by: VMware Senior Information Security Analyst Jeremy Frois
The enterprise’s ability to detect, analyze and respond to endpoint threats—especially those involving attack surface areas such as IP addresses—is a mission-critical initiative for IT personnel. Traditionally, such tasks placed oversized burdens on security teams, primarily since many involved labor-intensive manual tasks.
The VMware Detection and Response Team (DART) took a different approach to protecting the enterprise. Our engineers leverage a combination of VMware Carbon Black Cloud™ and VMware NSX® Network Detection and Response™ automation technologies to create a comprehensive enterprise detection and response (EDR) solution deployed across corporate, virtual and cloud workloads in VMware. Now teams can effectively monitor and seamlessly respond to endpoint threats without impacting the user experience.
A very sensitive issue
At the core of this intricate defense system is its tens of thousands of endpoint sensors incorporated in Windows, Mac and Linux operating systems in cloud and noncloud environments within VMware. They offer DART personnel unprecedented visibility—as well as the ability to assess, contain and remediate threats as they surface.
Let’s look at a common example.
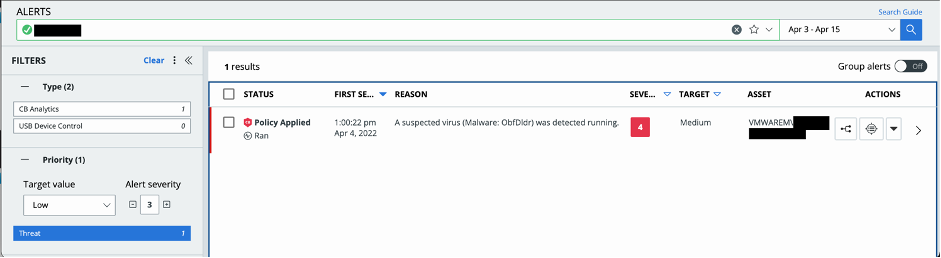
The system notifies DART of a suspicious file attempting to run on an endpoint through our security information and event management (SIEM) tools. Carbon Black generates an alert pinpointing the host on which it was detected, as well as a brief description of why the file was singled out. The information provides a snapshot of potential threat (what has been flagged, did it damage the host, any impact on the data, etc.) that enables the team to focus their efforts. See Figure 1.
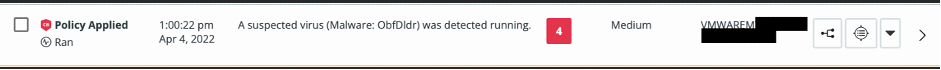
Diving into the alert details, DART personnel identify the alert is potential malware as it does not match any known antivirus signatures, largely due to it being a Windows scripting file (.wsf). See Figure 2.

This also demonstrates how ‘intelligent’ Carbon Black is. While the tool did not immediately identify the script itself to be directly malicious (based on known signatures), it did observe its runtime behavior matched known techniques, tactics, and procedures (TTPs) often seen in malware files. This led to the sensor automatically terminating the process as a proactive defensive measure defined by our corporate policies. See Figure 3.

Simply stopping the potential attack is not enough. The DART team next conducts a postmortem by leveraging Carbon Black’s Live Response feature to establish a connection with the impacted host and pull the script file for analysis from the host’s file system. See Figure 4.

Upon inspection, it is discovered the threat is a heavily obfuscated visual basic script file. Traditionally, teams would reverse-engineer the script, a practice that incurs asymmetrical cost in terms of time and effort needed to bypass the obfuscation and understand the script’s function as part of static analysis. See Figure 5.

In this case, DART personnel found a more effective alternative. Employing NSX Network Detection and Response sandbox technology to perform a dynamic analysis on the script, DART can quickly see what the script would’ve done if it was running to its full extent without any hindrances. Here, the sandbox analysis report identified the script as malicious. See Figure 6.

Cross checking the host’s start-up folder during the postmortem also showed the script did not run long enough to inflict damage. Had the Carbon Black sensor not terminated the attempt, the script would have duplicated itself to the host’s startup folder to ensure persistency. Its purpose was to create persistency (run every time the host is rebooted). See Figure 7.

The NSX Network Detection and Response sandbox analysis report also indicated an attempt to connect to a hardcoded C2 IP for further communication, an even more insidious threat since this is how additional payloads are retrieved and executed on the host. As with the other analyses, the Carbon Black console proved no such network traffic to the hardcoded IP was observed on the host, again confirming the threat was stopped as soon as it began. See Figure 8.
Knowing the complete nature of the malicious script file, DART next adds the file hash to the Carbon Black’s Banned reputation list. Now, all Carbon Black sensors will recognize and immediately deny future execution attempts of this file hash. This action also overrides the native reputation classification as Carbon Black sensors will now immediately terminate file run attempts instead of observing it for suspicious behavior prior to stepping in. See Figure 9.

Concurrently, via Carbon Black, DART triggers a purge of the malicious file hash across the entire VMware estate that completely removes it from the environment. These actions ensure the file can no longer be weaponized within the environment, even if it reintroduced under a different name or is hidden under a different folder path. See Figure 10.
The above is just one example demonstrating how Carbon Black and NSX Network Detection and Response can defend your enterprise unlike ever before. Get the complete picture by contacting your sales rep or vmwonvmw@vmware.com to schedule a customized briefing. Read more about VMware security solutions.
VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. Visit the VMware on VMware microsite and follow us on Twitter.



