Certificate management is crucial for security against “man in the middle” cyber attacks. When a certificate expires, servers and applications can become unresponsive, which may take time to bring them back online. Managing various certificates (vSphere, Aria, VMware vSphere Foundation (VVF), and VMware Cloud Foundation (VCF)) can be challenging due to different types and expiration dates. Missing deadlines can lead to outages, and managing up to four certificates on applications like vCenter can be even more complicated. VVF and VCF 5.2 provide a solution to this challenge. The new Diagnostic Console features a section that consolidates all essential certificate information, saving time and effort. This allows customers to quickly access valuable information and take necessary actions.
Here is an example of how to identify a vCenter 8 certificate.
Figure 1. Click on “lock” icon next to vCenter server name
Figure 2. Select “Show Certificate”
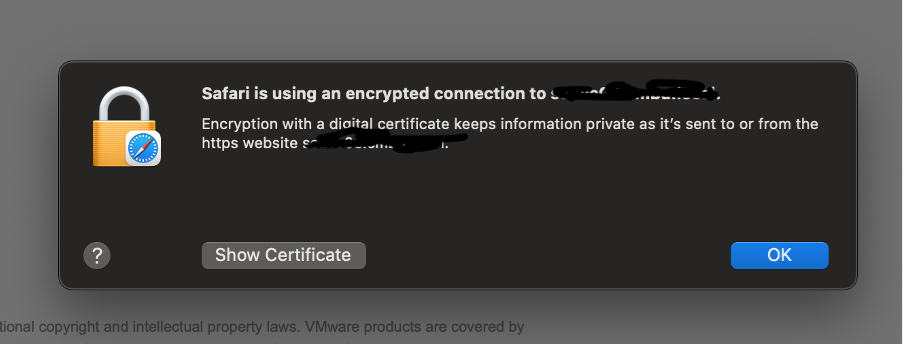
Figure 3. Review Expires Date
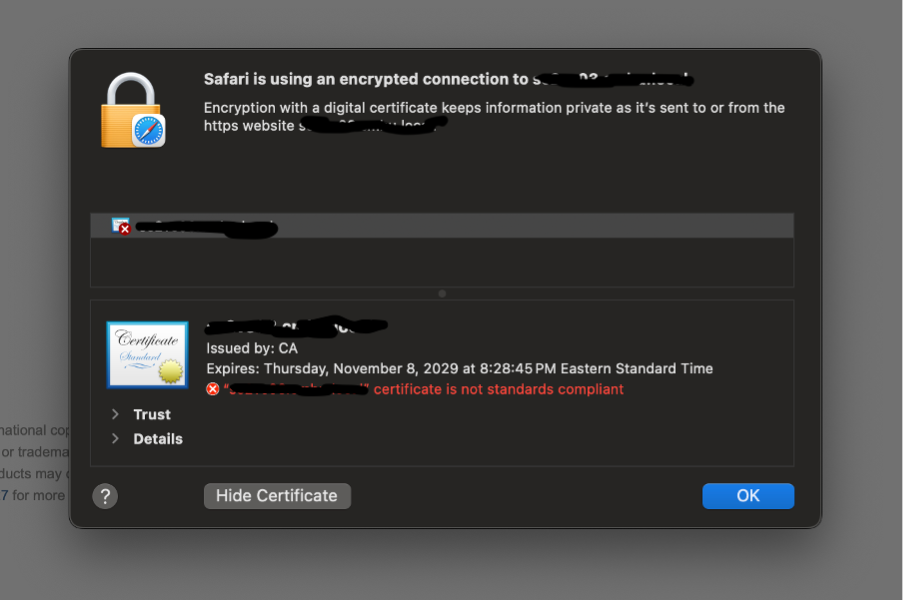
To request a CA certificate (like the one shown above), customers have to do the following:
- Generate a Certificate Signing Request (CSR)
- Log into the vCenter and select “Administration -> Certificate Management”
- Under “Machine SSL Certificate”, select “Actions -> Generate Certificate Signing Request (CSR)”
- Enter Info and select “Next”
- Common name
- Organization
- Organization Unit
- Country
- State/Province
- Locality
- Email Address
- Host
- Subject Alternative Name (Optional)
