This article was authored by Oren Penso and Ram Akuka
It’s no secret that Kubernetes and container adoption has skyrocketed over the last several years, with double-digit growth expected to continue as enterprises increasingly embrace the modern apps transformation. While there are many benefits to leveraging containers and Kubernetes to enable business agility, cloud-native technology introduces its own security challenges.
The rise of containerized microservices combined with the ephemeral nature of containers has resulted in exponential growth of the attack surface, which has not gone unnoticed. Attackers are taking advantage of these additional entry points and the rapidly expanding attack surface. Threat actors and cyber criminals are now creating attacks specifically targeting Kubernetes and container vulnerabilities. In order to effectively combat these new attack vectors, securing the container layer is not enough — we must also secure the infrastructure layer and the Kubernetes layer the workload is running on.
To address these challenges, we’re excited to announce the general availability of Container Runtime Security for VMware Carbon Black Container. Combined with our existing hardening and compliance capabilities, Security and DevOps teams are enabled to secure containers throughout the full application lifecycle — from development to production. Some of the newly released runtime security features include Integrated Alert Dashboard, Runtime Image Cluster Scanning, Kubernetes Network Visibility Map, Network and Workload Anomaly Detection, Egress and Ingress Security and Threat Detection.
Together, VMware Tanzu and VMware Carbon Black are bringing VMware’s deep knowledge and expertise in workloads and security to Kubernetes, to help organizations reduce risk, maintain compliance, and achieve simple, secure Kubernetes environments at scale. With VMware, organizations can implement comprehensive built-in security for a holistic DevSecOps approach – from workloads and pipeline to the infrastructure they run on.
Automate and Customize Vulnerability Assessments for Continuous Compliance
The use of public image registries has become commonplace, and many projects rely on third-party sourced components. Recognizing this trend, bad actors have started attacking these open-source projects to maximize their reach. It is more important than ever to scan these images for vulnerabilities throughout the development lifecycle to ensure images stay secure.
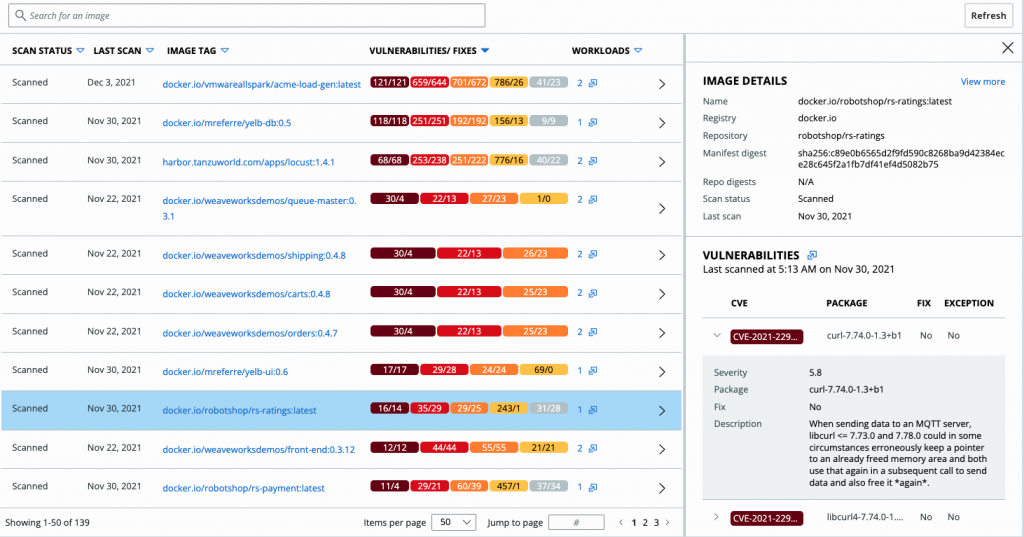
The expanded image scanning feature can now be used everywhere, for every image. Runtime Cluster Image Scanning means that teams are no longer restricted to only images that are going through your CI/CD pipeline and are now able to scan the images through runtime. The ability to carry vulnerability scanning through the runtime layer gives security and DevOps teams visibility to vulnerabilities in images that were not previously scanned, and images deployed from any third-party registries. By giving the user control to customize their scan, security teams can introduce automated, custom policies and be notified when those policies have been violated. Automation is a key component to helping security teams achieve continuous compliance.
