Recently, security researchers revealed a Proof of Concept attack that leverages the BlueKeep vulnerability. Whenever this type of news breaks on the twittersphere, organizations are left with the question: “Are we susceptible to this type of attack?” Using CB LiveOps, a real-time endpoint query tool, we are able to quickly identify the potential risk for the environment.
Remote Desktop is a remote management tool you can use with Windows that allows you to connect to any computer running Windows and take over the desktop, literally as if you were sitting in front of the monitor. Other popular remoting software include Teamviewer, Citrix GoToMyPC, Connectwise, and LogMeIn. RDP is by default included with Windows desktops.
It is important to ask your organization if there is a standardization on remote desktop software being utilized within your environment and if there is not, it is something to consider. Being able to limit the tools that can remotely access machines will reduce risk overall in your organization.
From an attackers perspective, when a RDP session is initiated, attackers infiltrate the connection between the machines within the session. The attacker then has access to your internal systems. Depending on their objectives, the attacker can leverage many post-exploitation techniques to exfiltrate data or move laterally to other machines. Once an attacker is in the organization, it is extremely difficult to detect because these attackers will mimic many of the same actions as a typical end user or admin.
If RDP is the tool of choice for remote management, it is time to see where exactly it is enabled by using this query to understand the possible attack surface for BlueKeep:
SELECT
CASE DATA
WHEN 1 THEN “Enabled”
WHEN 0 THEN “Disabled”
END “RDP Status”
FROM registry
WHERE PATH=”HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\fDenyTSConnections”;
Note: This query is already part of CB’s recommended queries, built right into the console. You can simply go to the Recommended Queries and search to see this query.
At this point, you will have a list of machines where RDP is enabled. To see where existing RDP connections exist, you will now run this query:
SELECT processes.pid,
processes.name,
processes.cmdline,
process_open_sockets.local_address,
process_open_sockets.remote_address,
process_open_sockets.local_port,
process_open_sockets.remote_port
FROM processes
INNER JOIN process_open_sockets
ON processes.pid=process_open_sockets.pid
WHERE remote_port!=0
AND local_port=3389;
Now, this is the time that you go gather your pitchforks and set the record straight that your organization should not be allowing this sort of behavior!
Just kidding. Put the pitchforks down. Yes you reading this. Drop it.
Sometimes, RDP is necessary for small businesses or even in larger organizations for specific use-cases. If RDP is enabled and required for your organization, you can at least use EDR tools like CB ThreatHunter to alert on things like RDP Connections outside of your internal organization if you cannot disable internet-facing RDP. This type of IOC (Indicator Of Compromise) can help quickly identify anomalous activity in the environment.
To further harden RDP usage in your environment, it is important to restrict access to remote desktop listening ports and ensure that Network Level Authentication is enabled. This feature is on by default, and ensures an extra level of authentication is enabled before an RDP session is initiated. This can be found in your group policy settings. There should be a setting that says, “require authentication for remote connections utilizing Network Level Authentication.” A great blog that walks through setting these settings up can be found here.
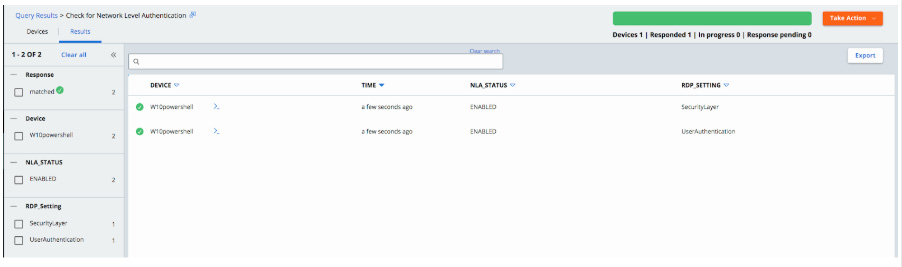
We can use CB LiveOps to ensure that the default setting was not altered anywhere:
SELECT name AS “RDP_Setting”,
CASE data
WHEN 0 THEN “DISABLED”
ELSE “ENABLED”
END “NLA_STATUS”
FROM registry
WHERE path = “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\SecurityLayer” or
path = “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\UserAuthentication”;
You can look at your results via the VMware Carbon Black Cloud UI and you can also export these results.
I can also sort my results by facets on the left-hand side, so that if something was set to disabled, I could just pull a report of endpoints with the default settings disabled and say…
So Why CB LiveOps?
As you can see from the above, using CB LiveOps allows you to go far beyond scratching the surface of identifying the risk in your organization from vulnerabilities like BlueKeep. Most organizations today will just try to apply the patch(es) that addresses these vulnerabilities, but for machines that cannot be patched, running through the processes above can ensure that you have the visibility into the risk against certain types of vulnerabilities. The answer of “we cannot patch X” is no longer the end state for organizations.
In addition, LiveQuery offers me the ability to pull results asynchronously, aka as soon as available. I do not need to wait for a full vulnerability scan or wait for all of my devices to report back with answers. As devices report in their results display immediately in order to address at-risk devices.
At the end of the day, BlueKeep is just one of many vulnerabilities that you can assess and tie a risk scope to within your organization. So, until the next breaking tweet, query on!
Additional Resource:
Note: Although this blog focuses on BlueKeep specifically, this can also apply to other vulnerability workflows (including the TeamViewer CVE released in September 2019).