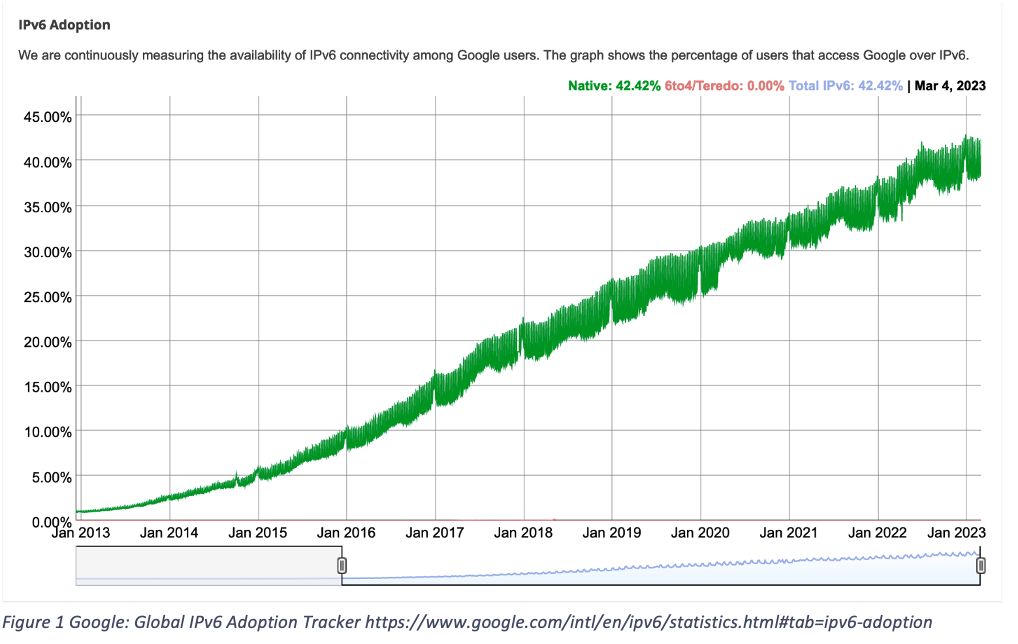
IPv4 has been the foundation of all communication on the Internet for decades. IPv6 has been expected to replace IPv4 as the most widely adopted protocol for years. Major service providers, organizations and governments have been adopting IPv6 for years, and now almost half of the world wide users access Google over IPv6.
Introducing IPv6 in VMware Cloud on AWS
Today VMware announces the introduction of IPv6 for workload communications in VMware Cloud on AWS. In VMware Cloud on AWS SDDC version 1.22, VMware introduces support for several critical use cases of IPv6. VMware Cloud on AWS Customers can now utilize IPv6 for their workloads inside the SDDC as well as to communicate with on-prem over Direct Connect and VMware Transit Connect.
This extends the core networking capabilities of VMware Cloud on AWS to address additional customer use cases using IPv6. Customers can create or migrate IPv6 VMs for Data Center migration, extension or replication use cases.
- VMware Cloud on AWS support for IPv6 VMs on customer generated Tier-1 Gateways
- IPv6 VM to VM communication inside the SDDC
- DHCPv6 and SLAAC for IPv6 address configuration
- Neighbor Discovery (ND) and Duplicate Address Detection (DAD)
- Gateway Firewall and Distributed Firewall support for IPv6 addresses and groups
- IPv6 VM communication over IPv4 VPN
- IPv6 VM communication to on-prem over Direct Connect or Transit Connect
- SDDC Groups and Transit Connect support for IPv6 across SDDCs or to on-prem destinations.
