VMware has released a critical security update for its VMware vRealize Log Insight products, which addresses multiple security vulnerabilities (CVE-2022-31706, CVE-2022-31704, CVE-2022-31710, CVE-2022-31711). To fully remediate the vulnerabilities VMware vRealize Log Insight must be upgraded to 8.10.2.
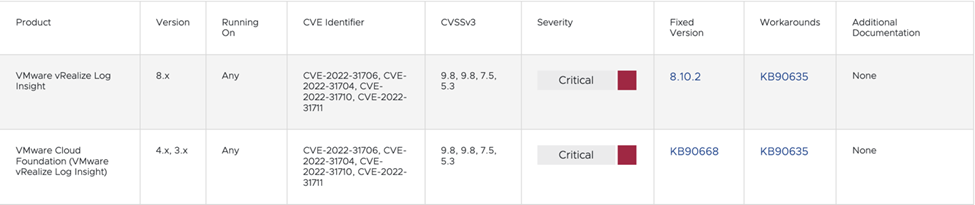
This critical security advisory impact of the VMware vRealize Log Insight version 8.x that you are running requires you to download a patch file from the KB article below.
We’ll use KB90635 to apply the fix.
| Product Component | Version(s) |
| VMware vRealize Log Insight | 8.x |
We’ll show you how to apply the VMSA-2023-0001 patch for VMware vRealize Log Insight Appliance (vRLI) version 8.8.2 in this post.
Before you begin
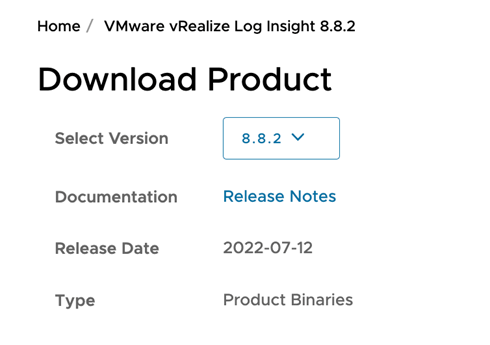
- Navigate to the VMware vRealize Log Insight, a product download page, and choose the version you’re using. We are using VMware vRealize Log Insight version 8.8.2 in this article.
2. Download the zipped file KB90635_3.zip (approximate file 2.65 KB
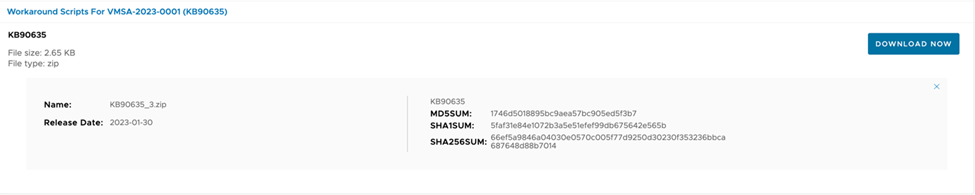
This contains 2 files
2.1) KB90635.sh
2.2) KB90635_validate.sh
3. Using the SCP protocol, transfer 2 files to each VMware vRealize Log Insight Appliance node in the cluster. Tools such as winscp can also be used to transfer the file to the appliance.
