by: VMware Cloud Security Staff Engineer Mike Schimmel
One of the most powerful ways for companies to combat threat actors is to know what tactics, techniques, and procedures (TTPs) they are using in the real world. This is where the MITRE ATT&CK framework becomes invaluable as it examines actual documented cases from advanced persistent threats, and maps those to attack matrices. For our purposes here, we are going to employ the framework and focus on the AWS public cloud and a specific tool often used to exploit it. That said, MITRE’s methodologies apply to every major cloud provider.
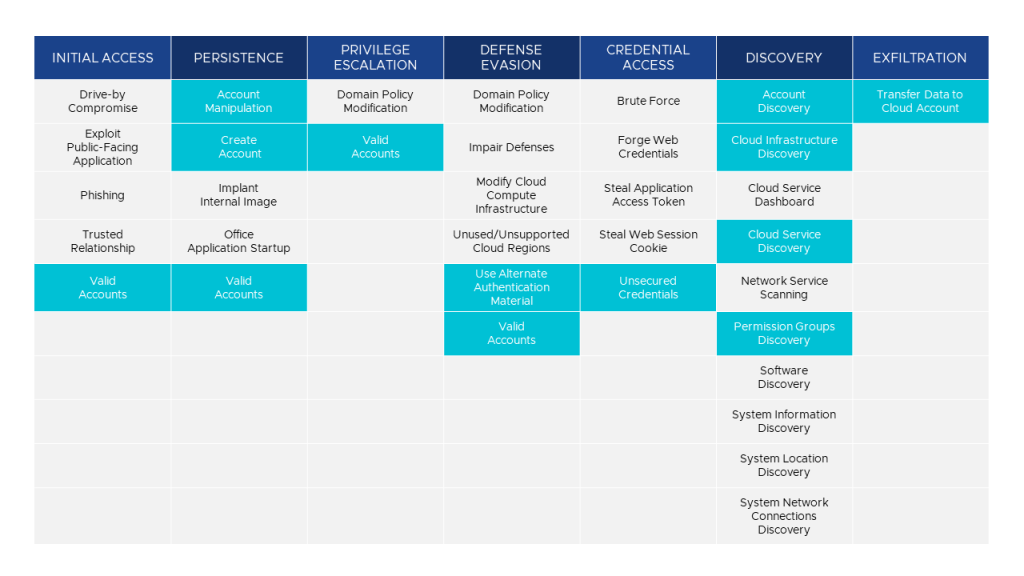
Cloud-based MITRE ATT&K Matrix for Enterprise. Source
“I don’t understand … how did they get in?”
Imagine you are on a social media platform like Twitter, but anonymous. You’re safe, right? Not always. A hacker just looks at whom you consider friends, checks out their profiles on other sites, and ultimately finds out more information on you that they have publicly posted, including ‘innocuous’ things like mother’s maiden name, a common security question. Conceptually, this is how data becomes a very effective weapon in the hands of wrong people.
For example, a developer creates some code, then tests the code in the AWS cloud via a public forum like GitHub. During the testing, the developer neglects to remove or omit access credentials via something like .gitignore, a seemingly harmless oversight. Yet this represents a door that is both public and potentially exploitable—and can stay open indefinitely without anyone’s knowledge.
Even if the developer realizes the mistake before merging the code—and removes these sensitive credentials from a previous commit—the GIT history of the source control management tool is often permanent. Those credentials are still available to anyone who downloads the repository and searches through the history. Therefore, the company is forced to rotate the credentials.
Opening the floodgates with open source

Now, you would think hackers are using sophisticated proprietary systems to breach credentials, right? While many do, especially state-sponsored threat actors, the vast majority simply use readily available open source tools.
A common scenario involves a development team with a need to access data in an S3 bucket they created. To make their lives easier, they attach an identity-based policy granting seemingly innocuous permissions like s3:Get* and s3:List* with a Resource of “*”. Simultaneously, the human resources team accesses a created S3 bucket that stores sensitive information like payroll data. This features a more granular identity policy of s3:GetObject, s3:ListBucket against only their S3 bucket resource. Although each team has created separate policies, attached to their respective users, the developer policy has now opened a door for hackers.
If any of the above S3 buckets are solely protected by the IAM identity-based permissions policy attached to users in the environment, then access is relatively easy. Any user with a policy attached with s3:List*, s3:Get* and Resource: “*” could gain access.
This is where threat actors exploit a loophole. They use an open-source tool like Pacu from Rhino Security Labs to find which buckets exist in the environment—and start exfiltrating data. Even if the stolen identity does not have the desired permissions, Pacu can still look at the attached permissions and attempt an escalation path of attaching an administrator policy. Administrator access turns a user into superuser, with the keys to the cloud environment kingdom.
All is not lost!

In ongoing cybersecurity wars, open-source tools are the weapons of choice.
Now to be clear, the security protocols in AWS are extremely safe when deployed correctly, as are other public cloud enterprise protocols. But just like the aforementioned Twitter example, tools like Pacu enable threat actors to put puzzle pieces together to gain access.
The good news is you can employ these same tools to prevent these situations. It starts by recognizing identity polices alone should not be your only defense in protecting corporate cloud resources. They should be augmented by defense-in-depth methods such as incorporating tools like Pacu, enabling encryption, using resource-based policies, implementing attribute-based access control, and similar. Approaches that substantially enhance your cloud environments’ least-privileged security posture.
VMware on VMware blogs are written by IT subject matter experts sharing stories about our digital transformation using VMware products and services in a global production environment. Contact your sales rep or vmwonvmw@vmware.com to schedule a briefing on this topic. Visit the VMware on VMware microsite and follow us on Twitter.



