Network segmentation—splitting a network into subnetworks or segments—is widely accepted to be a powerful and effective method for improving cybersecurity within the data center. Yet even though it’s acknowledged to be an essential component of network security hygiene, organizations have frequently avoided putting segmentation into practice.
Why? Because historically network segmentation has been complex, disruptive, and time-consuming to implement, requiring extensive changes to the physical network and/or network addresses. The potential impact of taking applications offline for network changes means that many organizations decide to forego this industry-wide best practice. Teams that do forge ahead often face months- or years-long effort to create security zones by re–architecting the network, relocating equipment, and re-assigning IP addresses.
It doesn’t have to be that way. Today there’s an elegant solution that greatly simplifies and accelerates network segmentation: VMware NSX Service-defined Firewall. Purpose–built to protect east-west traffic, VMware Service-defined Firewall enables segmentation without any disruptive physical network or address changes.
Attackers Love Flat Networks
To back up a step, let’s examine why network segmentation is an essential best practice. Flat networks, while simple, offer little to no resistance to cyberattacks that breach the perimeter. With a flat network, if hackers can establish a beachhead, they can then move laterally across the entire network to gain access to sensitive workloads. With no isolation of workloads within network segments or security zones, there are no internal control points that prevent traffic from traversing the entire network.
By contrast, network segmentation splits the network into security zones (see Figure 1), letting you group workloads by security risk and requirements. For instance, you can group workloads that have the same or similar compliance needs. Securing those workloads that must adhere to certain security requirements — by isolating them from workloads that don’t have to meet stringent guidelines — reduces your organization’s scope of compliance and simplifies policy management.
Successfully segmenting the network into security zones can significantly improve your organization’s cybersecurity posture by:
- Reducing the attack surface
- Providing an additional line of defense against outside attacks that breach the perimeter
- Protecting against malicious insider attacks and minimizing access to sensitive information
- Mitigating lateral movement outside of a compromised host
- Making it much more difficult for an attacker to discover targets in other security zones
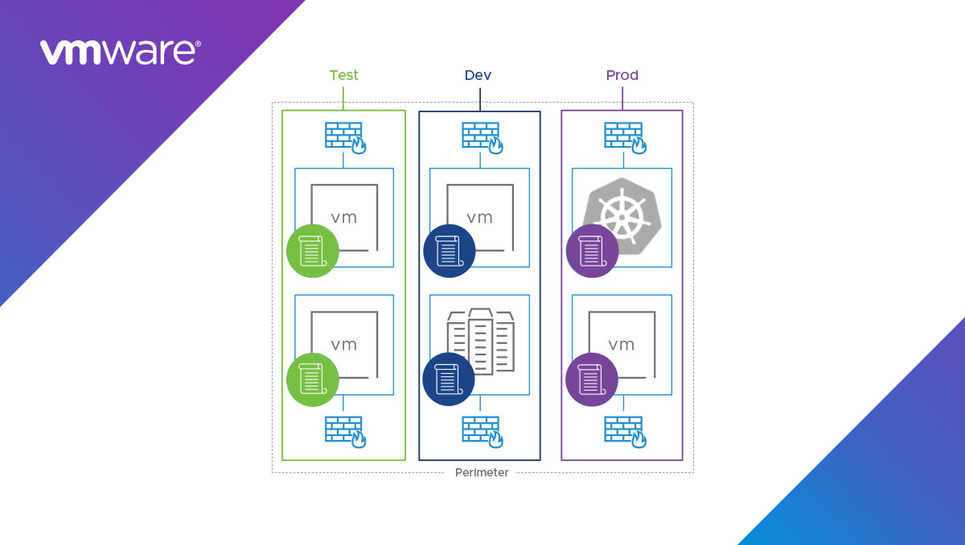
Figure 1. Segmentation of the Network into Security Zones
Segmentation the Traditional (i.e. Difficult and Time-Consuming) Way
Until now, practitioners have approached network segmentation projects with trepidation, because they know that the effort will be extensive and the risk of disruption high. Moreover, they know that network segmentation done the traditional way is a massive undertaking that touches many parts of the business, requires months or years to complete, and introduces considerable project risk.
At the crux of the issue is the type of firewall organizations use to segment and monitor east-west network traffic. Using a traditional, appliance-based firewall designed to protect the perimeter to instead create security zones within the data center has proven cumbersome at best — and expensive, complex, and difficult to scale at worst.
That’s because appliance-based firewalls require the organization to make changes to the physical network or network addresses to achieve segmentation. Teams must re-architect the network, re-assign IP addresses for workloads running on it, and then test all changes to make sure no workloads or users are impacted by those changes. Reconfiguring segments or adding new segments later can mean re-architecting the network yet again.
It’s no wonder organizations have viewed network segmentation as a nice–to–have capability that is simply unrealistic to achieve for most data centers.
Segmentation the Easier, Faster, and More Flexible Way
With VMware Service-defined Firewall, segmenting the network is non-intrusive, with no disruptive network re-architecture and no re-assignment of IP addresses required. Since no physical changes are necessary, implementing network segmentation can be accomplished in days, instead of months or years.
A two-step, wizard-driven process lets your team install the Service-defined Firewall on hypervisor clusters and then begin protecting every workload in the data center. To segment the network, you can create tags for workloads to identify the zone in which they belong. For instance, the “prod” tag would be for production workloads, “dev” for development/test, and so on.
Security administrators can specify distributed firewall policies that permit communication when both ends of the traffic flow have a common tag (i.e., they are both in the same zone). Traffic with tags that originate from, or are destined for, outside of the zone are denied.
A Proven Approach
A major telecommunications company needed to protect its business-critical, consumer-facing mobile application infrastructure. The company decided to use network segmentation to secure large amounts of network traffic on in-house infrastructure running on more than 10,000 virtual machines.
Using VMware Service-defined Firewall, the telecom created virtual security zones to isolate and secure its development, production, and DMZ environments. The Service-defined Firewall simplified management of firewall rules for the telecom by allowing policies to be expressed using tags rather than an IP address. This gave the company greater agility and speed for adding new workloads and moving or decommissioning existing ones.
Eliminating the Drawbacks of Network Segmentation
With the Service-defined Firewall, your team can deploy and support security zones without the substantial effort and risk associated with traditional methods of network segmentation. You can successfully mitigate risk across the data center in a short amount of time using network segmentation — with none of the constraints on traffic volume and policies associated with using appliance-based firewalls.
Using the Service-defined Firewall for network segmentation gives your team:
- Faster time-to-value: Implement network segmentation quickly to achieve improved security and compliance in weeks (or days).
- Simplicity: Radically simplify deployment of network segmentation by eliminating network redesign and re-assignment of IP addresses. Easily create, enforce, and automatically manage segmentation policies between applications, services, and workloads using reference tags.
- Adaptability: Defining security zones in software lets you deploy new network segments and reconfigure zones rapidly, without needing to re-architect the network.
- Elasticity: Autoscale the distributed internal firewall as workloads are spun up or down without worrying about running out of inspection capacity.
Helpful Resources
Learn more about why a distributed, scale-out internal firewall is the ideal solution for securing internal (east-west) traffic in our white paper “Internal Firewall: The Best Way to Protect East-West Traffic”







