Technology adoption cycles have been getting shorter because each transformative innovation is cumulatively built on the previous. These hastened cycles also bring with them ever-evolving policies and guidelines mandated through industry regulation as well as government organizations. For organizations in highly regulated industries, keeping up with compliance and regulatory guidelines can be not only disorienting, but counterproductive to meeting objectives.
Consider the timeline of a current United States Department of Defense (DoD) security framework:
- Established in 1997, the DoD Information Technology Security Certification and Accreditation Process (DITSCAP) was a first attempt to establish a standardized methodology for conducting the certification and accreditation (C&A) of defense information systems.
- This was followed by the DoD Information Assurance Certification and Accreditation Process (DIACAP). which was initiated on July 6, 2006, and was phased out beginning in March of 2014 in favor of the Risk Management Framework (RMF).
- First published in 2010, the RMF was established as a requirement in March 2014, and the deadline for DoD organizations to comply with RMF guidelines was in late 2020.
- By 2022, the concept of Continuous Authorization to Operate (cATO) became officially accepted. To be sure, the foundational principles and rapid embracement of cATO had much to do with the wide-scale adoption of the DevSecOps models pioneered at SpaceCamp and Platform One in the Air Force.
- Cyber Security Risk Management Construct (CSRMC) was announced in September 2025 as the replacement for RMF.
From guidance to implementation
On September 24, 2025, the CIO of the DoD announced the Cyber Security Risk Management Construct. The CSRMC’s stated purpose is to “produce a culture, mindset, and process that reimagines cyber risk management to be faster in keeping with the rate of change; more effectively assesses and conveys risk; and is less burdensome to cyber and acquisition professionals while ultimately providing operational combatant commanders with an accurate understanding of cyber risk to mission.”
A culmination of 15 years of DoD-wide work including the RMF, NIST 800-53, cATO, and modern innovative practices such as DevSecOps and the software factory model, the CSRMC is grounded in 10 core principles:
Automation – Driving efficiency and scale
Critical Controls – Identifying and tracking the controls that matter most to cybersecurity
Continuous Monitoring and ATO – Enabling real-time situational awareness to achieve constant ATO posture
DevSecOps – Supporting secure, agile development and deployment
Cyber Survivability – Enabling operations in contested environments
Training – Upskilling personnel to meet evolving challenges
Enterprise Services and Inheritance – Reducing duplication and compliance burdens
Operationalization – Ensuring stakeholders near real-time visibility of cybersecurity risk posture
Reciprocity – Reuse assessments across systems
Cybersecurity Assessments – Integrating threat-informed testing to validate security
[Source: Department of War Announces New Cybersecurity Risk Management Construct]
A visual representation of the construct and its phases can be found here.
Though the tenets of CSRMC have their beginnings in the DoD, they are familiar to large enterprises that operate in highly regulated industries like financial services because, ultimately, they will impact their own regulations and policies.
To understand CSRMC, understand RMF
One of the most prolific and widely adopted security constructs is the Risk Management Framework. Established more than 10 years ago by the National Institute of Standards and Technology (NIST), the RMF was widely adopted first by the DoD and ultimately across public and private-sector organizations. It provides a process that integrates security, privacy, and software supply chain risk management into a system’s life cycle. The RMF is also all about managing and controlling risk based on a process of repeatable steps demonstrated in the image below.
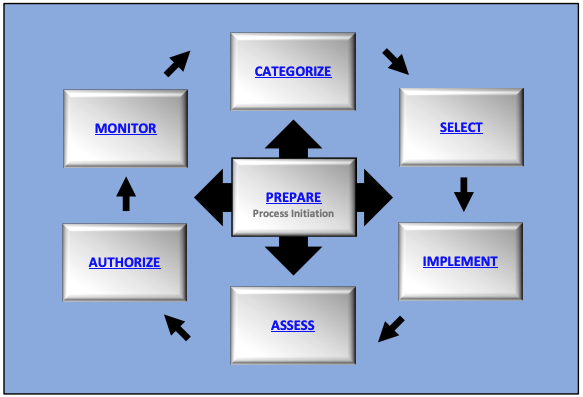
The seven steps of the RMF process: Prepare, categorize, select, implement, access, authorize, and monitor.
The above diagram, while simplified, obscures the actual scope of this work, which can include several thousand questions that must be answered, as well as a strategy for how the system will be maintained and defended during the period after the authorization is completed. For a detailed definition of these requirements, see the NIST Computer Security Resource Center. The perpetual nature of the RMF process requires operating models like the software factory, compliance architectures, and DevSecOps if it is to succeed at scale.
The continuous authorization mandate
Modern information systems are distributed by nature, which reveals the challenges of the RMF and its notion that cyber risk is managed in a three-tier system, as demonstrated in the boxes on the right in the image below. These tiers can help teams understand the role that the various inheritable controls play in reducing their risk, but as we see in the below graphic, this strategy doesn’t always work to capture the details of the development of modern applications.
