by: VMware Sr. Information Security Engineer Mauricio Espinosa and VMware Lead Security Engineer Prajwal Panchmahalkar
Domains, IP addresses, and classless interdomain routing (CIDR, also known as supernetting) are a vital part of any enterprise ‘surface’ infrastructure. They are also ideal targets for today’s threat actors. Currently, there is no single-pane-of-glass method to automate discovery of dynamic assets (and their associated vulnerabilities) through continuous scanning or exploitation. Existing solutions are proprietary, designed exclusively for a specific technology or program, and not readily scalable. This makes defending the ever-changing dynamic ecosystem a spotty affair, with varying levels of siloed security that may or may not communicate with other components.
A Day 0 in the life
Let’s take a typical scenario involving Day 0 software released on a regular basis. While market demands dictate frequent releases, there are significant security challenges when it comes to discovering affected surface artifacts at scale.
For example, a critical Day 0 advisory outlining potential remote code execution (RCE) and/or distributed denial of service (DDoS) bugs is issued. Attackers may utilize the working knowledge or wait for the Proof of Concept (PoC) / working exploit to be released. They then begin enumerating publicly exposed assets worldwide—using sources such as shodan.io or censys.io—in order to identify vulnerable instances and potentially exploit them. This often involves the creation of automated weaponized worms and bots designed for nefarious attacks such as ransomware.

If an enterprise has an offensive security team, the traditional attack response is to follow the same methodology as the attacker—leverage remediation based on service-level agreements (SLAs) and severity of the vulnerability in question. Unfortunately, this process usually involves inefficient manual labor, is poorly organized as it is generally reactive in nature, and is not as effective as with proper (defined) expertise.
If the organization does not have an offensive security team, remediation is commonly based on potential detection through vulnerability scanners, antivirus, firewalls, and intrusion detection systems (IDS) or intrusion prevention systems (IPS). The main problem with this approach is that it relies on vendors taking time to release the signature, indicator of compromises (IOC), or a plugin to identify vulnerable assets. This can take anywhere from 24 to 48 hours or longer after an advisory is released, ample time for a sophisticated threat actor to gain a foothold within the corporate ecosystem, often undetected.
On top of that, there is additional time needed to scan and patch all affected assets. This opens another uncomfortable window of exposure for attackers, as well as a potential a new threat—bug bounty hunters. Following the same process as threat actors and internal personnel, the primary intention of such bounty hunters is to uncover vulnerable Day 0 assets with publicly available technical information. While this isn’t always a malicious undertaking (many companies have a bug bounty program), there is no guarantee a bug bounty hunter is working in a company’s best interest. Some pride themselves on simply disclosing their findings to public assets or demanding a bounty if there isn’t one—with dire consequences if their demands aren’t met.
A new frame of mind
VMware Attack Surface Framework redefines what’s possible in this arena. For the first time ever, companies can take advantage of a comprehensive solution employing open source surface security tools for every aspect of a full vulnerability lifecycle—all wrapped in a single pane of glass residing on top of a graphical user interface (GUI). This allows infinitely scalable modules for scanning and exploitation, in addition to scripts, that can be easily integrated or imported for use within the attack surface framework.
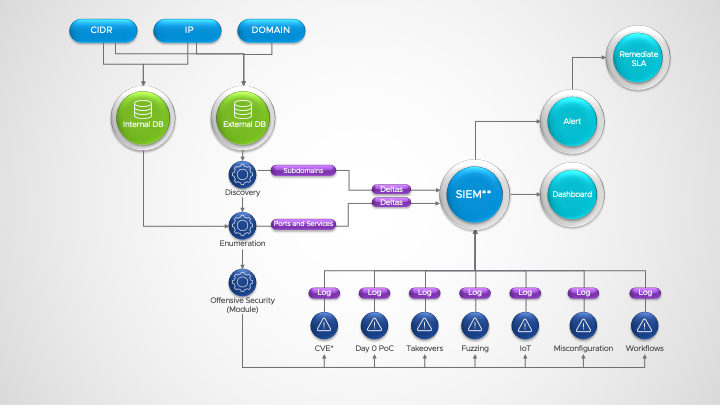
A snapshot of the Attack Surface Framework flow within the enterprise.
Attack Surface Framework is designed to augment existing cybersecurity efforts with a unique protective layer for an enterprise’s attack surface. That said, it is important to note there is no one-size-fits-all, ‘silver bullet’ remedy for modern surface attacks. Each enterprise is a complex (and unique) entity, and threat actors are equally diverse.
Contact your sales rep or vmwonvmw@vmware.com to schedule a customer briefing on this topic. We look forward to hearing from you.
Infographic legend: *Common Vulnerabilities and Exposures **Security Information Event Management
VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. Contact your sales rep or vmwonvmw@vmware.com to schedule a briefing on this topic. Visit the VMware on VMware microsite and follow us on Twitter.



