This is a guest blog post by Rob McLeod, Vice President, Threat Response Unit at eSentire – on behalf of eSentire TRU team
Zero-day attack — these three words can strike fear into CISOs and their organizations.
Simply defined, a zero-day attack is an attack that exploits a software vulnerability that is not known to the vendor or its users. Because the vulnerability is not known to the vendor, there is no patch to repair it. Since the vulnerability is not known to the software’s users, no specific protective actions are taken.
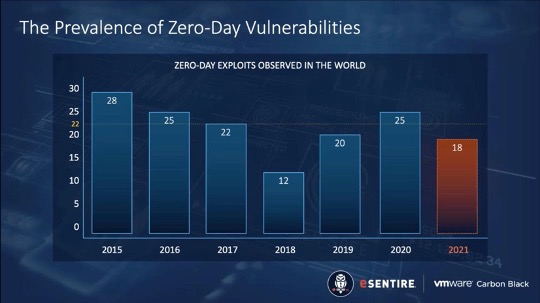
A threat actor equipped with a zero-day exploit is presented with a land of opportunity, which is one reason why these weapons are so highly valued in the cybercrime community and why the attacks can lead to business-disrupting events. Unfortunately, 2021 is on a record-setting pace. Businesses and other organizations need to pay special attention to zero-day threats.
However, as previously defined, a zero-day attack cannot be prevented (e.g., by patching). So what can organizations do?
Recently, VMware Carbon Black and eSentire teamed up to answer this question in an easy-to-understand report and an engaging 30-minute round table— both of which draw upon direct observations and the latest cybersecurity research. The shared insights include:
- Where zero-day attacks come from
- What makes them so dangerous
- Their lifecycle from vulnerability discovery through to mass-market cybercrime commodity
- How threat actors put them to use
- How businesses can remain resilient
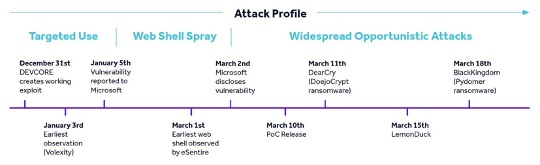
Using the notorious ProxyLogon zero-day episode as an example (see timeline below), the report demonstrates that quickly detecting post-compromise activity (e.g., reconnaissance and domain discovery, persistence through processes, web shells, credential dumping, C2, etc.) is the key to withstanding a zero-day attack.
The round table, featuring threat intelligence experts from both teams, provides additional commentary that touches on:
- How zero-day exploit severity is assessed
- How the combined VMware Carbon Black and eSentire Managed Detection and Response (MDR) service detects and responds to stealthy attacks
- Why the job isn’t done just because patching is available and deployed
It’s important for IT and security professionals to start the conversation with executives to raise awareness of the business risks associated with zero-day attacks. We must stop assuming there’s nothing that can be done to manage the risk of zero-day attacks. Armed with these insights, organizations can learn how to spot the signs of post-compromise activity; whether a threat actor employs a zero-day exploit or leverages some other vector.
eSentire, Inc., is the Authority in Managed Detection and Response, protecting the critical data and applications of 1000+ organizations in 70+ countries from known and unknown cyber threats. Founded in 2001, the company’s mission is to hunt, investigate and stop cyber threats before they become business disrupting events. Combining cutting-edge machine learning XDR technology, 24/7 Threat Hunting, and proven security operations leadership, eSentire mitigates business risk, and enables security at scale. The Team eSentire difference means enterprises are protected by the best in the business with a named Cyber Risk Advisor, 24/7 access to SOC Cyber Analysts & Elite Threat Hunters, and industry-leading threat intelligence research from eSentire’s Threat Response Unit (TRU). eSentire provides Managed Risk, Managed Detection and Response and Incident Response services. For more information, visit www.esentire.com and follow @eSentire.