Why Vulnerability Management and Assessments Matter
Scanning container images for vulnerabilities and misconfigurations is one of the best ways to reduce risk and exploitability. New containers are constantly being spun up by developers, leaving more entry points for attackers. Simultaneously, the same container image may be replicated and used throughout a specific environment. This means that if you have an unsecured image in one area, it can lead to more overall risk. Images need to be both scanned before deployment and scanned in production in order to effectively reduce the risk throughout the application development lifecycle. Whatever tool you are using for vulnerability management, it is important that your scanning tool integrates with your other security tools.
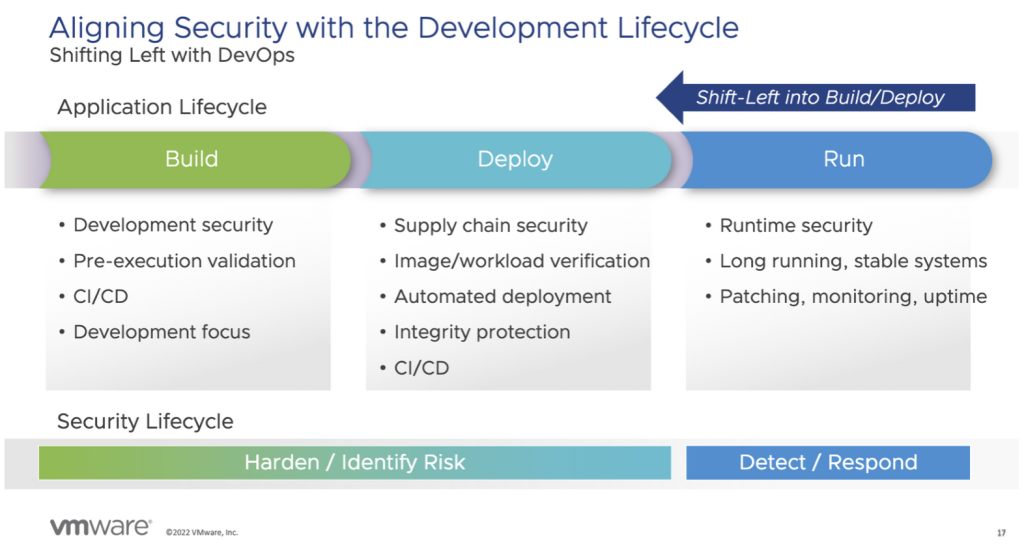
Figure 1: Aligning Security with the Application Development Lifecycle
What is Harbor Registry?
Harbor is a reputable open-source registry server that stores and distributes container images, ensuring images are scanned and free of vulnerabilities. A graduated project of the Cloud Native Computing Foundation (CNCF), this registry includes unique functionalities to help organizations improve performance and security and can be used in any Kubernetes environment.
Introducing Harbor with VMware Carbon Black Container
We’re excited to announce the new integration capabilities between VMware Carbon Black Container and the Harbor image registry. Using the scanning capabilities from VMware Carbon Black Container and leveraging Harbor’s Pluggable Scanner API Spec., this integration enables customers to use Harbor to scan images present in its registry and provide vulnerability reports for those images – directly in the Harbor interface.
Figure 2: easy setup to add Carbon Black as a Scanner in Harbor
Continuous Scanning
VMware Carbon Black Container can help any Harbor user continuously scan and rescan images while providing additional functionalities to enact policies to alert or block running vulnerable images on the Kubernetes level. However, it is important to remember that, while hugely important, vulnerability management is just a small piece of the larger puzzle. With visibility to all the container images in your Harbor registry, you can better protect modern applications from the device to the network, to runtime, stopping threats others can’t, and providing innovative protection for modern applications.
Additional Resources:
To learn more about this integration and how to get started, check out our GitHub page.