4. Unzip the file and put it in the “/opt/vmware/bin” directory.
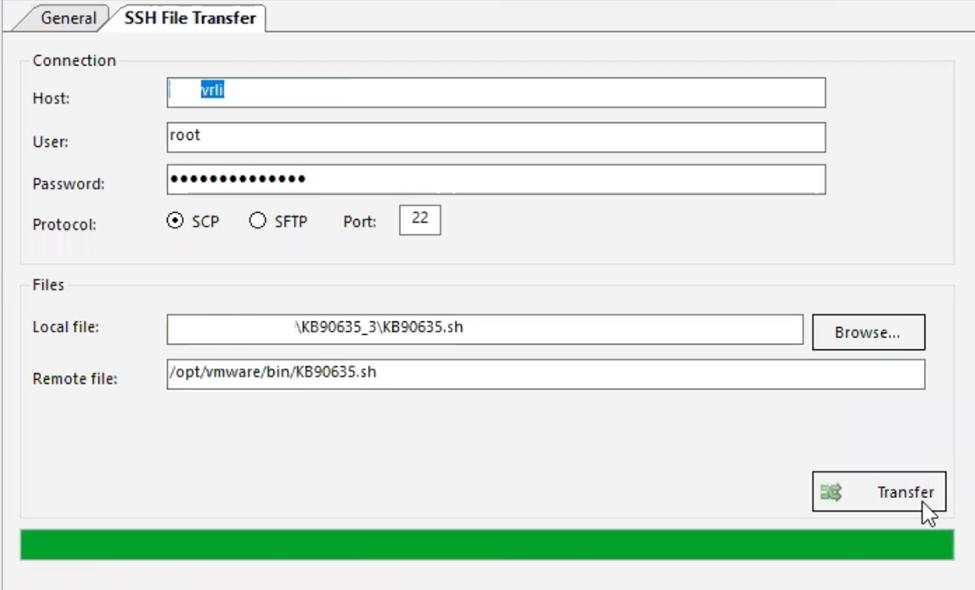
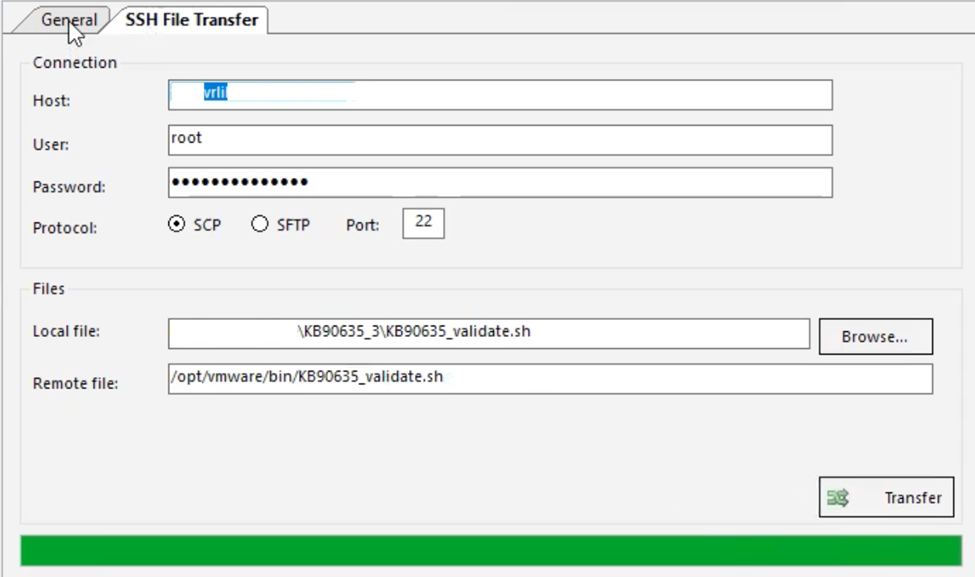
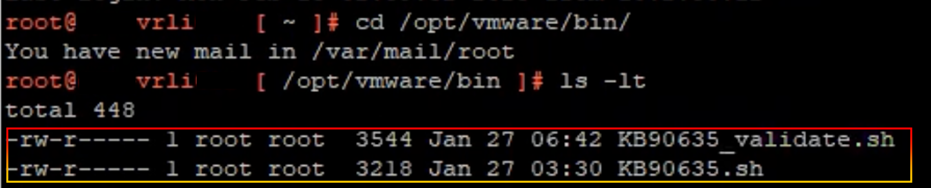
5. SSH into the VMware vRealize Log Insight Appliance and verify that there are already 2 files in the “/opt/vmware/bin” directory.
6. Run a script validation procedure to check the results prior to applying the script patch.
- Connect to VMware vRealize Log Insight Appliance with ssh.
