In the latest version of VMware Cloud Director – 10.5, there is now support for NSX Federation. This new capability allows service providers to deliver a common network and security across different locations, each managed by separate, regional NSX Manager instances within a single VMware Cloud Director environment.
Providers can register an NSX Global Manager in VMware Cloud Director (VCD) and utilize NSX Federation (global) constructs. In VCD, the feature is consumed by a new type of Data Center Group – Universal – that can include Organization Virtual Data Centers (VDCs) from multiple network fault domains or, in other words, various NSX Local Managers.
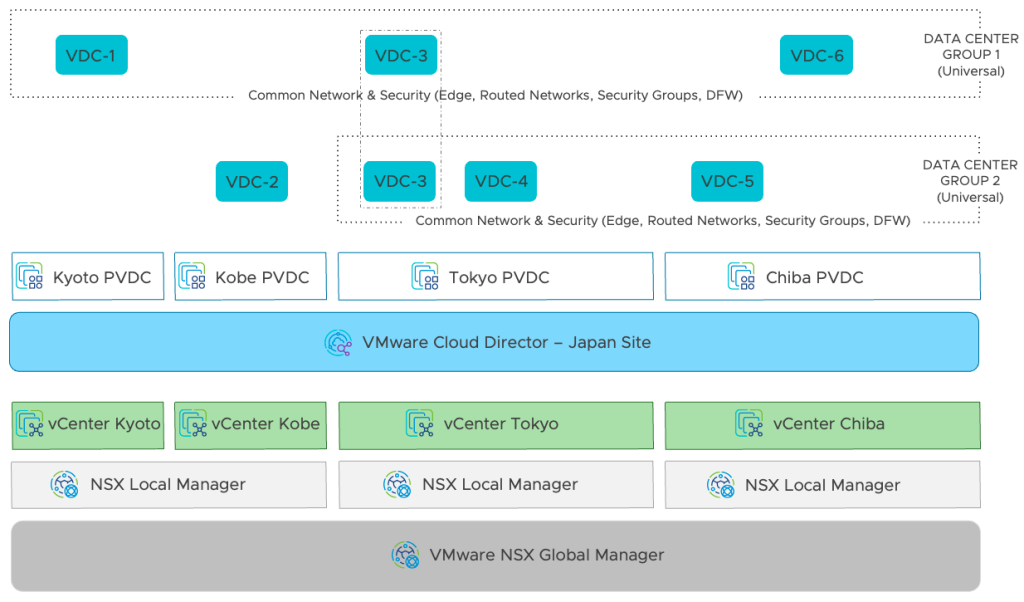
With the ability to include up to 16 VDCs, backed by up to 4 NSX Manager instances in a single Universal DC Group, organizations gain enhanced, scalable and flexible VCD infrastructure. The VCD Provider Gateway, which can now be backed by an NSX Federation, multi-location, stretched Tier-0 Gateway, defines the boundaries of that Universal DC Group.
Only Have Few Minutes?
Watch this 7-minute demo for a quick preview of how providers and tenants can consume and benefit from the VMware Cloud Director integration with NSX Federation.
Integration Deep Dive
The NSX Federation infrastructure has to be set up upfront with a Global NSX Manager cluster, and the respective Local NSX Manager clusters have to be added to the Global as Locations. The provider has to register all Local NSX Managers and their Global NSX Manager instance as Infrastructure Resources in VCD. The integration also provides support for global Segment Profile Templates configuration.

