The 10.2 release of VMware Cloud Director introduced key features in the networking and security areas. As part of this VCD release, enhanced NSX-T integration brings advanced functional parity and improvements such as VRF Lite support, Distributed Firewall, cross-VDC networking, NSX Advanced Load Balancer (Avi) integration, and much more! Those improvements have a massive impact on security, operational costs, scale, and efficiency. They will help partners expand their network and security services with VMware Cloud Director and VMware NSX-T Data Center.
VRF Lite Support for Improved Scalability
A VMware Cloud Director external network provides an uplink interface that connects networks and virtual machines in the system to a network outside of the system, such as a VPN, a corporate intranet, or the public Internet.
To provide a fully routed network topology in a virtual data center, you can dedicate an external network to a specific NSX-T edge gateway. In this configuration, there is a one-to-one relationship between the external network and the NSX-T edge gateway, and no other edge gateways can connect to the external network. Dedicating an external network to an edge gateway provides tenants with additional edge gateway services, such as route advertisement management and border gateway protocol (BGP) configuration.
Without VRF Lite, you had to dedicate a complete tier-0 to an external network to offer a fully routed network topology. This leads to a large number of edge nodes, given an NSX-T edge node can support only one tier-0 gateway.
Starting in VCD 10.2, an NSX-T VRF gateway can act as an external network. A single tier-0 gateway can support up to 100 VRFs, which improves a lot the scalability.
NSX-T introduced the support for VRF earlier in 2020 in its 3.0 release. VRF Lite support provides multi-tenant data plane isolation through Virtual Routing Forwarding (VRF) in tier-0 gateway.
From a tenant admin point of view, the consumption of a VRF gateway as an external network is similar to a tier-0 gateway. The only differences reside in the preparation work that has to be accomplished by the provider admin, as a VRF gateway requires a different configuration compared to a regular tier-0 gateway.
The steps for a provider admin are:
- Create a “parent” tier-0 gateway.
- Configure the external interfaces on the parent tier-0 gateway: those external interfaces require a trunk segment.
- Create the VRF gateway in NSX-T: VLAN tagging (802.1q) is used to differentiate traffic between VRFs. As such, access VLANs are used on the VRF gateway interfaces.
- Import the VRF gateway as an external network in the provider portal.

Considerations for VRF Lite support in Cloud Director:
- NSX-T supports up to 100 VRFs per tier-0 gateway, increasing the scale to thousands of dedicated external networks.
- From the tier-0 gateway, the VRF gateway inherits the failover mode, edge cluster, internal transit subnet, T0-T1 transit subnets, and BGP routing configuration.
- The provider can import into VCD as an external network, either the parent tier-0 gateway or its child VRFs, but not both at the same time.
- The overall edges uplink bandwidth is shared across all the tier-0 and VRF gateways.
Additional resources on VRF Lite support in Cloud Director 10.2:
Data Center Groups for Cross-VDC Networking and Distributed Firewall
With NSX-T now mainstream, a big focus in Cloud Director 10.2 is to deliver greater support and integration between NSX-T and VMware Cloud Director.
Starting with version 10.2, VMware Cloud Director supports data center group networking backed by NSX-T. A data center group acts as a cross-VDC router that provides centralized networking administration, egress point configuration, and east-west traffic between all networks within the group.
The cross-virtual data center networking feature enables organizations with virtual data centers backed by multiple vCenter Server instances to stretch layer 2 networks across multiple virtual data centers.
Additionally, distributed firewall can be enabled for a data center group with an NSX-T network provider type, creating a single default security policy that is applied to the data center group.
