by: VMware Incident Response Specialist Zhang Hongsheng
In 2023, innovative technologies, such as artificial intelligence (AI), machine leaning (ML) and 5G may pose potential challenges to organizations in securing their digital assets. The global cyber-attacks rose by seven percent in Q1 2023 as compared to the same period in 2022. It becomes crucial for organizations to respond timely to cyber security incidents and act swiftly to avoid huge financial losses.
Cyber security analysts respond tirelessly to malicious adversaries with an overwhelming number of alerts flashing on the security information and event management (SIEM) console. Analysts must perform triage, escalate the response, execute appropriate containment actions, and conduct impact assessment of an incident, which means they must be equipped with the best tools to accomplish these time-critical tasks, with the key focus on minimizing impact to the organization.
This blog illustrates a recent threat response scenario using VMware Carbon Black® EDR™ (Endpoint Detection and Response) solution to demonstrate how cyber security analysts can accomplish timely incident triaging tasks on a remote device that is not physically accessible. In the VMware Carbon Black EDR solution, threat intelligence is leveraged, together with multiple detection mechanisms, to enhance the monitoring and detection capability for threats in real time.
In a real-world cyber threat scenario, the analyst receives alerts on the EDR console when suspicious activities, like network connections to malicious IP address, are attempted on the host. Upon identifying the affected host, the analyst can immediately quarantine the host to isolate it from potential threats. See Figure 1.

Figure 1: EDR console display identifies the affected host, allowing the security analyst to quarantine the device.
Note: Specific information has been masked in some diagrams to avoid displaying personal identifiable information (PII).
From the information in the alert, the analyst can instantly pinpoint to the suspicious process that established the outbound network connection to an active and known command and control (C2) domain as shown in Figure 2. The EDR console will launch to the suspicious process tree when the analyst clicks on “View in Carbon Black Cloud.”

Figure 2: An EDR alert email shows the threat type, device, and process information.
Using VMware Carbon Black EDR
The EDR console provides useful triage information (timestamp; argument; privileges, hashes, process ID, signing certificate) on the process establishing the suspicious network connection. The parent processes can be easily traced via an intuitive process tree user interface (UI). See Figure 3.

Figure 3: The EDR console shows the process tree of the suspicious process.
In the process’s file modification activities, the browser credentials are read by the suspicious process. See Figure 4.

Figure 4: Browser credentials are read by the suspicious process.
After reading the browser credentials, the process created a temp. folder and data archives (edgest.db), possibly storing the read browser credentials in these data archives. See Figure 5.

Figure 5. The suspicious process creates “temp” file information.
When the data archives are created, the suspicious process makes multiple outbound network connections to an active and known C2 domain. In the console, the analyst can view when the suspicious outbound connections were made and to which IP and port number. See Figure 6.

Figure 6: Timeline of network connection information by the suspicious process.
Go live to look for sensitive data exfiltration
The analyst can immediately connect to the endpoint via the EDR “Go Live” feature, to download the data archives to examine for any sensitive data in them that could be exfiltrated. See Figure 7.

Figure 7. The EDR “Go Live” feature allows analysts to immediately access the remote host.
With Carbon Black EDR, the security analyst can attempt to retrieve the data archives from the affected host. The “Go Live” feature is a live response feature in the EDR that allows the security analyst to access the host remotely through the Carbon Black agent installed on the host. This feature supports various commands from navigating the file system, create/delete, execute native OS commands, and many others that an incident responder will perform. See Figure 8.

Figure 8. Many remote commands are available in the EDR “Go Live” console.
The operating system artifacts, such as Windows event logs, file system index, schedule tasks and system resource usage monitor (SRUM) can be extracted using forensics tools via live response. The security analyst can navigate to the “Windows\system32” folder on the affected host and perform a directory listing to search for useful artifacts to collect for further investigation. See Figure 9.
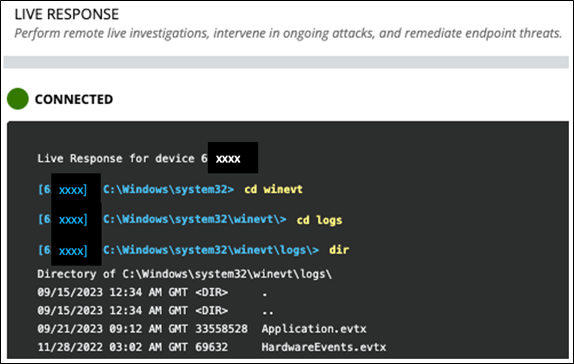
Figure 9. The EDR “Go Live” allows navigation of system folders on a remote host.
From remote triaging using Carbon Black EDR, the analyst is able to quickly determine the impact of the threat and decide to escalate for an in-depth forensics examination of the compromised system.
As the threat landscapes become more complex and digital footprints expand, it is imperative for organizations to be more aware of the security challenges that their analysts are facing. VMware Carbon Black EDR provides the tools and enables analysts to respond to security incidents in a swift and timely manner.
The above is just one example demonstrating how Carbon Black can defend your enterprise unlike ever before. Get the complete picture by contacting your sales rep or vmwonvmw@vmware.com to schedule a customized briefing. And check out our other security blogs.
We look forward to hearing from you.

VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. To learn more about how VMware IT uses VMware products and technology to solve critical challenges, visit our microsite, read our blogs and IT Performance Annual Report and follow us on SoundCloud, Twitter and YouTube. All VMware trademarks and registered marks (including logos and icons) referenced in the document remain the property of VMware.