Advanced Networking with IPv6
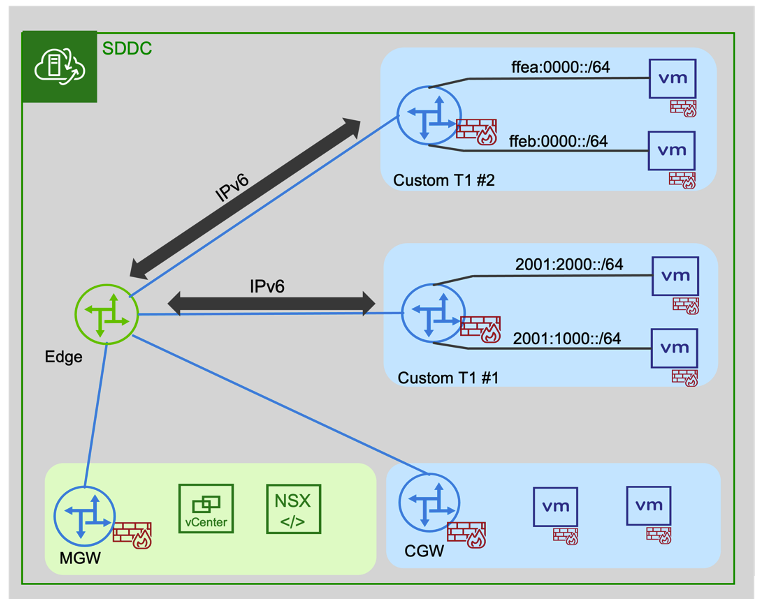
In version 1.18, we added several advanced networking and routing capabilities enabling users to create additional Compute Gateways (CGW or Tier1 Gateways). Logical segments created on custom CGW (additional Compute Gateways or Tier1 Gateways) now support dual stack networking. IPv4 is always automatically enabled, and now users can configure IPv6 addresses for VMs to communicate internally inside the SDDC.
At this time, we are introducing IPv6 as an option while IPv4 remains the default addressing protocol. Every SDDC is initially created with IPv4 addresses by default. Management appliances utilize only IPv4 at this time.
To start using IPv6, customers must first navigate to the SDDC Summary tab in the VMware Cloud Console UI. The Actions menu provides an option to enable IPv6. This sets up the SDDC for dual stack networking. As mentioned above, IPv4 continues to remain available for use. Note that each SDDC must be enabled individually because SDDC configurations are not automatically shared across the Org. Also, once enabled, IPv6 cannot be disabled. After it is enabled, the SDDC uses AWS auto-assigned IPv6 addresses. You can configure IPv6 policies on the Gateway Firewall as described below – a necessary step to enable North-South communication using IPv6.
Next, you must create a new Tier-1 Gateway and setup the VMware Cloud on AWS Advanced IP Discovery segment profile. This sets up IPv6 VMs on new logical segments to utilize on DHCPv6 or SLAAC and to rely on Neighbor Discovery (ND) and Duplicate Address Detection (DAD) to populate IPv6 Routing Tables. You can configure VMs with private IPv6 CIDRs on any logical segment in the Tier-1 Gateway. For an in-depth description of NSX Logical Segments, please refer to this Techzone article. https://vmc.techzone.vmware.com/understanding-segments-vmc-aws
As with IPv4, users can visualize IPv6 VM to VM connectivity using Traceflow.
Once you define the source/destination endpoints, Traceflow provides end to end visibility of the network path in a graphical or tabular format. Users can utilize Traceflow to validate the flow path before starting communications or use NTA to troubleshoot issues with existing flows.

On-prem Communications
For IPv6 VMs to communicate with on-prem or other SDDCs, you must configure route aggregation policies on the Tier-1 Gateway. Navigate to the Global Configuration tab under Networking. Then create a Managed Prefix List with IPv6 prefixes and add the Route Configuration over the INTRANET end point. This ensures that the IPv6 prefixes are advertised over Direct Connect or Transit Connect.
To allow North-South IPv6 traffic, you must configure IPv6 policies on the Gateway Firewall. NSX only creates auto-populated Groups for IPv4 routes on the default Compute Gateway. You must manually configure the IPv6 addresses or groups on the Gateway Firewall. The NSX Distributed Firewall protects every individual VM at the hypervisor level. It now supports IPv6 addresses as well as Groups with IPv6 members.