If the provider wants to utilize NSX Federation to deliver unified networking and security across locations, a Global Tier-0 Gateway/s must be created to stretch the different locations depending on the desired network topology. The stretched Tier-0 Gateways can be deployed in various fashions:
- Stretched Active-Active Tier-0 Gateway with Primary and Secondary Locations
- Stretched Active-Active Tier-0 Gateway with All Primary Locations
- Stretched Active-Standby Tier-0 Gateway with Primary and Secondary Locations
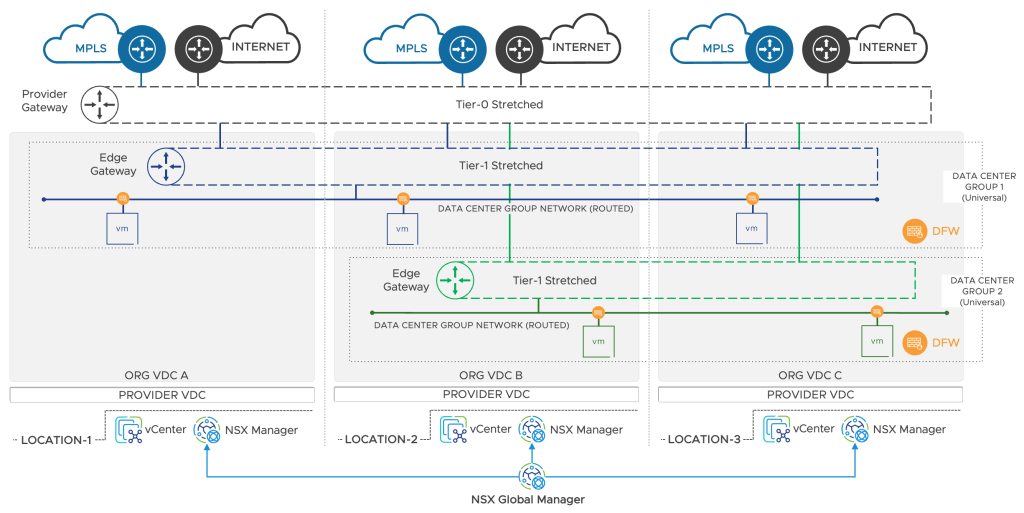
It is important to note that integrating NSX Federation with VCD does not alter how the provider virtual data centers (PVDC) are defined. Each PVDC is backed by its separate Local NSX Manager and respective GENEVE network pool.
Provider Gateway, backed by a Global Tier-0
Providers have the ability to select a Global NSX Manager when creating a Provider Gateway. This allows them to choose a backing Global Tier-0 Gateway, which can stretch across different Locations. One main difference is that IP Spaces is the only IP address management method supported for “Global” Provider Gateways.
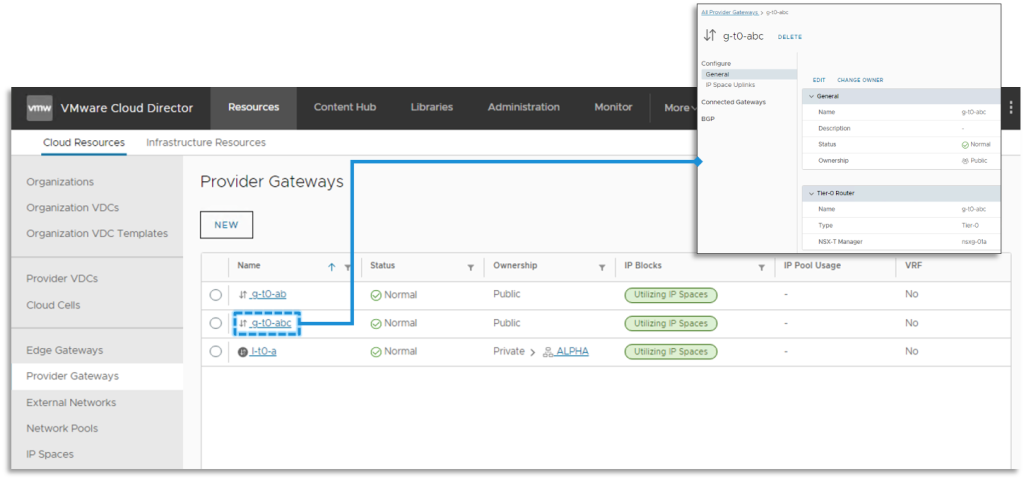
The following rules apply to “Global” Provider Gateways:
- Any Edge Gateway can be connected to a “Global” Provider Gateway.
