FTCODE is a fully PowerShell-based ransomware. It is distributed via malicious document files that contain macros or using VBScript to download and launch the malicious PowerShell script. FTCODE ransomware will scan a specific list of file extensions and encrypt them with Rijndael algorithm. Other than encrypting files, it will also steal sensitive data from the victim’s computer such as login credentials from web browsers. Similar to other variants of ransomware, it will delete backup and volume shadow copies to prevent victims from recovering their encrypted data.
Figure 1: Overall activity perform by FTCODE
Delivery Method
FTCODE could be delivered via various methods, for example, sending spear-phishing email by attaching malicious documents or a VBS script file.
Figure 2: Example of the opened FTCODE document, it will prompt users to enable Macros.
Figure 3: Extracting the document and analyzing it for embedded macros with olevba, shows that this it contains suspicious embedded VBA code.
Once a user executes the malicious document or malicious VBS script, it will then launch the PowerShell script to download and run the FTCODE ransomware. While the VBS script was written encoded, the following screenshot display the final output of executed powershell command from Cloud Enterprise EDR event log.
Figure 4: Screenshot of executed PowerShell command from Cloud Enterprise EDR (CB ThreatHunter) event log.
It will then download and save a malicious script in the following directory: “%Public%\Libraries\WindowsIndexingService.vbs”.
FTCODE creating persistence
To ensure the malicious script can be execute in every startup, it will perform the following:
- Create a shortcut file named “WindowsApplicationService.lnk” in Windows Startup folder to execute “WindowsIndexingService.vbs”.
- Creates a scheduled task named “WindowsApplicationService” to ensure the script will be executed every day at 00.00 in every 20 minutes
- “ schtasks.exe /create /TN “WindowsApplicationService” /sc DAILY /st 00:00 /f /RI 16 /du 23:59 /TR C:\Users\Public\Libraries\WindowsIndexingService.vbs”
- Create the file “%Public%\OracleKit\w00log03.tmp” to write and store Globally Unique Identifier (GUID) and will change the file attribute as ‘Hidden’.
- Check if the file “%Temp%\quanto00.tmp” exists and is created more than 30 minutes earlier, it will write the current time onto the file, otherwise it will exit itself to avoid the same malicious script execute at the same time.

Figure 5: FTCODE creates shortcut file and schedule task
Figure 6: FTCODE creating persistence files
Encrypting process
Before the encryption starts, FTCODE will connect to a Command and Control (C&C) server. If it does not get a response from the C&C server, it will terminate itself, otherwise it will send another post request to C&C and start the encryption process.