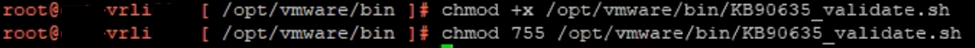
- The commands listed below should be used to modify the file’s permissions and make it executable.
chmod +x /opt/vmware/bin/KB90635.sh
chmod 755 /opt/vmware/bin/KB90635.sh
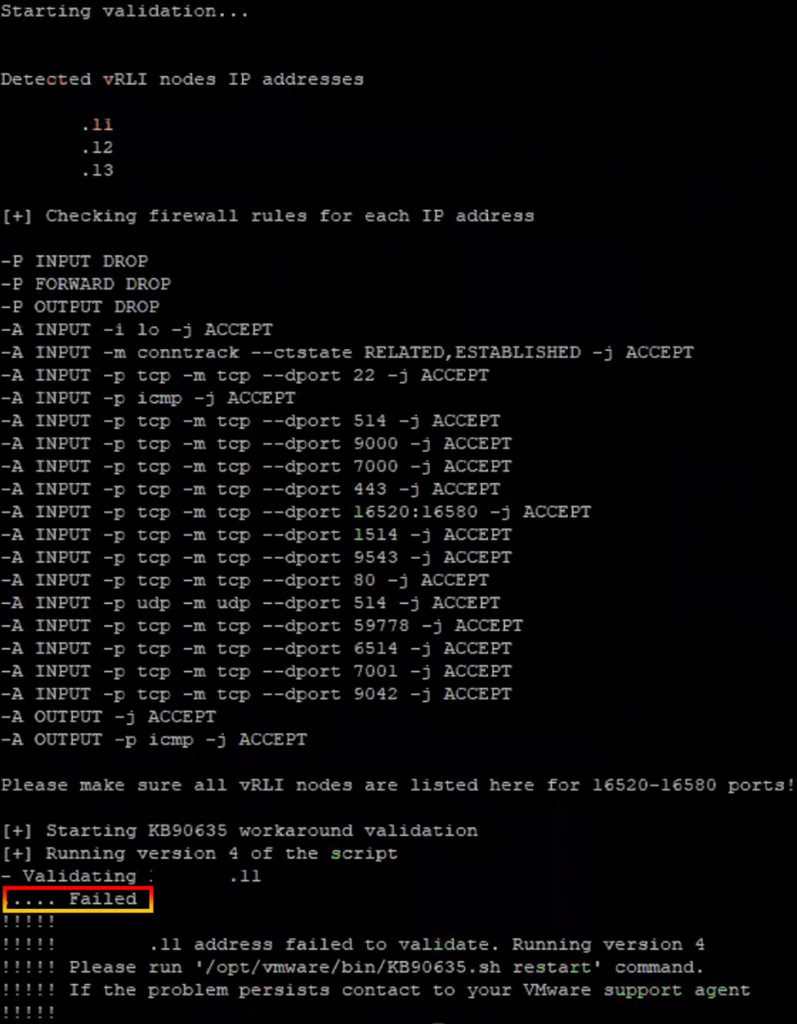
- Run the command to perform the validation steps.
/opt/vmware/bin/KB90635_validate.sh

- As a result, the message “Failed” will appear.