- An Edge Gateway created in a Universal DC Group context must be connected to a “Global” Provider Gateway.
- The “Global” Provider Gateway VDCs span must be a superset of the Universal DC Group VDCs span.
Data Center Group of type Universal
Traditionally VCD tenants can consume Data Center Groups as logical objects containing a set of Organization VDCs where the security and networking are unified. In other words, the PVDCs (backing those Org VDCs) had to be supported by the same Network Pool (NSX Transport Zone).
VCD 10.5 introduces the concept of a Universal DC Group. The VDCs part of such a group can be backed by PVDCs from different vCenters, Datacenters, and Local NSX Managers in the concept of NSX Federation. The Local NSX Managers define the scope of the Universal DC Group.
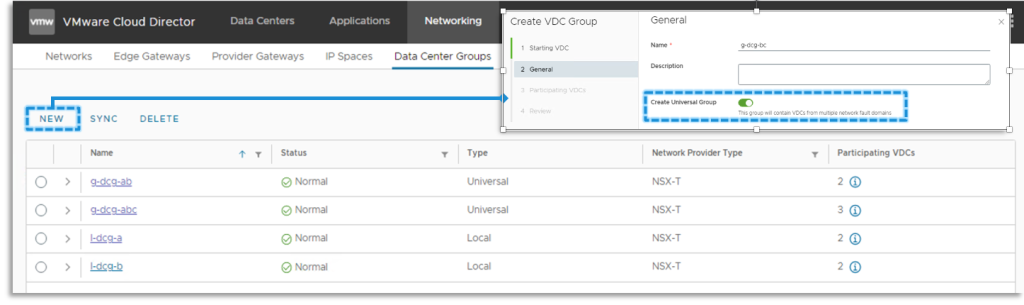
Universal DC Group Networking
Tenants can create and manage Edge Gateway and connected routed network components within a specific Universal DC Group context.
An Edge Gateway defined within the Universal DC Group context is backed by a Global Tier-1 with a Location span matching the VDC to Local NSX Manager mapping. Therefore such Edge must be connected to the appropriate “Global” Provider Gateway. This translates from the NSX Federation architecture requirement that a Global Tier-1 span is equal to or a subset of its upstream Global Tier-0 span. Unlike Local DC Groups, increasing/decreasing the scope of Universal DC Group Edge is not supported.
VCD supports only routed networks in the context of the Universal DC Group. The span of the network covers all VDCs in the Universal DC Group. This again translates from the NSX Federation requirement that a Global segment overlay span always equals its attached Tier-1 or Tier-0 span.

VCD supports only routed networks in the context of the Universal DC Group. The span of the network covers all VDCs in the DC Group. This again translates from the NSX Federation requirement that a Global segment overlay span always equals its attached Tier-1 or Tier-0 span.

Universal DC Group Edge Services
The Edge Gateway default configuration on its backing Tier-1 Gateway Locations mode and Edge Cluster placement is based on the upstream Global Tier-0 Gateway Locations mode and Edge Cluster configuration. However, if there is a need to modify this default setting, it is possible to make the necessary changes from the VCD.
