Detect Malware in Container Images
As organizations continue to adopt containers and Kubernetes for their applications, the need to secure these containers becomes increasingly important. Many applications are built with third-party sourced components from public image registries. Attackers are privy to the growing use of these third-party image registries, and often target them with malware, thus requiring special attention. At VMware, we define malware as the broad category name for harmful code used in cyberattacks that affect laptops, desktops, servers, mobile devices, and, more recently, IoT devices. Some of the most common examples of malware include:
- Viruses
- Bots
- Ransomware
- Cryptomining
When using malware, attackers typically have a set target and goal in mind and use malware as a mechanism to gain access and/or information.
As malware continues to pose a huge risk when developing new modern applications, organizations must scan these images for these specific types of attacks from build to run to ensure the security and integrity of their application.
Malware Scanning with VMware Carbon Black Container
With VMware Carbon Black Container, customers can now scan all executable files in their containerized applications to detect malicious files and malware. Just like vulnerabilities and Kubernetes workload
posture, users can now scan images for malware at runtime and in the build phase through CI/CD integration.
Users can now:
- Detect suspicious files in all containerized applications
- Alert or block containers and workloads with suspicious files during CI/CD pipeline
- Use the image scan log to review all scan activities, including file reputation scan information for all scan types
- Deny workload and images affected by malware through a policy
- Manage a list of customer-provided hash of known malware to utilize CBC enforcement capabilities
Increased Visibility
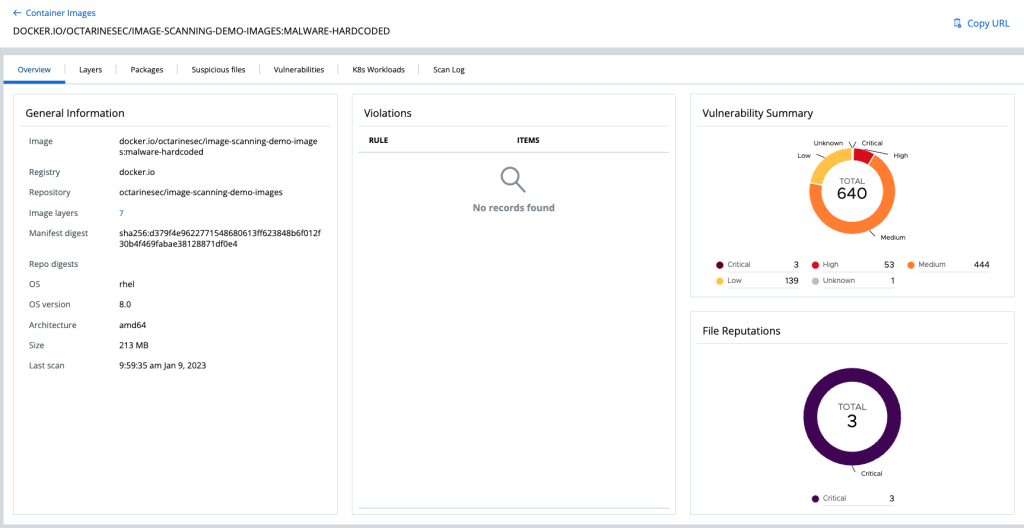
Figure 1: Updated Widgets on the Image Scanning Dashboard
With the updated image scanning dashboard, users can analyze and detect all relevant files in a given container for the first time. This newly added malware widget enables users to quickly identify suspicious files alongside critical vulnerabilities so they can be remediated as quickly as possible. This valuable and actionable data can be viewed across teams in the VMware Carbon Black dashboard, helping to increase visibility and reduce friction.
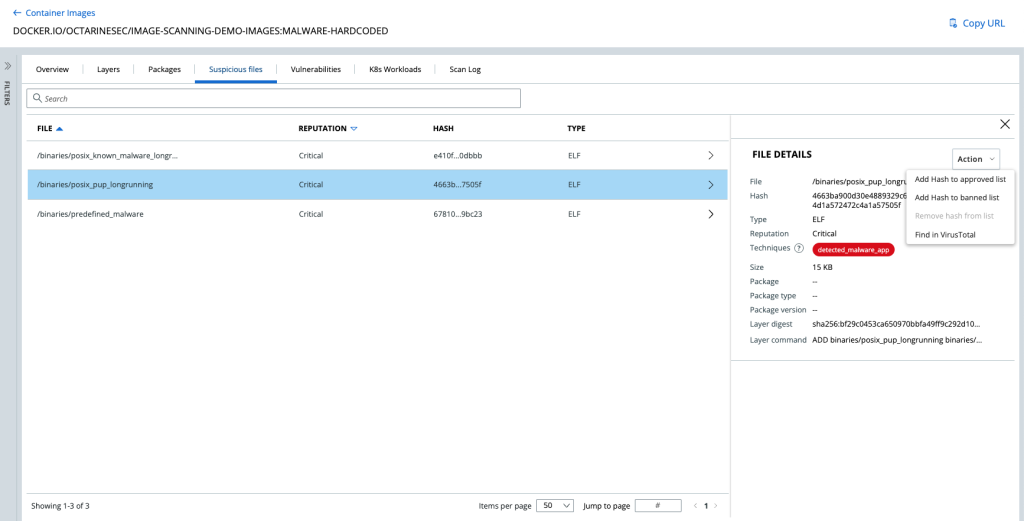
Figure 2: New Suspicious Files Tab with Identified Malware
The new malware scanning capabilities allow users to easily identify the origin of the file by identifying the layer and even the command(s) that contain malware for easy resolution.
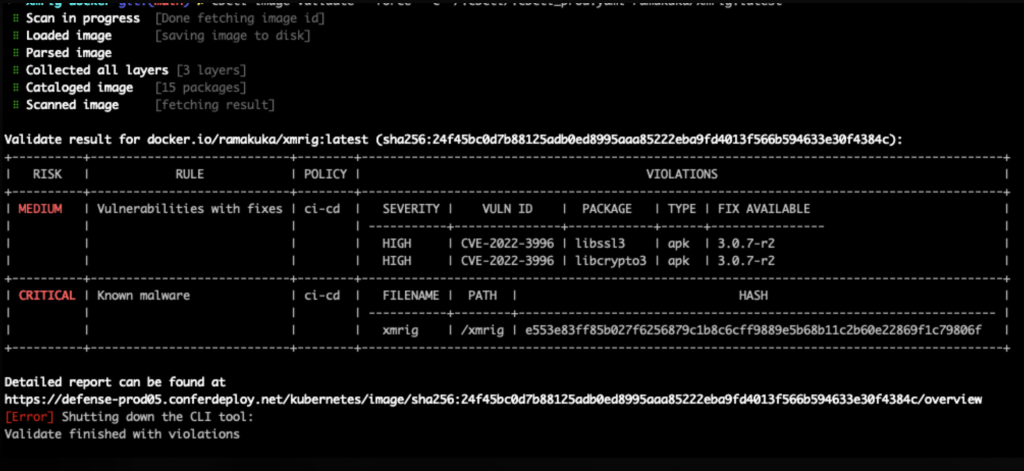
As we know, it is important to catch suspicious activity as soon as possible to remediate and reduce risk. Users are now able to use the cbctl to scan containers during the build phase to detect containers with suspected or banded files and to block risky containers early in the SDLC.
Additional Resources For more information, check out our technical release notes and the VMware Carbon Black Container page.