusions.
Figure 7: Screenshot of .royal_u extension used by the Linux Variant being foreshadowed in our sample
Detecting a Constantly Evolving Threat
It is clear that the Royal Ransomware Group is comfortable with quickly adjusting and evolving its ransomware to fit its target’s environments. With three different variants in just three months, the importance to stay aware of these changes to ensure proper detection is paramount.
When executed locally, Royal ransomware is successfully blocked in the Carbon Black EDR product via Default Ransomware Policies for sensor versions 3.7 and up. However, in the case of File Encryption over SMB or executing via a virtual machine, EDR products may not have full visibility into portions of the network activity.
The Endpoint Standard product receives updates for known malicious hashes and blocks all types of Known or Suspect malware files from executing through behavioral analysis. While the initial execution may be able to circumvent detection via a virtual machine, it is likely that when the malware runs, it will trigger additional alerts that are indicators of a more complex attack. This is a good reminder to ensure your network has detection capabilities across the entirety of the environment so that even if some undetected malicious activity does occur, it will still be blocked when threat actors attempt actions external to that device.
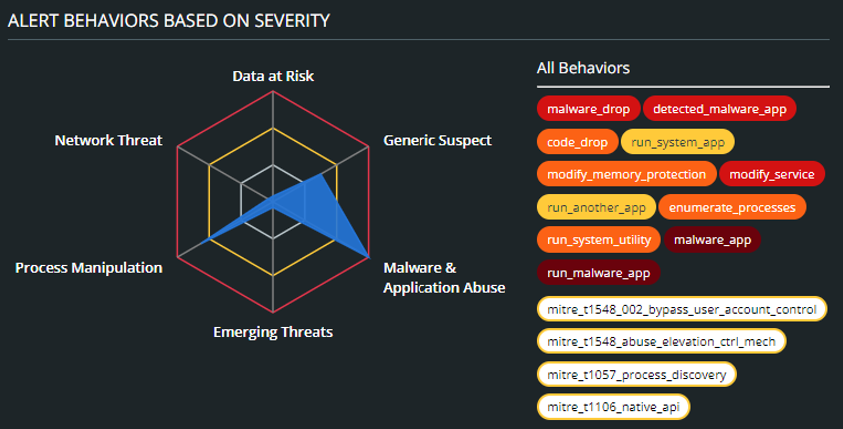
With evolving threats like these, products like VMware Carbon Black’s Managed Detection and Response (MDR) can be the difference between a fully encrypted network or a contained threat and adds a much-needed human element that can react with the ever-changing environment on a daily basis. The MDR team is comprised of highly trained analysts that specialize in post-exploitation defense. The team tracks technique changes and fulfills a crucial gap between sensor and hash reputation updates, as well as dramatically reducing the turn-around time for detecting emerging threats. For Royal Ransomware in particular, the MDR team has leveraged the insight gained through our wide customer pool to automate queries for proactive threat hunting which has helped customers contain the threat early during the initial infection, drastically minimizing network impact and preventing data exfiltration.
Figure 8: Screenshot of Carbon Black Console Summary of Alert Behaviors
Conclusion
Although it is expected for the threat landscape to continue to evolve over time, Royal Ransomware has shown that it is particularly worth keeping an eye on the threat actor in this case. With victims targeted across numerous industries and countries, the Royal Ransomware Group has demonstrated their ability to be pervasive, resourceful, and creative with their implementations. The use of old and new techniques, and now expanding their sights to Linux, Royal Ransomware has vastly increased its potential targets due to these developments. It would be no surprise, if not expected, for more adaptations in future variants to occur.
In fact, upon finishing our investigation our team detected new techniques in a more recent Royal ransomware variant that fellow researchers at Red Canary [10] had previously noted in 2018 involving a signed Microsoft binary called MSXSL.
Yara Rule
| rule royal_note_cmdln_fileext
{ meta: author = “Carbon Black TAU” //bdana & snyderd date = “2023-Feb-28” description = “Identifies Royal Ransomware Variant with -localonly and -networkonly options available for command line execution” rule_version = 1 yara_version = “4.2.0” exemplar_hash = 972429ab773f3f31180430f6fedc8b93b43f0f8d49b9e2d0ef22ac8589744648 strings: $ransom_note = “If you are reading this, it means that your system were hit by Royal ransomware.” ascii wide $cmdline_1 = “-path” ascii wide $cmdline_2 = “-id” ascii wide $cmdline_3 = “-ep” ascii wide $cmdline_4 = “-localonly” ascii wide $cmdline_5 = “-networkonly” ascii wide $file_ext_1 = “.royal_u” ascii wide $file_ext_2 = “.royal_w” ascii wide condition: all of them } |
References
[1] Hide Artifacts: Run Virtual Instance, Sub-technique T1564.006 – Enterprise | MITRE ATT&CK®
[3] Ransomware gangs move to ‘callback’ social engineering attacks
[4] Royal ransomware spreads to Linux and VMware ESXi
[5] Royal Ransomware Deep Dive | Kroll
[6] TAU Threat Discovery: Conti Ransomware – VMware Security Blog
[7] Royal Rumble: Analysis of Royal Ransomware
[8] Royal Ransomware Expands Attacks by Targeting Linux ESXi Servers
[9] New Royal Ransomware emerges in multi-million dollar attacks
[10] Detecting MSXSL Abuse in the Wild