by: VMware Incident Response Specialist, Dustin Hammond
In the cloud era where information is instantly shared via the internet, it’s easy to forget that people still employ USBs in their daily work. It’s also easy to forget malicious worms can and still do replicate to connected USB drives—a powerful and often-used technique malware authors leverage to successfully infect systems all over the world. And those drives are frequently connected to enterprise ecosystems, a fact that makes this threat even more dire as malware is no longer only infecting a solitary machine (as in the pre-cloud era).
- USBs can easily overlap between a user’s personal devices and their work devices, including air-gapped networks that are physically isolated from the rest of the world in highly secure environments.
- It is not uncommon for one or more USB devices to be used, shared, and passed around for a variety of storage needs. At scale, this delivery technique can infect hundreds, if not thousands, of systems all over the world.
Consider an internet café. A user connects a personal USB device to a system not knowing it is already infected with malware. Sensing the USB, the malware triggers an execution chain which infects the device behind the scenes. Not realizing any threat is present, the user leaves the café and ultimately plugs the infected USB into other home and/or office devices. The malware proceeds to infect those systems as well. See Figure 1.

Figure 1. How an infection quickly spreads, possibly to the enterprise ecosystem
This blog offers some helpful hints on how to both detect and eliminate USB-based malware. It contains many tips found in the Unit 42 posting that our VMware IT teams have employed with success.
On the hunt, knowing what to look for
Given the gravity of the USB malware threat, VMware IT conducted extensive investigations into how the malicious software operates.
We found the common denominator in such cases is Unicode character ‘00A0’, also called a non-breaking space character. It is employed to name the directory and looks like a normal space to the naked eye. See Figure 2.

Figure 2. The hexadecimal notation of this Unicode character is represented in the UTF-8 translation. When translating this further to be URL encoded, it translates to %C2%A0.
If you wish to copy this character, you can attempt to print the character to the console using Python (as in this example), or open a file and write the character to the file to allow you to copy it.
Now that you know what to look for, let’s look at what you can do about it via various scenarios.
Using VMware Carbon Black
When searching in the Investigate tab in VMware Carbon Black®, ensure the URL encoded value is present in the URL as highlighted here:
processes?query=%28filemod_name%3Ad%5C%3A%5C%5C%C2%A0%5C%5C%2A%29&searchWindow=THIRTY_DAYS
Please note that a regular space when it is URL encoded translates to %20, so your URL with a regular space will look like the highlighted below:
processes?query=%28filemod_name%3Ad%5C%3A%5C%5C%20%5C%5C%2A%29&searchWindow=THIRTY_DAYS
Be cautious copying and pasting the non-breaking space character when performing a query as various applications will translate it to a space character instead.
Append the following code to your VMware Carbon Black link:
https://<your cb tenant>/cb/investigate/processes?query=%28filemod_name%3Ad%5C%3A%5C%5C%C2%A0%5C%5C%2A%29&searchWindow=THIRTY_DAYS
This will translate to a search query similar to the following, although a ‘no-break space’ character is used instead of an actual ‘space’ character.
(filemod_name:?\:\\ \\*)
If rundll32 execution is required to load content, the additional ATT&CK Framework Watchlist detection ‘Execution through API’ can produce results on associated techniques that VMware IT teams regularly observe in relation via the following query:
((process_name:rundll32.exe -(parent_name:services.exe OR parent_name:svchost.exe))) -enriched:true
If at first you don’t succeed . . .
Depending on the variant, when an infected USB device is connected to a computer it may have some AutoRun or AutoPlay configuration files embedded that it will rely upon for execution. This, however, won’t always work. To compensate, malware authors rely instead on a secondary method of infection through user interaction.
It works as follows:
- A shortcut file typically named after the USB drive—and with an icon of a Windows drive—will sit at the root of the USB folder.
- As this shortcut is masquerading as the USB device, it is tempting to click on the icon to access files and folders.
- In reality, the shortcut file points to a hidden file buried under one or more hidden folders that both executes the malware and opens the browser to reveal your files that have been moved to another hidden directory.
Our teams also observed this shortcut technique with the Raspberry Robin worm that Red Canary revealed.
Is your USB infected? Let’s find out
When you plug in a USB device, navigating to the USB mount should immediately reveal files. Here are examples of a clean USB versus an infected one (Figures 3 – 4).
