As many more people work from any device in any location, the limitations of enterprise security become clear. Network security models originated in a time when people worked in office buildings on desktop computers. IT could assume that if you were on the network, you were already authenticated. As workers moved to laptops, then to mobile devices, and began accessing most enterprise applications from the cloud, the original model was patched and patched until it began to crack. Forrester Research and VMware estimate that companies use an average of 27.4 security products, and only 33 percent of these companies say that their security solutions are integrated.
Intrinsic security – built-in, not bolted-on – helps companies operate faster and more effectively in a cloud-centric model. The concepts of zero trust and ZTNA are important in building networks with intrinsic security for the modern workforce.
What are zero trust and ZTNA?
Zero trust is a term coined by Forrester Research in 2010. It comes from the security concept of “never trust, always verify.” The old castle-and-moat model of network security assumed that if you were inside the castle – the enterprise – you were verified. This model also thought of security in a very defensive way. Anyone outside the moat – the network perimeter – was a potential threat, but as hackers grew more sophisticated, it was hard to tell the insiders from the outsiders.
Zero trust starts with the assumption that no device, person, network, or packet is trustworthy. Zero-trust security controls grant access to small segments of the network at a time only to users who confirm through multi-factor authentication that they are authorized to access each network segment. The zero-trust model effectively stops criminals even after they have broken through initial defenses, because a zero-trust network blocks users each time they attempt to access a different part of the network. This model results in greater web application security, because applications and workloads have an additional level of protection within the network.
In addition, a zero-trust network does not automatically grant access to a user or device simply because that user or device has previously accessed the network. Each user and device must prove that they are authorized to access each segment of a zero-trust network every time they want access. Keeping a close eye on changing access privileges also eliminates security vulnerabilities that could be exploited by hackers. VMware’s Brian Madden has an excellent overview of what zero trust means in the real world in this VMware Tech Zone blog post.
Zero Trust Network Access (ZTNA), also a Forrester term, builds on this networking idea. ZTNA moves from a network-centric security process to an identity- and context-based security approach. In the digital world, users and their devices need quick and secure access capabilities to enterprise services and cloud-based apps from anywhere. ZTNA vets and grants users and devices policy-based access centered on the user and device identity for each connection. Users access authorized resources on-demand, and access is removed once the user disconnects.
VMware SD-WAN Zero Trust Service
VMware SD-WAN Zero Trust Service brings intrinsic security and zero trust to the enterprise WAN. VMware SD-WAN Zero Trust Service involves two of VMware’s popular and industry-leading solutions for end users: VMware SD-WAN by VeloCloud and VMware Workspace ONE. It provides Workspace ONE users with consistent, optimal, and secure cloud application access through a network of worldwide managed service nodes. The solution brings the best of both VMware SD-WAN and VMware Workspace ONE solutions into a single, cloud-hosted offer to ensure consistent application experience as users work at the office and remotely.
With VMware SD-WAN Zero Trust Service, users can access cloud resources without added latency and hairpinning, leveraging the security and benefits of a cloud-hosted solution, while easing IT deployment and maintenance of costly remote access services.
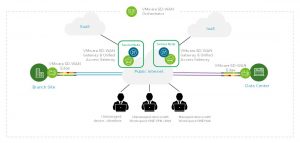
VMware SD-WAN Zero Trust Service: An adaptable network design focused on users, identity, and applications
Join our webinar, Deliver Better Remote Access with VMware SD-WAN Zero Trust Service, on Thursday July 30 to learn more about how ZTNA can improve work-at-home experiences.
To learn more about VMware SD-WAN Zero Trust Service, read our blog post VMware SD-WAN + Workspace ONE: Coming Together to Provide a Global Zero Trust Service, and the VMware SD-WAN Zero Trust Service Solution Overview.
Follow @VeloCloud on:






