Mobile single-sign on and device compliance with Workspace ONE UEM are essential methods to secure devices that access corporate applications. However, without user-facing authentication, these applications are still susceptible to preventable attacks on compliant devices.
Since the start of the coronavirus pandemic in 2020, the daily number of cybercrimes reported to the FBI has tripled. Users are increasingly directly targeted for their access to sensitive information, taking advantage of this time when more people are more vulnerable due to working from home or public locations on less secured networks. Attackers are also becoming more intelligent at phishing, crafting fake emails from seemingly legitimate sources.
For instance, can you tell that this is a phishing email?
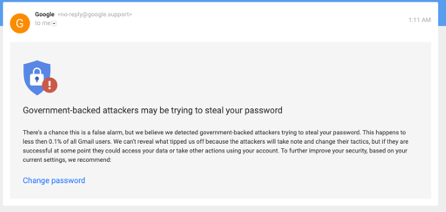
A vigilant user or a trained employee may know to hover over the “change password” button and notice that it redirects to a suspicious link; otherwise, anyone could easily fall for a phishing attack. This is why all companies need to have multi-factor authentication to add resistance to phishing, gating the end-user’s access to work applications.
Many of our customers leverage device management with certificate authentication, which is excellent for providing users with seamless, authorized access on a compliant device. What device management does not do is provide the necessary authentication that the intended user is the current user handling the device.
While physical breaches from mishandling a corporate device may feel unlikely, remember that it can just take one incident to cause major business disruption. Some of the worst cyberattacks in history came from breaches in physical security. In 2008, it was a random USB drive picked up from the parking lot of a U.S. military installation and inserted into a Department of Defense computer that spread malicious code throughout the U.S. military’s networks. Now, imagine an analogous situation that might happen today: an employee temporarily leaving their corporate laptop unlocked in an open coworking space. What layers of security does your company have to ensure that only the device owner can be granted access to launch applications containing highly confidential company data?

With mobile single-sign on, it is the goal of Workspace ONE Access to make access feel magically simple, but we often need another factor for identity – something you have, something you know, or something you are – to ensure a higher level of authentication.
Implementing multi-factor authentication does not need to be complicated or happen at the expense of user experience either! To make implementing multi-factor authentication simple, Workspace ONE Access has a set of built-in multi-factor authentication methods that can be configured and used for a variety of customer use cases. By providing options that are compatible with managed devices and personal devices, Workspace ONE Access is bringing multi-factor authentication capabilities to all users on any device.










