In June of 2019, researchers at Intego discovered a new Trojan for macOS systems which they named CrescentCore. Much like Shlayer and other common malware targeting macOS systems, CrescentCore is often delivered via a fake Adobe Flash Player installer or updater. This malware employs multiple anti-analysis techniques such as VM and AV product detection. If certain products are detected (which are defined in JSON-formatted configuration files in the application directory), the malware will halt execution and exit. If installation completes successfully, CrescentCore installs a LaunchAgent and LaunchDaemon for persistence, and some variants have been observed to install additional malicious or unwanted software and browser extensions.
Behavioral Summary
All identified variants of CrescentCore are identified by VMware Carbon Black products as known malware and as such will be blocked by standard policies. Although this threat has not been seen recently in the wild, it could resurface at any time. This post serves to inform our customers about detection and protection capabilities within the VMware Carbon Black suite of products against CrescentCore malware for macOS.
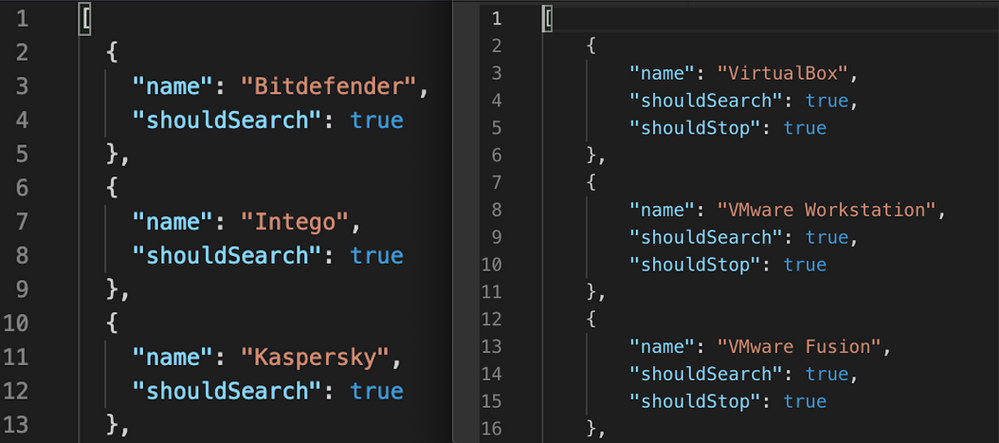
The application contains two configuration files in its resources section, antiviruses.json and virtualmachines.json (depicted below), that define a set of AV and virtualization products that it will check for on the system before execution.
Figure 1: Sample antiviruses.json and virtualmachines.json
At least one variant has been observed to gain root access using the system tool osascript with the command line option “with administrator privileges” and then move the malicious application and plists from /tmp to the Library system directory and then to the user’s Library directory. The established LaunchDaemon and LaunchAgent establish persistence for the malware, causing the application to be started automatically when the system is started or rebooted.
sh -c osascript -e 'do shell script "mkdir \"/Library/Application Support/com.apple.spotlight.Core\";mv /tmp/ddd/Updater.app \"/Library/Application Support/com.apple.spotlight.Core\";mv /tmp/com.google.keystone.plist /Library/LaunchDaemons;launchctl load -w /Library/LaunchDaemons/com.google.keystone.plist;echo Passed" with administrator privileges'
sh -c main_dir_name="com.apple.spotlight.Core";app_name="Updater.app";plist_name="com.google.keystone.plist";mkdir $HOME/Library/$main_dir_name;mv /tmp/ddd/$app_name $HOME/Library/$main_dir_name;mv /tmp/$plist_name $HOME/Library/LaunchAgents;touch $HOME/Library/$main_dir_name/dax;launchctl load -w $HOME/Library/LaunchAgents/$plist_name;
Below is a screenshot of how the execution of osascript invoking a shell command with administrative privileges would appear in the CB Defense console:
Figure 2: Execution of osascript
To learn more, click here.
Remediation:
MITRE ATT&CK TIDs
| TID | Tactics | Technique |
|---|---|---|
| T1064 | Execution | Scripting |
| T1159 | Persistence | Launch Agent |
| T1160 | Persistence | Launch Daemon |
| T1150 | Persistence | Plist Modification |
| T1514 | Privilege Escalation | Elevated Execution with Prompt |
| T1144 | Defense Evasion | Gatekeeper Bypass |
Indicators of Compromise (IOCs)
| Indicator | Type | Context |
|---|---|---|
| 638004ee6a45903dcbf03d03e31d2e83c6270377973a64188f0b89d4062f321e | SHA256 | CrescentCore DMG |
| 45eab9f25158b677877a447b052f024c44c80744bcfae59deb660c47a9cbf1ac | SHA256 | CrescentCore DMG |
| b111891b698dfdafb6952b0cf89aaebde51c5c1758df316e6b843624ed2db205 | SHA256 | CrescentCore DMG |
| 8938e48a0b0f8765a017d2e25ed5a68bd7954d220e460c5aa4b1c59763ec5a8d | SHA256 | CrescentCore DMG |