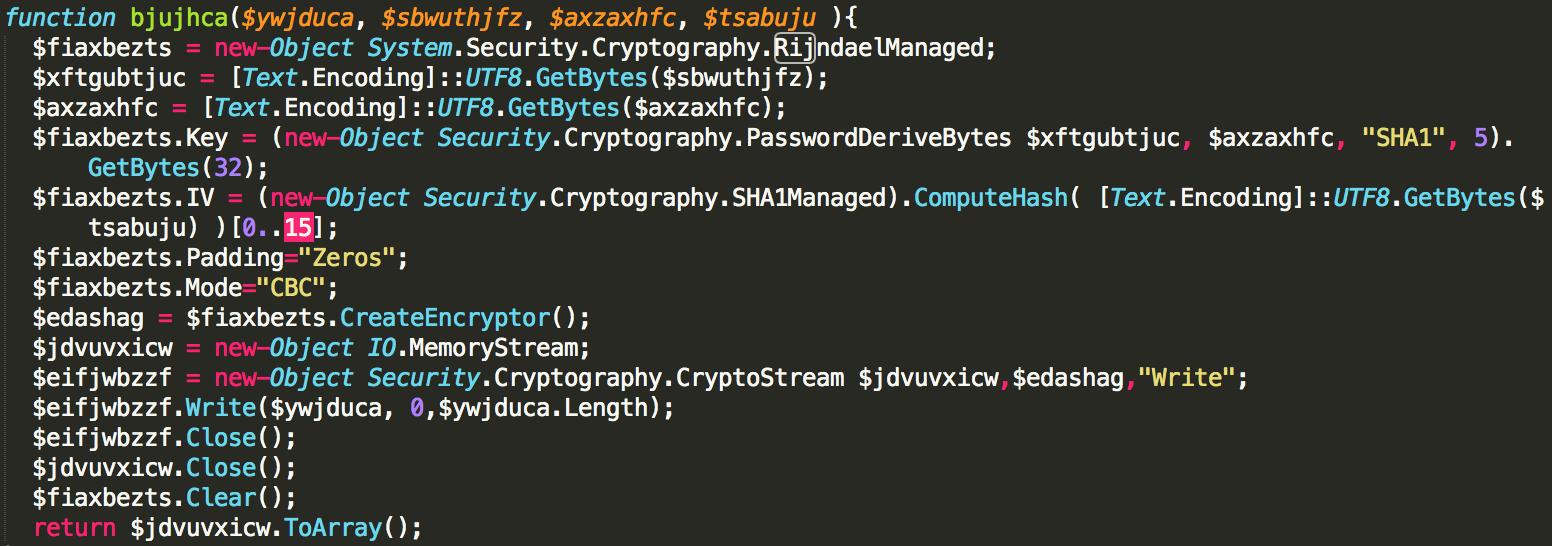
FTCODE is using Rijndael algorithm to encrypt files on drives that have more than 50 MB of free space. This is likely a check to either ensure it’s not running in a virtual machine or to ensure it has enough disk space to successfully perform encryption. This malware is unique in that it will only encrypt the first 40,960 bytes of a file. By encrypting a small portion the file is still rendered unusable by most applications while providing a large performance benefit to the ransomware.
Encryption will take place on files with the following list of extensions:
|
.sql |
.mp4 |
.7z |
.rar |
.m4a |
.wma |
.avi |
.wmv |
|
.csv |
.d3dbsp |
.zip |
.sie |
.sum |
.ibank |
.t13 |
.t12 |
|
.qdf |
.gdb |
.tax |
.pkpass |
.bc6 |
.bc7 |
.bkp |
.qic |
|
.bkf |
.sidn |
.sidd |
.mddata |
.itl |
.itdb |
.icxs |
.hvpl |
|
.hplg |
.hkdb |
.mdbackup |
.syncdb |
.gho |
.cas |
.svg |
.map |
|
.wmo |
.itm |
.sb |
.fos |
.mov |
.vdf |
.ztmp |
.sis |
|
.sid |
.ncf |
.menu |
.layout |
.dmp |
.blob |
.esm |
.vcf |
|
.vtf |
.dazip |
.fpk |
.mlx |
.kf |
.iwd |
.vpk |
.tor |
|
.psk |
.rim |
.w3x |
.fsh |
.ntl |
.arch00 |
.lvl |
.snx |
|
.cfr |
.ff |
.vpp_pc |
.lrf |
.m2 |
.mcmeta |
.vfs0 |
.mpqge |
|
.kdb |
.db0 |
.dba |
.rofl |
.hkx |
.bar |
.upk |
.das |
|
.iwi |
.litemod |
.asset |
.forge |
.ltx |
.bsa |
.apk |
.re4 |
|
.sav |
.lbf |
.slm |
.bik |
.epk |
.rgss3a |
.pak |
.big |
|
wallet |
.wotreplay |
.xxx |
.desc |
.py |
.m3u |
.flv |
.js |
|
.css |
.rb |
.png |
.jpeg |
.txt |
.p7c |
.p7b |
.p12 |
|
.pfx |
.pem |
.crt |
.cer |
.der |
.x3f |
.srw |
.pef |
|
.ptx |
.r3d |
.rw2 |
.rwl |
.raw |
.raf |
.orf |
.nrw |
|
.mrwref |
.mef |
.erf |
.kdc |
.dcr |
.cr2 |
.crw |
.bay |
|
.sr2 |
.srf |
.arw |
.3fr |
.dng |
.jpe |
.jpg |
.cdr |
|
.indd |
.ai |
.eps |
|
.pdd |
.psd |
.dbf |
.mdf |
|
.wb2 |
.rtf |
.wpd |
.dxg |
.xf |
.dwg |
.pst |
.accdb |
|
.mdb |
.pptm |
.pptx |
.ppt |
.xlk |
.xlsb |
.xlsm |
.xlsx |
|
.xls |
.wps |
.docm |
.docx |
.doc |
.odb |
.odc |
.odm |
|
.odp |
.ods |
.odt |
Figure 7: FTCODE encrypting process
Figure 8: FTCODE using Rijndael algorithm to encrypt files
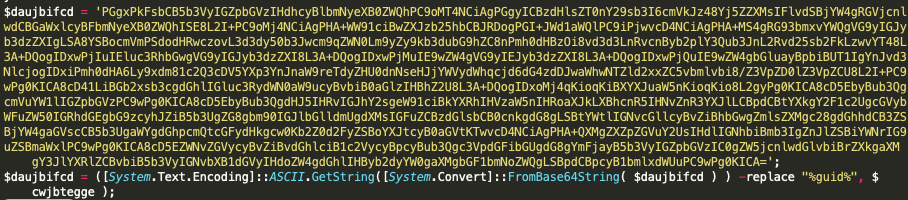
After the encryption process, it will append randomly generated six characters as file extension to the encrypted file and drop the ransom note named “READ_ME_NOW.htm” in all directory that have encrypted file as shown in the following Figure 11. The content of the ransom note is encoded in the Base64 string and the decoded string are shown in the following Figure 9 and 10.
Figure 9: Ransom note encoded in Base64 string
Figure 10: Decoded Base64 string