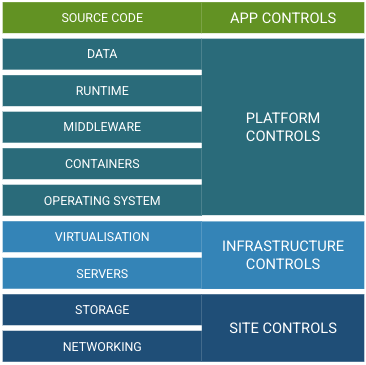
Diagram of tiered security controls from infrastructure level, business process level, and organizational level, including specific layers within each tier.
Since its inception, the RMF has served as the crux of many cybersecurity strategies. A recent significant milestone in the RMF’s history came in February 2022, with the DoD publishing a memorandum about Continuous Authority to Operate, which finds its foundation from the controls defined by the RMF. The significance of the cATO memorandum is that it signaled a shift away from a static authorization process to a continuous approach that can be more easily scaled, repeated, and audited.
This continuous approach is rooted in the understanding that managing and mitigating application security risks requires three pillars: continuous monitoring, active cyber defense, and secure software supply chain. You can read more about the strategy within the context of modern innovative practices in “Continuous Authorization to Operate Needs a DevSecOps Platform.”
But do we really need another acronym?
The new Department of Defense Cybersecurity Risk Management Construct improves upon cATO by operationalizing it into a fully integrated, automated, and life cycle-based framework. It doesn’t just turn guidance into policy—which is important in and of itself—it improves on cATO in several ways that ensure a system that maintains uniformity as it scales. Here are some ways that CSRMC refines cATO with more prescriptive outcomes.
Automation and real-time visibility
CSRMC introduces broad automation that replaces the manual, checklist-driven processes of continuous ATO. Tools now collect and analyze security data in real time, generating reports, alerts, and remedial actions automatically rather than through scheduled audits.[1][2][3]
Constant ATO posture
While continuous ATO made authorization rolling and data-driven, CSRMC formalizes a “constant ATO” model, i.e., systems remain authorized as long as real‑time metrics prove compliance. This reduces downtime from reauthorization cycles and aligns risk management directly with live operational data.[4][2][5]
Lifecycle integration
CSRMC embeds security into all five phases of a system’s life cycle—design, build, test, onboard, and operations—ensuring cybersecurity is continuous across development and deployment rather than applied after completion. This reduces risk introduction and accelerates secure capability delivery.[2][1]
DevSecOps alignment
The construct directly integrates with DevSecOps principles, emphasizing security baked into agile development pipelines. This means every code update and deployment event includes automated compliance and security checks, strengthening continuous assurance.[3][2]
Dynamic dashboards and reciprocity
CSRMC replaces static reporting with real‑time dashboards and visualization tools to maintain situational awareness for both managers and operators. It also uses reciprocity—allowing reuse of validated controls across systems—to reduce redundant assessments and speed authorization.[6][4][2]
Threat-informed and survivability focused
Unlike cATO, CSRMC includes formal threat‑informed testing and emphasizes cyber survivability—ensuring systems can operate under attack. It’s designed for “cyber defense at the speed of relevance,” directly addressing the realities of contested digital environments.[1][2][3]
The takeaway
The CSRMC is grounded in decades of work to establish a continuously viable compliance and security posture that can scale safely. It transforms cATO from a monitoring practice into a systemic, automated, and intelligence-driven construct, achieving cybersecurity at operational speed.
Simplified table of the benefits of CSRMC
| CSRMC Improvement | How It Extends Continuous ATO | Benefit |
| Automation | Moves from partial continuous assessment to full, real‑time risk management | Cuts manual effort and reporting lag |
| Constant ATO Posture | Establishes continuous authorization tied to live compliance data | Eliminates periodic reauthorization |
| Life cycle Integration | Expands monitoring into all system development phases | Embeds security from design to operations |
| DevSecOps Integration | Embeds security checks into pipelines | Speeds authorization and secure releases |
| Reciprocity and Dashboards | Enables control reuse and visibility across environments | Reduces redundancy and improves transparency |
| Threat-Informed Assessments | Adds active adversarial simulation | Improves operational resilience |
Tanzu Platform: your foundation for continuous compliance
Tanzu Platform is designed to support a continuous security and compliance model so our customers can easily understand their risk profile so they can mitigate any critical vulnerabilities and improve their MTTR in the case of a compliance or security breach.
For ore about Tanzu Platform 10.3 and its security-enhancing features check out these resources:
(Video) Tanzu Platform 10.3: Your Apps & Platform Just Got Safer 🔐 | Cloud Foundry Weekly #77
(Blog) Navigating the Vulnerability Minefield: Transforming Platform Security with Vulnerability Insights in Tanzu Platform