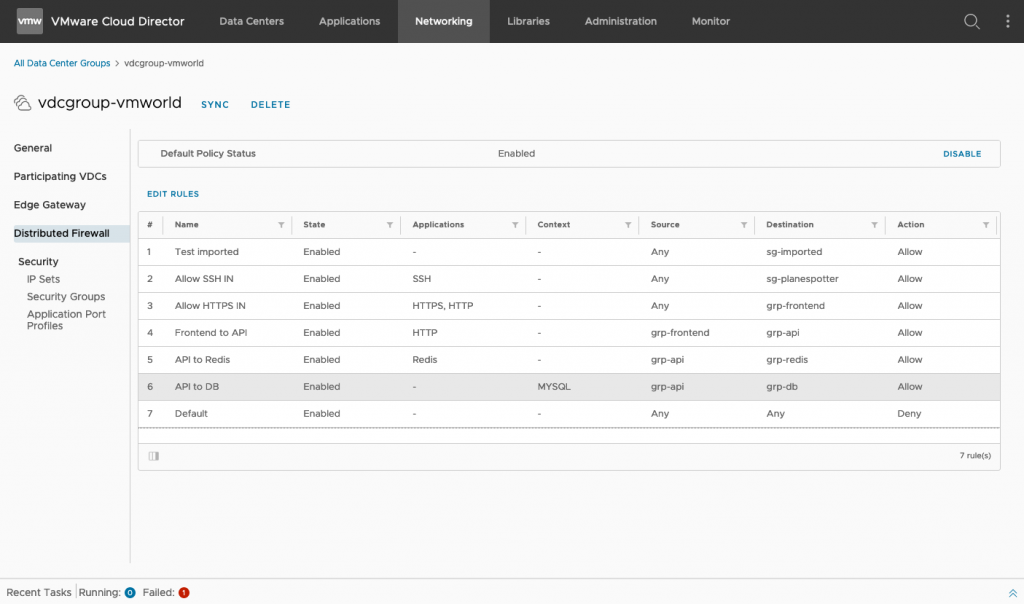
In terms of capabilities, VMware Cloud Director 10.2 supports L4-L7 distributed firewall rules (limited to static membership).
Considerations for NSX-T data center groups in VCD:
- A data center group can contain between one and 16 VDCs that you configure to share an active egress point.
- A system administrator must configure the availability zones for group networking with NSX-T by setting a Compute Provider Scope for the vCenter Server instance and, optionally, for the provider VDCs backed by the vCenter Server instance.
- When you configure an edge gateway to be the egress point for a data center group, you increase its scope to the data center group. The edge gateway becomes shared across all data centers that participate in the group. All routed networks attached to the edge gateway are attached to the data center group and scoped to it.
- The distributed firewall service is not enabled by default. After enabling the distributed firewall, you can create IP sets and security groups to facilitate the creation of distributed firewall rules.
- Distributed firewall rules that you create apply only to the workloads attached to the data center group networks.
- The organization VDCs must all be backed by the same network pool (NSX-T transport zone).
Additional resources about cross-VDC networking in Cloud Director 10.2:
NSX Advanced Load Balancer (Avi)
VMware NSX Advanced Load Balancer (Avi) provides multi-cloud load balancing, web application firewall and application analytics across on-premises data centers and any cloud. Starting with version 10.2, VMware Cloud Director provides load balancing services by leveraging the capabilities of VMware NSX Advanced Load Balancer through the tenant portal.
Load balancing services are associated with NSX-T edge gateways, which can be scoped either to an organization VDC backed by NSX-T or to a data center group with NSX-T network provider type.
As a system administrator:
- You deploy and configure NSX Advanced Load Balance to use with your NSX-T Data Center deployment
- You register Controllers with VMware Cloud Director: controllers serve as a central control plane for load balancing services. After you register your controllers, you can manage them directly from VMware Cloud Director.
- You register your NSX-T Cloud instances with Cloud Director.
- You import service engine groups into Cloud Director. The load balancing compute infrastructure provided by NSX ALB is organized into service engine groups. You can assign more than one service engine group to an NSX-T edge gateway.
After a system administrator assigns a service engine group to an edge gateway, an organization administrator can create and configure virtual services that run in a specific service engine group.