Figure 11: Screenshot of Ransom Note
Ransomware Deleting Backups
The ransomware will perform the deletion of volume shadow copies and disable Windows automatic startup repair with the following command to ensure all the data cannot be restored easily:
- bcdedit /set bhcuhciv bootstatuspolicy ignoreallfailures
- bcdedit /set bhcuhciv recoveryenabled no
- wbadmin delete catalog -quiet
- wbadmin delete systemstatebackup
- wbadmin delete backup
- vssadmin delete shadows /all /quiet
Figure 12: Ransomware makes victim harder to recover encrypted data
Stealing Sensitive information
Other than perform encryption on the files, FTCODE will also steal sensitive information such as login credentials from several applications and then send the stolen data to C&C.
The malware will attempt to steal data from both the Firefox web browser and the Thunderbird email client. These two applications, both created by Mozilla, use a file named “logins.json” to store saved login information. If a user saves their login to a website, such as their banking site, the login information will be encrypted and stored here. However, there are numerous tools that can easily decrypt the information. The malware will look to find this file in the following locations:
- %APPDATA%\Mozilla\Firefox\Profiles\*.*
- %APPDATA%\ThunderBird\Profiles\*.*
Figure 13: Stealing login credentials from Mozilla Firefox and Mozilla Thunderbird
In addition, it will also attempt to steal login credentials from Google Chrome browser that are stored in the file “%AppData%\Local\Google\Chrome\User Data\*\Login Data“
Figure 14: Stealing login credentials from Google Chrome
Furthermore, it will also steal Outlook account credentials that are stored in the following registry key from Microsoft Outlook application:
- HKCU:\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\*\9375CFF0413111d3B88A00104B2A6676\*
- HKCU:\Software\Microsoft\Office\1[56].0\Outlook\Profiles\*\9375CFF0413111d3B88A00104B2A6676\*

Figure 15: “function ol_dump” to stealing Microsoft Outlook credentials
Moreover, FTCODE will steal Internet Explorer (IE) browser’s history with the reference of “$shell.NameSpace(34)” in code which refers to the file system directory that serves as a common repository for Internet history items. Besides that, it also steals user’s login credentials that are stored in the registry “HKCU:\Software\Microsoft\Internet Explorer\IntelliForms\Storage2”.
Figure 16: Stealing IE history and stored credentials
Additionally, it also steals saved login credentials from Vault which is a Credential Manager on Windows 7 and above.
Figure 17: Stealing credentials from Windows Vault
Product Detections: Please see the related TAU-TIN document here.