We are happy to share that VMware Cloud Director Availability 4.2.1 is now GA and includes an extension to one of the features that came with VMware Cloud Director Availability 4.2 – the automated on-premises network stretching.
What’s new?
VMware Cloud Director Availability 4.2 introduced the automated on-premises Layer 2 network extension to the cloud. However, it only supported VMware Cloud Director clouds backed by VMware NSX-TTM Data Center.
Because there is still a significant share of Cloud Providers who use VMware Cloud Director with VMware NSX® Data Center for vSphere® in their clouds, with 4.2.1, we add the capability to stretch an on-premises network to such clouds as well.
Now you can offer your tenants a smoother migration path to your cloud, no matter if you use NSX-T Data Center or NSX Data Center for vSphere!

Interoperability
To utilize this new feature, all the VMware Cloud Director Availability appliances (Cloud and On-premises) need to be upgraded to 4.2.1.
The cloud site should be running VMware Cloud Director 10.x and NSX Data Center for vSphere 6.4.10 or later.
Requirements and Limitations
- Only Routed Org VDC networks with Subinterface interface type can be used as Server networks as only networks that are attached to the Trunk interface of the NSX Data Center for vSphere Edge.
- Guest VLAN Allowed should be deactivated on the network. If it was initially activated and then deactivated, the network should be recreated with deactivated as the initial state of the setting.
- After creating an L2 VPN Server Session, the selected Server Network(s) cannot be changed. To be changed, the Server session needs to be recreated.
- For VLAN-based Org VDC networks, the Trunk interface should be manually created by the Provider.
- For large-scale setups (50 or more paired vCenters), there is a known issue with NSX Data Center for vSphere where the Edge VM crashes due to a kernel panic issue. It leads to IO failing to run in Edges which are facing this kernel panic issue.
- The Edge Gateway deployment should not be changed after the initial setup. In cases when it needs to be changed from Compact to Large, the IPSec configuration should be removed and the L2 Server Session should be recreated.
Cloud Configuration
There are two things a provider needs to do to enable their tenants to stretch on-premises network to the Provider’s cloud:
1. Register the NSX Data Center for vSphere Manager in the VMware Cloud Director Availability UI. In this step, the Provider will enter the NSX Data Center for vSphere administrator password and accept its certificate to establish a trusted relationship with VMware Cloud Director Availability.

2. Create an L2 VPN Server session specifying the IP addresses and network(s) used for the stretch. This step can be executed by the Provider or by an Org Admin in case of self-service.
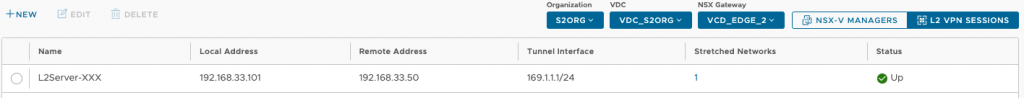
On-Premises Configuration
Like the NSX-T Data Center case, stretching an on-premises network to an NSX Data Center for vSphere backed cloud requires the VMware® NSX Edge™, also known as ‘NSX Autonomous Edge’, and is done in just four simple steps.

No extra cost is involved as there is no need for an NSX license.
You can see the whole configuration process in this video. For more details, please refer to the official VMware Cloud Director Availability documentation and watch the full demo video in YouTube.
Upgrade
If you are running an older version of VMware Cloud Director Availability, please refer to the upgrade guides to get it up-to-date.
- VMware Cloud Director Availability Upgrade Guide for Providers
- VMware Cloud Director Availability Upgrade Guide for Tenants
Remember, to get the latest updates check this blog regularly, you also can find us on Slack, Facebook, Twitter, LinkedIn as well as many demo videos and enablement YouTube, especially our Feature Fridays series!




