by: VMware Sr. Manager, Physical Security Systems and Technology Philip Jang and VMware Senior Security Strategist Craig Savage
Even in physical security, the usual expense-in-depth approach to security is being challenged by the simplicity of Zero Trust.
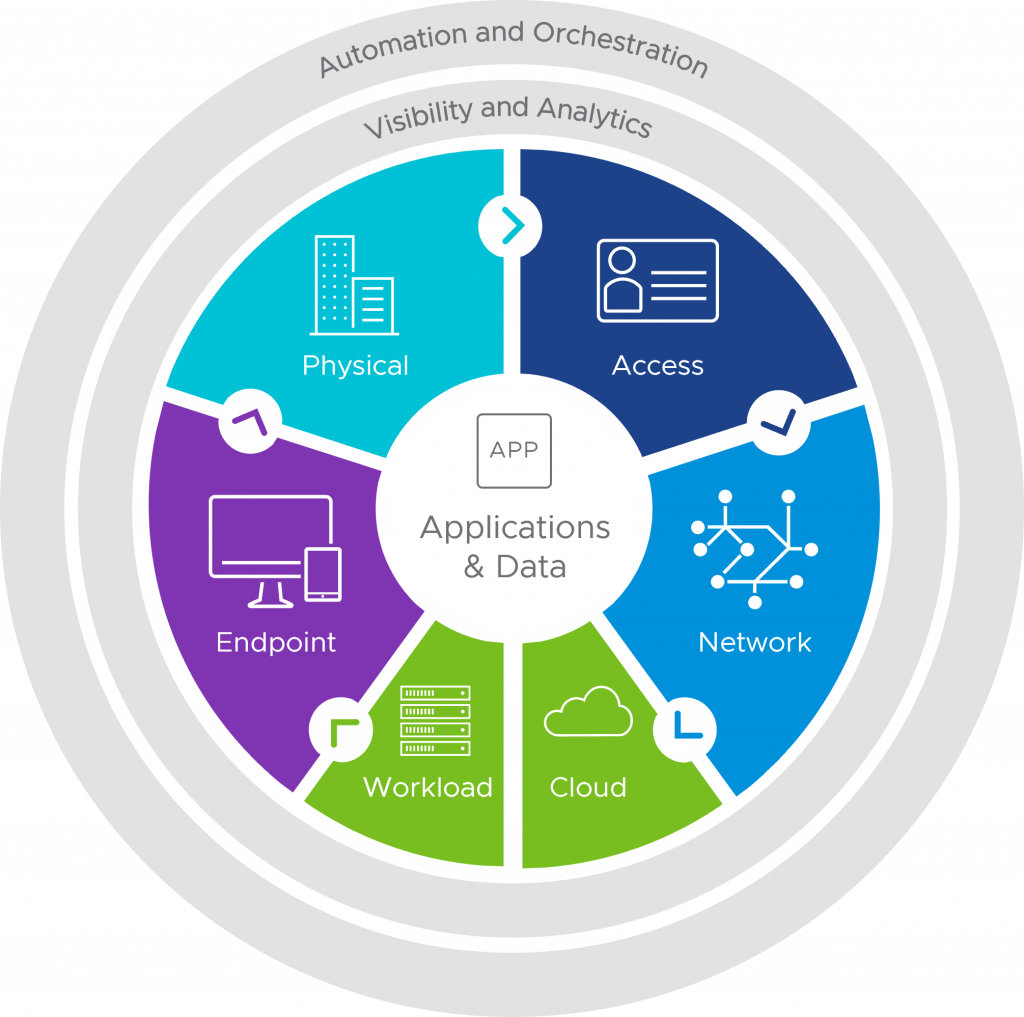
The Zero Trust model as applied to the enterprise ecosystem, including physical security.

In a previous blog, Understanding Zero Trust Via Physical Security? What a Concept!, we discussed how physical security (PhysSec) principles can help you gain an understanding of a Zero Trust cybersecurity framework. Here, we discuss the reverse: how to apply Zero Trust virtual-ecosystem concepts to PhysSec efforts to create the best defense possible—even if a breach occurs—and a nightmare for would-be threat actors.
Macro gains via micro-segmenting
It’s a hard fact to accept, but human courtesy (opening the door for someone or not challenging a missing badge) often overrides corporate mandates—people don’t want to seem rude or they simply forget about security protocols.
This is where the Zero Trust cybersecurity concept of micro-segmentation comes into play. We might not be able to change human behavior 100 percent , but we can mitigate issues created by how people act. Using clearance and access levels, sensitive areas can be micro-segmented. Such areas include R&D labs, raised-floor data center areas, forensic rooms, ad high-dollar storage areas. These levels act as physical segments requiring authentication at each layer to gain access, and can be paired with automated deprovisioning. Or to put it another way, imagine your physical badge credential is a key for certain locks. If you change the locks, the key no longer works. Now with Physical Access Control Systems (PACS), we are able to ‘change the locks’ in real time.
Plugging leaks using physical encryption
Another important Zero Trust concept is encryption. In the PhysSec world, encryption involves protecting sensitive audible information being shared within a conference room—and perhaps outside of it via sound leakage—as well shared physical data such as handouts. At VMware, we look at all possible ways data can be shared. That means PhysSec teams conduct bug sweeps of conference rooms, ensure leftover handouts are shredded, and ‘encrypt’ any audio by employing sound-masking technologies.

Persistent reauthentication
Typically, a badge has ‘evergreen’ active credentials, even if its authorization is removed from the PACS. This is because the visual appearance of a static printed badge never changes, and thus always appears valid. This represents a threat actor’s dream opportunity. Emerging smart dynamic-badge screen technology seeks to remedy this challenge by implementing visible authorization periods, ensuring the ecosystem knows a badge is active via persistent reauthentication. The software can be mated to other Zero Trust measures, such as constant authentication and real-time visual badge validation elements that are nearly impossible to replicate. Combined, these are the PhysSec equivalent of such nonpassword cybersecurity protocols as ever-changing, one-time password (OTP) codes.
Rev up the engines
In the cyber world, logging and monitoring systems ensure every application and service is visible per the Zero Trust model. Similarly in the physical world, VMware employs security patrols, cameras backed by artificial intelligence (AI), and even robots on our campuses as visibility and analytics ‘engines.’ This approach can uniquely mitigate issues like unsecured devices, persons not displaying badges, and unauthorized door access.
Coming together in perfect harmony
In the near future, our teams foresee a unified, end-to-end Zero Trust security infrastructure that encompasses both virtual and physical worlds. Such a system would detect anomalies, such as a colleague swiping a badge in Palo Alto, but then accessing a VPN based in Paris. The integrated security model would deactivate VPN access, and the Palo Alto security team members could verify the colleague’s identity in person—all in real time.

Likewise, we envision deploying advanced multifactor authentication (MFA) where a step-up-type push notification or possibly biometrics would be required in conjunction for badging for highly secure areas. Naturally, this could integrate with the entire ecosystem such that a person—even with the proper badging and biometric credentials—would only be granted access to a highly secure area in Palo Alto once it is confirmed s/he is, indeed, in Palo Alto (the system does not detect any strange ‘location anomalies’ as with the Paris VPN example).
There’s a lot more to this story as new technologies and Zero Trust models are deployed, so stay tuned!
VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. Contact your sales rep or vmwonvmw@vmware.com to schedule a briefing on this topic. Visit the VMware on VMware microsite and follow us on Twitter.