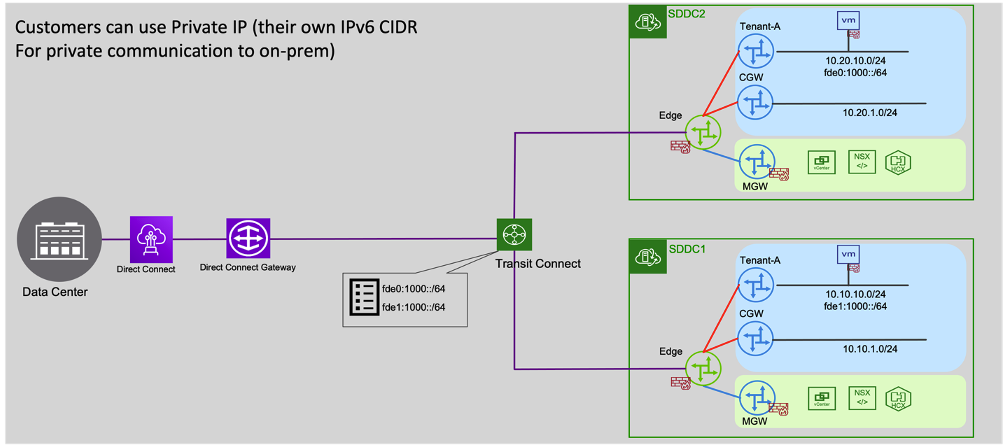
IPv6 VMs can also communicate with destinations on-prem using Direct Connect or Transit Connect. SDDC Groups and VMware Transit Connect now support IPv6 communications between SDDCs and on-prem destinations. IPv6 prefixes that are advertised from a connected SDDC are propagated to other SDDCs. Similarly, Transit Connect auto-propagates IPv6 routes learnt from on-prem to SDDCs. Note that the Direct Connect Gateway attachment can be configured only once when it is created. If your SDDC Group already has a Direct Connect Gateway attachment, you must update the VMC Prefixes in your AWS account with the required IPv6 CIDRs in VMware Cloud on AWS SDDCs.
Using VPN for IPv6 Traffic
VMware Cloud on AWS provides IPSec VPN connectivity to remote sites. Route Based and Policy Based VPN are supported using IPv4 endpoints. Customers can utilize VPN IPv6 communications to remote sites. To enable this option, first establish an IPSec VPN session to the remote site using IPv4 endpoints on the Tier-1 Gateway. Next, configure a static route to tunnel the IPv6 segment over the VPN session. Ensure that firewall policies permit traffic to the VPN Tunnel Interface (VTI).
If the remote site supports BGP, you can choose Route Based VPN to the SDDC, which automatically summarizes the IPv4 and IPv6 networks attached to the CGW and Routed Tier-1 Gateways. If the remote site does not support BGP, you must utilize Policy Based VPN and specify the individual IPv4/ IPv6 networks to be tunneled. At this time, native IPv6 communications over the Connected VPC (SERVICES endpoint) or Internet are not supported.

