We’re thrilled to announce the general availability of VMware NSX 4.0.1.1, another exciting release with updates in networking, security, and operations for private, public, and multi-clouds.
With this release, VMware NSX customers will be able to leverage accelerated NSX networking and security performance, enhanced network observability, and new network monitoring and troubleshooting features for increased flexibility.
NSX 4.0.1.1 will also deliver enhanced threat detection and prevention capabilities, helping customers bolster network defenses to block advanced threats from moving laterally across multi-cloud environments.
Read on to get the details on our latest NSX release.
Distributed Malware Prevention
The NSX Distributed Firewall has added malware detection and prevention support for Linux guest endpoints (VMs). Linux has become the most common operating system across multi-cloud environments, powering more than 78% of the most popular websites. With the recent emergence of more Linux-specific threats, and current malware countermeasures being mostly focused on addressing Windows-based threats, there is an imperative to address the specific security needs of Linux machines. Adding Linux to our prevention solution enables the NSX Distributed Firewall to provide more effective prevention coverage and fewer false positives across multi-cloud environments.
In addition, we expanded the support for malware analysis for known and unknown files. Along with hash-based detection for new files, we added support for local and cloud analysis for unknown files of up to 64MB.
Distributed Intrusion Detection & Prevention (IDS/IPS)
NSX Distributed IDS/IPS now provides the flexibility to choose how you want to service a flow in conditions such as CPU oversubscription. Once you reach a pre-defined CPU threshold you can configure the system to drop or bypass the IDS/IPS engine. You can also choose to apply this behavior at a rule level providing flexibility to service different applications based on business needs.
NSX Gateway Stateful Active-Active Services
Prior to NSX 4.0.1.1, the NSX Gateway supported Active/Standby High Availability mode where traffic is forwarded through a single active NSX Gateway. This deployment mode required additional design and architecture considerations such as limits induced by the Active/Standby mode on bandwidth and CPU utilization.
Deploying stateful services on Tier-0 and Tier-1 gateways in Active-Active HA mode will allow you to use the full power of the NSX Gateway cluster to scale out and scale in your services as needed including L4-L7 Gateway Firewalling, URL Filtering, NAT, and TLS proxy – all from a single NSX Manager. Support is included for both bare metal and VM form factors for deployment flexibility.

Additionally, 4.0.1.1 brings added support for malware detection to the NSX Gateway Firewall running directly on bare metal, allowing for consistent protection regardless of whether customers choose a virtual or physical form factor.
DPU-based Acceleration for NSX