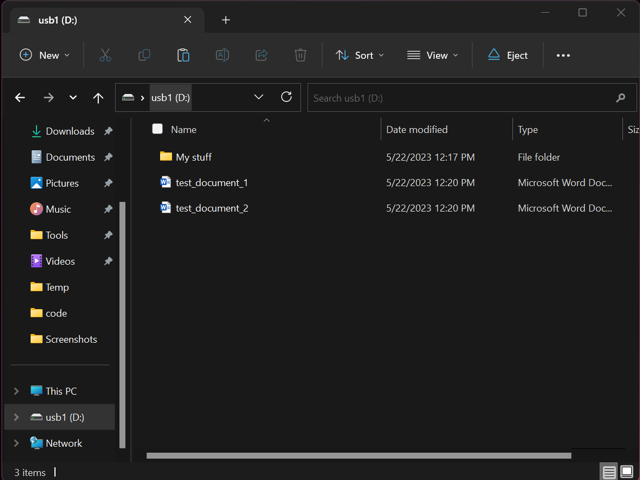
Figure 3. Normal view—USB is highlighted on the left, documents visible immediately on the right.

Figure 4. Infected view—note the hidden folder with no name, and the shortcut file with the same name as the USB drive.
If you observe a shortcut file in your USB root directory, right-click on the file and view the properties to reveal the true target executable it is pointing to.
Use the ‘show hidden folders’ view in your browser to see if there are any hidden folders.
Lost in the shuffle
USB worm infections commonly perform what’s called a file shuffle by employing the user files present at the time of infection. It creates another hidden directory somewhere on the USB drive, and then moves all your files to that newly created hidden directory as seen in Figures 5 – 6.
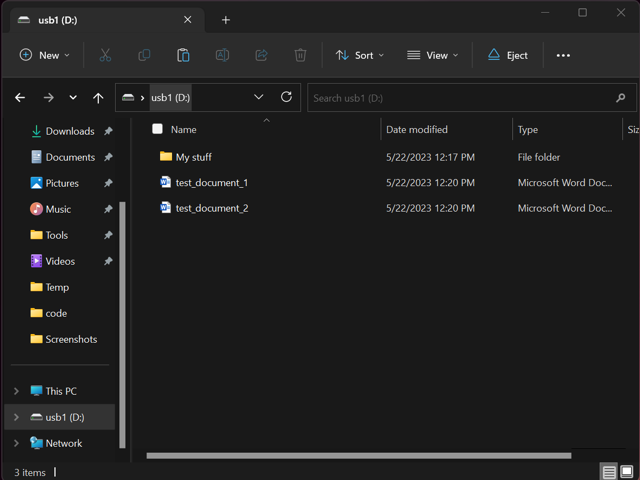
Figure 5. Note the odd file path at the top that includes what looks like an unnamed parent directory.

Figure 6. View of the drive with hidden folders unchecked
On the case with Splunk
If you have a Splunk integration, try the following search query regex pattern. This can assist you in hunting for anomalous hidden directories when a process is executed from such a directory structure.
index=<your CB index> (childproc_name=”*:\\ *”)
| regex childproc_name=”^[d-z]:\\\\[\w\W\d\D]+.[\w\W\d\D]{3}$”
MITRE ATT&CK
| ID | Name |
| T1091 | Replication Through Removable Media |
Indicators of compromise
These file hashes are shared here along with the AV Signature name sourced from the Avira engine.