Migration to VMware Cloud on AWS
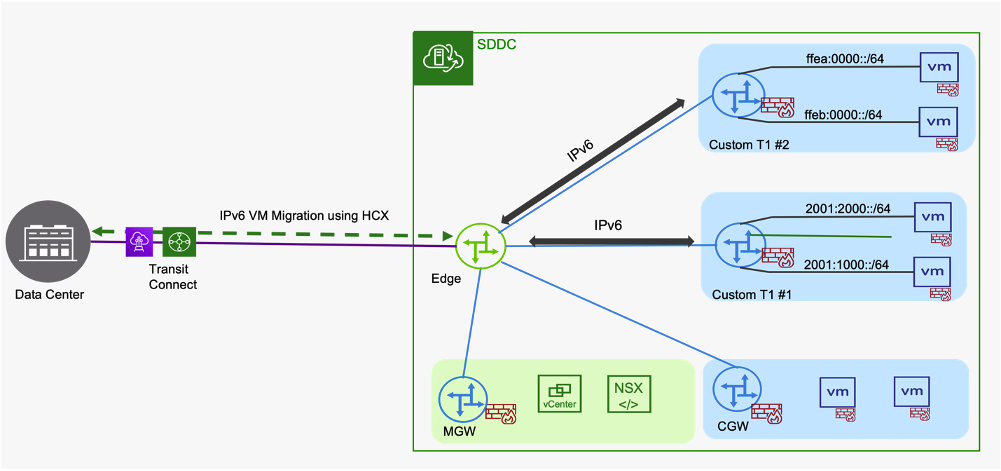
VMware HCX now supports IPv6 workload migrations to VMware Cloud on AWS. HCX Version 4.6 introduced migration support for Dual Stack or IPv6 VMs over IPv4 based transport. After migration, IPv6 VMs can communicate with on-prem IPv6 destinations. At this time, Advanced functionality such as Network Extension (NE) and Mobility Optimized Networking (MON) are not supported for IPv6 VMs.
Certificate Based Authentication for IPSec VPNs
In this release, VMware Cloud on AWS also introduces Certificate Authentication for Route Based and Policy Based VPNs. This gives customers an alternative to using Pre-Shared Keys (PSK) for Authentication. This is particularly useful for customers who need to enable connectivity to a number of external endpoints with whom sharing keys is impractical.

NSX supports multiple Certificate Authorities (CA) and offers a choice of compliance suites for Authentication to VPNs. As a user, you can import Certificates or CA Certificates under the System tab. Certificates can be configured for local VPN Endpoints, including Tier-1 VPN Endpoints. After it is configured, you can utilize the available Certificates for authentication while creating Route based or Policy based VPN sessions. This enables customers to achieve advanced use cases such as FIPS compliance in VMware Cloud on AWS.
NSX Alarms Dashboard
VMware Cloud on AWS users can view all their NSX Alarms using the new NSX Alarms Dashboard in VMC. This gives users visibility into potential issues in the network and provides recommendations on remedial actions to resolve them.
Networking & Security UI
The VMware Cloud Networking & Security tab presents a simplified single-page view of networking and security status in the SDDC. The page presents separate sections for VPN, Direct Connect and SDDC Groups/ Transit Connect based connectivity. Additional sections for the Management Gateway Firewall, Compute Gateway Firewall and Cloud Provider (Connected VPC) services are available. Each section provides a summarized view at a glance, which makes it easier for administrators to check connectivity status on the main page.
As announced earlier, VMware Cloud on AWS customers should use the NSX Manager UI for networking and security actions. This UI provides an extended set of Networking and Security configuration actions, replacing the Networking & Security tab in 1.22. All new features such as the Alarms Dashboard are available only in the NSX Manager UI. Learn more about this new update.


To learn more about all other VMware Cloud on AWS capabilities released in VMware’s Fiscal Year 2024- Q1, check out this blog.
Meanwhile, if you would like to learn more about VMware Cloud on AWS, here are some additional resources for you:
Additional Resources:
- Learn more about VMware Cloud on AWS Networking at Network Virtualization blogs
- Learn more about our VMware Cloud on AWS service at the VMware Cloud on AWS website or by viewing VMware Cloud on AWS: Overview.
- Follow us on Twitter @vmwarecloudaws and give us a shout with #VMWonAWS.
- Watch informative demos, overview videos, and webinars, and hear from our customers: VMware Cloud on AWS on YouTube.
- Try the VMware Cloud on AWS Lightning Lab for a first-hand immersive experience.
- Read our latest VMware Cloud on AWS blogs.
- Obtain the VMware Cloud on AWS Solution Brief and VMware Cloud on AWS TCO 1-pager.
- Follow the VMware Cloud on AWS release notes on continuing updates.
- Visit VMware Cloud Tech Zone for technical articles, guides, videos and more
- Listen to latest episodes of VMware Cloud on AWS Unplugged Podcast
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.