- Key Size
- Access CA web enrollment (https://ca-fqdn/certsrv)
- Select “Request a certificate”
- Add CSR
- Add newly generated CA certificate
- Return to vCenter UI
- Select “Certificate Management” page
- Under “Macine SSL Certificate” select “Import and Replace Certificate”
- Select “Replace with external CA certificate where CSR is generated from vCenter Server (private key embedded)
- Cut and paste “Machine SSL Certificate” and “chain of trusted root certificate”
- Select “Replace”
- Return to vCenter UI
- Confirm new SSL certificate
- Return to vCenter web portal
- Perform the “identify vCenter certificate” from above
When dealing with Self Signed certificate, here are the steps for vCenter 8:
- Log into the vCenter via command line
- Run certificate-manager (/usr/lib/vmware-vmca/bin/certificate-manager)
- Select “option 4”
- Enter in administrator@vsphere.local password (when prompted)
- Review existing settings:
- Country
- Name
- Organization
- OrgUnit
- State
- Locality
- IPAddress
- Hostname
- VMCA Name
- Type “Y” when confirmation request is prompted
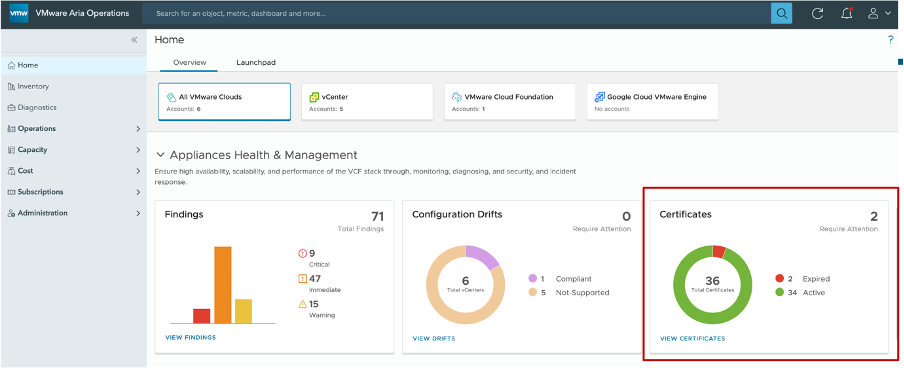
To view the status from the Home dashboard, customers can access the Certificate Management on middle right corner. When selecting “VIEW CERTIFICATES”, customers can see more details.
Figure 4. Home dashboard
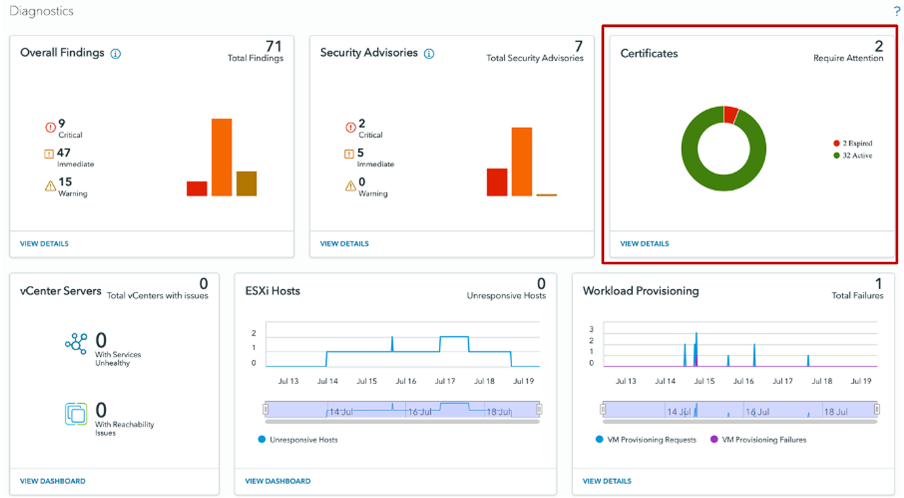
From the Diagnostics Console, customers can also see Certificate Management on the right top corner. When selecting “VIEW DETAILS”, customers can see the same details.