Patch deployment procedure
- Take a VMware vRealize Log Insight snapshot before applying a fix. If you are operating a VMware vRealize Log Insight cluster, take a snapshot of each VMware vRealize Log Insight node in the cluster:
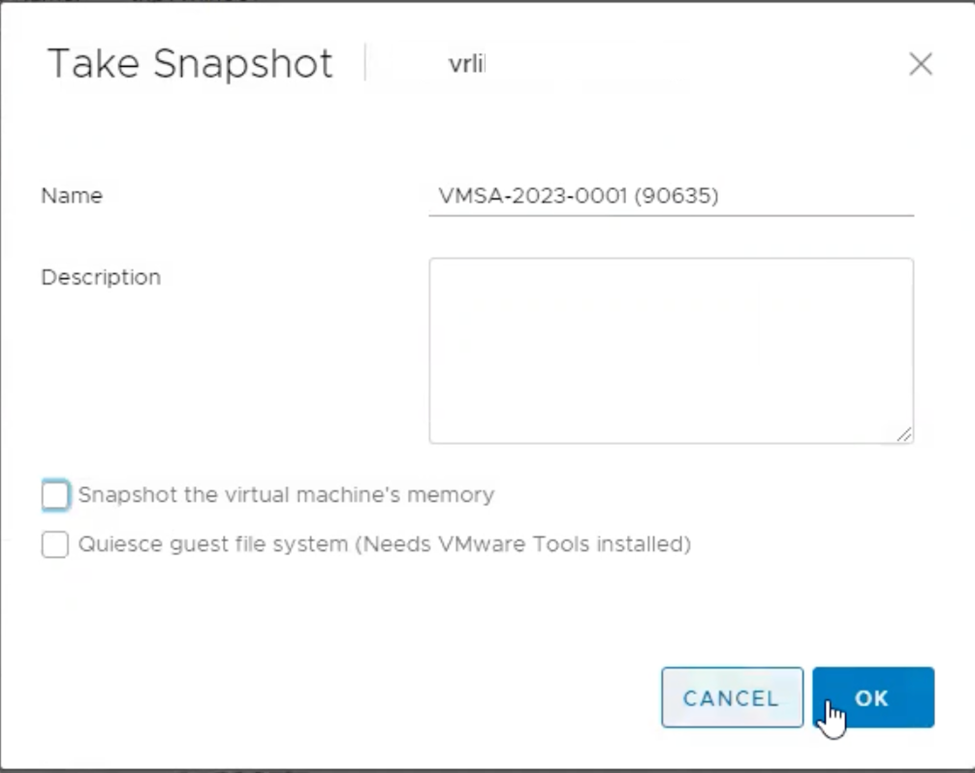
2. SSH to VMware vRealize Log Insight Appliance.
3. Log in as root to VMware vRealize Log Insight Appliance.
4. Navigate to the “/opt/vmware/bin” folder and use the “cd” command.
5. Run the instructions below to change the file’s permissions and make it executable.
chmod +x /opt/vmware/bin/KB90635.sh
chmod 755 /opt/vmware/bin/KB90635.sh

6. Run the script, passing the “setup” option.
/opt/vmware/bin/KB90635.sh setup
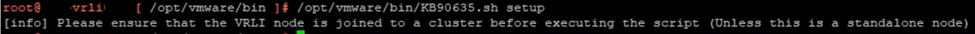
7. Continue to the next node in the cluster and repeat steps 1-6 for each appliance.
Patch deployment validations
Perform the following steps for each VMware vRealize Log Insight node in the cluster to validate the workaround for VMSA-2023-0001:
Before continuing with the workaround, please check that you have completed the preceding procedures on ALL nodes in the cluster.
1. SSH to VMware vRealize Log Insight Appliance.
2. Log in as root to VMware vRealize Log Insight Appliance.
3. Navigate to the “/opt/vmware/bin” folder and use the “cd” command.
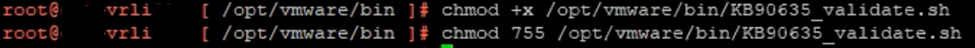
4. Run the instructions below to change the file’s permissions and make it executable.
chmod +x /opt/vmware/bin/KB90635_validate.sh
chmod 755 /opt/vmware/bin/ KB90635_validate.sh
5. Run the command to perform the validation steps.
/opt/vmware/bin/KB90635_validate.sh

