According to the VMware State of Kubernetes 2021 Report, the containerized application attack surface has grown in orders of magnitude relative to virtualized applications with four times (4x) the growth in median containers per host from 2017 to 2020. That means many more points of entry for attackers, who have already taken notice of the paradigm shift and new software ecosystem.
Securing the Full Container Lifecycle Starts with Visibility
To address this growing threat, a comprehensive security strategy for modern apps needs to span the entire application lifecycle from build to run. The concept of “shifting left” has gained a lot of momentum in the security industry, and refers to shifting security earlier in the development process towards the build phase, where security gaps are less expensive to fix. By integrating security to the build, we can create workloads which are secure by design, and reduce the attack surface. In fact, planning your security strategy starts with understanding your environment and that requires visibility into your workloads, how they are configured, and how your infrastructure – your Kubernetes environment in this case – is configured. You also need to prioritize the risk associated with each workload, so you know where to focus your remediation efforts.
Earlier this year, we released a comprehensive set of features to help customers get started with visibility into their Kubernetes environment, defining security and compliance policies, scanning for vulnerabilities and misconfigurations, and prioritizing risk. In addition to spanning the entire application lifecycle, security must also address directly (or through integrations with other components) all of the layers (virtual, physical, etc.) as one. Visibility into the correlation between Kubernetes nodes and container events are critical to better understanding overall security posture, managing risk and mitigating as much as possible.
Securing Modern Applications with the Kubernetes Connectivity Map
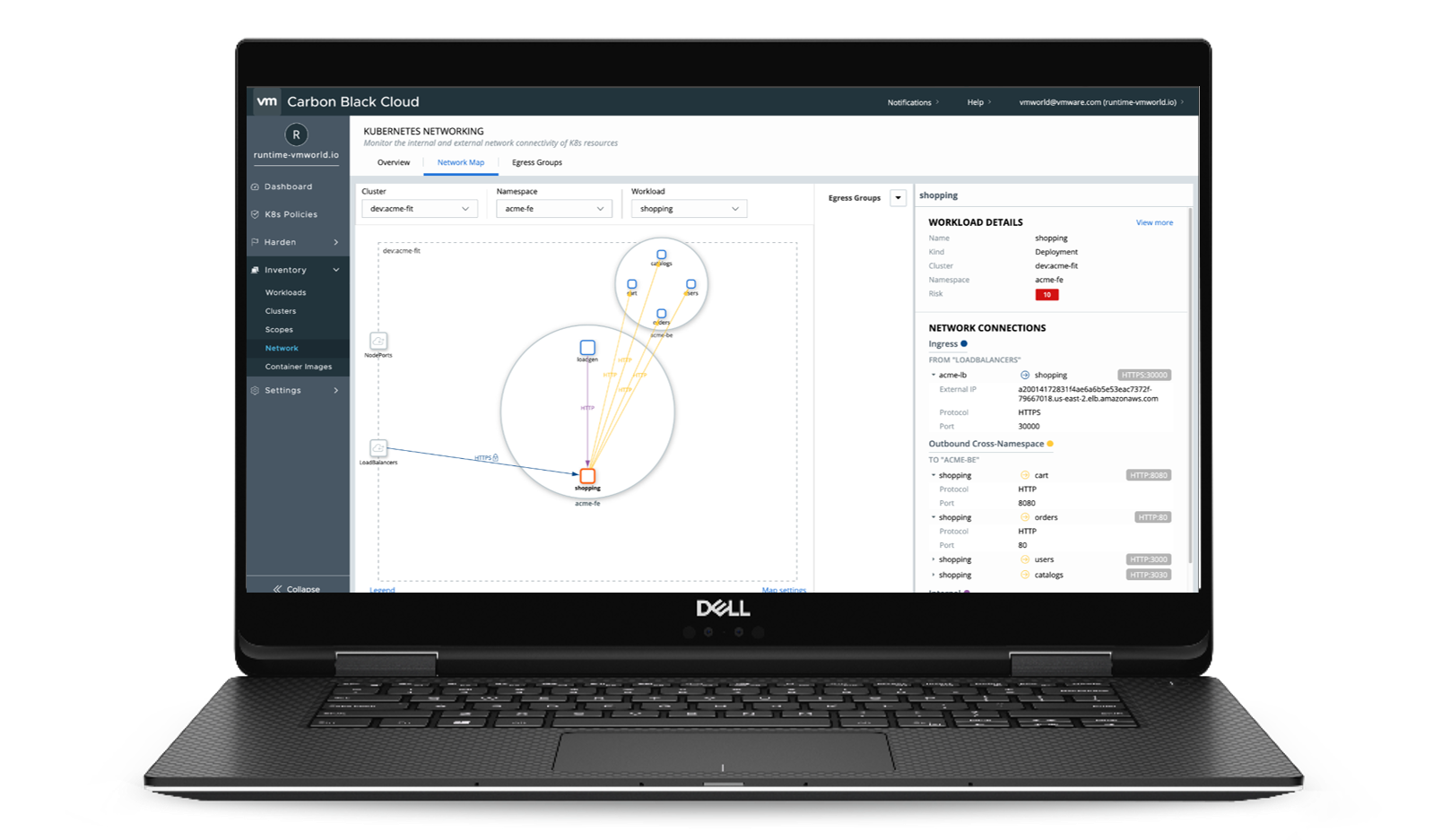
Today, DevOps and Security teams often lack visibility into different workloads that are running in a given cluster, and the connectivity to and from those workloads. The newly released network connectivity map for VMware Carbon Black Container helps these teams understand the application architecture, the connectivity between different workloads, and how they consume services with an egress connection from an external source outside of the cluster.
