This is an article about how I used VMware Carbon Black Cloud ONLY as a showcase to secure desktops running on VMC on AWS.
In this showcase we will use following Solutions:
-
VMware Cloud on AWS
-
VMware Carbon Black Cloud
The VMware Carbon Black Cloud is a cloud-native endpoint & workload protection platform (EPP/CWP) that provides what you need to secure your endpoints/workloads, using a single lightweight agent and an easy to use console. By the way, Carbon Black have a big and nice community! There are more than 30k security professionals! Give it a try and join the community!
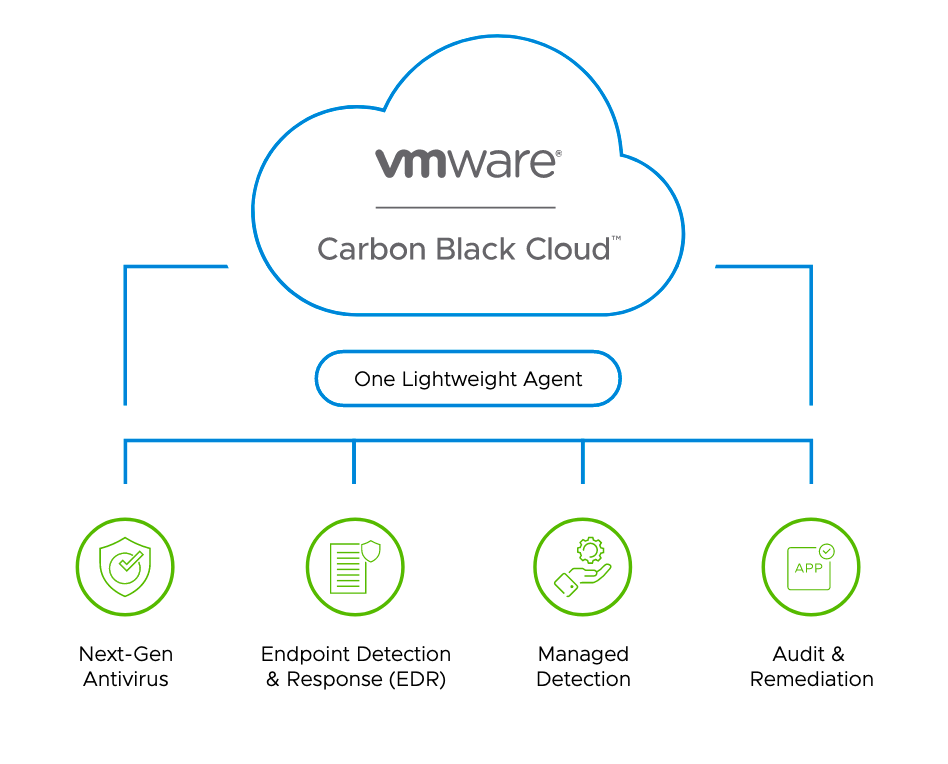
VMware Carbon Black provides:
-
Superior Protection
-
Actionable Visibility
-
Simplified Operations
We will secure our VMC on AWS Horizon Environment with Carbon Black endpoint protection.
First let’s take a look on the Console. It is a web-based Console hosted in a AWS Datacenter. You can login via SSO or E-Mail and Password, as well as 2FA with DUO Security / Google Authenticator. The Dashboard give you a good overview about what is going on, any events or issues.


Let’s start to get CB rolling and define some policy groups. In a policy group you can define all kind of settings, what should happen if something get’s detected, or just simple things like, when should the system get scanned. To create a new Policy let’s get to enforce and then policy.
Add a new Policy, name it, add a description and copy settings from existing Policy Groups (in my case, the standard Policy Group).
Perfect, now we can do some modifications. Let’s define a application bypass rule for powershell. Switch to “Prevention”, open the permissions tab and add an Application. You have several options, but for now we just want to bypass any operation with this application. Confirm the change and we are good.

In the “Blocking and Isolation” tab you can see some predefind rules. We can do several operations if a known malware appear, but for this showcase we just want to terminate the process to stay safe. By the way, you are always able to perform a “Rule test”, to see how this rule affact your environment! Thats a pretty cool feature to protect you from stopping business and being more accurate in creating policies.

You also can change the local scans, On-Access File scan, frequency and more. I changed the Frequence to 12 hours (default 4 hours). You are also able to change your Update Servers, where the client get his security updates. Maybe for a Offsite device or another region. Keep in mind, if you have Database Servers you would like to disable on-Access file scan mode, for our Horizon Environment on-Access Scan is fine.

On the last Tab “Sensor”, you can edit the sensor settings of the client. I will deploy CB to our demo and test environment, in this case I allow user to disable protection. Usually you will not allow the User to disable the security! Guess what, if user can disable it, most of them will do and they will not enable it again. In the screenshot below you can see lot of different settings like “scan files on network drives” etc. Lot of them depending on the usecase or device itself. But i would recommend to enable “require code to uninstall sensor”, so no Device admin are able to uninstall the sensor.

Let’s get back to the general tab, can you see the “Sensor UI: Detail message”? If CB blocking anything on your device, you will get a notification on your device OS and here you are able to personalize the message! Below you can find a example message:



