| Indicator (SHA256) | Signature Name |
| 0d9688c058fe24662321fcbd86fac53ba1f72ee7378fb543771b94a327e0ea4e | WORM/Autorun.aaer |
| 1dd385d4dc6330ba15b3f0781fc38c7eec4393b0b2ae335e95f6f36431aa8cc8 | WORM/Taranis.2719 |
| 3617f708a910ec6c1b17dc940addfd1e9fe3076d18740e375e2f94e96d3e8c7a | Trojan/Enosch |
| 609d9893cc27193c3ffec0107893ff9baf116341e84f0cee238e191306f6f594 | W32/Slugin.A |
| 16996f69d393b324240c3420a540e1380730a3f6bea141d4c99fd2b1727f28f8 | Trojan/Razy |
| bfec66aa9d8a503292565fe7f82130c8ea3289bf7ddae34d0b8acbeecfa6dfce | WORM/Autorun.hfp |
| 118418433f1244357712184648c286e033fee81a45d0a1bd790c6c5090359355 | WORM/Lodbak.Gen4 |
| 24726892b09e4cfc49c3effae4f0ddbd8c5e3b4ec85e699e6e5b8de182a2d4f1 | WORM/Lodbak.Gen |
| 355965fa3d6c0f1964d28858043c7ec5329fd08a6d8459d6308aaea5565e8f83 | WORM/Lodbak.Gen4 |
| 52213f3af0ccf3f244902cf4483769844649adaea931bbcc6d199e01bd84d0be | WORM/Taranis.295 |
| a10d17ba338ba3e9b387d1b4f7f3b0bde3c332f212234d8ed43e5969c5964b46 | TR/Taranis.2852 |
| d1d14eb3ed48710ed8cea34742b5e25d75885d3a42dd9cd2508d734d0d73b452 | TR/Taranis.458 |
| 68d4ad401a085bc98345ccf4440e8cc3d8cd76df918e2b0fbf4ba310f862c314 | WORM/Lodbak.Gen4 |
| 8c128f2eb1a31c5d4259339103dbe199d4941cde1badb51a1402b135882eb791 | TR/VB.Downloader.Gen |
| bfec66aa9d8a503292565fe7f82130c8ea3289bf7ddae34d0b8acbeecfa6dfce | WORM/Autorun.hfp |
| 1c25f8e9ebe0f34cce6cb20e58e564e1318bd92902b3325ddea6299d9b048518 | WORM/Lodbak.Gen |
| 319a961f0590829d125346298dc53dfb3bf51d2fa1619603baf0c56720cbb8d2 | TR/Crypt.ZPACK.Gen4 |
| 693bde25d369a1116b82170c3283f134b6f9d17b3494073b81fc01a951e96de8 | TR/Crpyt.ZPACK.Gen4 |
| 996ff55de5931b921ddde4a7bf0abc953f569e16b5c4a937e3aff33af318bdc0 | WORM/Taranis.2666 |
| fb6c3e430a1b0af757fffceddf74f463033f8232eb90415c548ae448372e0909 | TR/Spy.Gen8 |
| b262e7ce0967761a2a6bf22d4605edcd91002fa73a8cc5b436175814077ac4c1 | WORM/Lodbak.Gen |
| bb2913e23ec9e47a127d89d77748ba655f683e8242175086a7c4d912e4de8413 | HEUR/AGEN.1322093 |
| b328a9c08dbba2e4c5284076ed5338d49e025484c77a9e64dc5d06581ed9a7bf | WORM/Lodbak.Gen4 |
| 2ce718b6dc9cc1f43240e196e7cec6a1bbf0bcb0283bed4da7cda619fac597e3 | WORM/Taranis.1075 |
| 8dffd3e9a784486be8f7b6a66ea98aea203944842968d03ce4fbc65df601dd79 | WORM/Lodbak.Gen4 |
| 2abfee02624c522bd6d3f944cf7046814c833527f7540e174e5df13f2575b0fa | TR/Taranis.2683 |
| 2875cde5e229db388c8d8ed8cd77368872daacb7fc81f275cd2a6359bb1fe952 | WORM/Lodback.Gen |
| f5e5f532a39a87e4474b77ee451df882201b65ab1afecae6e18d0537e2136023 | TR/AD.Phorpiex.ikyxs |
| 2d08deed8c871203aeff265e5316023a828bb1152983148043961b382c6d2522 | WORM/Taranis.295 |
| 5c4043a72fe2d469d3abee73c56ffb28a03bea75b97d7f856d7eef8f8598e63f | WORM/Taranis.295 |
| 92d0e914e5662dee11fd75ceaeff5dd6996a05474120bd2058f92dc68df1c9a3 | WORM/Lodbak.Gen4 |
An ounce of prevention . . .
As any security expert knows, human nature is still the #1 vulnerability of any enterprise ecosystem, whether a malicious breach was intentional or not. That’s why awareness training is a great way to expose these threat actor techniques (and their remedies) to the largest user populations possible. A more direct (and recommended) approach is to simply block any/all USB devices on enterprise systems to fully prevent malware from spreading in the first place.
There’s a lot more to this dynamic topic than is presented here. That’s why we encourage you to contact your account team to schedule a briefing with us. No sales pitch, no marketing. Just straightforward peer conversations revolving around your company’s unique requirements.
VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. To learn more about how VMware IT uses VMware products and technology to solve critical challenges, visit our microsite, read our blogs and IT Performance Annual Report and follow us on SoundCloud, Twitter, and YouTube. All VMware trademarks and registered marks (including logos and icons) referenced in the document remain the property of VMware.