Kubernetes Network Connectivity Map
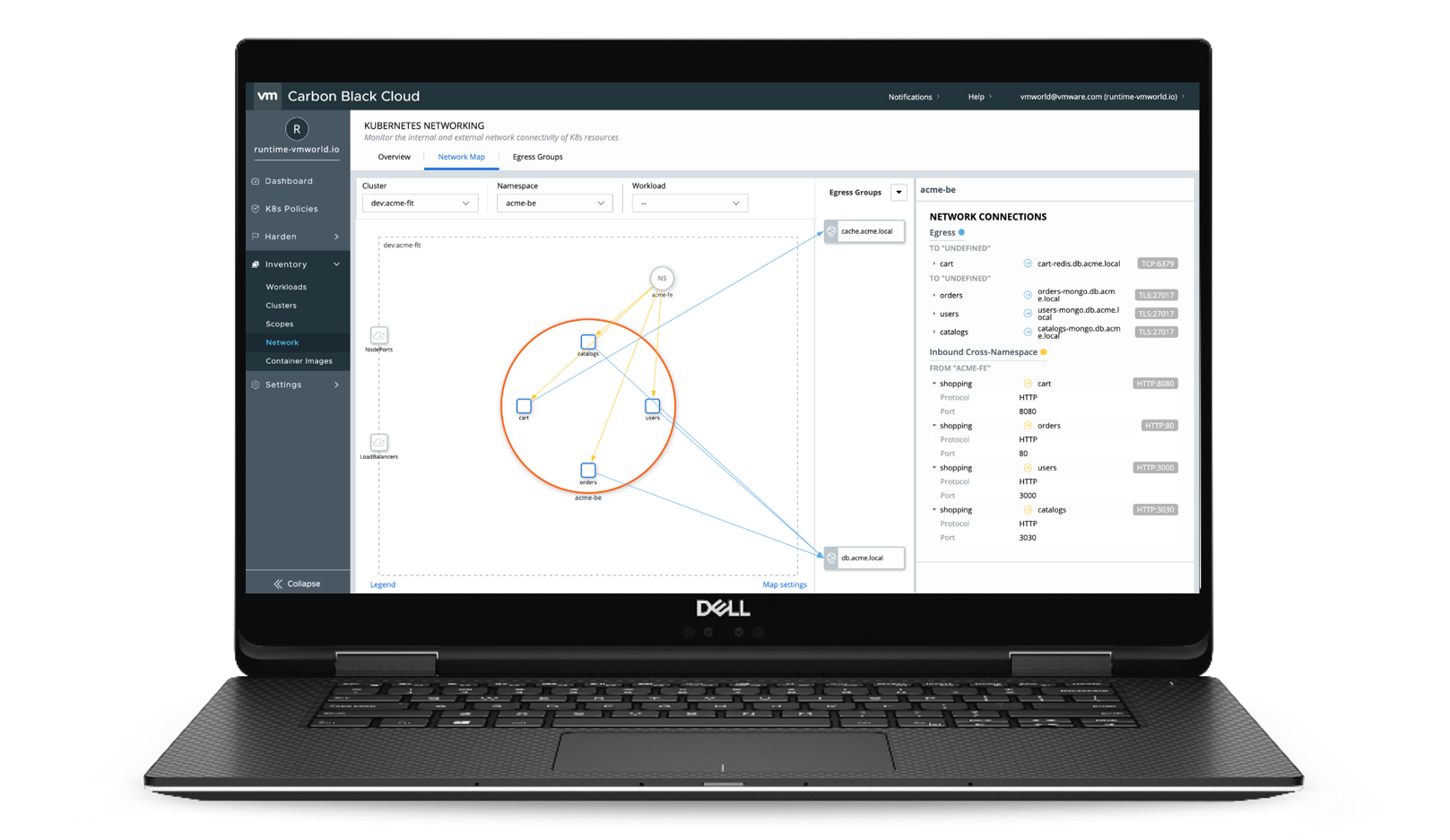
To simplify this process, the network connectivity map allows you to view these workload connections in a single map of the application architecture. You can also create your own egress group-to-group internal or external IP’s you know and approve access to.
Egress Groups View
To have a clean view of your application, you can filter the connectivity of the map to remove system name spaces, or if you want to better understand what connection is encrypted or not encrypted you can filter by that as well. The goal of the networking map is to give teams a better understanding of the connectivity and configuration of applications installed in Kubernetes clusters. You can see a demonstration of the Network Visibility Map on YouTube here.
Kubernetes Cluster View
To learn more about VMware Carbon Black Container, please visit the following resources:
- Product Webpage
- Product Datasheet
- Customer Webinar
- Securing Modern Applications in TechZone
- VMworld 2021 Session: Kubernetes Security Posture Management (Requires VMworld Account)