DPU-based Acceleration for NSX is a result of Project Monterey—an initiative that VMware began two years ago. VMware NSX customers can now leverage DPU-based acceleration using SmartNICs. This new implementation allows customers to run NSX networking and security services on DPUs, providing accelerated NSX networking and security performance for applications that need high throughput, low latency connectivity, and security. The DPU-based implementation also enhances network observability across different workload types while simultaneously increasing the host resources available to applications.
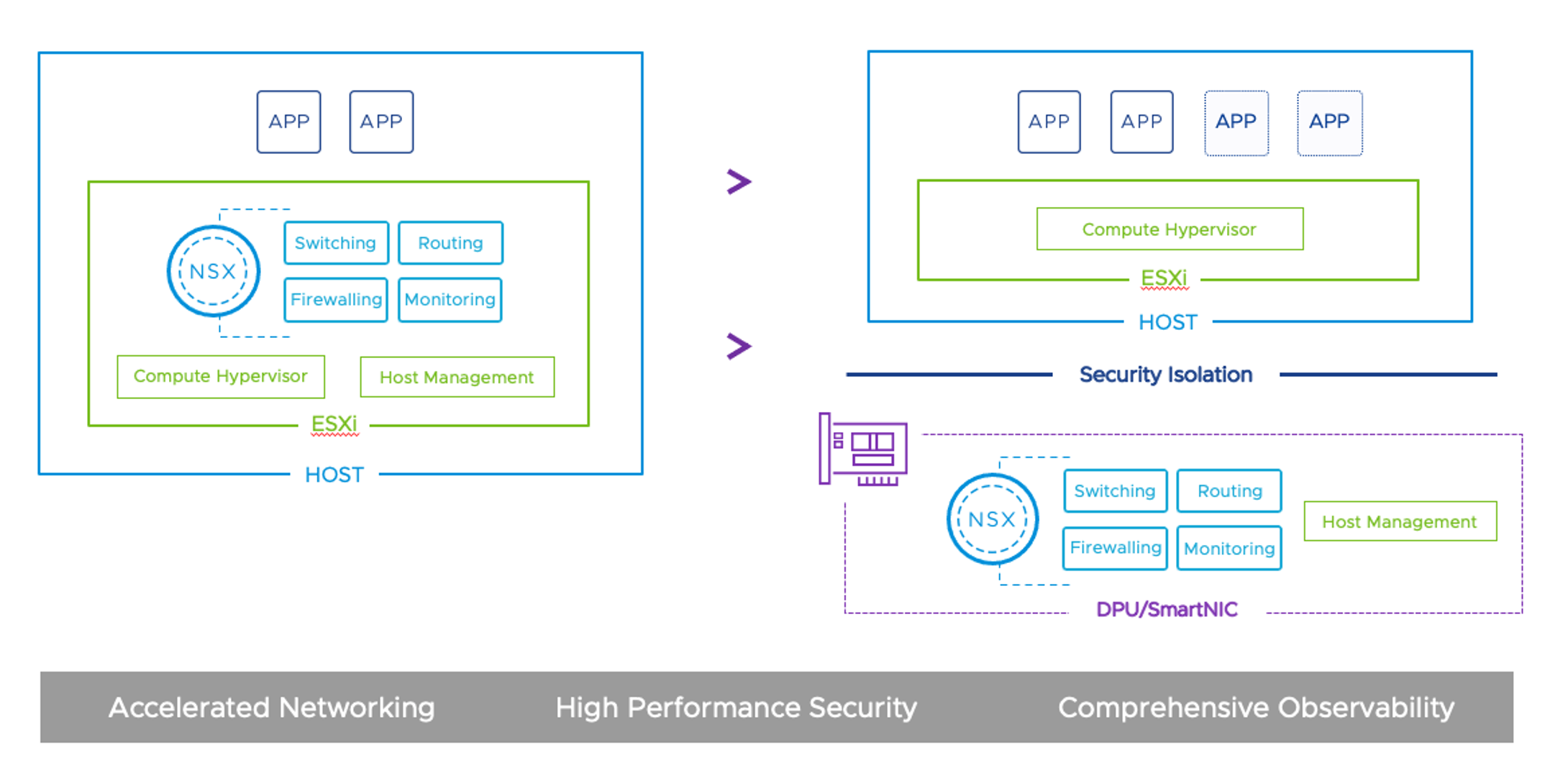
VMware is delivering on Project Monterey with VMware vSphere 8, announced at VMware Explore. Combined with other future innovations introduced by Project Monterey, such as the ability to support VMware Cloud Foundation (VCF) networking and storage for bare-metal workloads, DPU-based NSX acceleration will free up networking and security teams and developers more than ever from depending on generic host computing resources to power operations.
Network Monitoring with Time-Series Metrics
New NSX Edge monitoring metrics – NSX 4.0.1.1 introduces 16 additional NSX Edge metrics that further enhance monitoring and troubleshooting. This includes flow cache metrics, queue occupancy for fast path interfaces, and NIC throughput on ingress and egress on the NSX Edge fast path interfaces. These new metrics are available through NSX Application Platform – Metrics API.
Enhanced UI for NSX Edge monitoring metrics – NSX Edge Transport Node Monitoring user interface is enhanced to show Current Packets Processed, Highest Packets Processed, and Packets Processed Trend over time. Enhances NSX Edge Network Interface Statistics > Dropped Packets Trend UI page to show Rx packet drops per second (due to memory buffer allocation failures, due to lookup match failure).
Enhanced UI for NSX Tier0 & Tier1 Gateway Interface Statistics – Adds UI trend charts to show Tier0 and Tier1 Gateway Network Utilization Trend, to show IPv4 vs IPv6 packets per second
NSX for vSphere to NSX-T Migration
Bring your own Topology for NSX Load Balancer – As part of the deprecation of the NSX Policy APIs for the NSX Advanced Load Balancer (NSX ALB), the migration coordinator now adds support for configuration migration from the NSX for vSphere Load Balancer to the native NSX Load Balancer (configuration only) in addition to in-place migration which was previously supported.
Configuration and Edge Migration in NSX Migration Coordinator – The migration coordinator introduces a new mode that supports both configuration and edge migration. It also establishes a performance-optimized distributed bridge between the source NSX-V environment and the destination NSX-T environment to maintain connectivity during the lift and shift migration. Additionally, customers can leverage a compatible HCX release for workload migration. This mode is available for local manager only.
Summary
The NSX 4.0.1.1 release delivers exciting new updates across NSX use cases for private, public, and multi-clouds. The release is generally available along with detailed Release Notes covering all the features and capabilities included.
Follow us on Twitter @vmwarensx and LinkedIn for updates, and stay tuned for additional blogs on the key capabilities and features in NSX 4.0.1.1.


Comments
0 Comments have been added so far