In the first public test of is kind for Network Detection and Response, SE Labs awards the industry’s first NDR AAA rating to VMware NSX Network Detection and Response (NDR). The modern cyber battlefield is everywhere, and every attacker has to traverse multiple networks and in most cases many firewalls to achieve their goals. Internal to networks they look to move freely within the environment discovering valuable information they wish to exfiltrate. As attackers have continually innovated so must the industry and our testing. As a leader in the security industry, VMWare has gone through the industry’s first Network Detection and Response (NDR) test and received a AAA rating. It is well-known that attackers continually evolve and chain together an ever increasingly complex chain of events. These techniques, tactics and procedures occur across networks and often traverse and bypass traditional security tools like firewalls and antivirus. As our understanding of attacker’s behaviors evolve, so must our engineering and testing.
VMware customers can be assured that their data is better protected in this new arena as they continue to modernize their application and network infrastructure as part of their digital transformation initiatives.
According to the results from SE Labs, VMware NSX NDR provides 100 percent protection across multi-cloud environments from four major advanced and persistent threats (APT) groups—including FIN7&Carbanak, OilRig, APT3 and APT29—while returning zero false positives. This ability allows security operations teams to rapidly detect malicious activity and stop the lateral movement of threats inside the network.
According to the report, “VMware NSX Network Detection and Response was tested against a range of hacking attacks designed to compromise systems and penetrate target networks in the same way as criminals and other attackers breach systems and networks. VMware NSX NDR was able to detect every targeted attack and tracked each of the hostile activities that occurred during the attacks.”
Not only did VMware NSX NDR score the highest possible rating in the industry’s first test on NDR, Simon Edwards, CEO of SE Labs said “We test NDR products privately and regularly, and have not awarded any other products a AAA rating.”
Join us on November 15 for a deep-dive on the testing results.
How it Works
VMware NSX NDR ingests signals from built-in and distributed sensors located throughout the environment, detecting, and preventing threats at every stage of the MITRE ATT&CK Framework. This gives SOC teams unparalleled visibility into malicious events as they occur. VMware NSX NDR built-in and distributed sensors include:
- VMware NSX® Sandbox provides advanced malware analysis of artifacts traversing your data center. NSX Sandbox™ deconstructs every behavior engineered into a file or URL and sees all instructions that a program executes, all memory content, and all operating system activity.
- VMware NSX Network Traffic Analysis (NTA) helps SOC teams rapidly detect anomalous activity and malicious behavior as it moves laterally across your network. VMware NSX NTA can uncover active threats inside your network and secures your east-west traffic across multi-cloud environments – virtualized, containerized, or bare metal. VMware NSX NTA is distributed as a service to the underlying software defined data center (SDDC) infrastructure at each host, bringing authoritative context, accuracy, and speed to your security teams.
- VMware NSX Distributed IDS/IPS is an application-aware traffic inspection engine purpose built for analyzing internal east-west traffic and detecting lateral threat movements. NSX Distributed IDS/IPS combines industry-leading signature sets, protocol decoders and anomaly detection-based mechanisms to hunt for known and unknown attacks in the traffic flow.
VMware NSX NDR was the pioneering network security platform to participate alongside VMware Carbon Black in the latest MITRE’s Engenuity ATT&CK evaluation providing unprecedented lateral movement and privilege escalation detections. This test being primarily focused on endpoint security solutions, SE Labs developed and pioneered the industry’s first test focused on network detection and response capabilities.
SE Labs aims to improve information technology security by assessing products and services designed to detect attacks, protect against intrusions or both. As outlined in the SE Labs Breach Response Detection Test report, VMware NSX NDR detected all malicious network activity and all malicious network payloads with zero false positives against four major APT groups as defined by MITRE.
