This blog is part of a series to help organizations of any size optimize their security. Our experts provide insights and recommendations based on common security use cases, customer questions and security developer needs.
It’s no secret that the number of cyber threats and cyberattacks continues to grow in every industry. Organizations both large and small must take a serious stance on security to maintain their customers’ and employees’ trust.
But is there a way to do this when you don’t have a conglomerate-sized budget? If you plan your security operations center (SOC) wisely, you’ll get the security posture you need with the budget you have.
If you don’t already have a SOC, why do you need one? A SOC will help you detect, prevent and resolve threats in real-time from a centralized view. It will help your organization respond to incidents as quickly as possible so you can minimize damage and data loss across all your critical applications, devices, systems and clouds. A SOC is especially recommended if your business stores any customer or employee information or is subject to industry or government regulations.
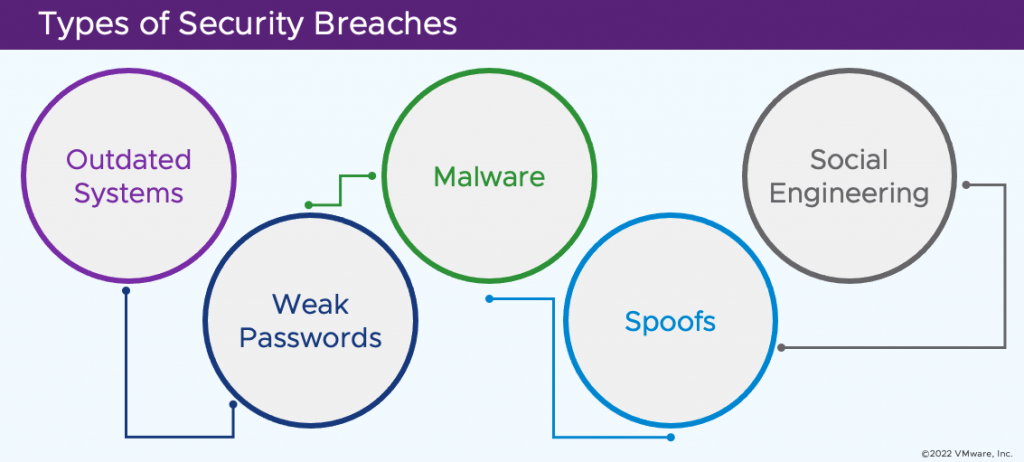
What are the most common security breaches?
The most common types of breaches to guard against and plan for in your SOC include the following:
- Outdated or legacy systems are vulnerable to exploit attacks due to lack of manufacturer support.
- Cybercriminals or nefarious software can crack weak and common passwords.
- Malware attacks, such as ransomware attacks, often infiltrate through phishing emails when someone on your network clicks a link.
- Spoofed websites deliver malware or viruses.
- Social engineering breaches occur when people share sensitive information with a cybercriminal posing as a legitimate group, such as the IT department.
What does a SOC do?
A SOC provides surveillance of all your networks, applications, hardware and software and will monitor and manage prevention systems, remediation solutions and troubleshooting needs. It helps with the enforcement of security policies and procedures, third-party vendors, security log analysis, and data backup, storage and recovery.
For a SOC to be fully optimized, it should include staff who are experts in all the tools used within the organization. This will enable them to resolve and remediate security vulnerabilities and will also help them investigate the root cause of any issues to prevent future breaches.
What is a SOC made of?
Investing in the tools that fit your environment is another key aspect of optimizing your budget. The following are some of the most common needs within a SOC.
- Asset discovery system: Discovers, catalogs and monitors all IT assets within your organization
- Data monitoring: Tracks and evaluates data integrity and security
- Endpoint protection: Protects your network from any device that connects to it or lies within it
- Firewall: Monitors all incoming and outgoing traffic on your network and blocks unauthorized traffic
- Governance, risk and compliance (GRC) system: Ensures compliance with industry or government policies and regulations, if applicable
- Log management system: Logs all messaging from every IT asset within your organization
- Security automation: Automates testing and remediation for vulnerabilities
- Security information and event management (SIEM): Supplies visibility of all activity within your network
- Vulnerability scanners and penetration testing: Searches for vulnerabilities and weaknesses within your network
Whether you decide on an internal SOC with full-time staff, a virtual SOC made up of a mix of employees and contractors, or an outsourced SOC that’s externally managed, accurately determining which technology investments you need to make can be the difference between effective security operations and having expensive technology sitting on the sidelines.
Who works in a SOC?
Defining the right staff for your SOC will ensure that it runs smoothly and makes the most efficient use of everyone’s skills. A SOC should include incident responders, experts who can quickly assess the root level and infrastructure location of an issue, high-level personnel actively searching for vulnerabilities, and managers to oversee team activities including assignments, training and hiring.
Staff should understand different operating systems, security engineering and architecture, and application and network security in addition to all the technology tools used within the SOC. Different members of the team should also be able to complete tasks related to ethical hacking, cyber forensics and intrusion prevention systems.
SOC staff typically possess strong programming skills in multiple programming languages and security certifications, such as Certified Information Systems Security Professional (CISSP) and CompTIA Security+ certification.
A key aspect to retaining in-demand SOC staff is to make active investments in continuous training and in enough staff to prevent burnout.
Get started building your SOC
If you’re not sure what your organization needs or how to begin to analyze your current security posture, a security assessment can help you understand any security gaps, vulnerabilities and possible remediation needs to consider as you start your SOC journey.
Learn more about security assessments and security operations on our Professional Services for Security pages or contact us at [email protected].





