This article was authored by Stephane List, Abby Costin, and Ram Akuka
Container Security Challenges
Vulnerability management has never been more important than it is with cloud-native technologies and containers. While cloud native technology offers agility and innovation, attackers take advantage of some of the risks that come with container adoption. These challenges with container security include:
- A growth in attack surface: It is no secret that there has been an extreme rise in the use of containers in recent years. As with any newer technology, security is often playing catch up to the creative ways attackers exploit containers.
- Ephemeral nature of containers: Not only are containers themselves growing rapidly, but their average lifetime is less than 5 minutes. Development teams are constantly spinning up new containers and releasing them more frequently. This results in more entry points for attackers than ever before.
- The use of third-party image registries: Third-party image registries provide many advantages and benefits for developers. As a result, attackers are finding ways to insert malicious code into the images of these registries
Visibility into Container Images
With these risks, image hardening becomes a key component of your container strategy. Effective container security must address image scanning, both in the CI/CD pipeline and in runtime to understand the overall security posture and manage risk. DevOps and Security teams need to ensure that only approved images that meet their organization’s compliance and security standards are deployed in production. Both teams need a cross-collaborative tool that can:
- Continuously manage vulnerabilities
- Identify images with fixes
- Provide visibility into vulnerabilities over time
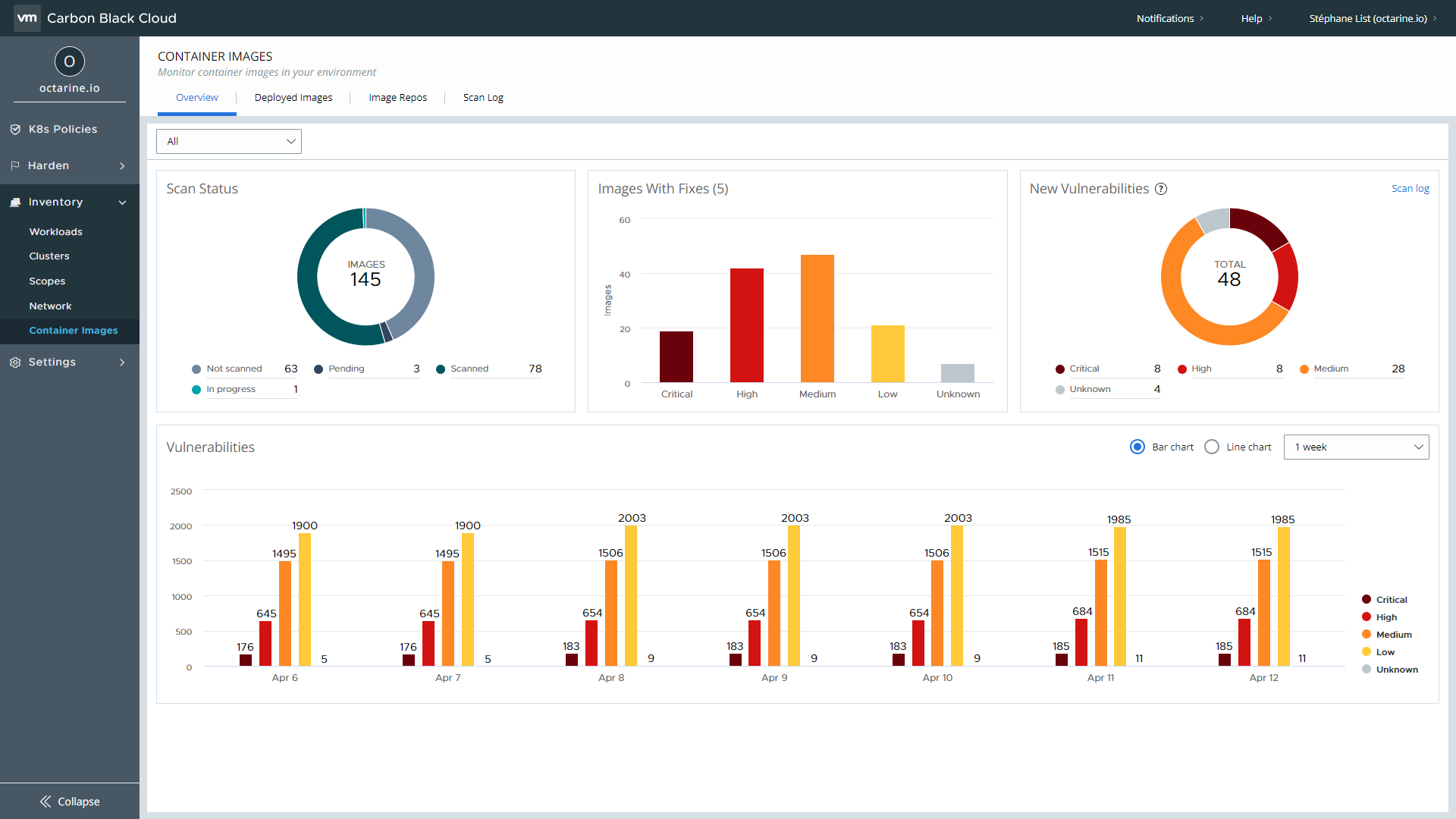
Image Scanning Dashboard
The image scanning dashboard feature in VMware Carbon Black Container helps teams manage and understand the state of vulnerabilities and misconfigurations in their environments. This dashboard provides robust risk prioritization so DevOps teams can focus on the most exploitable and critical risks and close security gaps quickly. Additionally, security teams can easily enforce security standards and compliance by restricting container deployments to prevent running unauthorized workloads. They can automate minimum security standards and compliance requirements to align with security frameworks, such as STIG or CIS to make compliance easier than ever before. With the VMware, security and DevOps teams can:
- Reduce time to resolution
- Increase operational confidence
- Provide future-ready security across multi-cloud environments.
To learn more about everything you need to properly assess image vulnerabilities, check out our latest demo here. For additional information, view the release notes.