The Evolution of VMware NSX Service-defined Firewall
Today, many people take micro-segmentation for granted. It’s incredible to recall that just a few years ago, VMware introduced micro-segmentation to support the concept of Zero Trust — a security model that does not automatically trust entities within the security perimeter. Fast forward to the present, and many people have embraced that concept and made it their own. Meanwhile, VMware has extended its solution for micro-segmentation into a full-blown internal firewall. Let’s step back in time and see how VMware progressed from the initial micro-segmentation use case to today’s powerful Service-defined Firewall, deployed by thousands of organizations.
Pioneering the Market for Micro-segmentation
Back in 2013, VMware pioneered micro-segmentation with the release of VMware NSX, the VMware network virtualization and security platform, which propelled VMware into the world of software-defined network and security virtualization. This initial release enabled customers to run a complete Layer 2-Layer 4 stack in software. The guiding philosophy was to make world-class security easy to operationalize.
Some customers used NSX for network segmentation: they created virtual security zones in software where they had previously used hardware. Other customers adopted NSX for micro-segmentation: they were now able to provide granular protection for apps in the data center. A typical usage pattern involved securing virtual desktop infrastructure (VDI) by centralizing all traffic on the data center.
Soon, VMware customers wanted to extend micro-segmentation to include Layer 7 application-ID and user-ID based policies. These customers also wanted to segment their data center applications but were concerned about managing a large number of security policies — especially in a fast-paced data center.
Layer 7 Access Controls and Policy Automation
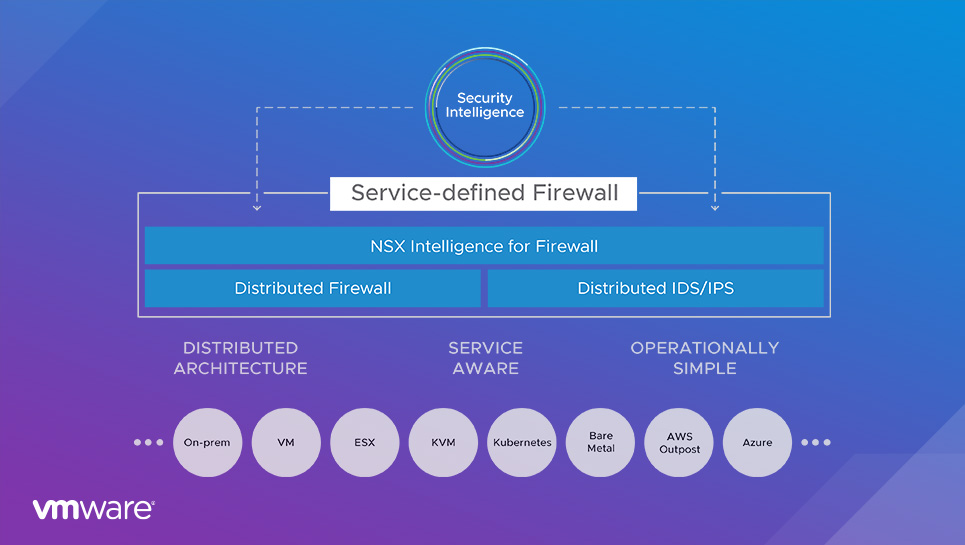
VMware responded to customer feedback by adding a complete suite of Layer 7 access controls. The company also leveraged the distributed architecture of NSX to automate security policy management: it created NSX Intelligence to analyze application traffic, make policy recommendations, deploy and enforce policies, and monitor traffic for policy compliance. This capability processes all packets inline as they move through the hypervisor, collecting information about apps and their communication flows. The data is analyzed centrally, creating a comprehensive topology map of applications and flows that allows NSX to automatically generate recommendations for security policies.
Policy automation is leading to a significant increase in the number of customers considering the Service-defined Firewall. The ability to visualize and gain deep insight into all flows across the data center, and to embed security management within the NSX UI, meant that customers could significantly increase the number of applications they protected with the Service-defined Firewall.
Naturally, with increased usage came more requests: in addition to access controls, customers began to ask for threat controls. And because threats often masquerade as normal-looking traffic, it isn’t enough to settle for traffic-blocking rules.
Enhanced Threat Control with IDS/IPS
VMware enhanced the platform’s capabilities to add threat control via an intrusion detection/prevention system (IDS/IPS), which scans traffic and uses predefined signatures to identify threats. A critical use case for the IDS/IPS capability in the Service-defined Firewall is regulatory compliance: customers can easily set security policies to enable IDS/IPS inspection for all traffic flows in the compliance zone, without requiring new hardware.
The inclusion of IDS/IPS in the Service-defined Firewall means that customers can now replace internal physical firewalls with the Service-defined Firewall, since it provides fine-grained policies at scale to secure east-west traffic — without the need for additional firewalls. Armed with contextual knowledge of all workloads within the hypervisor, the Service-defined Firewall can be intelligent about how rules and signatures are applied, resulting in more efficiency, optimized traffic flow, zero inspection bottlenecks, and much better security coverage.
A Widely Accepted Internal Firewall
Building on the foundation of NSX, VMware has accomplished what few others have: an elegantly simple solution that leverages centralized policy management to enable customers to quickly turn on advanced analytics and threat control — all in a single software-defined internal firewall.
The results are impressive. Several enterprise customers have 10,000+ NSX Service-defined Firewall instances deployed — and the largest deployment has over 250,000 workloads under protection. NSX has thousands of customers using the Service-defined Firewall functionality — a much larger footprint than any other micro-segmentation vendor. No wonder NSX clocked $1.7B in bookings and grew at 30% in fiscal-year 2020.
The Service-defined Firewall has received acceptance and acclaim from customers around the world. VMware continuously works to incorporate customer feedback as a primary driver for increased capabilities that are centrally managed and coordinated. Point products can only accomplish some of this, and often result in a fragmented approach to security that’s exacerbated by poor communication and complex management requirements. In contrast, VMware NSX makes world-class security easy to operationalize.
In Summary
The VMware Service-defined Firewall is a distributed, scale-out internal firewall that protects all east-west traffic with security that’s intrinsic to the infrastructure, radically simplifying the security deployment model. From its humble beginnings providing micro-segmentation with only Layer 2-4 policies, NSX has evolved into a complete, stateful Layer 2-7 firewall with an intrusion detection/prevention system (IDS/IPS) and deep analytics via VMware NSX Intelligence.
To learn more, download the VMware white paper “Internal Firewall: The Best Way to Protect East-West Traffic.“