Figure 5. Diagnostics dashboard (Certificates panel is to the right)
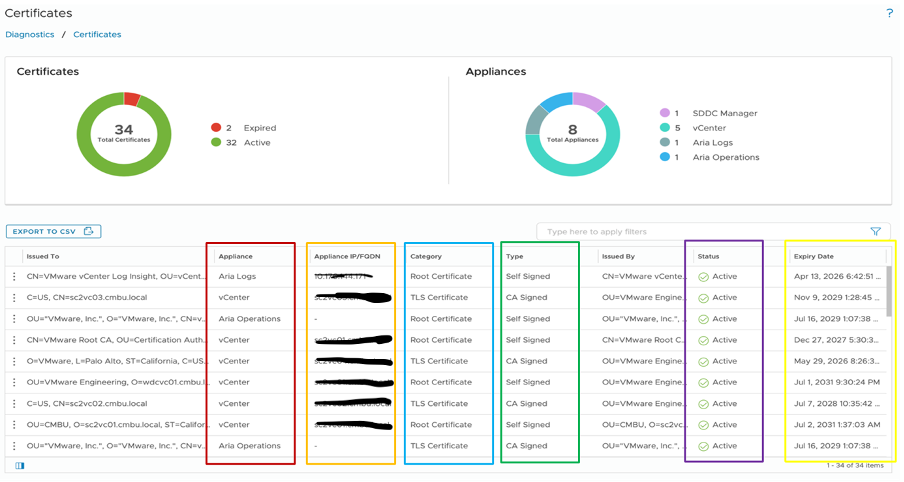
Key sections include:
- Appliance – the application the certificate belongs to (red)
- Appliance IP/FQDN – the actual host that holds the certificate (orange)
- Category – the kinds of certificate (Root, TLS, and STS) (blue)
- Root – self-signed or CA
- TLS – CA
- STS – CA
- Type – CA and Self Signed (NOTE: CA certificates may require time to acquire. Leave enough time to request and install to reduce unneeded outage). (green)
- Status – identify immediately if certificate has a problem (purple)
- Expiry Date – see in advance the cutoff date to start processing new certificates (yellow)
Figure 6. Certificates dashboard
Here are some common use cases:
- If “status” is not “Active,” fix it right away.
- If “status” is “Active” but “Expiry Date” is approaching:
- For Self Signed certificates: create a new certificate in the application.
- For CA certificates: request a new certificate from the CA authority.
- If an internal customer complains about an application being offline, check the certificate for expiration.
- When components are offline, check certificates on all associated components.
- If an application fails to start, check the logs for expired certificates.
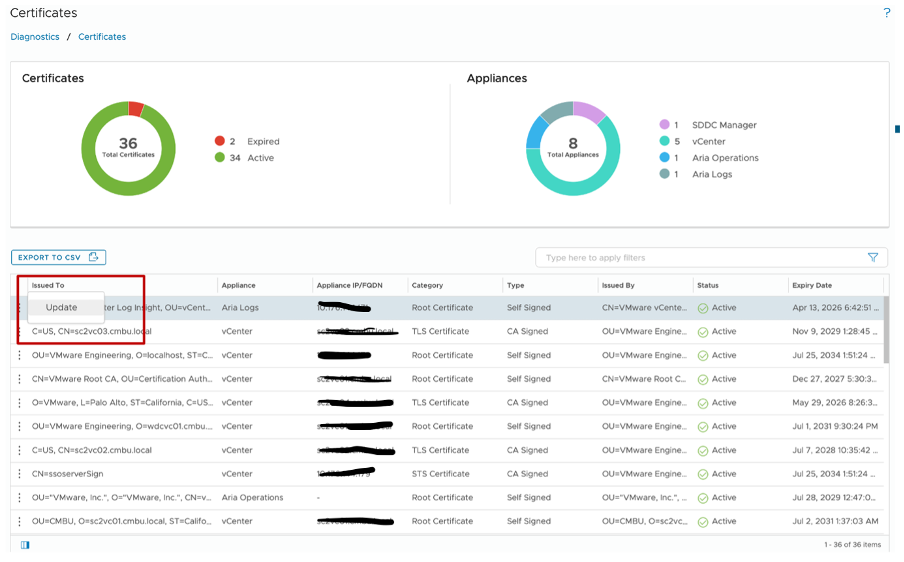
In order to fix a specific certificate, click on the three dots and then select “Update”. This will redirect you to the web portal of the specific application.
Figure 7. Update option
This consolidated view of certificate management has never been available before. Integrating Certificate Management into the VVF and VCF Operations Diagnostic Console will offer improved visibility for managing certificates, ensuring stability, and reducing unnecessary downtime. For Self Signed certificates, customers can swiftly address certificate concerns. For “CA” certificates, administrators can prepare for new certificates before they expire. It is empowering to have this knowledge in advance.
Resources:
- vSphere Security Certificates
- VMware Aria operations 8.18 Release Notes
- VMware Cloud Foundation 5.2
- What is Diagnostics for VMware Cloud Foundation
- Renew VMCA Certificates with New VMCA-Signed Certificates Using the vSphere Client
- Configure a Certificate For Use With VMware Aria Operations
- Install a custom certificate in VMware Aria Operations for Logs 8.12 and Later
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.