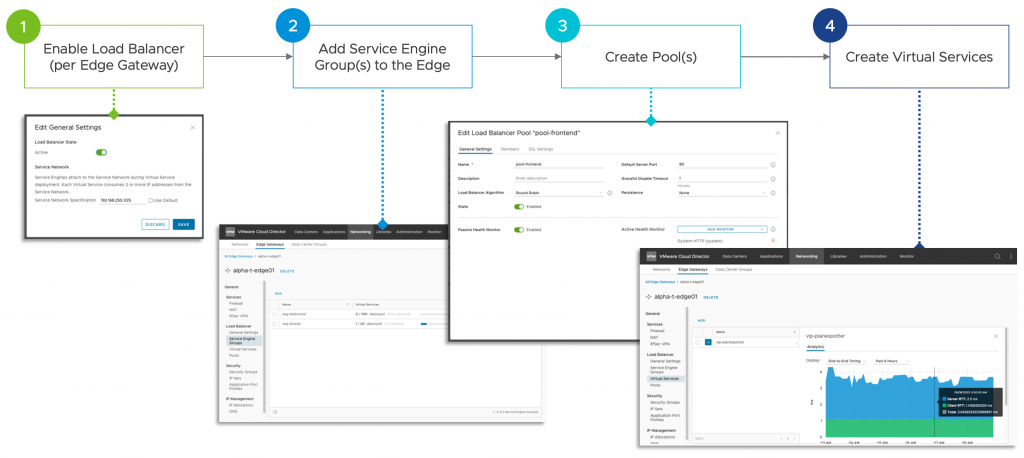
Be sure to check Tomas and Avnish extensive articles on this topic
Additional resources about network load balancing in NSX-T backed organization VDCs:
- Feature Fridays Episode 19 – NSX-T Advanced Load balancer
- For information on how to configure NSX Advanced Load Balancer with NSX-T, see Avi Integration with NSX-T.
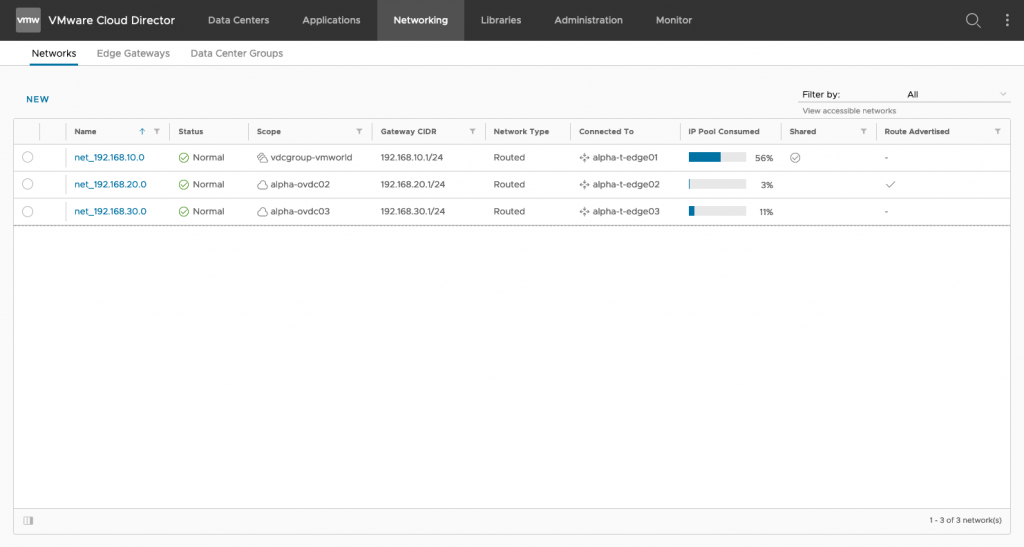
Networking section in the Tenant Portal
The user interface has been redesigned, and it is now easier to find a network, an edge gateway, or a data center group in the new Networking tab from the tenant portal.
Summary
VMware Cloud Director 10.2 introduced many updates, with the highlights focused on helping partners expand their business with key network and security services (i.e., key VMware NSX-T capabilities fully integrated), crucial to supporting customers’ needs for network simplicity and secure cloud requirements.
- While transparent for a tenant, the adoption of VRF gateway as external networks has many benefits from a provider point of view: it helps provide a fully routed topology in a virtual data center without dedicating a complete tier-0, thus increasing the scale.
- Data center group networks backed by NSX-T Data Center provide layer 2 network sharing, single active egress point configuration, and distributed firewall (DFW) rules applied across a data center group.
- VMware Cloud Director 10.2 provides load balancing services by leveraging the capabilities of VMware NSX Advanced Load Balancer through the tenant portal.
Check also my VMworld 2020 #HCPS2625 session where I go through distributed firewall and NSX ALB support in VCD 10.2: All Things Networking for VMware Cloud Providers.