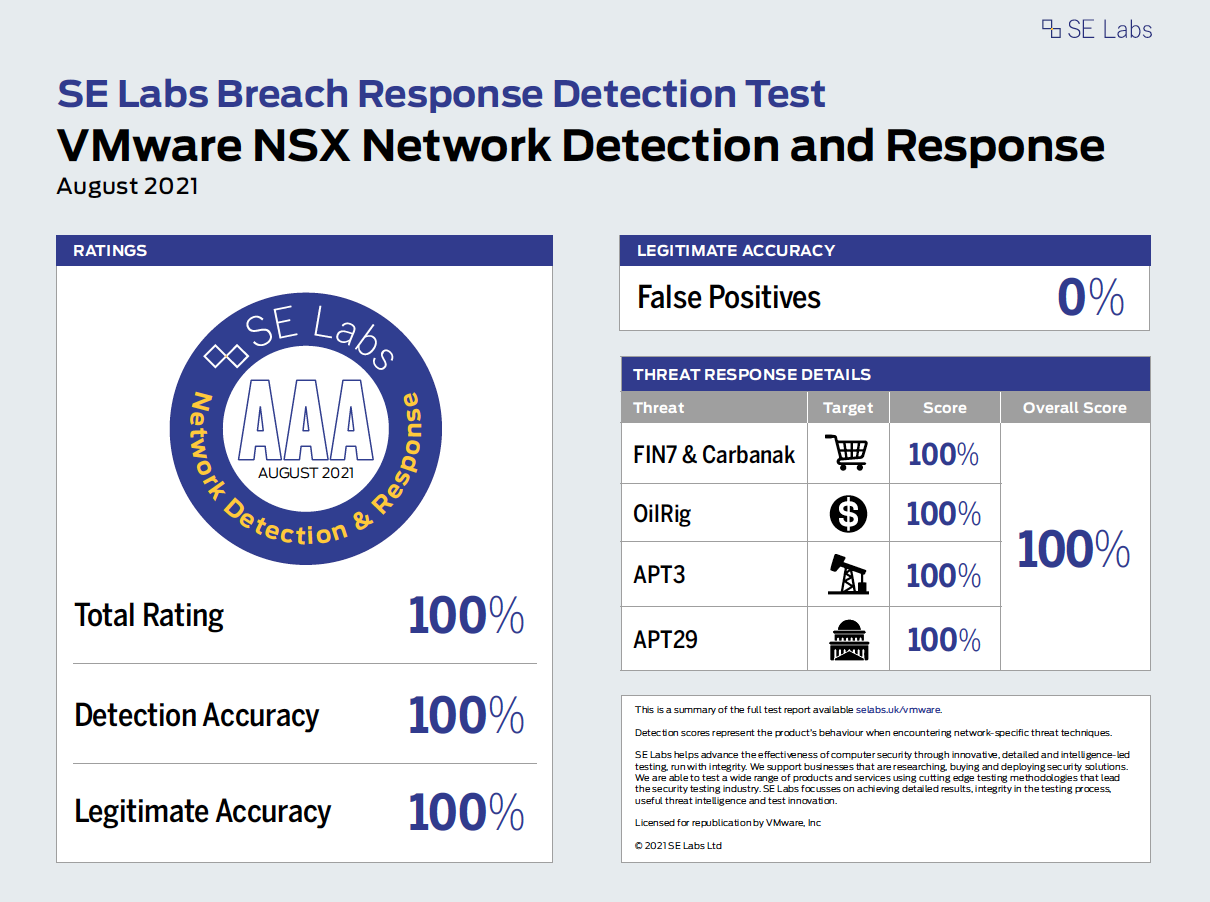
100% Legitimate and Detection Accuracy Ratings
Security, IT, and operations teams each approach protecting an environment from different perspectives. Each group uses a plethora of different point tools that generating unique—and often isolated—data in the process. Too often, security teams are forced to make decisions with incomplete and inaccurate data. The SE Labs evaluation demonstrates VMware NSX NDR’s authoritative context with high-fidelity from visibility, depth, and accuracy of data collection.
This enables security operators to scale response with confidence, speed, accuracy and implement Zero Trust with fewer tools and silos.
At the same time, SOC teams require an elevated level of clarity regarding the events occurring within the organization’s assets, and the SE Labs results prove that VMware NSX NDR is best positioned to give security teams the visibility and context they need to take decisive action against adversaries. This visibility and control allow them to transition to next-generation systems and modern applications without increasing security complexity or reducing the attack surface.
Independent Testing
VMware fully supports independent testing organizations that, like SE Labs, innovate, expand, and continually test to improve cybersecurity products. SE Labs evaluated VMware NSX NDR in July 2021 against four major APT’s as described by MITRE:
- FIN7 is a financially-motivated threat group that has primarily targeted the U.S. retail, restaurant, and hospitality sectors since mid-2015.
- OilRig is a suspected Iranian threat group that has targeted Middle Eastern and international victims since at least 2014.
- APT3 is a China-based threat group that researchers have attributed to China’s Ministry of State Security.
- APT29 is a threat group that has been attributed to Russia’s Foreign Intelligence Service (SVR).
SE Labs used current threat intelligence to look at what the threat actors have been doing over the last few years and copied them quite closely. All the attacks deployed by SE Labs in this test are valid ways to compromise an organization, including:
- Delivery of malicious payloads and links via phishing attempts that result in beaconing, command and control and connections on suspicious ports.
- Discovery and enumerating of network assets to include SMB share enumeration, trusted domain enumeration and active directory queries.
- Lateral movement activities, including suspicious RDP connections, WinRM connections, command execution over SMB and the use of SMBv1.
- Lateral movement of malicious payloads between internal hosts such as scripts, archives, and files.
- Date exfiltration and suspicious data downloads over alternative protocols.
According to the SE Labs Report, “this test exposed VMware NSX NDR to a diverse set of exploits, file-less and malware attacks and reconnaissance ‘discovery techniques. The testers behaved as attackers, pivoting between systems (and generating lateral movement traffic), attempting to use credentials, exfiltrating data and creating command and control data flows. This product detected all of the threats.”
Changing the Meaning of Security Success
The cybersecurity industry is changing, and it is important that the way we test and evaluate security solutions change with it. It has been generally accepted that modern threats will eventually penetrate your perimeter and get inside your network. Rather than focus exclusively on stopping attacks at the endpoint, it is critical that organizations can monitor network traffic inside the data center to identify abnormal behavior and stop the spread of these attacks before they can take hold. We need to shift left in the attackers kill chain pushing visibility as early as possible to have the best position to prevent, detect and respond to attackers. Continual testing of security products against advanced threats, tactics, and techniques helps prove to customers and prospects that VMware NSX NDR has the visibility and efficacy to detect, prevent and respond to advanced threats.
You too can take advantage of the authoritative context and high-fidelity prevention of advanced threats as part of VMware’s Zero Trust Architecture. VMwareNSX NDR offers a unique opportunity to deploy a comprehensive security solution that provides the visibility and fine-grained enforcement necessary to address advanced and persistent threats.
Join us on November 15 for a webinar hosted by SC Media to get an in-depth look into the testing results and how NSX NDR can help you better defend against advanced threats. Register today!