Figure 1: Runtime Cluster Image Scanning
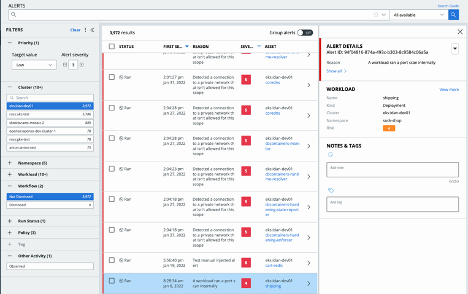
Connect the Dots Between Hardening, Runtime, And Vulnerability Scanning Data
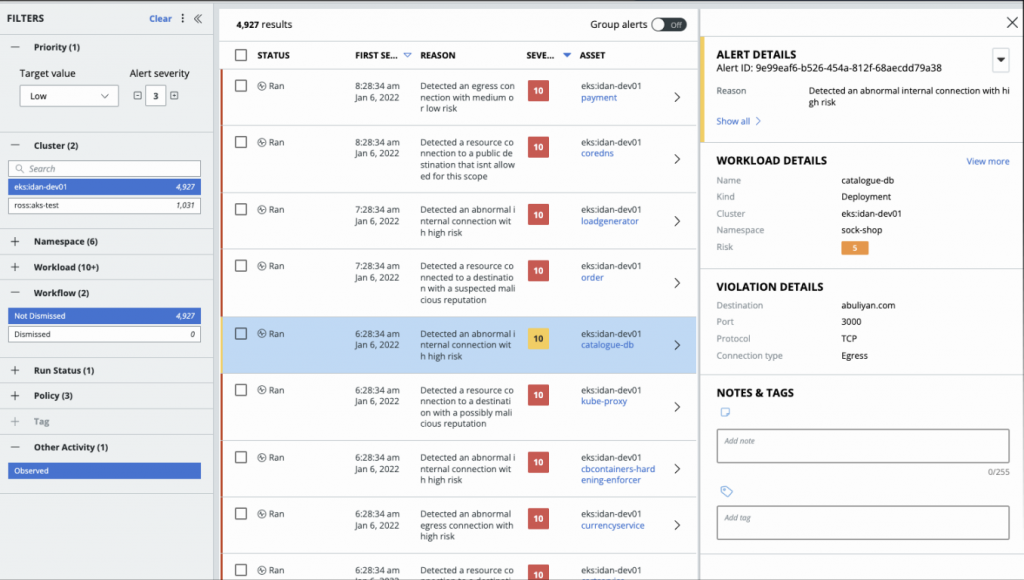
The Integrated Alerts Dashboard provides security teams with a single pane of glass to connect data to help detect and address runtime anomalies. A consolidated view of these events enables better investigation and correlation of different types of events for different types of objects.
Figure 2: Integrated Alerts Dashboard
Increase Visibility into Kubernetes Connectivity
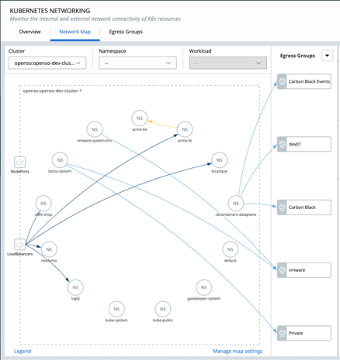
Security teams need the ability to quickly understand the architecture of an application that was set pre-deployment to quickly identify potential workload policy violations and vulnerabilities. The Kubernetes Visibility Mapping feature gives them visibility into the Kubernetes workloads in a cluster, traffic flow between the Ingress entry point, and the internal traffic between workloads and Egress traffic to external destinations. By utilizing this feature, teams can view all the information on the workload vulnerabilities, misconfigurations, and policy violations with risk scores to better mitigate the risk. This sets the baseline for the “best behavior” that is later used for anomaly detection.
Figure 3: Kubernetes Network Visibility Map
Easily Identify Anomalies in Your Kubernetes Clusters
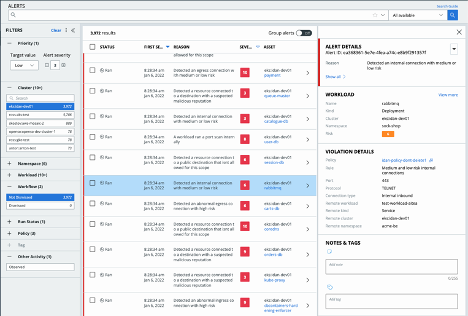
Cloud-native is a declarative, pre-architected way to deploy your applications, so the right behavior is known and easy to visualize. Using AI models and the information from the visibility map feature, you can identify anomalies across the entire networking flow. SecOps teams can use this Workload Anomaly Detection capability to standardize the networking model. After setting the standardized model, the platform alerts on any deviation from that model or any potentially malicious connections. This ability to identify changes and anomalies in the Kubernetes cluster is crucial to identifying active attacks because it gives an instant understanding of malicious activity in the Kubernetes environment.
Figure 4: Workload Anomaly Detection Alert (Internal Connection with Medium Risk)
Visibility into Egress and Ingress Connections and Anomalies
Service-to-service connections (egress) can be used to leak data from the cluster layer. Today, we see attackers using egress connections to mine cryptographic coins to an external wallet. Needless to say, gaining visibility to these egress connections and anomalies, and potential malicious connections has never been more important to spot and stop attacks faster. The new Egress and Ingress Security capabilities allow security teams to quickly understand good behavior and alert the user to any deviations from that good behavior.
Figure 5: Egress Security Alert (Destination with Malicious Reputation)
Quickly Identify Potential Attacks
The Threat Detection capability looks for port scanning activity both internally and externally. This is especially critical in stopping lateral attacks — where an attacker gets initial access into your network environment and then leverages their current access to gain further traction into your network and workloads. Any internal or external port scans will trigger an alert, helping security teams quickly identify port scanning activity and potential attacks.
Figure 6: Threat Detection Alert (Internal Port Scan)
This brings together an end-to-end security solution spanning the entire lifecycle from development through production with enforcement points that span the CI/CD pipeline, container infrastructure, the Edge, microservices network and API layer as well as the container runtime. Our goal is to enable security leaders to enforce the same Zero Trust design principles for secure workload access across their virtualized and modern application deployments.
For more information on this release, register for our webinar, Securing the Container Lifecycle from Build to Run with VMware Security, and check out our technical release notes page.