6. As a result, the message “Congratulations!” will appear.
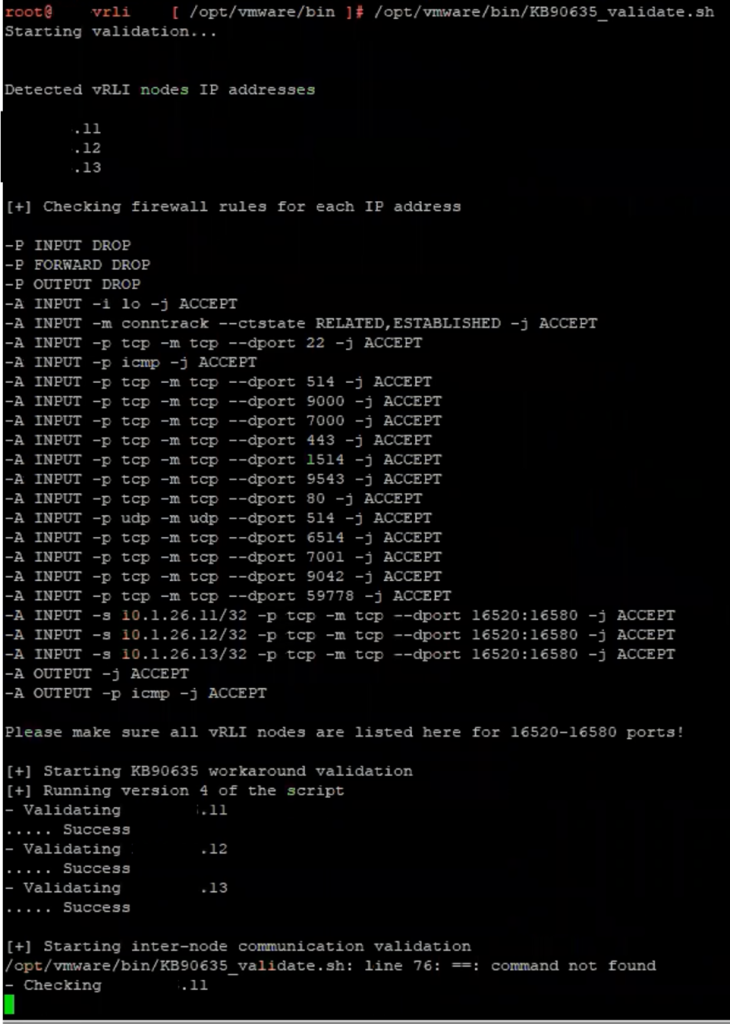
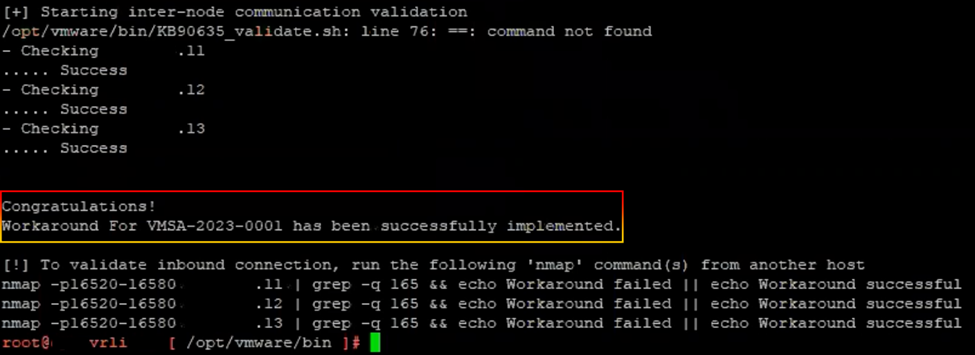
As a result, when we execute validate scripts, we can observe that the validated script will also verify the other node in the cluster and ensure that no errors are reported.
Technical advice and recommendations
The VMware security team has published a list of critical vulnerability alerts.. The VMware vRealize Log Insight contains a Directory Traversal Vulnerability meaning an unauthenticated, malicious actor can inject files into the operating system of an impacted appliance which can result in remote code execution. To reduce the risk to your VMware environment, we recommend applying the patch or upgrade version as soon as possible.