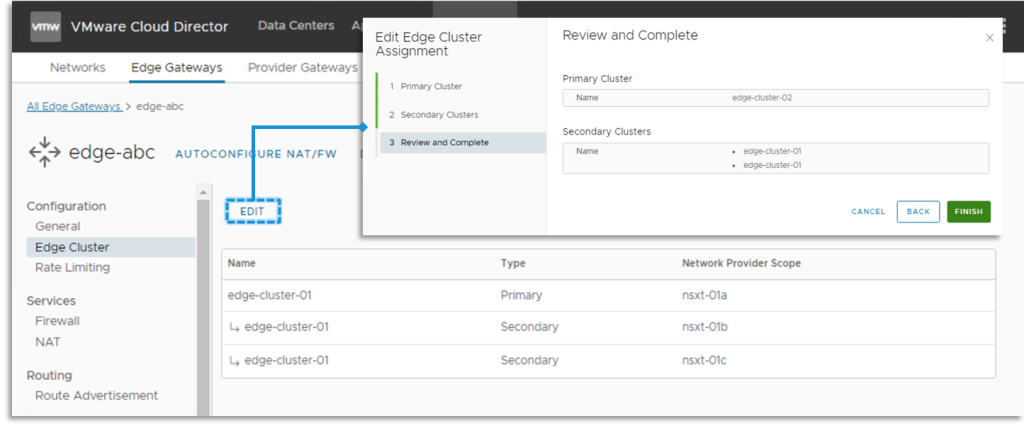
The supported Universal DC Group Edge Services are analogous to the standard Edge, excluding the following significant ones:
- VPN Services (both IPSec and L2VPN)
- BGP and Static Routes
- Load Balancer
The Non-Distributed routing is automatically activated on Universal DC Group Edge and cannot be modified.
Connecting External Networks to a Universal DC Group Edge is impossible because Service Interface cannot be established on a stretched Tier-1 Gateway. Also, the only supported DHCP mode is Relay.
Universal DC Group Security
Security for Universal DC Groups can be consumed on both the Edge Gateway and Distributed Firewall (DFW) levels.
The security objects, such as IPSet, Static and Dynamic Groups, and Applications Port Profiles, are created as Global NSX managed entities and can be used in both security contexts (Edge Gateway and DFW) for the given Universal DC Group. All Universal DC Groups security objects are created in the NSX Federation Global Region scope.
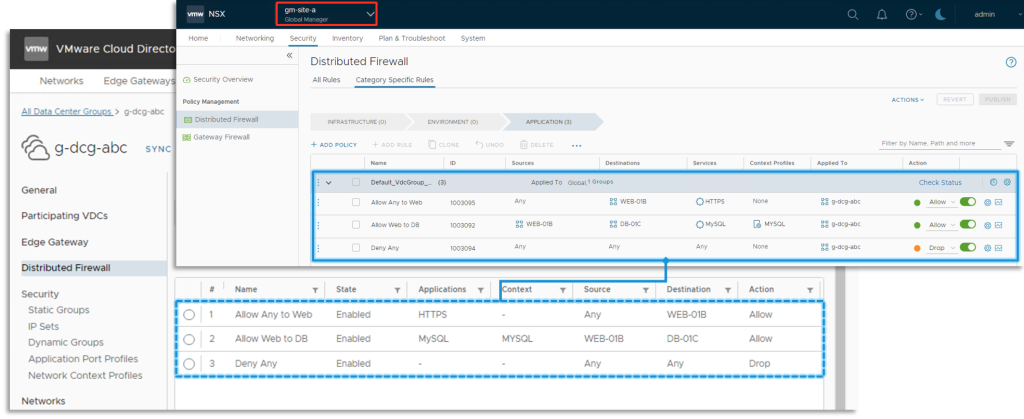
NSX Federation applies the Tags on the Local NSX Manager level. From that perspective, the tags for VMs connected to networks within a Universal DC Group context are handled the same way as for Local DC Group.

On a Final Note
Adding the support for NSX Federated environments in VMware Cloud Director enables providers and tenants to easily scale networking and security services across multiple networking availability zones. This integration aids disaster recovery and business continuity plans by allowing workloads and applications to be moved and replicated across data centers effortlessly. It also streamlines the management of multi-location environments, thus improving both providers’ and tenants’ operational experience.
If you haven’t already, check my previous blogs about VCD 10.5 IP Spaces’ new features.
- Default NAT and Firewall auto-configuration in VMware Cloud Director 10.5
- IP Space Migration in VMware Cloud Director 10.5
Remain up-to-date by regularly checking this blog for the latest updates. You can also connect with us on Slack, Facebook, Twitter, and LinkedIn.
Stay tuned for new demo videos and enablement on YouTube, especially our Feature Fridays series.





